Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
The modern security operations center (SOC) team requires high levels of agility and accuracy to detect and respond to the latest threats. To further empower the SOC in this objective, ReversingLabs has introduced the File Enrichment API for Microsoft Sentinel offer in the Azure Marketplace.
This solution, powered by ReversingLabs TitaniumCloud, allows Microsoft Sentinel users to automatically obtain threat classification and rich context on file hash entities from a repository of tens of billions of files. This will provide users a high level of confidence in classifying a program, file, or object as goodware, malware, or unknown status. Integrating with Microsoft Sentinel's deep visibility and automation features enhances the efficiency of SOC teams.
Speed is everything when it comes to reducing the impact of an attacker in your environment. For reference, it takes an average of four hours for the QuantumLocker group to go from initial access to data encryption and eight days if they decide to exfiltrate your data. Meanwhile, IBM’s Cost of a Data Breach report (2022) found that it takes an average of 207 days for an organization to identify a data breach.
How can a SOC keep up with attackers that move this quickly? The best answer is to reduce the amount of analyst toil via automation. The use of “toil” in this post was initially defined in Google’s SRE handbook as any type of work that is: manual, repetitive, automatable, tactical, has no enduring value, and scales linearly as a service grows. Iman Ghanizada and Anton Chuvakin, both of Google, adapt this concept for the SOC in their paper “Autonomic Security Operations — 10X Transformation of the Security Operations Center”. Among other great recommendations for applying Google’s SRE lessons, they make a point to have an “automate-first” mindset. This generally means using SOAR to automate away analyst toil.
Your average SOC deals with dozens, even hundreds of alerts per day. Many of those alerts are probably missing context for the associated indicators that could help an analyst quickly decide whether or not there’s an actual threat, such as whether or not an IP address is known to be used by threat actors or if a file is goodware or malware. The analyst has to jump between tools to perform lookups and conduct additional analysis on those indicators. This is a massive waste of time, and any analyst will tell you it is one of the most tedious parts of the job.
Using automation via a SOAR platform slashes the time spent dealing with this “toil.” Rather than spending several minutes of legwork trying to see if an alert indicator is malicious, implementing a SOAR playbook that automatically enriches the alert with this additional context means the analyst only needs to spend a few seconds checking the resulting output. This empowers your analysts by allowing them to spend more time on real threats instead of wasting time closing out yet another false positive.
With the File Enrichment API offer, you can access two popular TitaniumCloud REST APIs: file hash reputation and analysis details. Enhance your Microsoft Sentinel operations to:
We've published this offer to put it in the hands of a wide variety of SOC teams, whether you're just getting started with Microsoft Sentinel or are a mature team handling many file-related alerts per day. The license structure is based on daily usage with the following tiers:
In addition, because this is a self-serve solution available in the Azure Marketplace, you're free to cancel the subscription anytime. For more details, see the offer in the Azure Marketplace.
See Free Trial on Azure Marketplace: ReversingLabs Enrichment APIs For SentinelLearn More: ReversingLabs Threat Intelligence for Microsoft Sentinel
See our full video walkthrough on how to get started, and how to provision credentials:
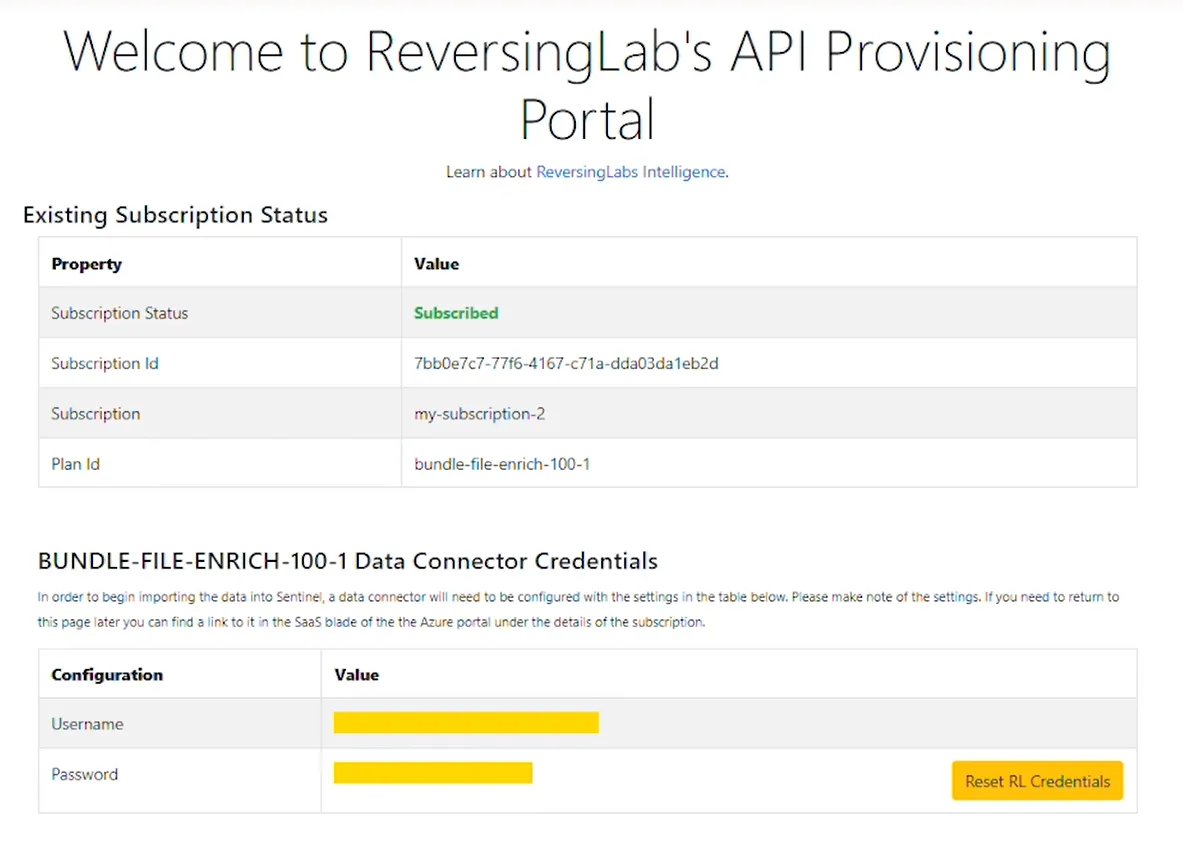
Upon finalizing the purchase and deploying the integration, you will be directed to the provisioning portal to activate the subscription. You'll be asked to provide some basic information in the provisioning portal. Once this is submitted, the activation process begins, including a provided username and password. Make sure to store these in a secure location. The credentials will be ready to use once the “Subscription status” field changes to a green “Subscribed” value, as shown below:
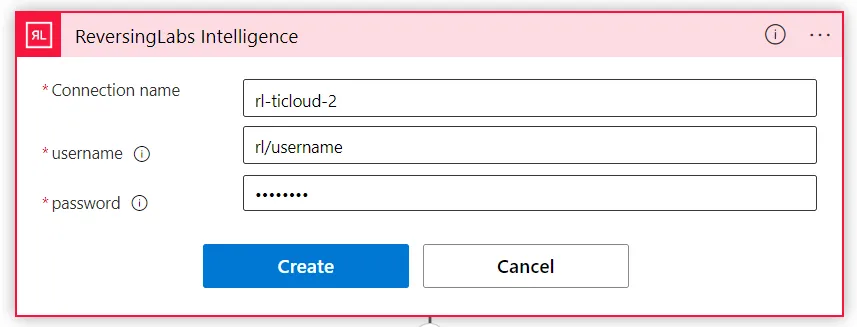
The username and password will be supplied to the ReversingLabs Intelligence Logic App connector, as seen below:
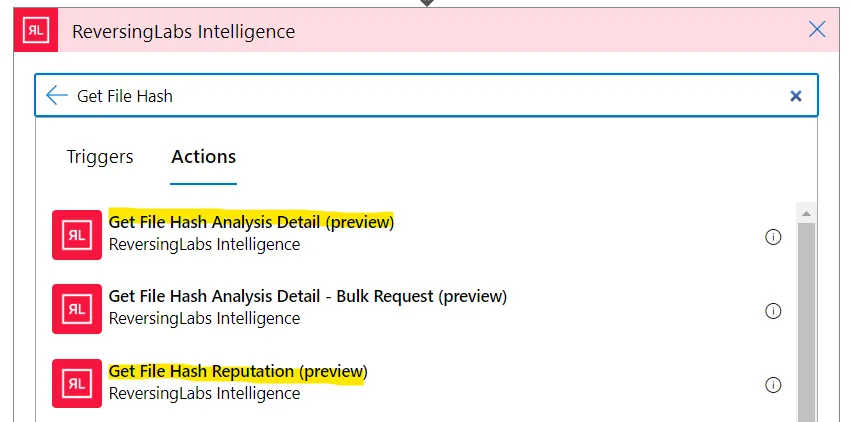
Once you've created the API connection, you're ready to start enriching files! This offer gives you access to the following connector actions:
To help you get started, we've published the ReveringLabs content pack solution for Microsoft Sentinel, which contains an example enrichment playbook and other valuable Microsoft Sentinel content. This solution can be found in the Azure Marketplace here.
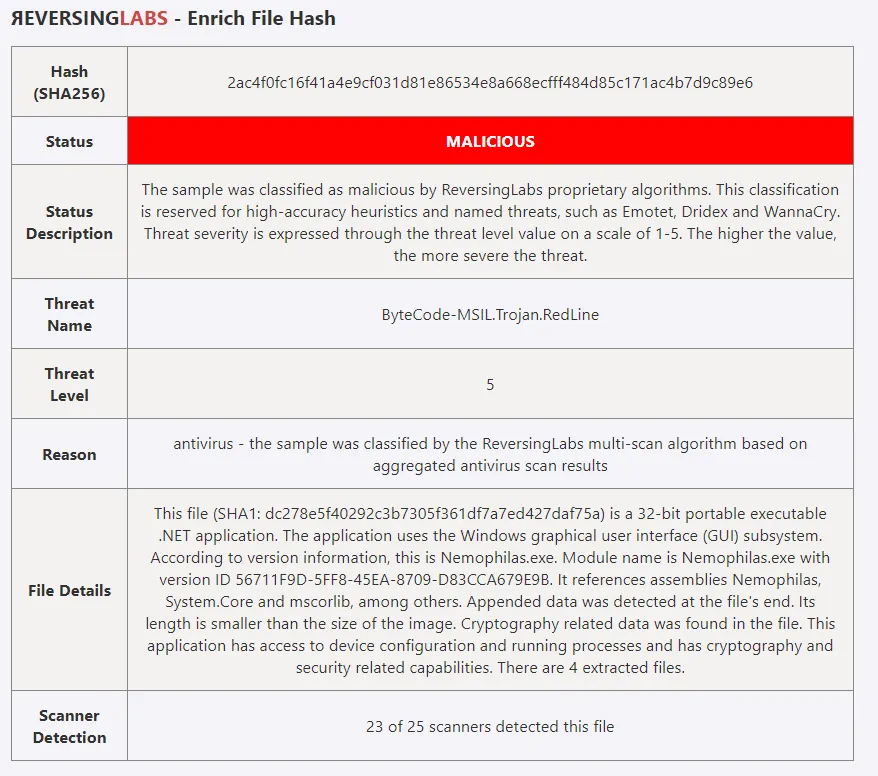
This playbook adds a comment to your Microsoft Sentinel incidents with enrichment data, as shown below:
We highly recommend installing this solution found in the Microsoft Sentinel content hub.
Some other potential use cases may include:
Contact ReversingLabs if you have other cool ideas for using the File Enrichment API for the Microsoft Sentinel offer! We're always excited to see how people are using our products. If you have any questions or need assistance with these offers, please contact support@reversinglabs.com.
Sign up to get the weekly Sentinel Threat Intelligence Briefing newsletter
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial