
Go Beyond the SBOM
The Most Comprehensive SBOM and Risk Assessment
Identify Malware, Tampering, Suspicious Behavior, and More in Any Application
While a Software Bill of Materials (SBOM) is a foundational first step toward building security transparency between enterprise software producers and buyers, it is merely a list of ingredients—more coverage and context to how internal software components map to software deployment risks is necessary.
To make tangible steps toward securing the software supply chain, organizations need to have actionable security assessments that identify immediate software risks and enable steps to mitigate them, while addressing ML, services, and cryptographic elements.
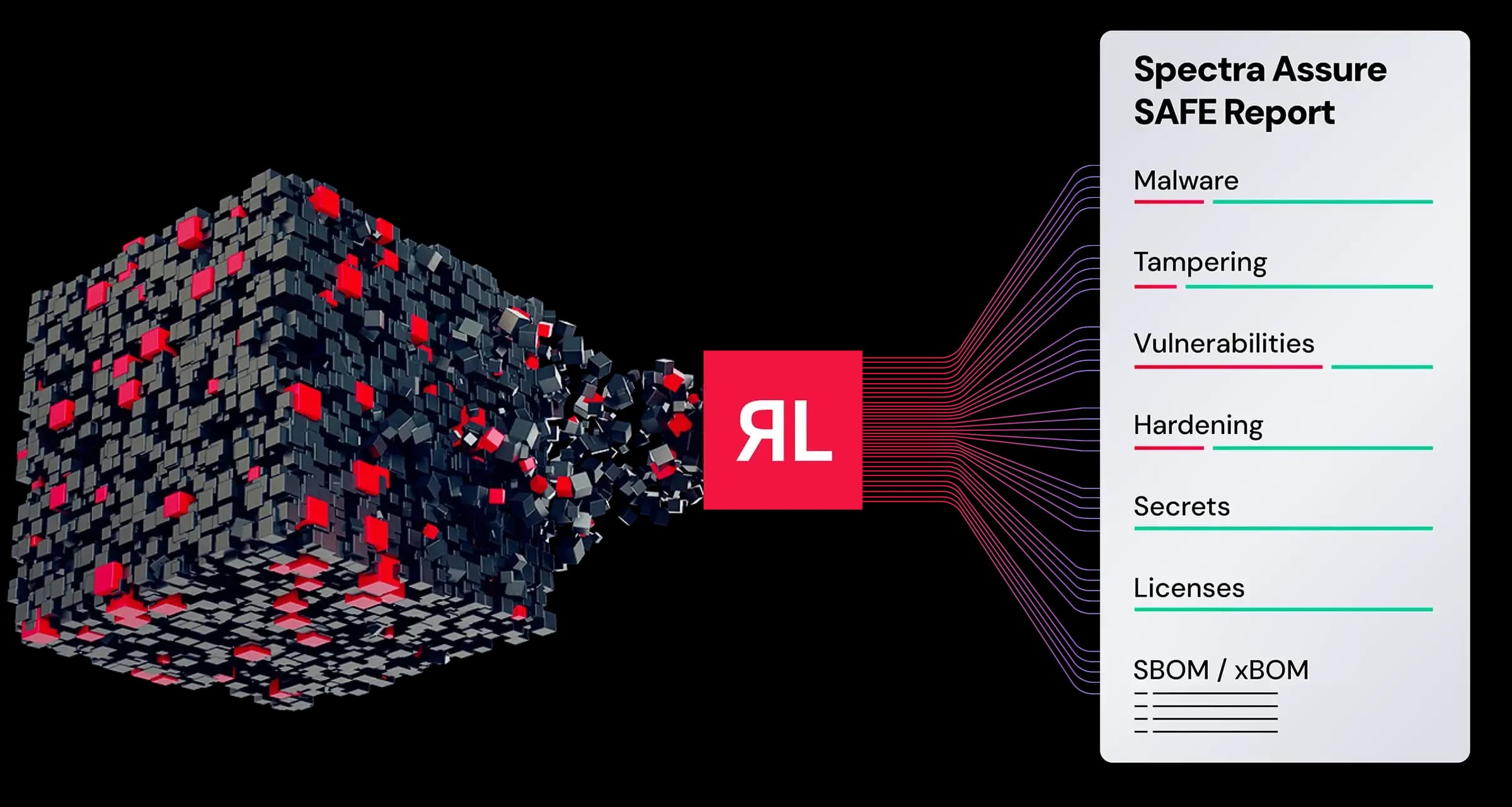
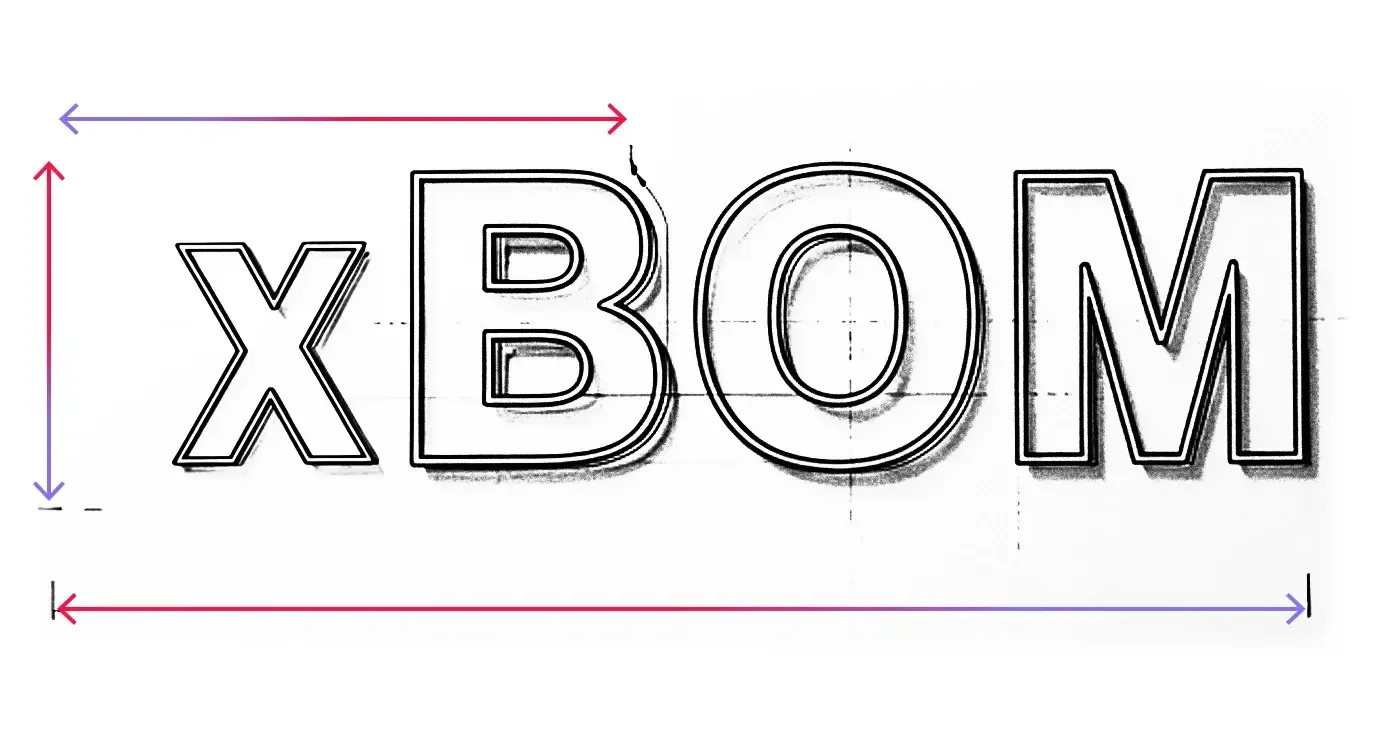
The Spectra Assure® SAFE Report goes beyond the scope of traditional SBOMs by generating more than a simple ingredient list. It provides a comprehensive and actionable analysis of first-, second-, and third-party components, including build artifacts, and maps them to embedded critical risk categories like embedded malware, code tampering, exposed secrets, and more. In addition to providing the most comprehensive SBOM in both CycloneDX and SPDX format, it has broad xBOM capabilities for ML-BOM, CBOM, and SaaSBOM.
The SAFE report raises the bar in software supply chain transparency for software producers, buyers, and regulators. It can be securely and privately shared to remove barriers, build transparency, and collaborate to address critical security fixes.

The SAFE report provides a summary of the key software safety concerns critical to AppSec, TPRM, and cyber-risk professionals. It provides a summary of all findings and buckets them across six risk categories - malware, tampering, secrets, hardening, vulnerabilities, and licenses. This helps identify, prioritize, and mitigate issues based on the category they belong to.

CycloneDX defines several xBOM capabilities that facilitate transparency between software vendors and software buyers beyond the scope of the SBOM. Spectra Assure provides visibility into cryptographic elements, ML and AI models, and services with the ability to generate CBOM, ML-BOM, and SaaSBOM from fully compiled software so you can prepare for AI and quantum computing threats.
The SAFE report enables transparency between software vendors and buyers by aggregating analysis results into digestible software risk Levels, and by providing a bi-directional view of findings through a shareable link that is:

The ML-BOM, which can be generated from compiled software, will identify and document all machine learning models, datasets, and configurations within your software. Software producers can also declare these components, facilitating transparency in and accelerating software transactions. This is especially important because serialized ML models can harbor malware and other threats.

Address the challenge of hidden software service risks with the SaaSBOM, which details all software services, APIs, and data flows within your software. This advanced visibility uncovers dependencies, service endpoints, and data classifications, as well as reliance on other services, empowering organizations to reduce exposure, strengthen compliance, and ensure safer adoption of distributed, service-driven applications.
Address hidden cryptographic risks with the CBOM, which inventories all algorithms, keys, certificates, and protocols in your software. This detailed visibility helps organizations identify weak or outdated cryptography, prepare for quantum computing threats, and ensure compliance with evolving standards, empowering proactive risk management and safeguarding sensitive data across the entire software supply chain.

Policy criteria within the SAFE report can be customized to align with internal controls. Businesses can also meet compliance mandates by generating SBOMs in either the CycloneDX or SPDX templates. This helps satisfy government regulations and guidance such as:



Binary analysis is a must-have control for securing third-party software, before installation.

How Sophisticated Malware, AI, and Broken Trust are Reshaping Software Security
Inside the Next Generation of SBOMs