Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Threat intelligence indicator feeds can be a force multiplier for the SOC team looking to improve their efficiency in detecting specific threat actors. However, many organizations rush into purchasing indicator feeds without understanding how to integrate them into their security operations effectively.
Microsoft Sentinel, a cloud-based SIEM and SOAR platform, makes it easy for SOC teams to get started with threat intelligence to boost their existing detections. Here's how threat intelligence indicator feeds can enhance Microsoft Sentinel.
Before jumping into the details of using threat intelligence with Microsoft Sentinel, it’s essential to make the distinction between cyber threat intelligence (CTI) and threat indicator feeds. CTI as a field evolved from the traditional intelligence cycle and the need to understand and counter threats to computer networks. As these threats became more complex, the need for specialized intelligence focused on the tactics, techniques, and procedures (TTPs) used by threat actors emerged. Today, many private organizations have dedicated teams focusing solely on producing CTI to enhance their security posture.
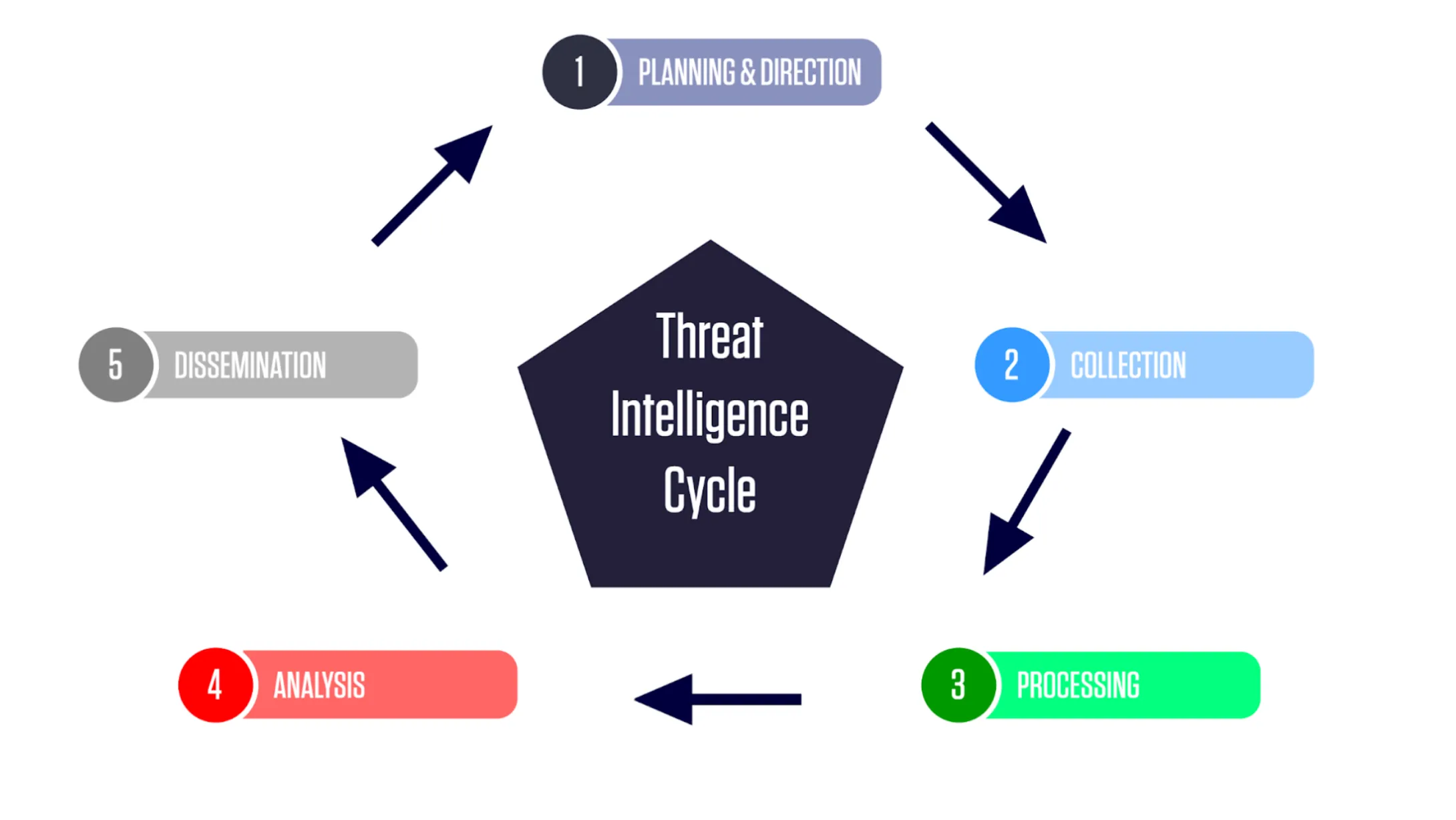
Threat intelligence cycle flowchart.
Threat intelligence indicator feeds are a direct product of the cyber threat intelligence cycle. These feeds contain indicators of compromise (IOCs) and other actionable intelligence related to threats derived from the ongoing monitoring and analysis of threat actor activities. Indicators typically found in a feed include IP addresses, domain names, URLs, and file hashes. Feeds are generally provided by trusted third-party vendors, government entities, or open-source sources.
See Free Trial on Azure Marketplace: ReversingLabs - Early Detection of Ransomware for SentinelLearn More: ReversingLabs Threat Intelligence for Microsoft Sentinel
A regular influx of new indicators is an excellent way to measure threat indicator feed value, but the quality of their indicators is the most important.
Threat intelligence feed providers must ensure that the included indicators are still valid. The feed should indicate if a threat actor no longer uses a previously marked IP address. Feeds that provide helpful context for each indicator, such as threat actor names and type of threat, demonstrate the level of care from the intelligence provider.
Many feeds focus on particular threat categories, such as the ReveringLabs ransomware indicator feed. All of this analysis leads to the false positive/false negative rate, which is the ultimate deciding factor in the value of an indicator feed. There’s little value in flooding security tools with indicators irrelevant to the environment.
Microsoft Sentinel makes it easy to start working with threat intelligence indicator feeds. There are currently five ways to import indicators into Microsoft Sentinel:
After connecting an indicator feed to Microsoft Sentinel, analysts can access the indicators within the Threat Intelligence menu. This menu empowers analysts to apply filters based on various attributes such as feed source, threat type, and confidence level. Additionally, indicators are easily searchable, providing analysts with convenient access to the desired information.
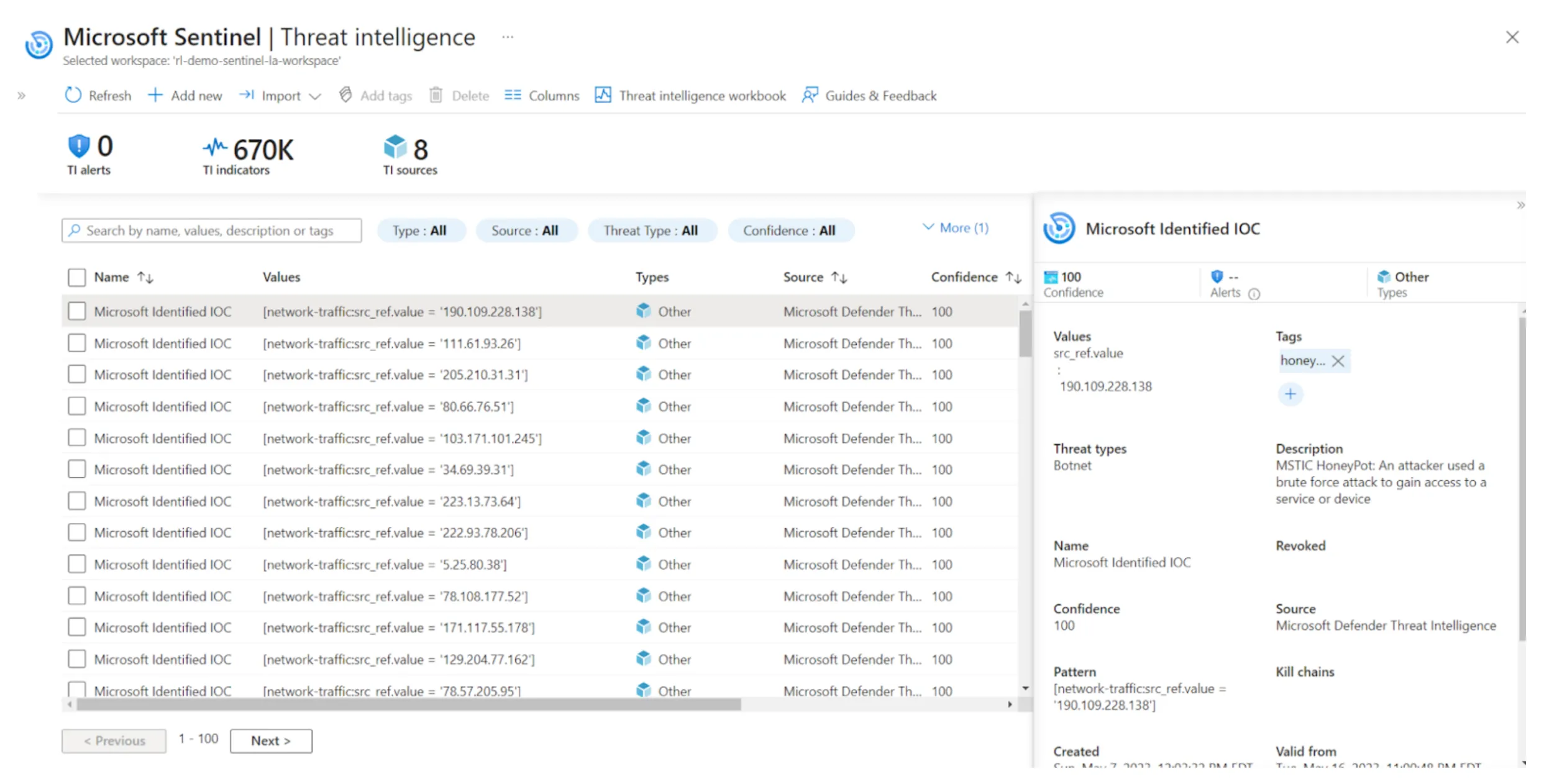
Microsoft Sentinel’s Threat Intelligence menu.
It is important to note that each threat intelligence feed may have distinct methods for describing each indicator. At a minimum, Microsoft Sentinel requires inserting the indicator value and type into the threat intelligence table. However, the threat intelligence module offers several additional fields that the SOC Operator can utilize to provide valuable contextual information.
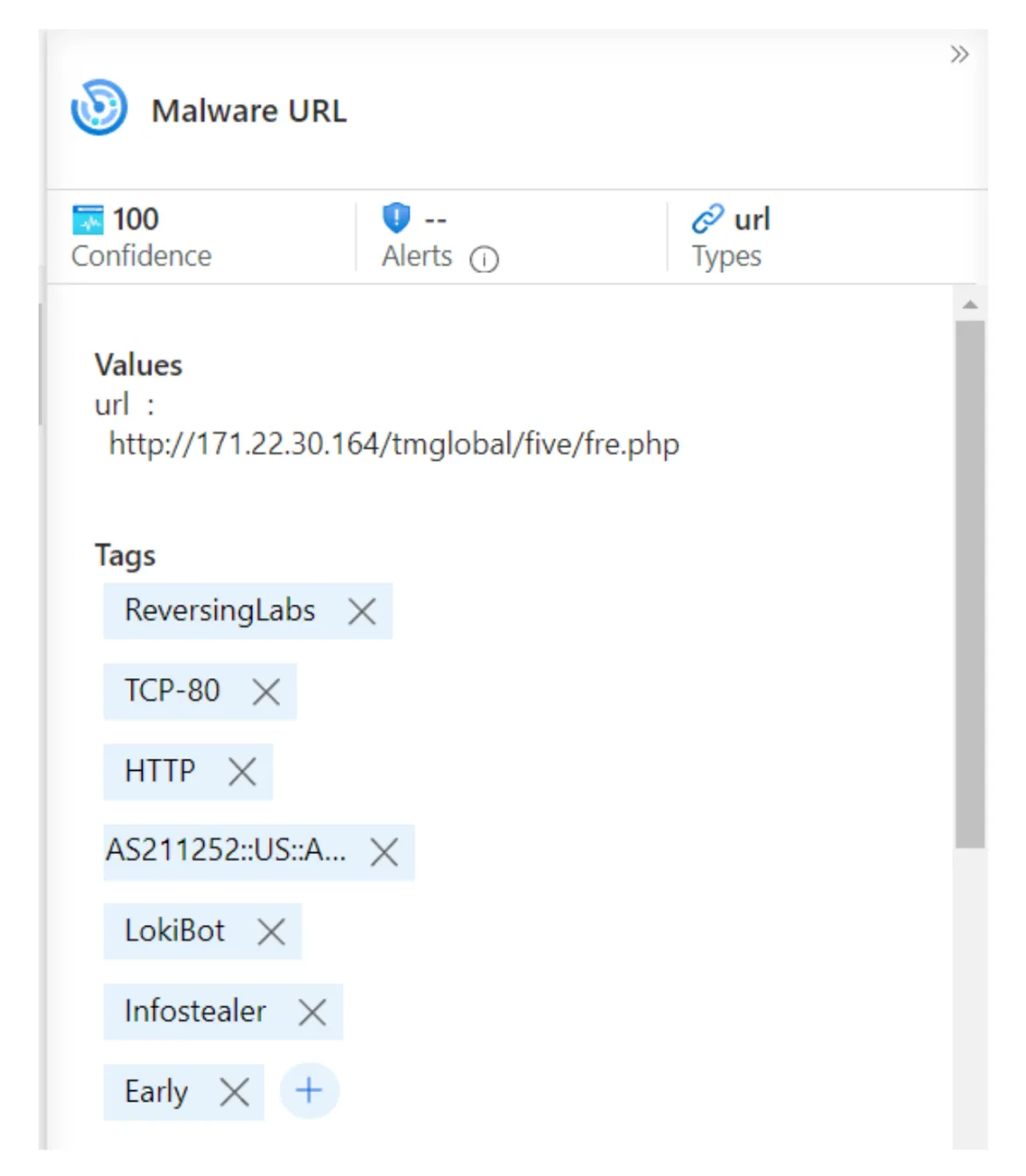
Indicator tags example.
Understanding where to get indicators and how to plug them into Microsoft Sentinel is only one half of the equation. Once the SOC team has added a healthy set of indicators, the next step is using Microsoft Sentinel’s powerful querying, hunting, and alerting capabilities.
Enable TI analytic rule templates
Enable rules relevant to ingested data sources. Several out-of-the-box analytic rule templates map threat intelligence indicators to log data. In the rule templates tab, using the data source filter values "Threat Intelligence - TAXII," "Threat Intelligence Platforms," and "Microsoft Defender Threat Intelligence," return the associated rule templates.
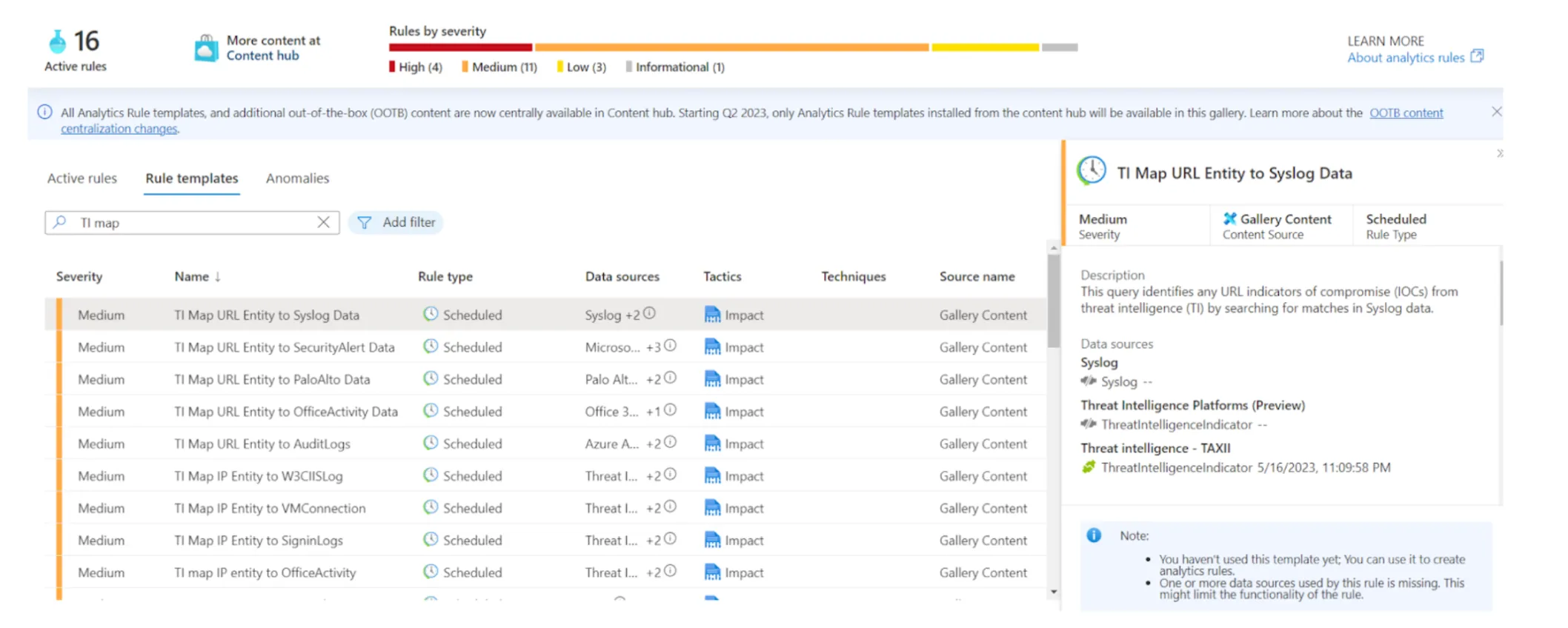
Example analytic rule templates for threat intelligence indicators.
Hunt for threats with indicator matching queries: Microsoft Sentinel's threat hunting feature enables SOC teams to search for threats in the environment proactively. There are few out-of-the-box hunt queries for threat intelligence indicators imported to Sentinel. However, it's also straightforward to create customized hunt queries.
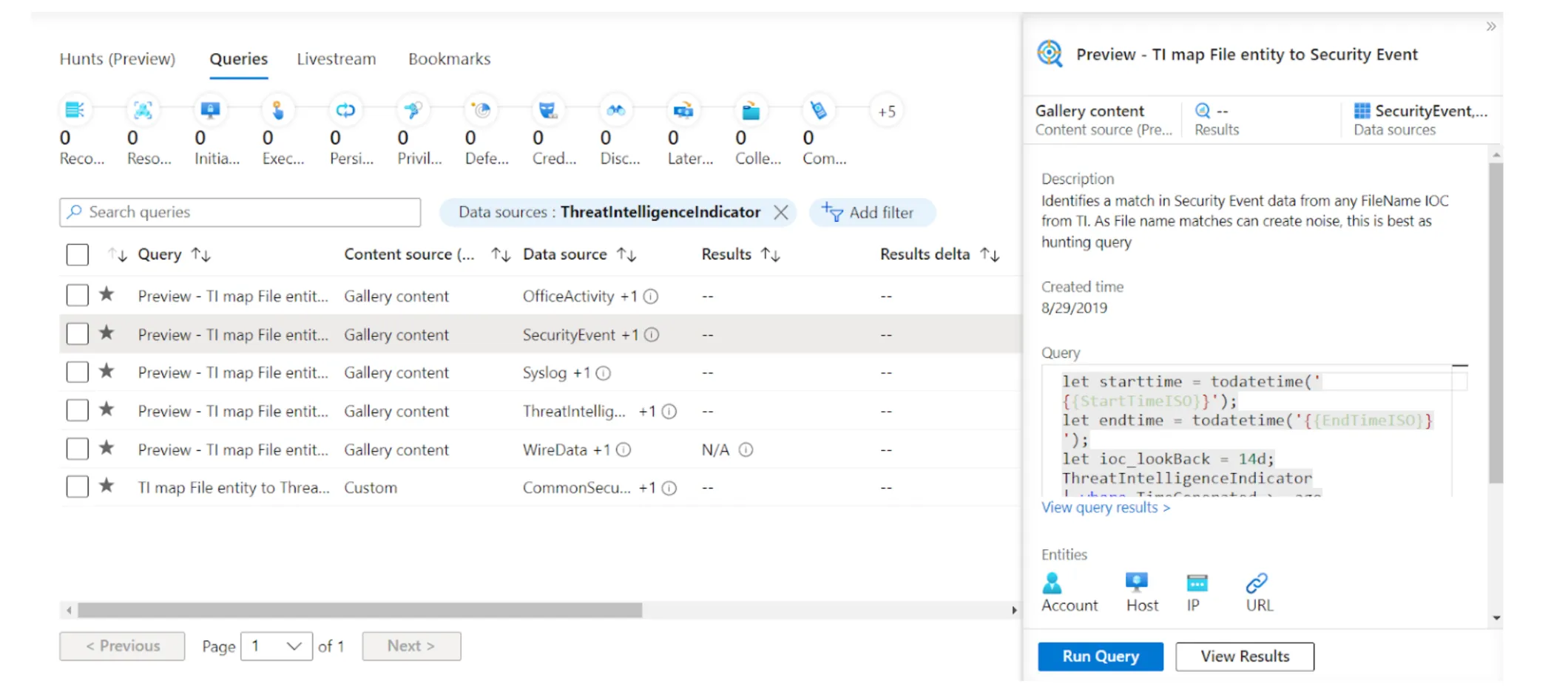
Hunt queries for the ThreatIntelligenceIndicator table.
Visualize indicator data with workbooks: In addition to the above, installing workbooks relating to threat intelligence indicators, such as Microsoft’s “Threat Intelligence” template or workbooks included in ReversingLabs’ free Content Pack, provides helpful visuals for metrics and identifying threats.
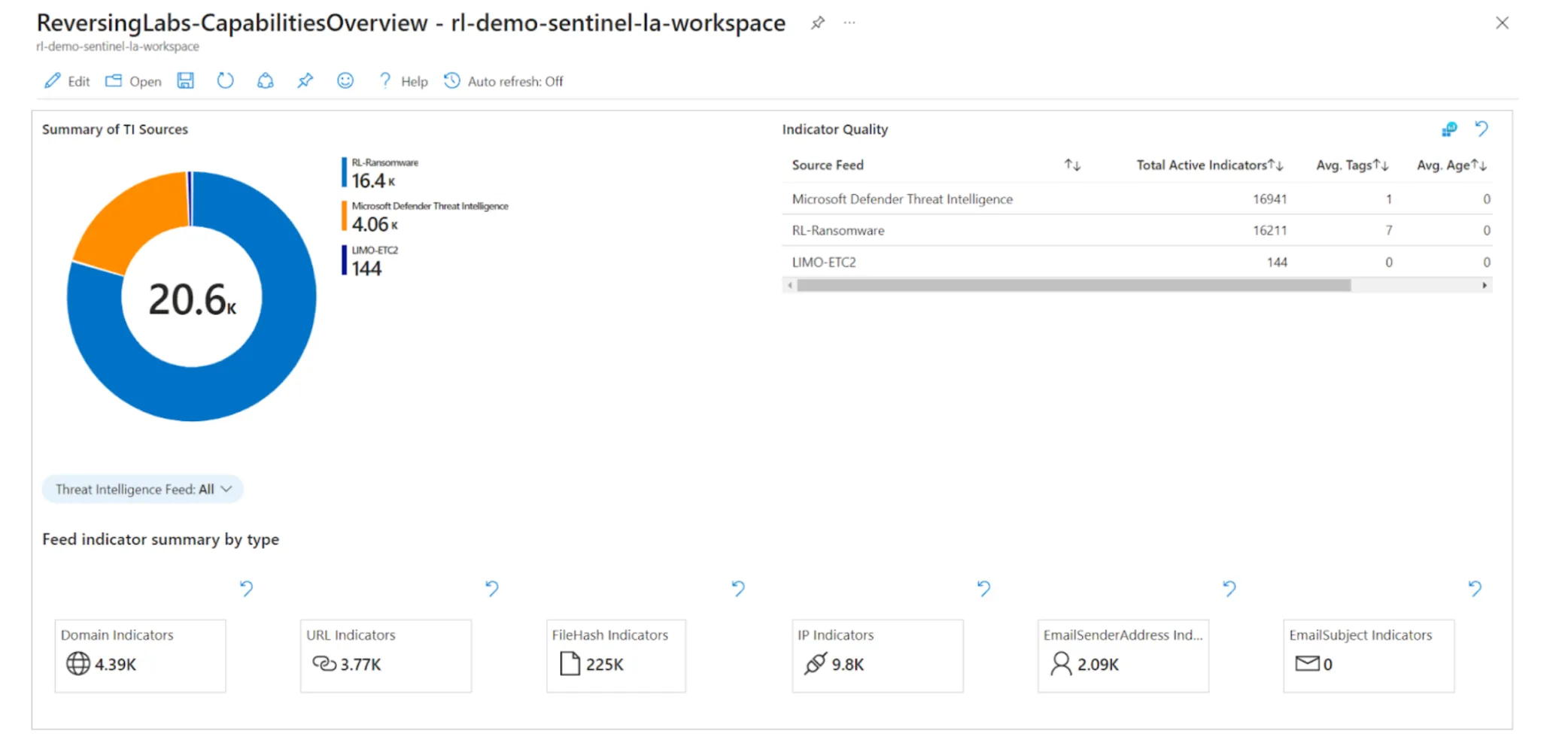
ReversingLabs-CapablitiesOverview workbook.
The out-of-the-box content mentioned in the previous section covers most use cases for the average SOC team. Building a query to match custom data sources is easy with KQL table joins. The query should be based on a particular indicator type to keep things simple - this example will focus on IP address indicators. Using the ThreatIntelligenceIndicator table, the first step is to get the latest hands summarized by the IndicatorId value. From there, adding a filter for only active indicators is a good idea. To get only IP address indicators, add another filter to include rows with values for NetworkIP, EmailSourceIpAddress, NetworkDestinationIP, and NetworkSourceIP columns using the isempty() function.
ThreatIntelligenceIndicator
| summarize LatestIndicatorTime = arg_max(TimeGenerated, *) by IndicatorId
| where Active == true
| where isnotempty(NetworkIP) or isnotempty(EmailSourceIpAddress) or isnotempty(NetworkDestinationIP) or isnotempty(NetworkSourceIP)
Finally, the indicator column name is normalized into the name TI_ipEntity:
| extend TI_ipEntity = iff(isnotempty(NetworkIP), NetworkIP, NetworkDestinationIP)
| extend TI_ipEntity = iff(isempty(TI_ipEntity) and isnotempty(NetworkSourceIP), NetworkSourceIP, TI_ipEntity)
| extend TI_ipEntity = iff(isempty(TI_ipEntity) and isnotempty(EmailSourceIpAddress), EmailSourceIpAddress, TI_ipEntity)
The first half of the query should now look like this:
ThreatIntelligenceIndicator
| summarize LatestIndicatorTime = arg_max(TimeGenerated, *) by IndicatorId
| where Active == true
| where isnotempty(NetworkIP) or isnotempty(EmailSourceIpAddress) or isnotempty(NetworkDestinationIP) or isnotempty(NetworkSourceIP)
| extend TI_ipEntity = iff(isnotempty(NetworkIP), NetworkIP, NetworkDestinationIP)
| extend TI_ipEntity = iff(isempty(TI_ipEntity) and isnotempty(NetworkSourceIP), NetworkSourceIP, TI_ipEntity)
| extend TI_ipEntity = iff(isempty(TI_ipEntity) and isnotempty(EmailSourceIpAddress), EmailSourceIpAddress, TI_ipEntity)
Next, join the indicator results with your targeted data source. For this example, the table used is called DemoTable_CL, and the column containing IP addresses is ip_address_s. To find only matching IP addresses with those found in the ThreatIntelligenceIndicator table, simply use the join operator on the appropriate columns:
| join DemoTable_CL on $left.TI_ipEntity == $right.ip_address_s
Without specifying the join flavor the default is innerunique, which returns each matching row on the right table (DemoTable_CL) for each TI_ipEntity indicator value. The full query is now:
ThreatIntelligenceIndicator
| summarize LatestIndicatorTime = arg_max(TimeGenerated, *) by IndicatorId
| where Active == true
| where isnotempty(NetworkIP) or isnotempty(EmailSourceIpAddress) or isnotempty(NetworkDestinationIP) or isnotempty(NetworkSourceIP)
| extend TI_ipEntity = iff(isnotempty(NetworkIP), NetworkIP, NetworkDestinationIP)
| extend TI_ipEntity = iff(isempty(TI_ipEntity) and isnotempty(NetworkSourceIP), NetworkSourceIP, TI_ipEntity)
| extend TI_ipEntity = iff(isempty(TI_ipEntity) and isnotempty(EmailSourceIpAddress), EmailSourceIpAddress, TI_ipEntity)
| join DemoTable_CL on $left.TI_ipEntity == $right.ip_address_s
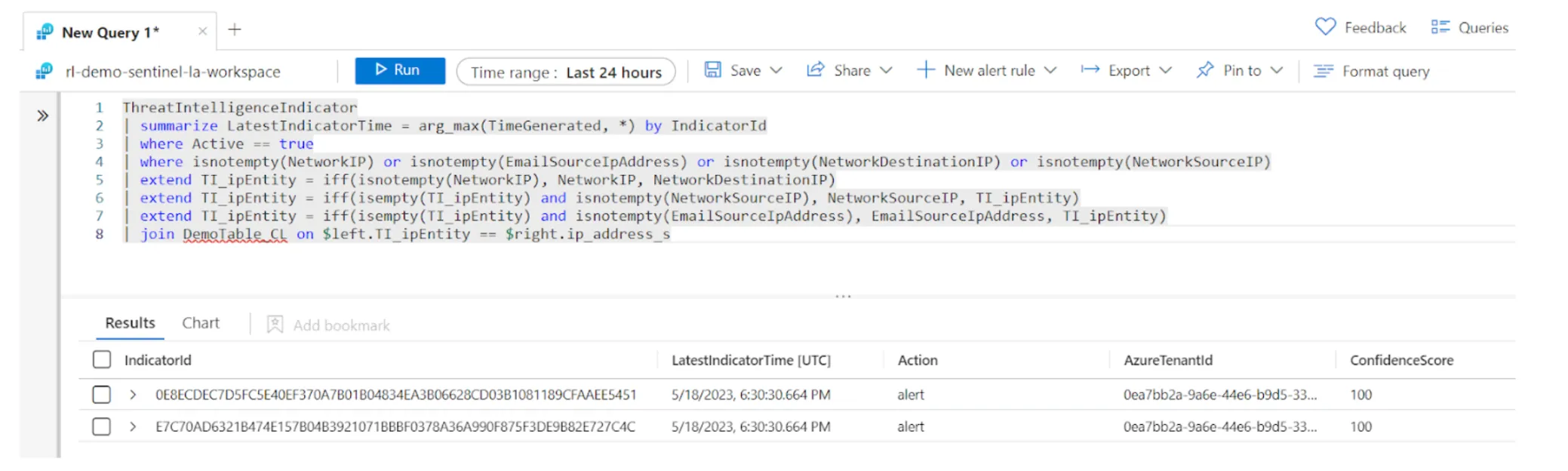
Indicator matching query results.
This is just the tip of the iceberg when building queries that match threat intelligence indicators in Microsoft Sentinel. Be sure to check out the templates mentioned above for more ideas.
This overview of cyber threat intelligence and threat intelligence indicator feeds demonstrated a few examples of using Microsoft Sentinel's threat intelligence capabilities, and finding threats in your data sources using threat intelligence indicators. For SOC teams looking to get started with a threat intelligence indicator feeds, ReversingLabs offers a free 30-day trial of the ransomware indicators feed available in the Azure Marketplace.
Sign up to get the Sentinel Threat Intelligence Briefing newsletter
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial