Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
In the software arena, winning the mind share means becoming widespread to the point of being considered a de facto standard. And when it comes to the ways in which information is shared, this means being the object format everyone gravitates to. While aspirational for many software vendors, such success is impossible to predict, difficult to achieve, and challenging to maintain.
Sometimes the solution that's first to market is the one that takes the share majority. Sometimes it's the one that solves the problem the best. And sometimes it’s the one that speaks the language of its users.
Localization is why certain object formats can only be seen within certain regions or particular language-speaking groups. Because of their limited reach, those formats are thought of as exotic or globally unknown.
In a world as diverse as ours, a security company must do much more than just localize its software. It must both speak the language of its users, and cater to their information-sharing needs. To keep its users safe, a security solution must be able to inspect both the popular and the exotic.
As an illustration of the dangers lurking in exotic email attachments, let us dissect one such regional attack. The following email has recently been received by a company based in Korea.
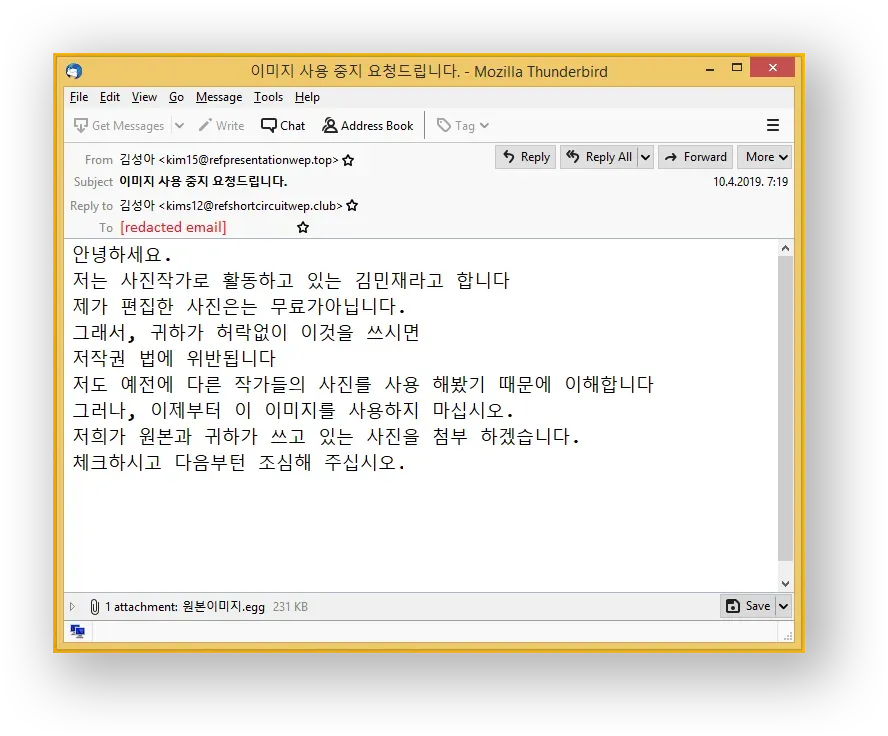
When run through an automated language translation service, the message reads something like this.
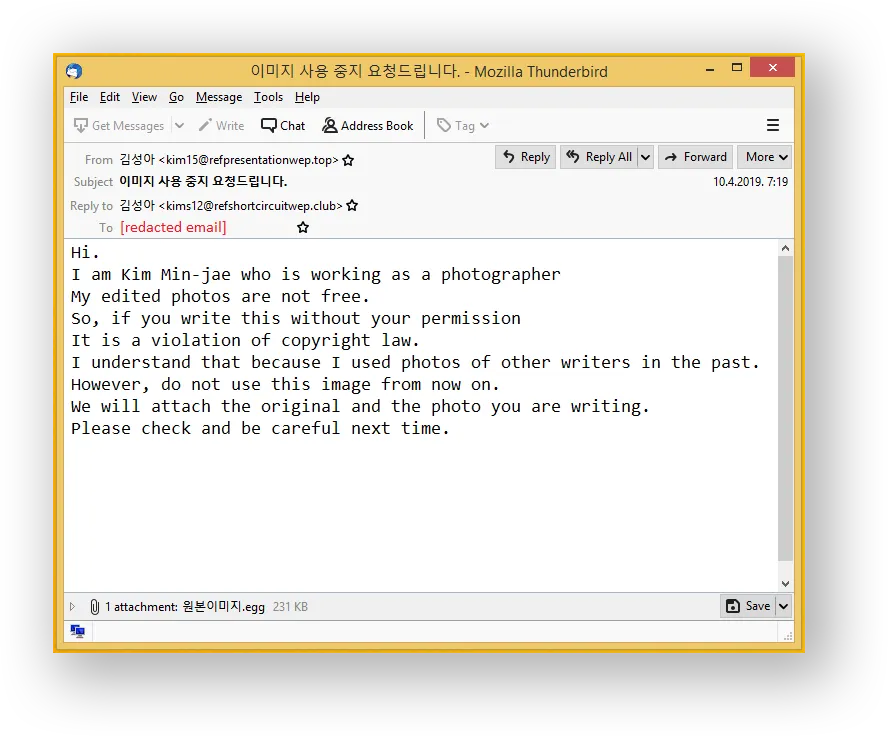
Sounds quite convincing. Because of that, it has a high chance of tricking an unvigilant reader into opening the attachment. That is where a security solutions’ breadth and depth are truly tested.
EGG is a perfect example of a regionally successful object format. It was made by a South Korean company at the time when archivers battled for dominance. From its inception, it supported Unicode, which allowed it to gain traction in the local market. It quickly expanded to business and home users alike, gaining just enough of the mind share to be thought of as the de facto standard. While all this happened in the early 90’s, it did survive through the ZIP popularity surge at the turn of the century. EGG is still around today, and it can be opened by the majority of South Korean computers.
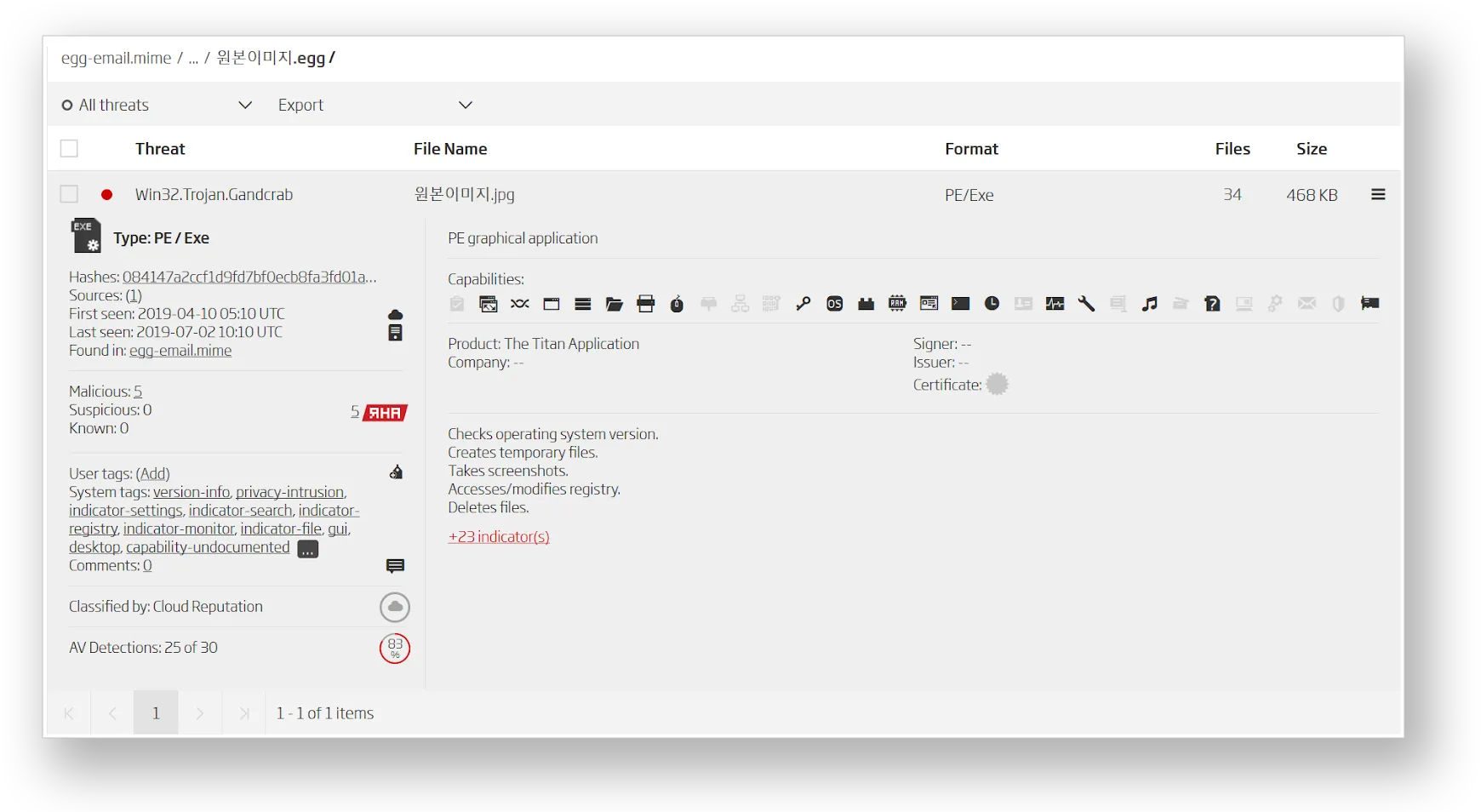
The attached archive is titled “Original image”, and the file with the same name can be found within the EGG archive as well. But its extension is a deceptive one. The “image” within is using the double extension trick in order to deceive the reader. A large number of space characters is used to hide the executable extension from being displayed in the software for extracting archives. Since the executable extension might not be visible, the unvigilant reader could assume that the file is a simple image, and open it. That wouldn’t be a good move, because in this case, the attachment is actually GandCrab ransomware. Opening the attachment would result in major problems for the organization, as most of their files would be encrypted and held for ransom. Luckily, that didn’t happen.
ReversingLabs A1000 visualizes the email headers and allows analysts to browse email contents. Email body is clearly separated from the attachments, as shown below.
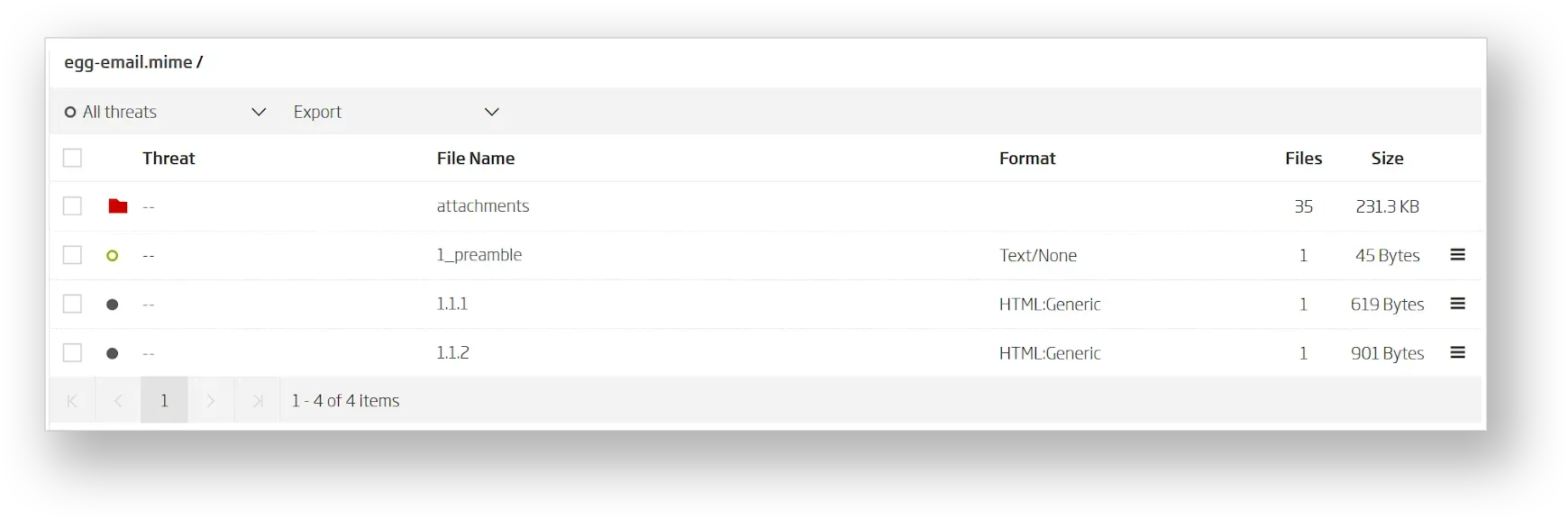
In the attachments folder, the A1000 lists all email attachments, along with their original Korean file names. They are recursively analyzed in order to increase the inspection surface. Our advanced static decomposition technology supports the EGG file format, alongside more than 360 others, and its extraction yields the actual malicious payload.
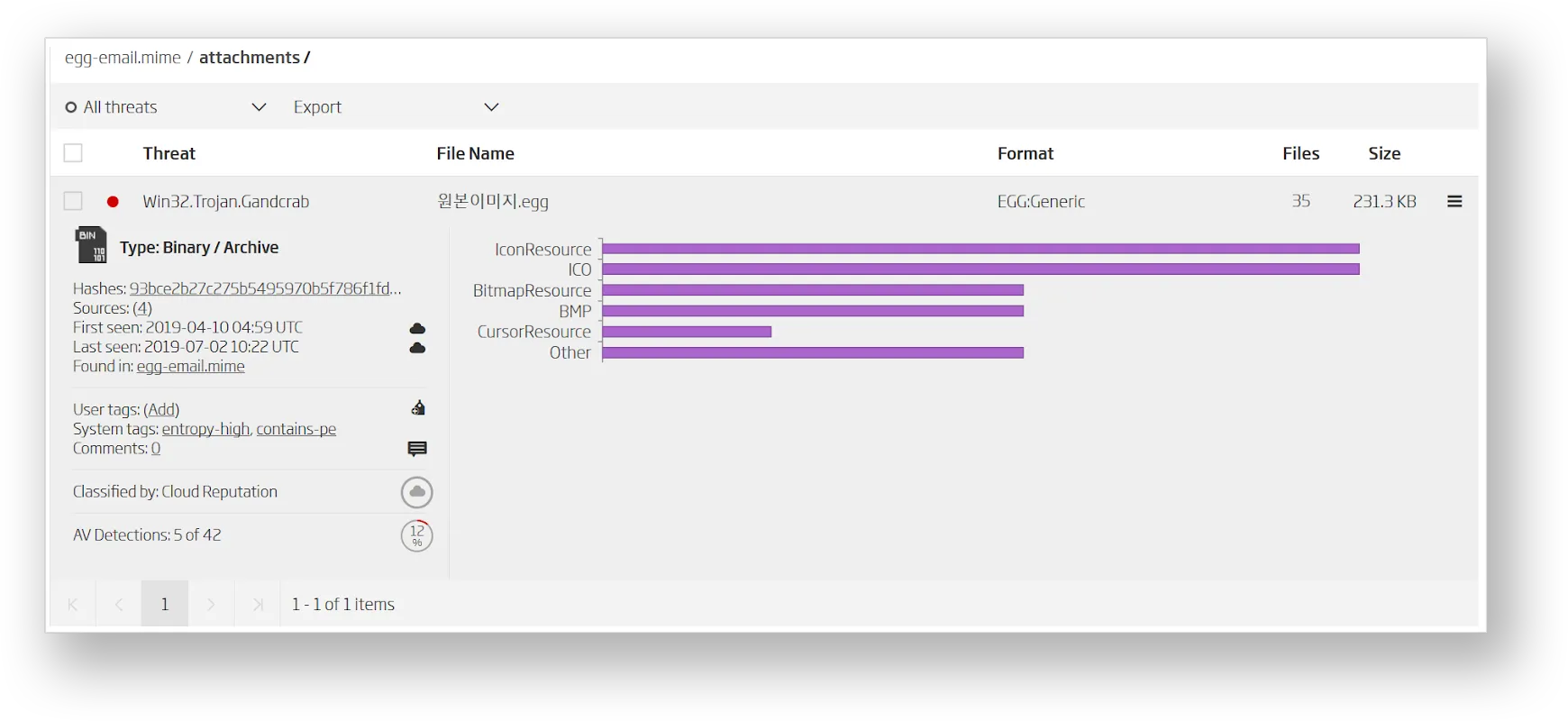
Since the archive format is an exotic object format, not many security solutions support it out of the box. ReversingLabs Titanium platform not only supports the format, but it also uses the decomposed results to determine the final classification, and ultimately convict the malicious email.
EGG archives are just one of many exotic object formats that organizations working globally will eventually see in their environment. The modern way of life entails adapting to the ways information is exchanged. Regardless of the object format that is shared, ReversingLabs Titanium platform is there to inspect the contents, and ensure that the users are protected.
IOC:
MIME - c0a947372f0b76335ce55908c5f028ada7d280b4a26ce42e0bd14f28ad0040c0
Read our prior blog in the series on Catching deceptive links before the phish.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial