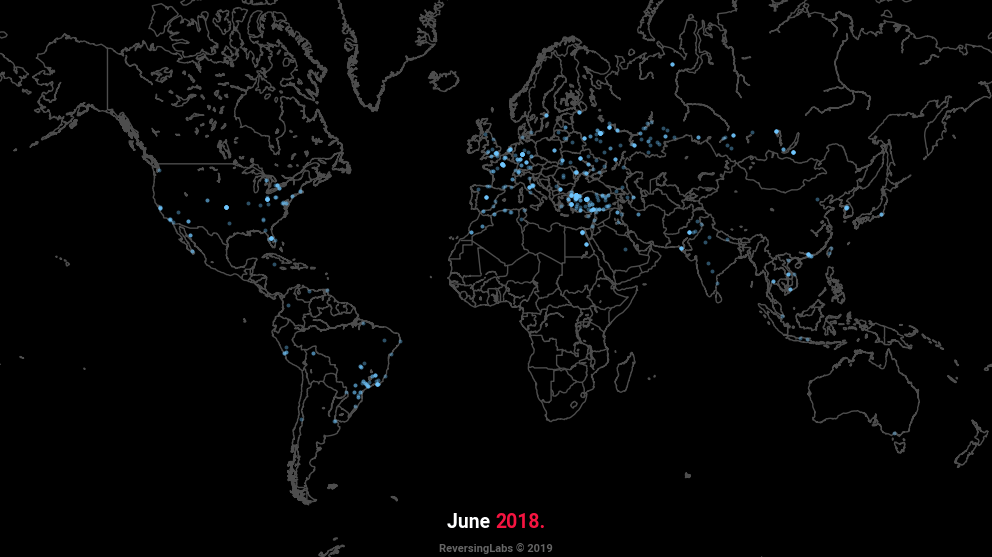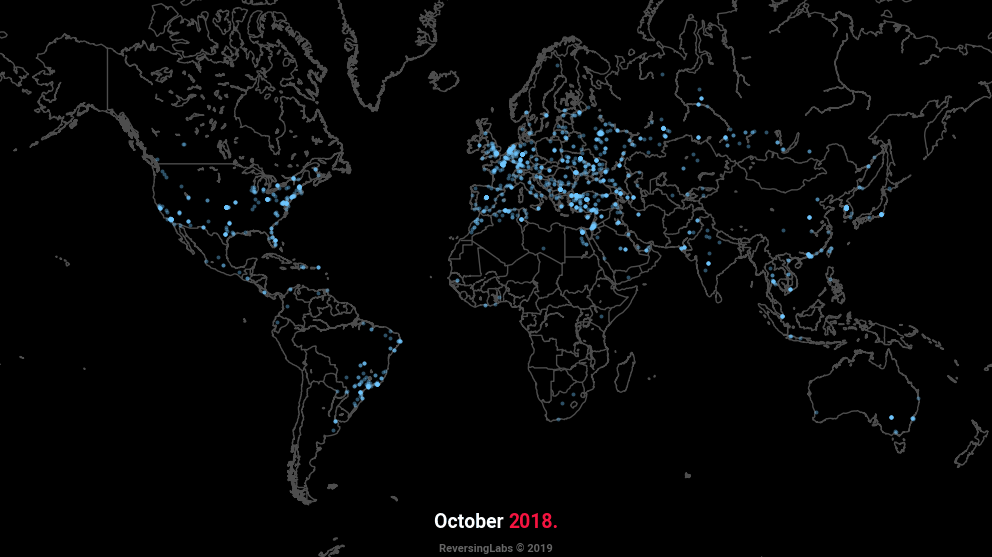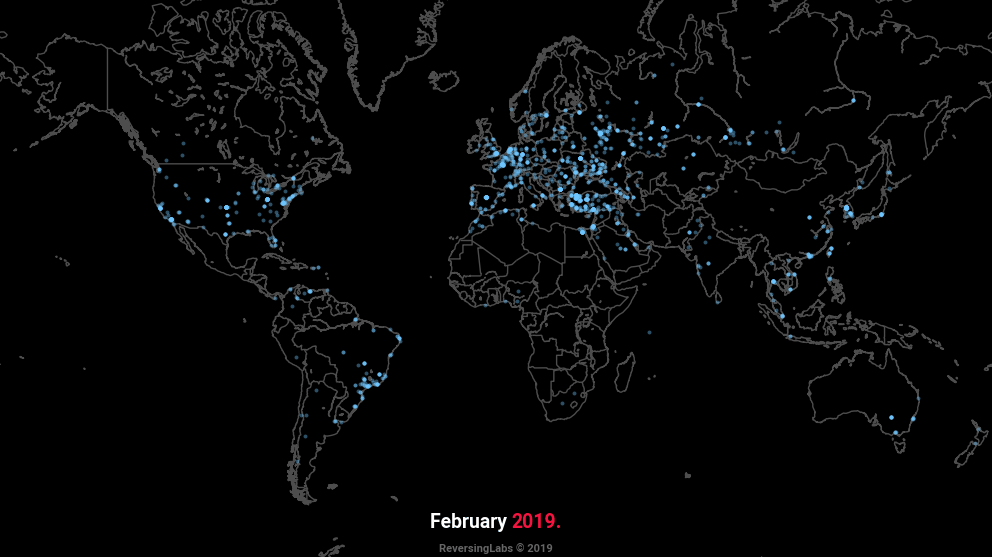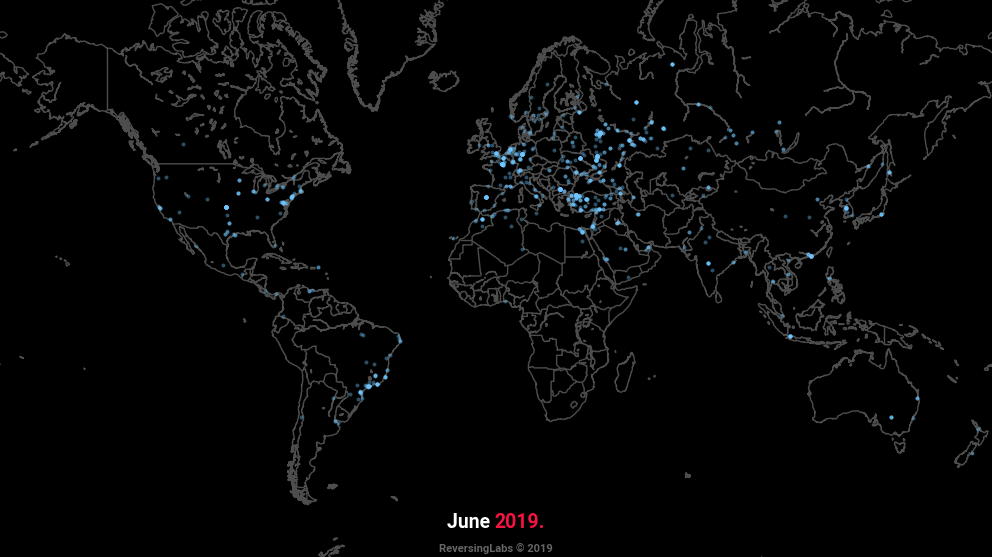
Geographical location of C2 servers in the past year
In their attack campaigns, malicious actors and APT groups often utilize commonly available malware configured for their use and control. Such configurations usually contain Command and Control (C2) servers, passwords used for communication with those servers, campaign identifiers, mutexes, installation locations, and more.
Exploring different malware configurations, e.g. host geolocation and DNS preferences, gives us insight into the inner workings and trends set by the malicious actors and groups. The wealth of malware we collect allows for correlating the data from different samples and recognizing emerging actors and campaigns. With the rising trends of advanced attacks and government-backed APT groups, this becomes essential for recognizing coordinated efforts and providing comprehensive threat intelligence.
The ReversingLabs Titanium Platform supports configuration extraction from over 40 different RATs, Backdoors, Keyloggers, Downloaders, Ransomware and POS malware. We collect and analyze over 2,000 of such unique samples per day. In this blogpost, we will present a brief breakdown of their configurations.
As shown in the chart below, these malware samples are mostly Remote Administration Tools (RATs) with the exception of one Keylogger - iStealer. RATs offer attackers a wide range of powerful tools such as remote desktop access, keylogging features, file system and webcam access, all of which are often available to the attacker through a convenient GUI.
Their effectiveness and simplicity of use propelled them in popularity with DarkComet at the forefront. DarkComet is a feature-rich, easy-to-deploy RAT created by a French developer Jean-Pierre Lesueur. It was previously distributed for free through the official website, which contributed to its worldwide usage.
Unique samples per malware family
Remote Administration Tools and Keyloggers pose a serious threat to individuals as well as organizations, since they are likely to steal and tamper with sensitive information. They have been repeatedly used in attacks targeting government organizations and spear phishing campaigns on private companies. New threats are developed and discovered every day, which is why ReversingLabs reinforces its more conventional classification methods with Machine Learning (ML) classification based on industry-leading static file analysis, targeted specifically at Remote Administration Tools, Keyloggers, and Ransomware.
Furthermore, malicious actors often try to avoid detection by packing malicious executables in order to hide malicious code and evade traditional signature-based detections. This is achieved by encrypting and/or compressing original code so that it only becomes readable once the binary is executed. To combat this, the ReversingLabs static analysis engine unpacks more than 400 different file formats and performs steganographic detection and extraction of embedded files. Since this is done statically - without ever executing the file - it is a safe, fast, and reliable method that enables us to process files in milliseconds and even perform recursive unpacking, potentially defeating multiple layers of encryption.
This kind of approach allows us to detect and extract configuration from off-the-shelf malware, as those are likely to appear packed and obfuscated because they are easily detectable otherwise. In fact, only 14% of the samples we analyzed in this breakdown appeared as unobfuscated standalone malware, with the most popular first layer of detection evasion being the UPX (Ultimate Packer for Executables) executable packer.
Once all the layers have been beaten, we can dive deeper into the malware configuration to examine installation locations, startup keys, passwords, mutexes, C2 domains and IP addresses, which we can geolocate and use to determine likely origins of attacks.
C2 servers per country
The animation at the beginning of this text plots the geographical locations of C2 servers encountered in the past year, and is indicative of the widespread popularity of aforementioned types of malware. Whilst Turkey remains the most popular point of origin for malicious servers, in recent months we’ve observed a significant increase in those originating from Russia. Dynamic DNS (DDNS) services remain the most frequent choice when it comes to addressing, with tunneling services becoming increasingly popular.
Geolocation data was obtained using MaxMind’s GeoLite2 database. According to the database, most C2 servers are located in Turkey, the United States, and Russia, with the latter seeing a significant increase in recent months, as shown.
Normalized number of C2 servers in the USA and Russia
DDNS services are heavily utilized to resolve IP addresses of Command and Control servers due to the fact that the attacker can change the IP address to which a DNS record points frequently and on-the-fly. This means that if one C2 server gets taken down, the attacker can quickly update the DNS record to point to a new server, thus restoring connections to the infected clients. Most commonly abused DDNS service providers are duckdns.org and no-ip.com, with duckdns.org being especially popular in Turkey.
C2 servers addressing
Another commonly observed addressing method uses services such as ngrok.com and portmap.io, which allow users to expose local servers through VPN tunnels. This approach is used in an attempt to hide a malicious actor’s true location and identity, and to make it more difficult to file an effective abuse report to the hosting provider.
The most abused hosting providers are listed in the following table.
| Hosting provider/ISP | Country | C2 servers |
| Turk Telekom | Turkey | 1,281 |
| Rostelecom | Russia | 514 |
| Tellcom Iletisim Hizmetleri A.s. | Turkey | 292 |
| JSC ER-Telecom Holding | Russia | 186 |
| Comcast Cable Communications, LLC | United States | 159 |
| Vodafone Net Iletisim Hizmetleri Anonim Sirketi | Turkey | 148 |
| TELEFÔNICA BRASIL S.A | Brazil | 128 |
| Free SAS | France | 122 |
| PVimpelCom | Russia | 117 |
| Ielo-liazo Deploiement Fibre | France | 115 |
| Telecom Algeria | Algeria | 107 |
| TE-AS | Egypt | 104 |
| OVH SAS | France | 97 |
| Orange | France | 95 |
| PJSC Ukrtelecom | Ukraine | 94 |
| Deutsche Telekom AG | Germany | 93 |
| CLARO S.A. | Brazil | 87 |
| MTS PJSC | Russia | 87 |
| Charter Communications Inc | United States | 84 |
| Turksat Uydu Haberlesme ve Kablo TV Isletme A.S. | Turkey | 83 |
| SFR SA | France | 82 |
| Amazon.com, Inc. | United States | 79 |
| Kyivstar PJSC | Ukraine | 72 |
| Telecom Italia | Italy | 63 |
| Telemar Norte Leste S.A. | Brazil | 63 |
| MT-MPLS | Morocco | 61 |
| AT&T Services, Inc. | United States | 60 |
| Korea Telecom | South Korea | 60 |
| DigitalOcean, LLC | United States | 36 |
| Liberty Global B.V. | Germany | 24 |
Extraction and collection of passwords, campaign identifiers, and mutexes make it possible for us to detect malicious campaigns and correlate data between a number of different malware used in the same campaign. Malicious actors often reuse the same passwords throughout campaigns, which makes passwords a sensible datapoint to focus on. Additionally, well-executed campaigns may deploy mutexes with the same name to ensure only one running malware instance.
Examples of encountered RAT samples that use the same passwords
As an example, we’ll look at malicious samples using the password “crocro35” that have been encountered over several months. All of them were either CyberGate or Xena Remote Administration Tools. As the password would suggest, the attack originated from Croatia, but C2 servers have since been shut down. Malicious files were most likely distributed by email, since they were disguised to look like email attachments. Most of them were custom-crafted .Net files with either WinRAR or Gmail icons meant to trick the user into opening them. After the file was opened, it would indeed display a funny JPEG picture, but the RAT would be launched in the background.
The ReversingLabs Titanium Platform seamlessly extracted the CyberGate RAT that was embedded in the .Net executable using steganographic detection. Other files used in the campaign were also disguised to look like WinRAR archives or installers, but they used UPX and CigiCigi executable packers. They were also statically unpacked, which enabled RAT detection and configuration extraction to take place automatically.
The following domains were used in the campaign:
- haso.ddns.net
- mujo.ddns.net
- koko35.ddns.net
- vulin.ddns.net
- brobro55.ddns.net
- etotako.ddns.net
- manipulacija.ddns.net
All of the configuration data used in this breakdown is available to our customers via our File Reputation Service, TitaniumCloud, through the exposed malware feeds. These feeds produce this kind of data in real time, as new malicious samples are encountered in the wild. The information from the feeds can be used to proactively block and monitor corporate networks for connections to the malicious IPs and domains, as well as to employ per-file blocking strategies by blacklisting malicious hashes. These methods fortify your defenses against emerging threats through threat hunting actions, and provide an efficient way to neutralize and reconstruct an attack in post-breach forensic analysis situations.
Keep learning
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








