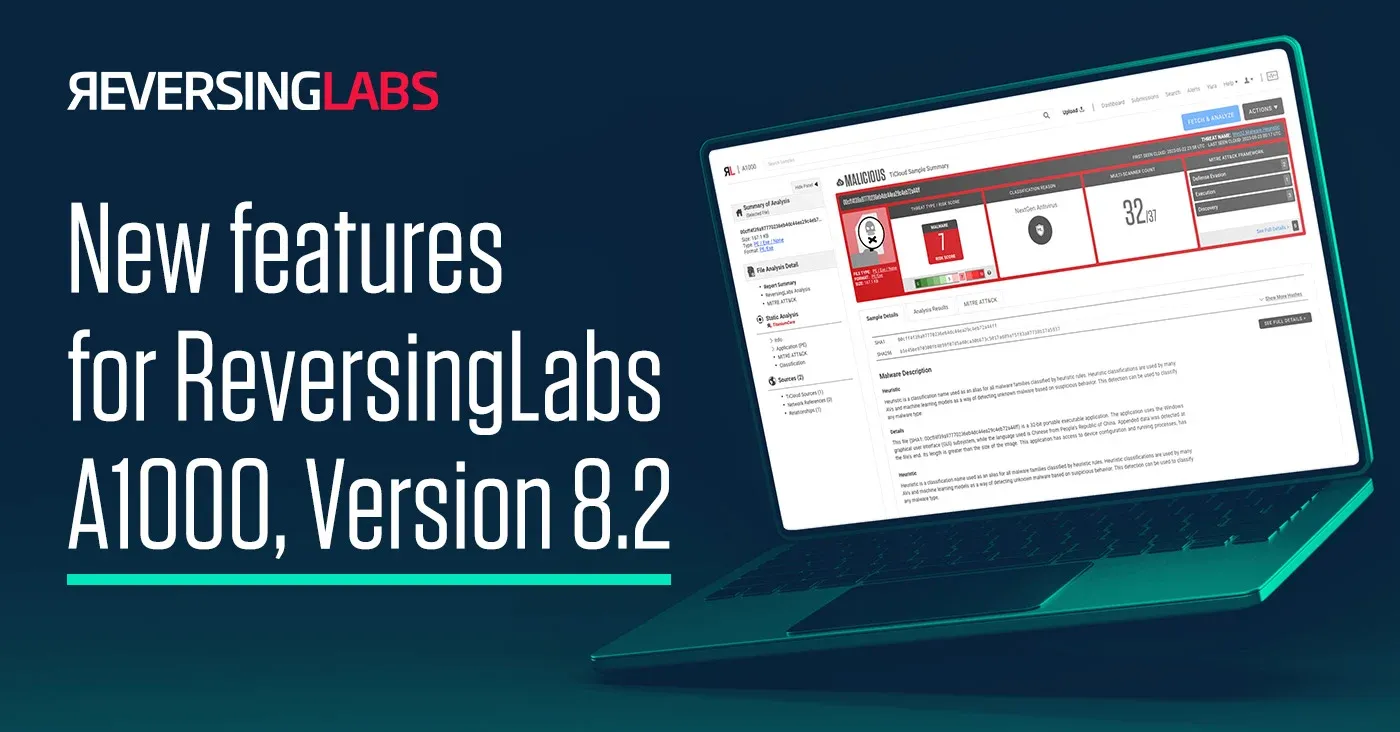
The Latest Update to the ReversingLabs A1000 Threat Analysis and Hunting Solution
We’ve updated our threat analysis and threat hunting solution with new and improved features in ReversingLabs A1000, Version 8.2.

We’ve updated our threat analysis and threat hunting solution with new and improved features in ReversingLabs A1000, Version 8.2.

Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world and our team across the full stack of security: application security, cybersecurity, and beyond.

Safe programming languages and packages can dramatically reduce vulnerabilities in your systems and applications. Here's my rundown on the safest bets for secure coding.

The big-fish IAMaaS cloud identity service provider opens its kimono. What can you learn from the exposure?

CISA and NSA issued security guidance on continuous integration/continuous delivery (CI/CD) environments — but missed an opportunity to escalate the conversation.

Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world and our team across the full stack of security: application security, cybersecurity, and beyond.

With CycloneDX 1.5, OWASP is introducing a number of new types of SBOMs. Here's a full run-down on changes — and what they mean for software transparency.

Meet ReversingLabs Software Supply Chain Security's newest feature: Levels.

The privacy of user data is one thing — but security of that data is equally important.

Here's what you need to know about third-party risk management — and why to prioritize comprehensive supply chain security.
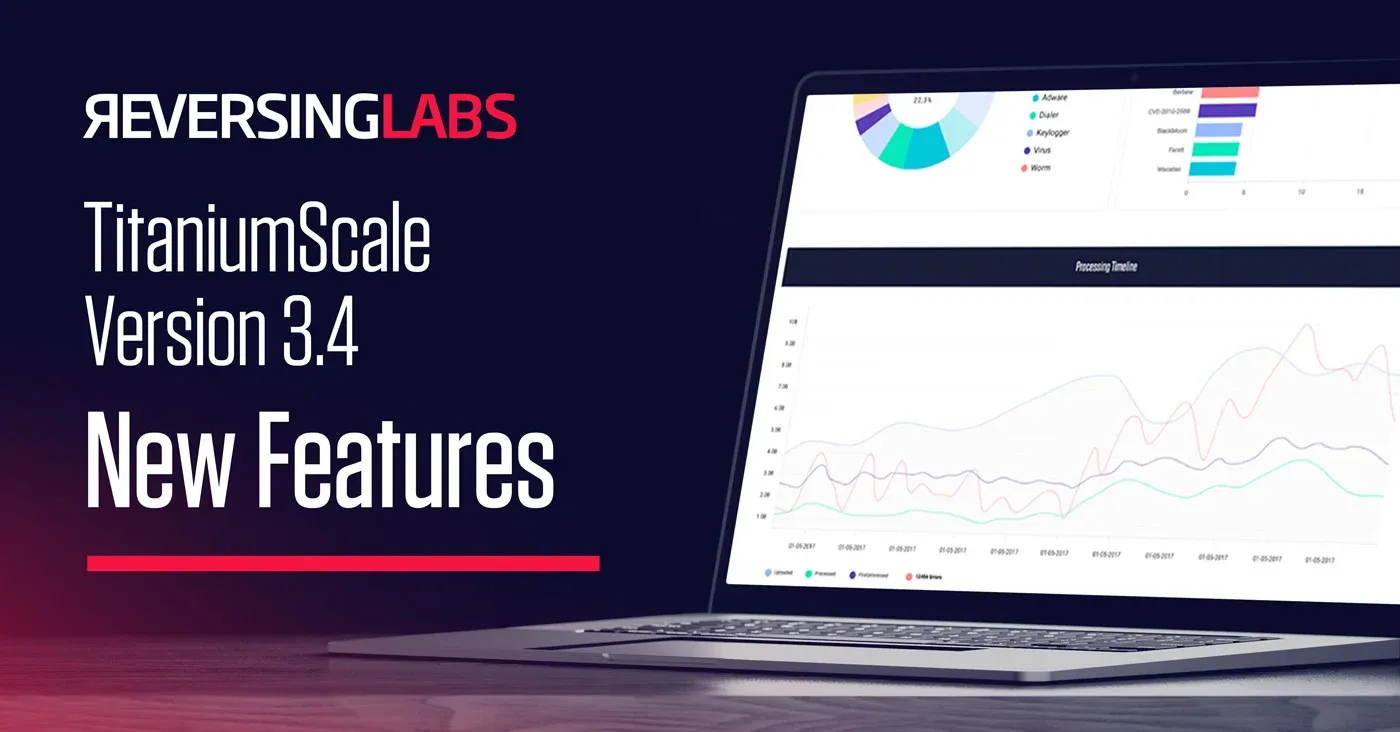
Automations, integrations, and usability improved

Tracking StealC's Rise: How YARA Rules Help Uncover a New Breed of Information Stealers

“Write once, infect everywhere” might be the new cybercrime motto, with newly discovered campaigns showing malicious npm packages powering phishing kits and supply chain attacks.
.webp&w=3840&q=75)
Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world and our team across the full stack of security: application security, cybersecurity, and beyond.

Here's how to use basic HTML to dress up your security incidents
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial