Spectra Assure® for Software Producers
Release Securely. Release with Confidence.
Detect the Full Spectrum of Software Supply Chain Threats Before You Release
Malicious actors attack every software development and supply chain stage with increasingly subtle tactics. They add malware or alter your software releases and updates with the intent to harm your business and customers.
Some of the most notable software supply chain attacks such as SolarWinds, CodeCov, and 3CX are not due to open-source issues or vulnerabilities. A post-compilation pre-deployment binary scan is critical to identifying critical hidden malware or tampering.
.svg)
Spectra Assure® examines release packages to detect embedded threats across software components, libraries, scripts, and artifacts. The analysis delivers a comprehensive SAFE report highlighting immediate threats such as malware, tampering, suspicious behaviors, or changes, and provides actionable remediation feedback.
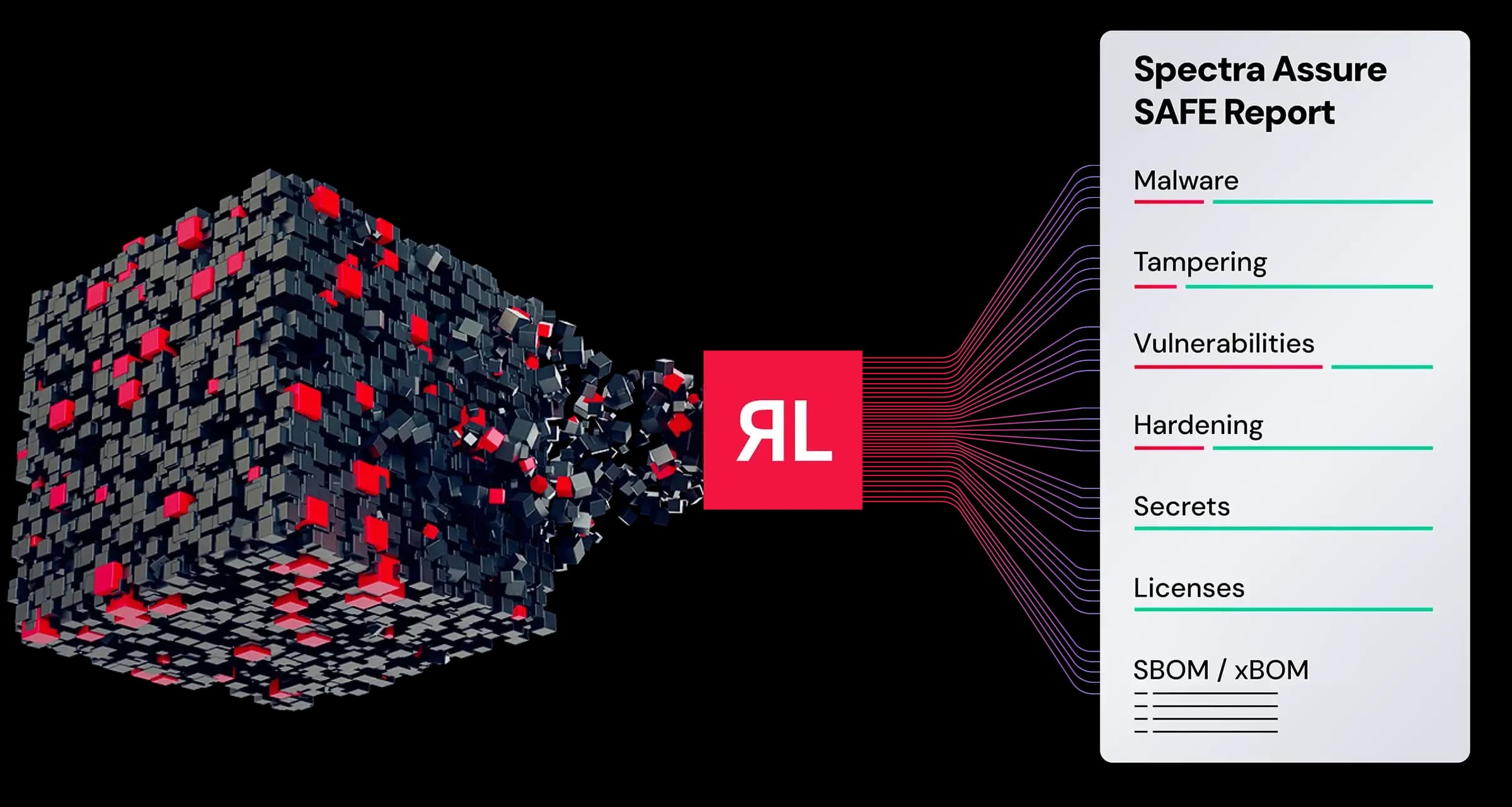
See the threats without the alert fatigue. Spectra Assure’s proprietary threat detection engines cut through noise so you focus on embedded malware, anomalous changes, and targeted attacks. It minimizes false positives using threat intelligence curated from billions of components, predictive threat models, and our in-house research team.

Spectra Assure assesses large, complex software packages, containers, virtual machines, and ML models in minutes, ensuring release workflows operate without interruption. Protect your business and customers from supply chain attacks with comprehensive visibility across proprietary, open-source and third-party software components, libraries, and artifacts within the release.

Spectra Assure maps embedded threats to specific components, libraries, and artifacts to reveal risk insights. It improves collaboration, transparency, and remediation effectiveness by clarifying:

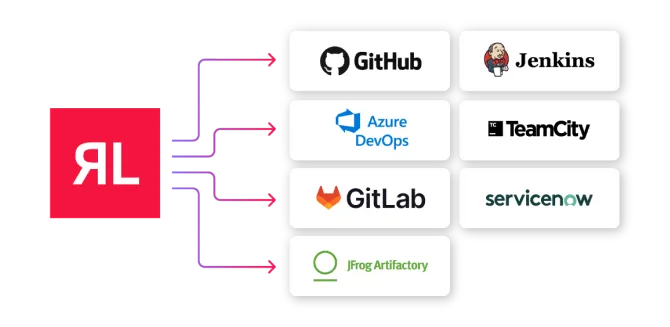
Spectra Assure has out-of-the-box integrations with popular CI solutions such as GitHub, Jenkins, Azure, and TeamCity. Assess releases from multiple product pipelines by integrating with JFrog Artifactory. Populate ServiceNow with SBOMs generated from binaries. Extensive CLI, SDK, and Docker images provide universal support for unique workflows and hybrid-cloud or on-premise deployment.
Easily tailor policies based on assigned risk tolerances. Confirm critical issues are remediated before release. Streamline compliance and attestation tasks by securely sharing report data with internal stakeholders, customers, and regulators. Spectra Assure SAFE Reports contain comprehensive SBOMs, easily digestible risk assessment summaries, and remediation guidance.



The SunBurst supply chain attack, which was behind the breach of SolarWinds, took sophistication and patience.

Discover key attack trends in RL’s third-annual Software Supply Chain Security Report. Get expert insights on emerging threats over the past year.

See what product and application security teams need to know to protect against software supply chain compromises.