
Pre-Deployment VM Security
Secure Your Virtual Machines the Fastest and Easiest Way
No Deployment. No Keys. Drop in the Images. Get the Insights.
Spectra Assure® provides the industry's first pre-deployment security scanner that comprehensively analyzes VM disk images across all major formats and file systems for malware, vulnerabilities, exposed secrets, and tampering - eliminating the need for deployment or runtime tooling.
Reduce your security assessment process from days to minutes with comprehensive security analysis of VM images without the deployment complexities. Automated workflows deliver complete visibility into security risks before your VMs ever reach production.
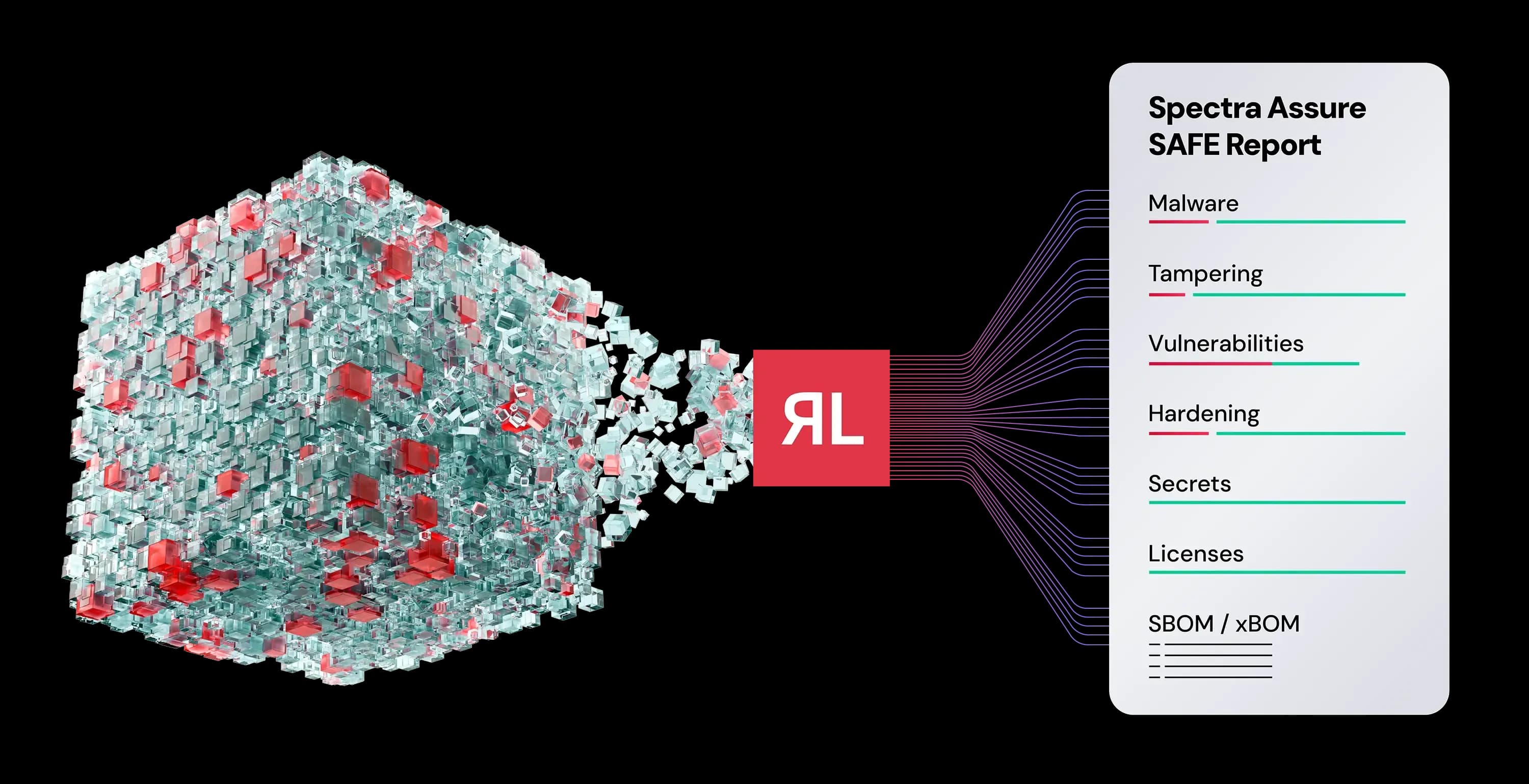
No deployment, no keys - get visibility into security risks by just scanning your VM images. Transform your security assessment process from days to minutes. Spectra Assure delivers the most comprehensive SBOM and risk analysis of VM images without the time and complexity of deployment.

Find malware, unwanted programs, vulnerabilities, and exposed secrets hidden in your VMs. Spectra Assure deconstructs your VM to its base elements to surface malware, tampering, licenses, secrets, vulnerabilities, and more. A SAFE report displays the results in an easy to consume and easy to share manner for rapid remediation.
Handle enterprise VM images with support for scanning file sizes up to 50GB. Works with Windows, Linux, and MacOS file systems with fast and comprehensive scanning. Support for VMDK, VHD, VDI, QCOW2, DMG, and OVA formats. No matter where your VMs come from or how they're packaged, we can analyze them for security risks without complex setup or runtime environments.

Streamline security validation with automated assessment workflows. Transform VM security assessment from a complex multi-day process into rapid scanning. Get standardized reports for all your virtual-machine images. Seamlessly integrate security scanning into your existing pipelines and processes for consistent, repeatable assessments across your organization.

Meet guidelines and compliance requirements like CISA, NIS2, DORA, and others with documented pre-deployment security validation. Help security teams demonstrate strong software supply chain controls while maintaining comprehensive audit trails of all assessment decisions. Give auditors and security leaders confidence with detailed reporting on every VM's security posture, from third-party virtual appliances to internally developed images.



Learn about complex binary analysis and how it tackles supply chain threats like malware, tampering, exposed secrets and more — all without source code.
Leveraging binary analysis, Spectra Assure uses a pre-deployment, static approach for virtual machine security, which is faster and more thorough. Here's how it works.
Quickly understand the current level of software safety, which threats require immediate action, and how the other risks and exposures can be addressed over time.