
In one of our earlier blogs we illustrated how remote access trojans (RATs) can inadvertently serve as a wealth of information, revealing their geolocational spread, information about the malicious actors using them, and their infrastructure. The fact that these tools, usually by definition, hold a communication channel open provides an opportunity for a small peek to the other side. In this blog post, however, the spotlight will be on something different.
Malware is like a constantly evolving open-source project. It’s often modified daily by the same or different authors. In the fight against malicious software, it is crucial to find and successfully detect all its iterations. The example of the SpyNet RAT will show why static analysis is an ideal tool for this purpose. Using static analysis, it is possible to find out what the evolution of SpyNet looked like, how different versions can be found without even looking at the code, and how to find its authors so their future activities can be monitored.
From outlier to ancestor
The research starts with CyberGate, a RAT that is still active 9 years after its initial release. CyberGate is one of the 40+ malware families whose configuration gets statically extracted through the ReversingLabs Titanium Platform.
While reviewing the extracted configuration of the server samples, some discrepancies can be noticed in the extracted version string. One version, 2.6, doesn’t contain a version prefix and uses a more succinct major.minor versioning format, as shown in the chart below. There are enough such samples of this version that a CyberGate sample, picked at random, has a good chance to fall into this group.
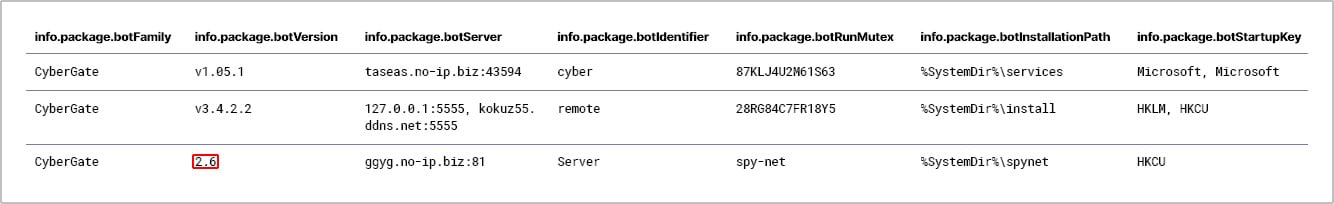
Figure 1: A snippet of CyberGate configurations extracted by the TitaniumPlatform. The outlined version sticks out suspiciously from the other two
New and valuable insights may be found by digging deeper into some of the other configuration fields of the misfit samples. A good number of them reference a known RAT, SpyNet, in other configuration fields. According to various ‘hacking’ forums, it is not a secret that the two of them share a connection. In fact, the author’s post about the first version of CyberGate is still available.
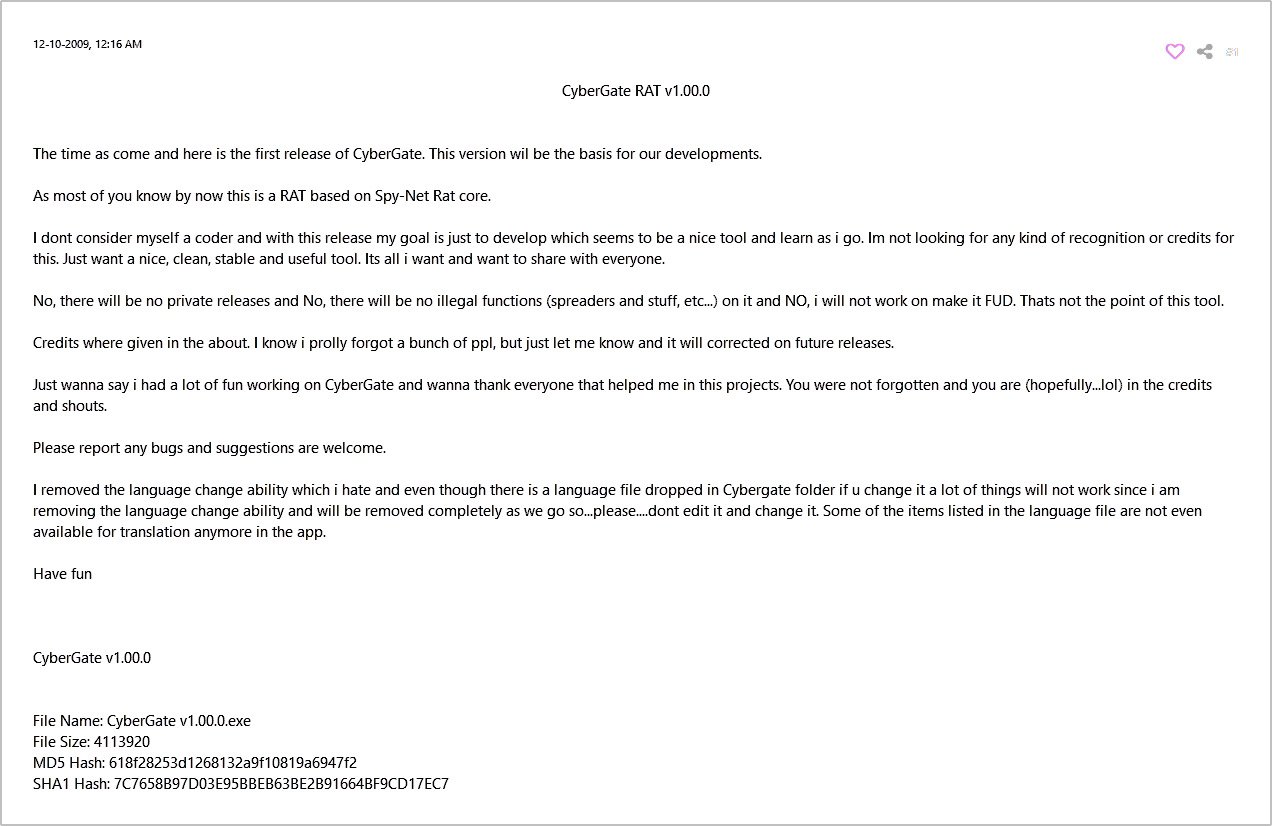
Figure 2: The original CyberGate v1.00.0 text posted on the HackHound board, and later reposted to HackForums
The post suggests that the CyberGate author picked up SpyNet source code, which is publicly available, and continued its development from there. Based on the outlier versioning, it can be presumed that they used the version 2.6. Our first step is to find earlier versions of SpyNet using various ReversingLabs technologies, starting with the RHA1 file similarity algorithm.
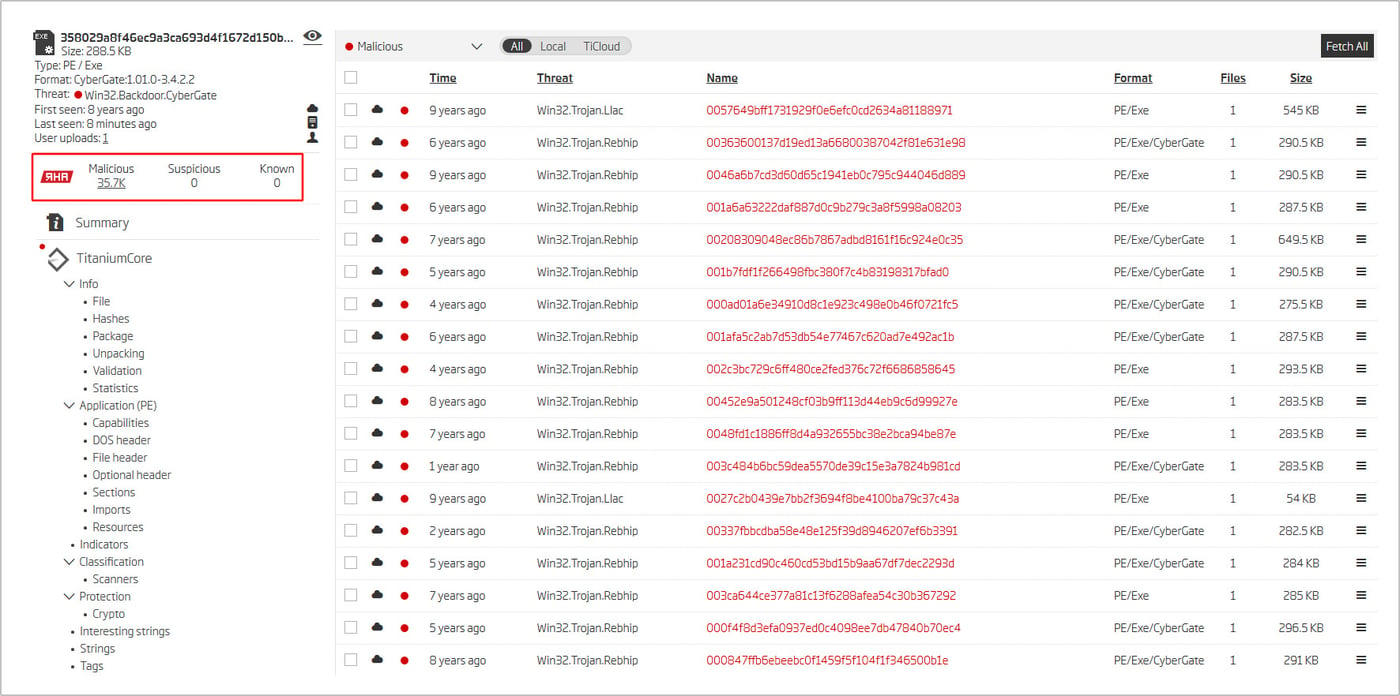
Figure 3: The RHA1 file similarity results returned for the sample with the suspicious version string
There are more than 35,000 malicious samples similar to the observed sample. Analyzing this bucket with the Titanium Platform revealed the existence of not only the 2.6 version, but other 2.x predecessors as well (specifically, 2.4 and 2.5).
Those samples have something else in common - the threat name ‘Rebhip’. We can use the Titanium Platform Advanced Search feature to find more files with the ‘Rebhip’ threat name. The goal is to find files similar enough to be classified as the same threat, but different enough to belong to a different RHA1 similarity bucket.
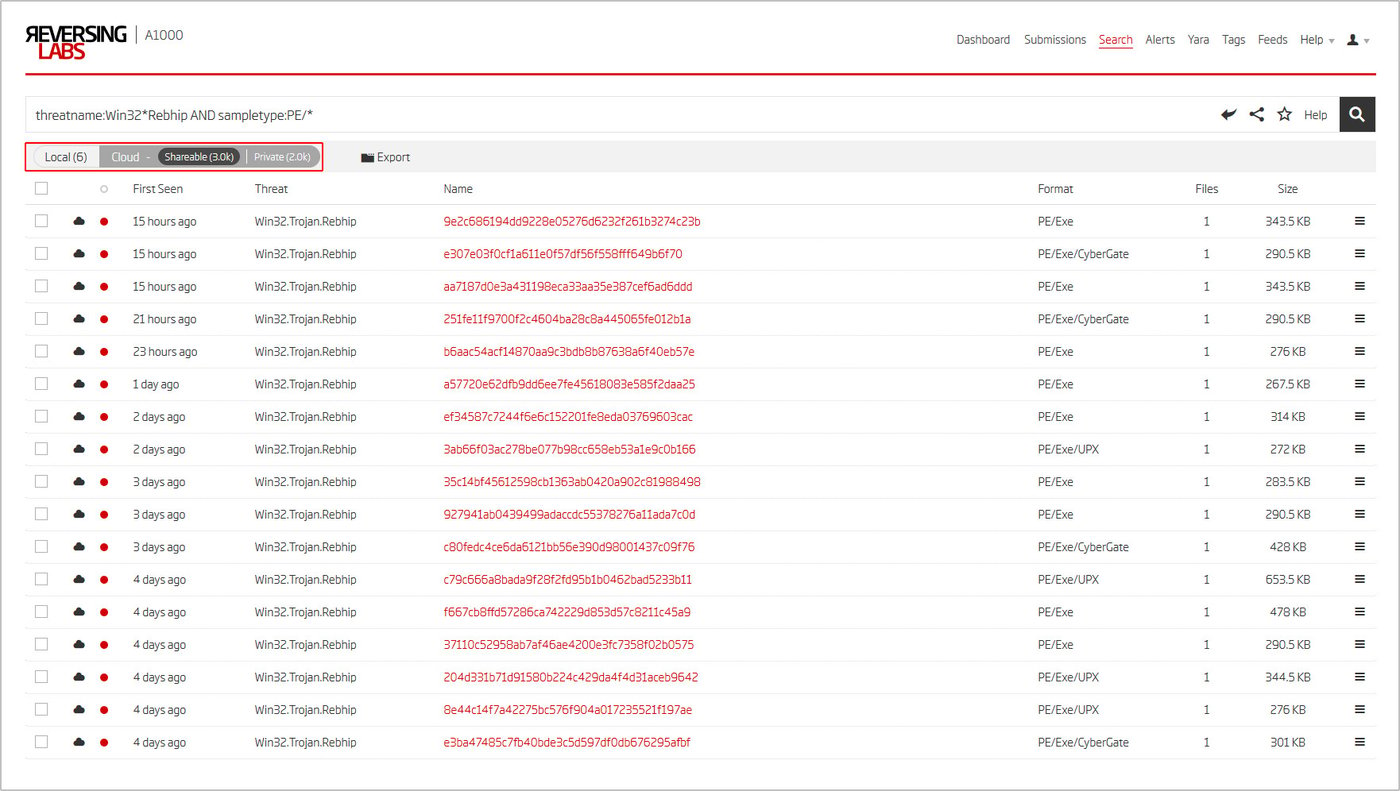
Figure 4: A1000 Advanced Search results for files with the ‘Rebhip’ threat name
The result looks promising, providing many additional samples. Among those samples, the Titanium Platform identified the majority as the previously seen CyberGate RAT. Furthermore, it identified yet another family - the Cerberus RAT.
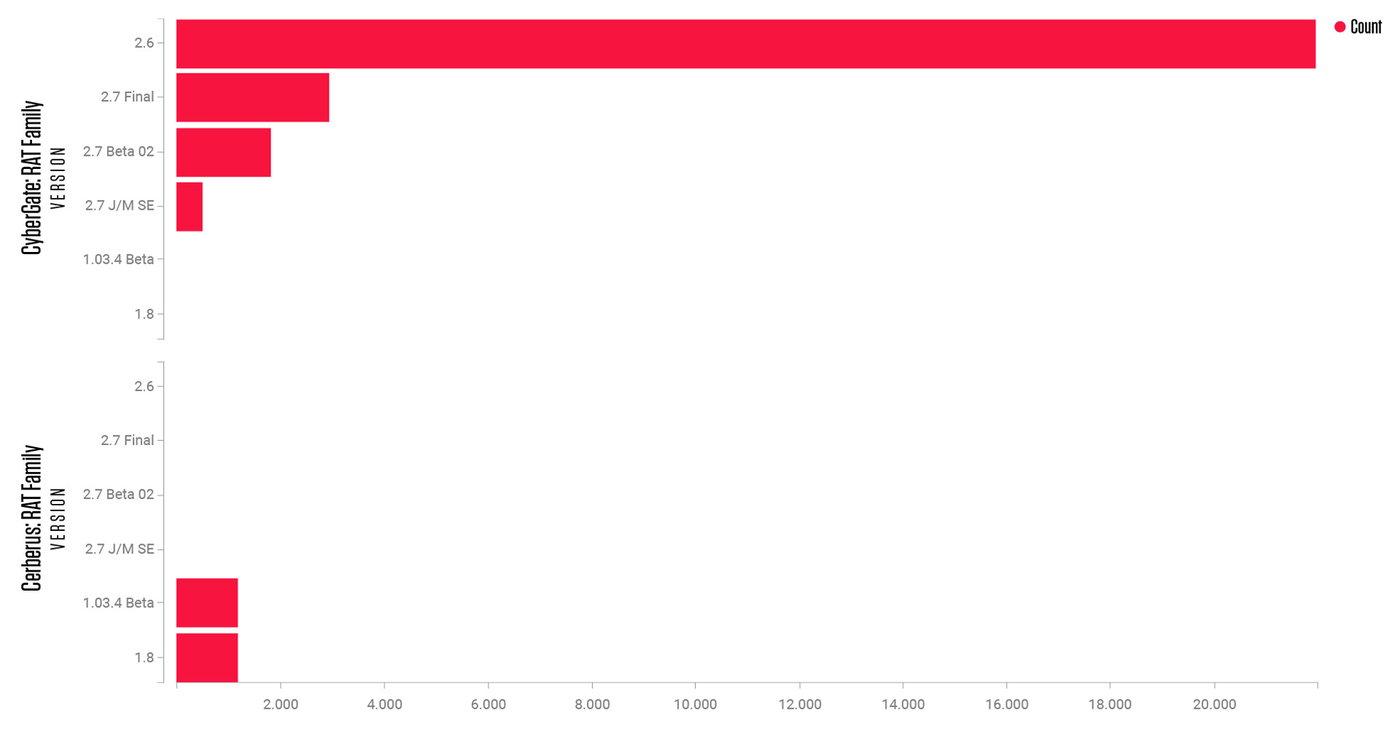
Figure 5: Samples with the ‘Rebhip’ threat name splitting into two families, CyberGate and Cerberus
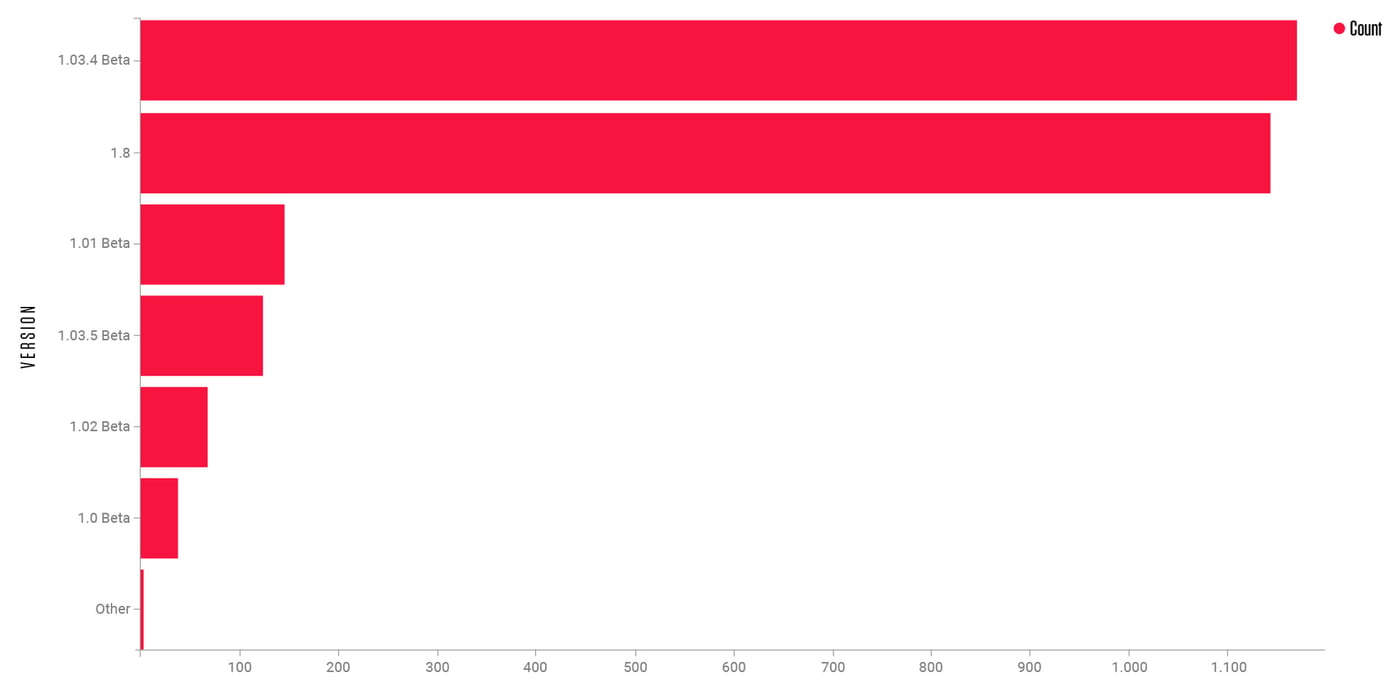
Figure 6: Cerberus samples by version
Among extracted Cerberus version strings, there seems to be one outlier. Version ‘1.8’ is making up nearly a half of the total shown in Figure 6. If we rinse and repeat what was done with CyberGate, the same SpyNet references would pop up in the same configuration fields.
This time something even better emerged. The PE resource storing the RAT configuration has a very helpful name - ‘SpyNet’. It seems that the SpyNet version 1.8 code was used as a base for the Cerberus RAT family, mirroring SpyNet 2.6 and CyberGate. Could it be that SpyNet is the ancestor of both these families, or does it go further? A deeper dive is needed to answer this inquiry, and gathering as many versions of SpyNet is the first step. The resource names of a PE file are searchable with the Advanced Search feature. If other versions of SpyNet store their configuration under the same name, then they are just a single query away.
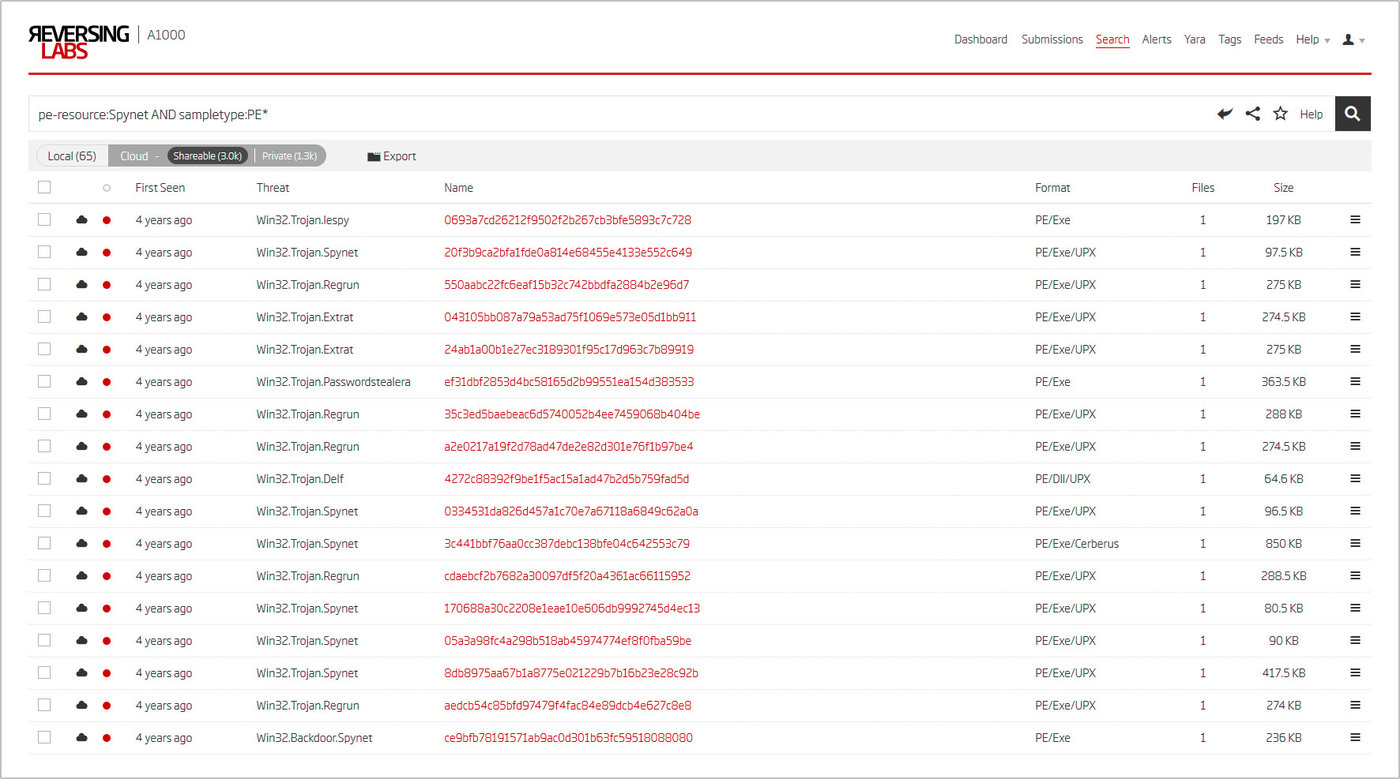
Figure 7: A1000 Advanced Search results for files with a ‘Spynet’ resource
Almost 30,000 samples are found. Some already received a Cerberus identification (the 1.8 version), while those unidentified share a relevant threat name - SpyNet. The threat name may again be used as an additional pivot point to go even further.
At this point, a lot of unidentified server samples have been uncovered, all linked to one of three known RAT families. They also share some other attributes. Worth pointing out is the unique timestamp identifying them as being compiled with one of a few specific Delphi versions, storing the configuration in a resource with one of a few distinct names, an almost identical configuration structure, and more. This shows how deep static analysis can go. We can get all this information without even taking a look at the actual code.
Finding the ‘SpyNet proper’ client would perhaps allow us to link all this together. The most straightforward thing to try is looking up files that reference SpyNet somewhere in the filename. Many of the SpyNet samples contain “spy-net” strings in their configuration, so that will be our keyword of choice. Openly distributed malware often gets passed around in archives, so searching for ZIP or RAR files could return results with additional metadata to work with.
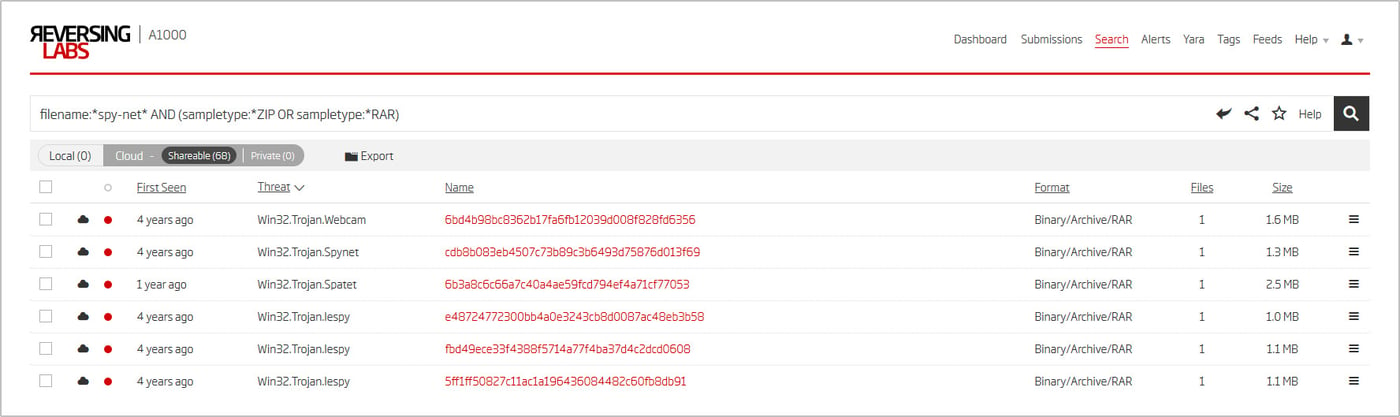
Figure 8: A1000 Advanced Search results for ZIP and RAR archives containing a ‘spy-net’ substring in their filenames
As shown, a few matches do exist. One of the files even has the SpyNet threat name. To see why limiting the search to archives was worthwhile, just look at the files the static analysis engine managed to extract.
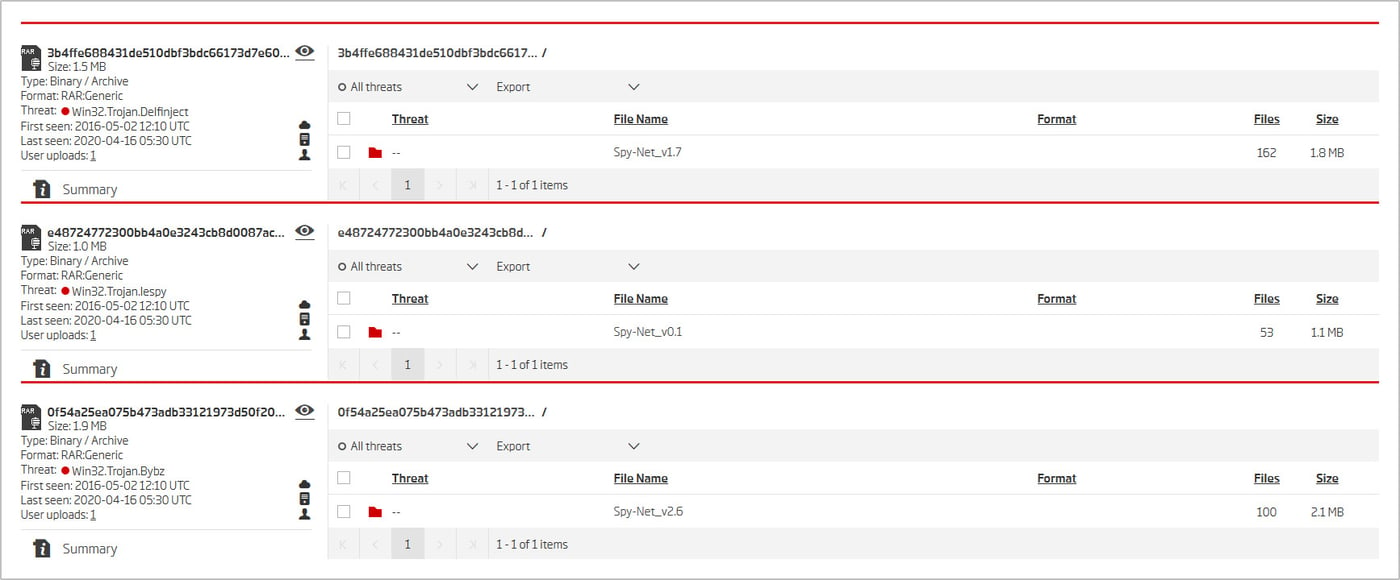
Figure 9: Contents of a few of the archives found through the query featured on Figure 8
A simple query returned a wide range of versions. One of the client executables found is already known - the 2.6 version. Embedded inside the PE resource section are various files, one of which gets identified as a CyberGate server sample. RAT client executables often embed a stub file that the configuration gets glued onto in the building process.
This goes in line with the SpyNet - Cybergate connection, but also gives a huge leverage point because of the location of the embedded file. The CyberGate executable is stored under the ‘Server’ resource. If any of the other client executables were to be inspected and a resource of a similar name found, it would very likely be that version's server file.
Finding as many versions of SpyNet is an exercise in Titanium Platform advanced search creativity. The static analysis report contains a plethora of information that can be used for pivoting. Here are just a few examples of possible advanced search queries:
(pe-resource:TFormNewServer AND pe-resource:Stub) OR
(pe-resource:Funcoes AND pe-resource:Server)
AND classification:malicious
email:[spynet-rat@hotmail.com, spynetcoder@gmail.com] AND classification:malicious
pe-resource-sha1:[ 843fc9feabab604b76ef0ced63737c478191cc27,
a6c0127ee3c18b11e88bd1ab99846de7334122bd] AND
classification:malicious
Queries search for files with relevant resource names, the author's e-mail addresses, and icons specific for SpyNet. The 0.x versions use a very distinct icon, while all other versions share a different one.
![]()
Figure 10: The two unique icons used by SpyNet for its C&C client executables
Multiple advanced search strategies do pay off, as the last two queries reveal the existence of SpyNet 3.x. This one is quite different from the rest. The client itself gets classified under the name Win32.Trojan.Xrat. XRAT is a known RAT family, but the connection is vague as it is undoubtedly written in C#, while both the client and server of SpyNet 3.1 are Delphi executables.
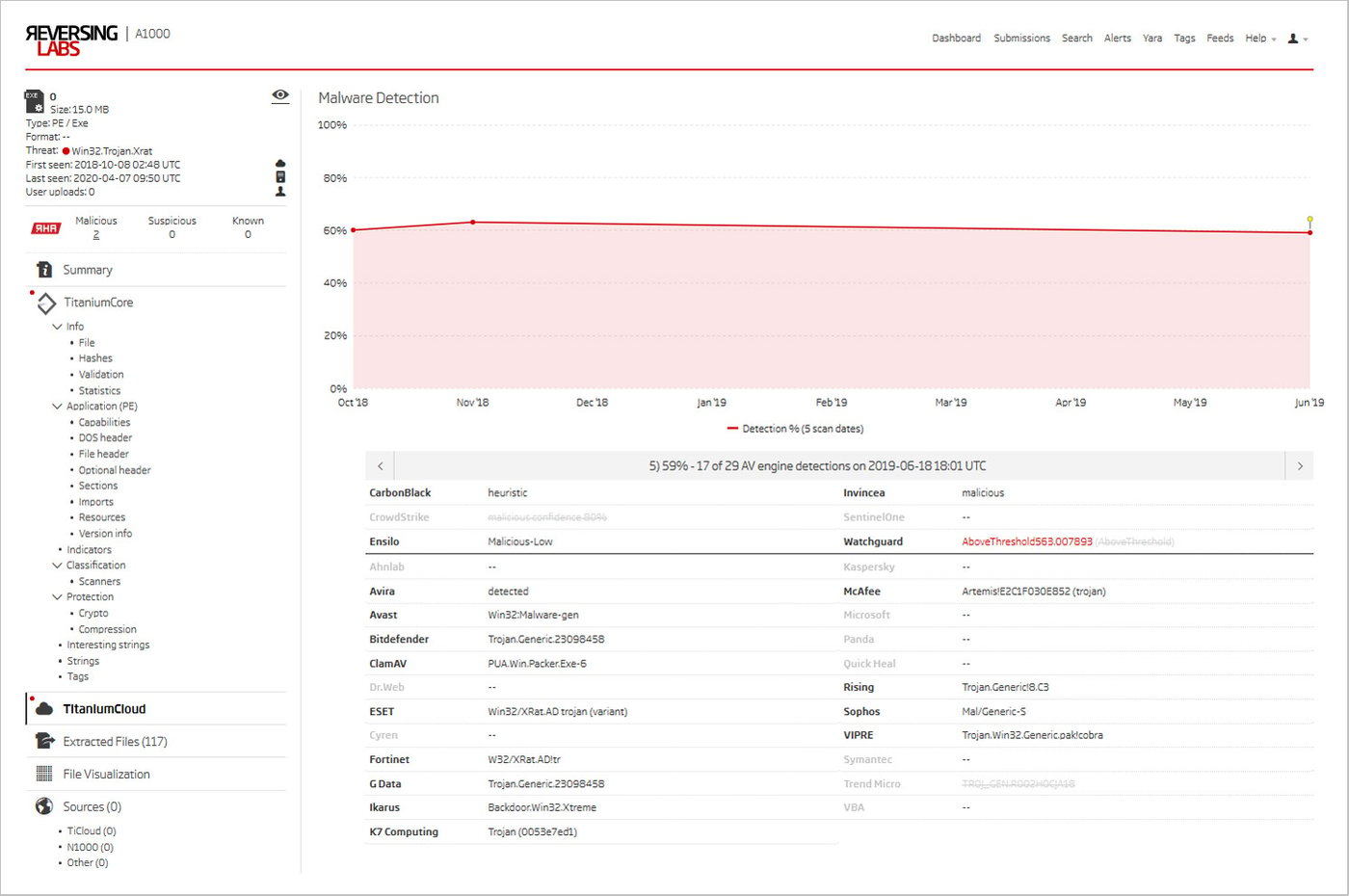
Figure 11: Recent TitaniumCloud AV engine detections for the SpyNet 3.1 C&C executable
Looking at some of the TitaniumCloud classifications shows that one of the malware detection engines, IKARUS, recognizes the newly found SpyNet 3.1 client executable as Backdoor.Win32.Xtreme. This is noteworthy because it is more specific than any of the other detections. It could be a reference to a family that better fits the bill - XtremeRAT.
The XtremeRAT executables are Delphi compiled. The servers store their configuration in a PE resource named “Xtreme”. The client follows almost analogously with the others, but the most striking similarity is that the author of the RAT is xtremecoder, a curious double to spynetcoder.
Further examination based on explained methods would confirm the relation between XtremeRAT and SpyNet. As is often the case with open-source malware, a number of clones exist. Some were deemed inconsequential and were not explored in detail, as they are not used to the same extent as their more famous relatives. For example, GreameRAT and JokerMask are in this category.
Finally, there are two blogs that confirm the relationship between the found families, exploring XtremeRAT and digital signatures. However, until now a detailed investigation has never been performed, nor the real ancestor discovered.
From ancestor to the era of rebrands
The next step in our research of detected families is a web search. It will shed some light on the similarities between the found families, and allow us to construct a basic timeline. Moreover, it will result in a historical analysis that reveals hacker collaboration, code rebranding, the authors' private information, and backdoored client samples. Let's unpack this web of intrigue.
With openly distributed malware, there is a good chance of finding plenty of information on public forums known to distribute it. Using only a search engine, one might come across a few interesting threads on the HackForums board. They date all the way back to October 2008, and promote early versions of SpyNet posted by the author himself.
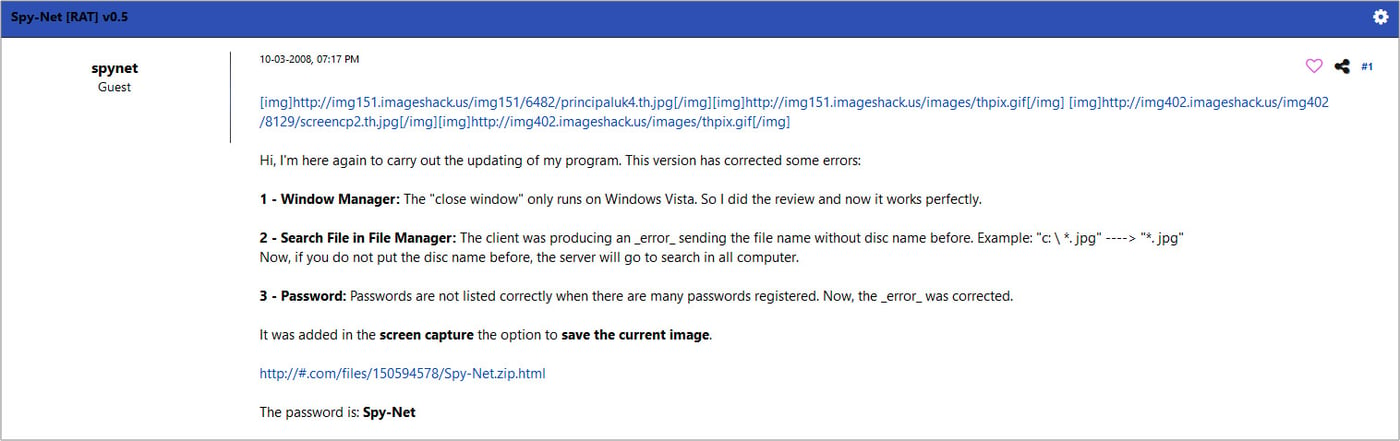
Figure 12: The original post on the HackForums board for the release of the 0.5 version of SpyNet
The author does not reveal much about himself, and rarely replies to posts. He is purely interested in sharing new versions of SpyNet. The contact addresses (used in our earlier queries) identified the author simply as spynetcoder. One of those SpyNet contact addresses has been compromised. The breach in question was one from June 2009 that included the HackForums board users. This spynetcoder didn’t include a lot of information in their profile. However, the creation time of the user profile and their geolocation were still revealed. The ‘spynet’ account was registered on September 25th 2009 in Brazil. It is presumed that the first SpyNet version was released around that time. The location makes sense because the default language in all the C&C executables is set to Portugese, while English wasn’t even supported until the 0.3 version. Some of the clients contain strings revealing the following:
C:\Users\[redacted]\Desktop\Spy-Net [RAT] 2 Sockets\Client\graphics32-1-8-3\GR32.pas
For earlier versions, no other “official” release seems to be conveniently available online. With the starting point now established, let’s look at the timestamps of the found samples and archives. Cross-checking the versions shows a complete match with the dates found on the release blog posts on HackForums. In general, the creation time of a file may not always match the official release, but in this particular case it seems to paint a complete picture.
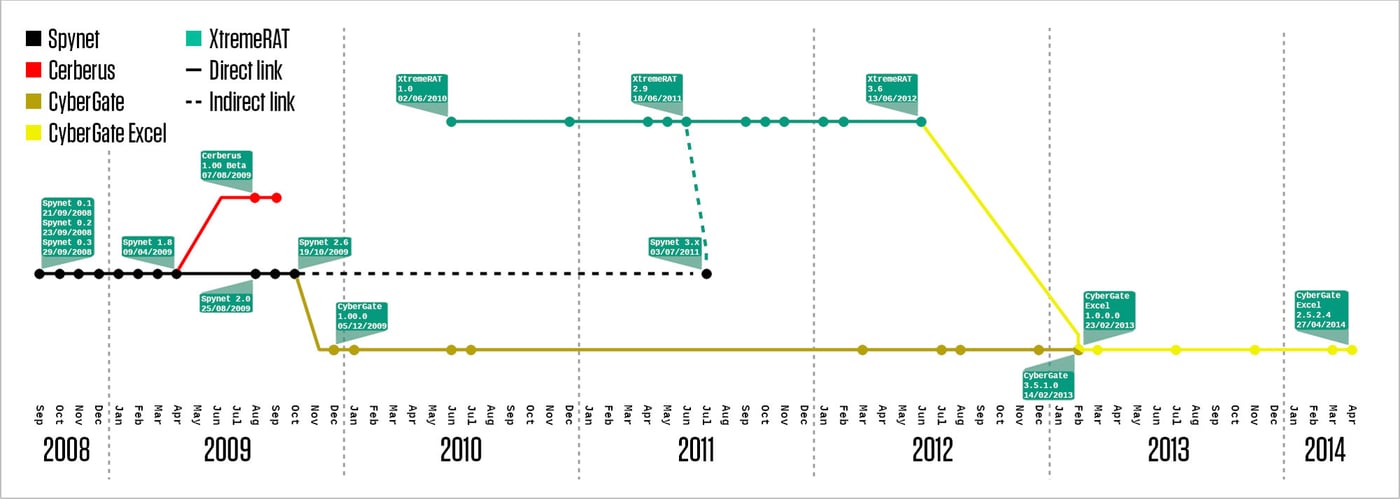
Figure 13: Release timeline and relationships for SpyNet and all related families. Dots indicated verified release dates, with the most notable ones annotated in more detail
SpyNet has been updated quite consistently since its first release. However, it didn’t gain much attention until early April 2009, when the 1.8 version was released. This version made some changes on the technical level, making it very similar to the Cerberus RAT. Just a quick look at the code makes it obvious that Cerberus was based on the SpyNet 1.8 code.
Cerberus was the creation of a trio frequently active on Hackhound.org - another hacker forum. The three in question are 2sly and Sam from the US and Steve10120 all the way from the UK. It was released sometime in the late half of 2009. Hackhound connects SpyNet and Cerberus due to the fact that SpyNet gives credit to members of Hackhound in its ‘special thanks’ section. Cerberus passed a few iterations, but without any significant changes, giving it a somewhat demeaning role of a SpyNet clone.
SpyNet 2.x development continued until October 2009 when the last public release became available. Only a few private 2.7 versions were introduced later. At this point, SpyNet and its coder disappear for a while. Just a few months later, in December, CyberGate takes the stage.
According to his biography, Viotto, the author of the Remcos RAT, worked as beta tester of SpyNet from version 1.8 onward. Afterwards, he became a beta tester for CyberGate.
“I became the official Spy-Net betatester, the RAT which widely replaced the use of older ones like Poison Ivy and Bifrost, from version 1.8 until the project's closure (2.7). After the end of Spy-Net project, with version 2.6 to be the last public released one, I become betatester of Cyber-Gate, RAT based on Spy-Net 2.7 source.”
CyberGate inherited the SpyNet 2.7 source code. Much like Cerberus, in the beginning it was nothing more than a clone. However, the case of Cybergate gets interesting very early on. The person responsible for its inception is jonhyK, previously known as one of the Cerberus RAT beta testers. The same HackForums leak mentioned earlier pinpoints jonhyK's location as Ontario, Canada. He would later be joined by others and turn what was Cyber-Sec.org, a kind of hobbyist community, into a brand known as cyber-software.org.
CyberGate very quickly became a commercial product that went through numerous versions over the course of years, still being active well into 2013. CyberGate was most definitely its own branch of SpyNet, and a lot of work went into it. The remote agent, however, stayed mostly unchanged, making detection somewhat trivial. CyberGate would later evolve into CyberGate Excel. A footnote also goes to GreameRAT (by Greyme-CoderSc from Morocco), a simple CyberGate clone which saw moderate usage.
While the SpyNet code traveled the globe, on June 2nd 2010 spynetcoder reentered the scene under a different alias - xtremecoder. The first version of XtremeRAT was released. Although this seems to be a complete rewrite, it undoubtedly follows the basic design of SpyNet. Most of the versions are still available through the Internet Archive on the XtremeRAT URL. The new RAT saw steady development all throughout the rest of 2010 and the middle of 2011, when version 2.9 was released. Afterwards, in late September of 2011, XtremeRAT 3.0 was introduced to the public. It was the last major iteration, which steadily upgraded until mid-2012 to the final 3.6 version.
During the development of XtremeRAT, the author went back to the SpyNet RAT and modernized the old code with the more sophisticated XtremeRAT features. This explains why versions 3.x are quite different from the earlier ones. The revamp was motivated by user requests.
“When [I] started this project, some users asked me to use better things from old Spy-Net and better things from Xtreme RAT and fix some little bugs. Now, users can control any remote computer with stability and no errors.”
The author continued the development through a few more versions before going back to the XtremeRAT. This finally marks the end of SpyNet development.
There have been accusations that some SpyNet executables have been backdoored. In fact, the version 3.1 client sample found on the official SpyNet blog reveals a potential threat. TitaniumPlatform extracted an AutoIt executable and unpacked a DarkComet remote agent that gets run upon execution of the SpyNet client.
As we mentioned before, CyberGate remained active for many years. At one point, the authors rebranded their product to CyberGate Excel. Not only was it a rebrand - it was marketed as a new product. CyberGate Excel is undeniably based on XtremeRAT code. The count for CyberGate Excel samples found in TitaniumCloud is far below those seen for the original, which is still used even today, suggesting that the last member of the CyberGate family didn’t quite live up to its heritage.
Today's presence of CyberGate and its relatives was noticed during our research of RAT configurations. The research revealed their surprisingly high usage (considering their age), and warned us to stay alert for threats that were first seen years ago. We published our findings in the blog post introduced at the beginning of this adventure. Let's end it with an illustration of SpyNet legacy through the last couple of years.
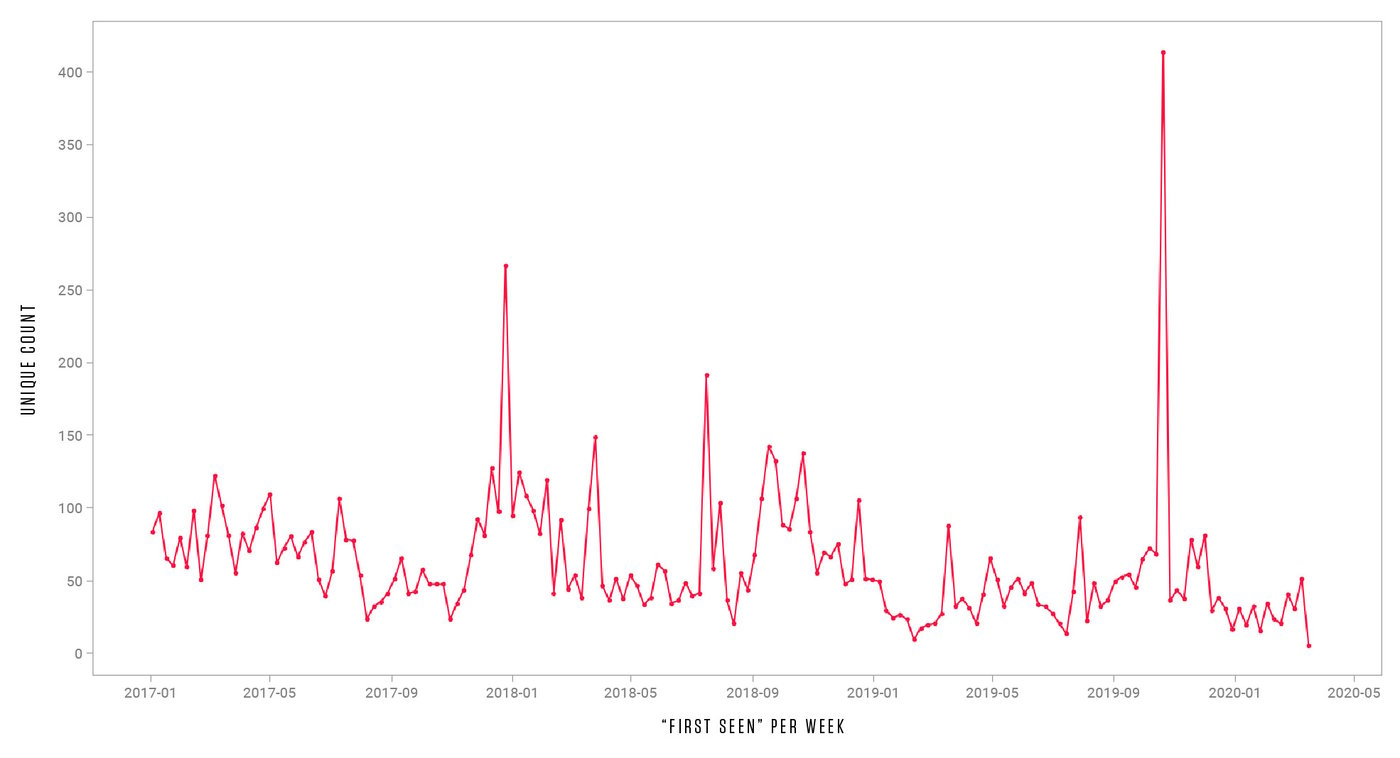
Figure 14: Appearances of SpyNet, and related families, in the last couple of years
Conclusion
Identifying SpyNet as the ancestor was the root of this research. The ancestor is often the base for multiple malware families, and holds the key to their detection. TitaniumPlatform detects SpyNet successfully, correspondingly handling rebrands and originals.
Some of the rebrands evolve, adding sophisticated features through their development. Titanium Platform has proven to be a perfect choice for detection of evolved malware that holds similarities and attributes across different versions. Its power lies in the multitude of extracted data, which can be crucial in the identification process.
IOC list
The following link contains the data extracted from samples of one of the discussed families, mostly limited to those seen in the last 31 days. The IOCs are sorted by first appearance in the TitaniumCloud.
Additional RAT blogs of interest:
Keep learning
- Read the 2025 Gartner® Market Guide to Software Supply Chain Security for software engineering and security leaders. Plus: Join RL's May 28 webinar for expert insights.
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.







