 The software supply chain has never been more complex — or more critical to secure. For years, the Software Bill of Materials (SBOM) has been the go-to tool for documenting components within software, offering much-needed visibility into what’s under the hood. It is called out by Executive Order 14028, as well as the EU Digital Operational Resilience Act (DORA) and EU Cyber Resilience Act (CRA). But as software systems grow to include machine learning models, cloud services, cryptographic risks, hardware dependencies, and low-code platforms, the traditional SBOM simply isn’t enough.
The software supply chain has never been more complex — or more critical to secure. For years, the Software Bill of Materials (SBOM) has been the go-to tool for documenting components within software, offering much-needed visibility into what’s under the hood. It is called out by Executive Order 14028, as well as the EU Digital Operational Resilience Act (DORA) and EU Cyber Resilience Act (CRA). But as software systems grow to include machine learning models, cloud services, cryptographic risks, hardware dependencies, and low-code platforms, the traditional SBOM simply isn’t enough.
The SBOM has been fully supported by the OWASP Foundation’s CycloneDx, an industry-recognized standard for machine-readable SBOMs. And in 2023, CycloneDx introduced the Extended Bill of Materials (xBOM) to address the full stack bill of materials, adding 11 other bills of materials (BOMs) for areas that span software as a service, cryptography, hardware, manufacturing and other technology ecosystems. In its most current form, CycloneDX v1.6 was ratified as an Ecma International standard, providing a global xBOM specification for use across multiple domains.
Here's what you need to know about the SBOM’s purpose, what the xBOM entails — and how RL Spectra Assure now provides the most comprehensive support for the xBOM.
[ Get the White Paper: Go Beyond the SBOM. And see the Webinar, Welcome CycloneDX xBOM ]
Understand the SBOM
For both software producers and their enterprise buyers, SBOMs are an essential first step in upholding software supply chain security. They provide a comprehensive list of all of the ingredients that make up a software product, much like how the U.S. Food and Drug Administration’s mandated black-and-white nutrition label informs shoppers of the ingredients that make up the food and beverages they purchase. As with food labels, SBOMs provide a level of transparency about what exactly is in a piece of software for those building or buying commercial software applications, services, hardware and so on.
 SBOMs follow one of two main file formats: SPDX or CycloneDX. Regardless of the SBOM format, the files typically contain these key elements:
SBOMs follow one of two main file formats: SPDX or CycloneDX. Regardless of the SBOM format, the files typically contain these key elements:
- Product/Component Name: Designation typically defined by the original publisher.
- Publisher Name: The name of an entity that creates, defines, and identifies components.
- Product/Component Version: Identifier used by the supplier to specify a change in software from a previously identified version.
- File Name: Serves as an additional identifier within a larger package of software.
- Software License: Indicates how open-source components can be used, modified and/or shared.
- Dependencies: Identifies other sub-components that are included within the component.
Understand the xBOM
The xBOM is a full-stack BOM standard that provides advanced supply chain capabilities for cyber risk reduction, and includes 12 different BOMs spanning the software and hardware ecosystems. The xBOM builds upon the traditional elements of an SBOM to provide a more comprehensive view by including a broader range of components and information related to software-based products.
| Acronym | Name | Focus |
| SBOM | Software Bill of Materials | Software |
| SaaSBOM | Software as a Service Bill of Materials | Software |
| CBOM | Cryptography Bill of Materials | Software |
| ML-BOM | Machine Learning Bill of Materials | Software |
| BOV | Bill of Vulnerabilities | Software |
| VDR | Vulnerability Disclosure Report | Software |
| VEX | Vulnerability Exploitability eXchange | Software |
| CRNF | Common Release Notes Format | Software |
| CDXA | CycloneDX Attestations | Software |
| HBOM | Hardware Bill of Materials | Hardware |
| OBOM | Operation Bill of Materials | Operations |
| MBOM | Manufacturing Bill of Materials | Software |
The 12 BOMs included in CycloneDX xBOM.
SBOM (Software Bill of Materials)
An SBOM is a complete, machine-readable inventory of software components, including metadata, dependencies, and licenses, providing transparency across the software supply chain.
SaaSBOM (Software as a Service Bill of Materials)
SaaSBOM identifies and inventories cloud-based applications, APIs, endpoints, and data flows to help ensure governance, compliance, and risk mitigation in SaaS environments.
CBOM (Cryptography Bill of Materials)
A CBOM lists cryptographic assets such as keys, algorithms, and libraries to evaluate crypto agility, policy compliance, and potential vulnerabilities in cryptographic implementations.
ML-BOM (Machine Learning Bill of Materials)
ML-BOM provides transparency into machine learning systems by documenting models, datasets, parameters, training processes, and dependencies – enabling better governance and trust in AI development.
BOV (Bill of Vulnerabilities)
BOV enables structured sharing of vulnerability data affecting software components, supporting automated analysis, coordination, and remediation across the software ecosystem and threat intelligence systems.
VDR (Vulnerability Disclosure Report)
The Vulnerability Disclosure Report (VDR) standardizes how known vulnerabilities are communicated, enhancing collaboration between suppliers, researchers, and consumers during coordinated vulnerability disclosure processes.
VEX (Vulnerability Exploitability eXchange)
VEX communicates the exploitability of a vulnerability in a specific context, helping organizations prioritize remediation based on actual exposure, not just CVE presence.
CRNF (Common Release Notes Format)
This format standardizes software release notes, allowing automated systems to interpret changes, improvements, and fixes in a structured, machine-readable and developer-friendly format.
CDXA (CycloneDX Attestations)
CDXA provides cryptographically verifiable, machine-readable proof of build integrity, policy compliance, and artifact provenance to support secure software development and delivery.
HBOM (Hardware Bill of Materials)
HBOM inventories hardware components, firmware, and associated metadata, ensuring security, compliance, and lifecycle management of embedded systems and connected IoT hardware devices. Items are related to, but not contained within software.
OBOM (Operation Bill of Materials)
OBOM captures operational configurations, environments, and runtime dependencies that impact system behavior, helping to manage post-deployment risk and ensuring secure and consistent software execution. Items are related to, but not contained within software.
MBOM (Manufacturing Bill of Materials)
MBOM outlines the manufacturing and assembly details of software, services, and hardware to ensure traceability, quality assurance, and regulatory compliance throughout the production process. Items are related to, but not contained within software.
xBOM Support with Spectra Assure
ReversingLabs is supporting the CycloneDx xBOM standard to bring more visibility and security to software supply chains for both software producers and their enterprise buyers. RL Spectra Assure already provides the most comprehensive SBOM, but now extends its CycloneDx 1.6 support with coverage for the SaaSBOM, ML-BOM, and CBOM – all in one click.
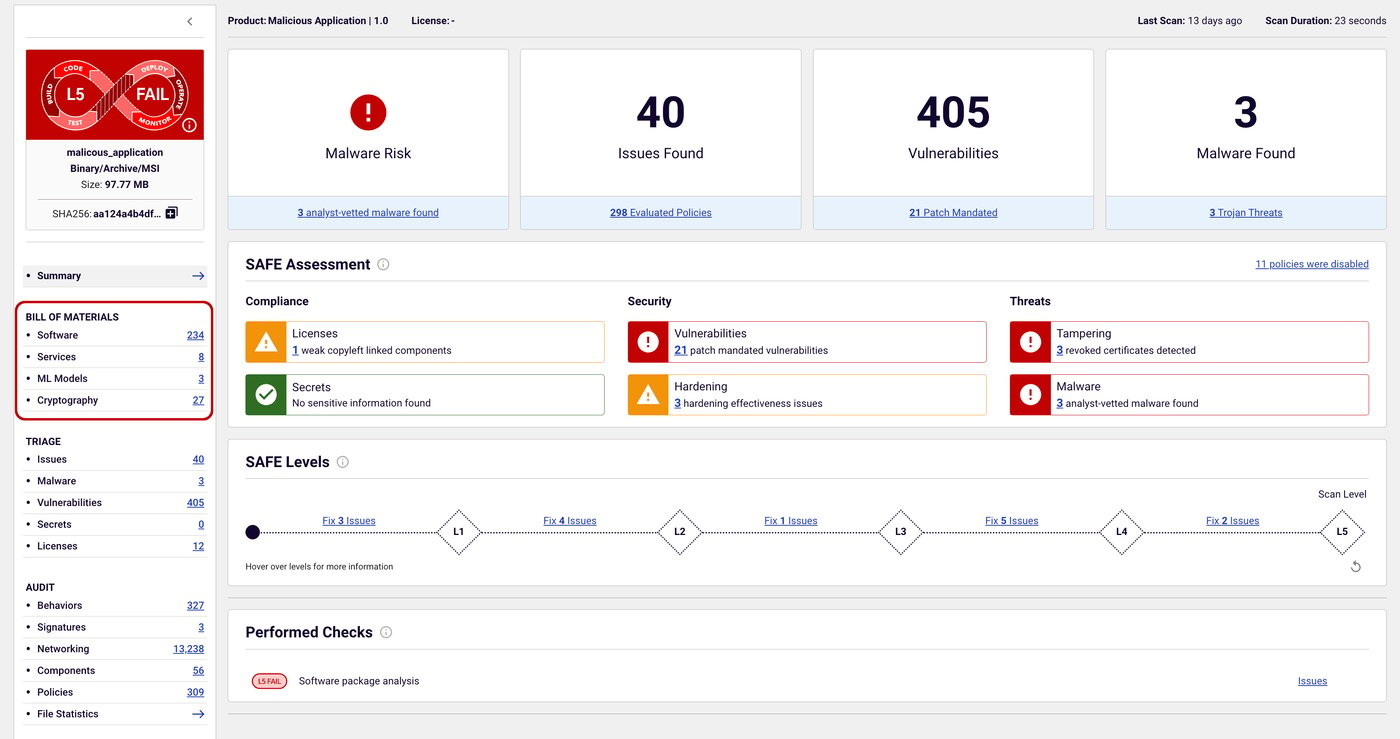
Figure 1: Spectra Assure provides easy access to all Bill of Materials in the left nav.
Here’s a breakdown of each of these new BOMs, and why they are essential for enterprise software supply chain security:
The SaaSBOM
Spectra Assure support for the SaaSBOM provides a better insight into the dynamic relationships between the services the software integrates with. It allows organizations to check the level of security of those third-party services, as well as identify and more effectively manage risks regarding insecure APIs, vulnerable data exchanges, and misconfigured services. As a result, users can confidently make more informed decisions on what they include in their applications.
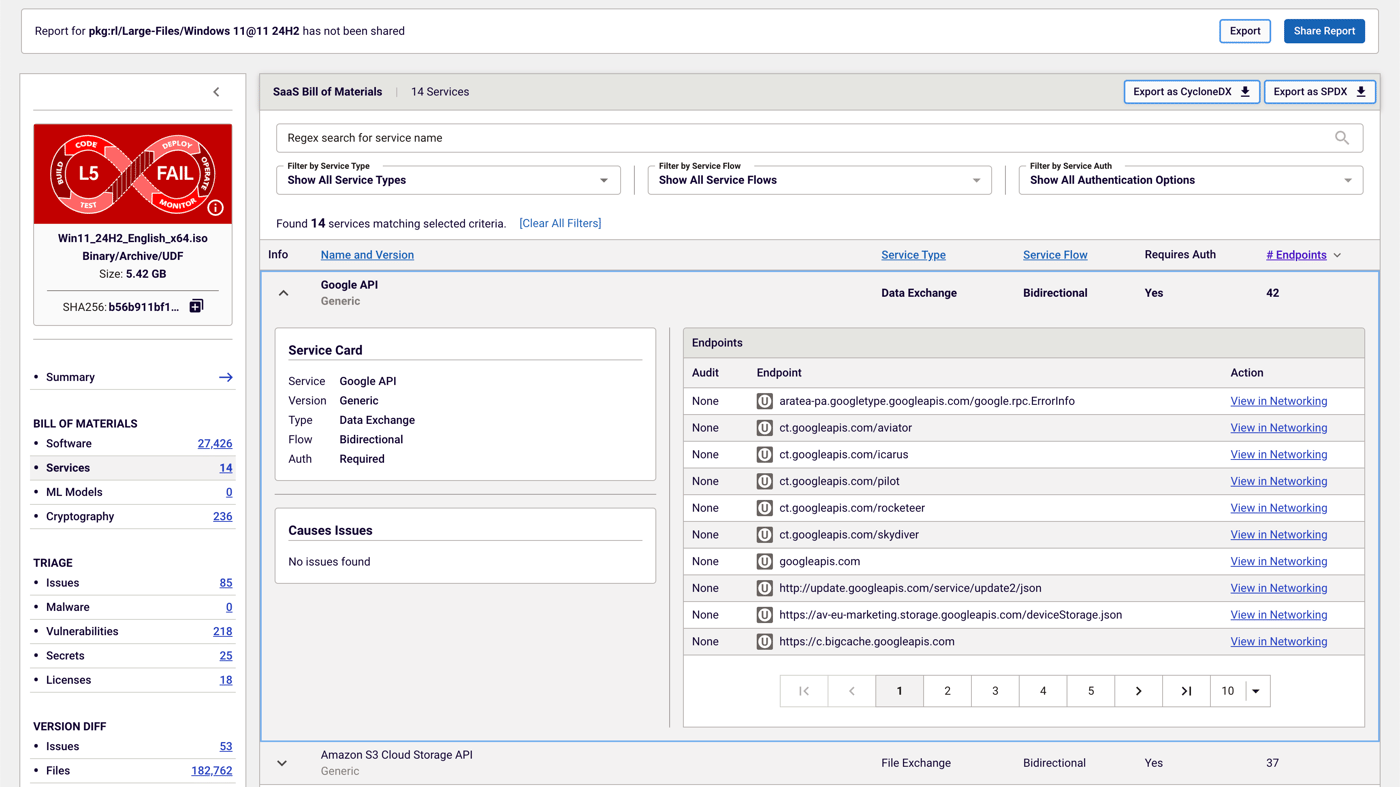
Figure 2: Spectra Assure SaaSBOM provides visibility into all services used by an application.
The ML-BOM
Spectra Assure provides visibility into every ML model contained within a software package and the software components containing each model, even without access to source code. With support for over 8,000 publicly available models, the ML-BOM delivers detailed insights, including publisher, architecture, task, data inputs and outputs, and license.
Using complex binary analysis, Spectra Assure analyzes each model for embedded threats such as nullifAI or BadSeek, which simplifies risk management for both software producers and enterprise buyers.
In addition to Spectra Assure being able to assess the security risks presented by AI/ML, organizations can use the ML-BOM’s clearly documented components to achieve regulatory compliance called for by the U.S. National Institute of Standards and Technology’s (NIST’s) AI Risk Management Framework, as well as the European Union’s AI Act that targets AI risks in high-impact sectors.
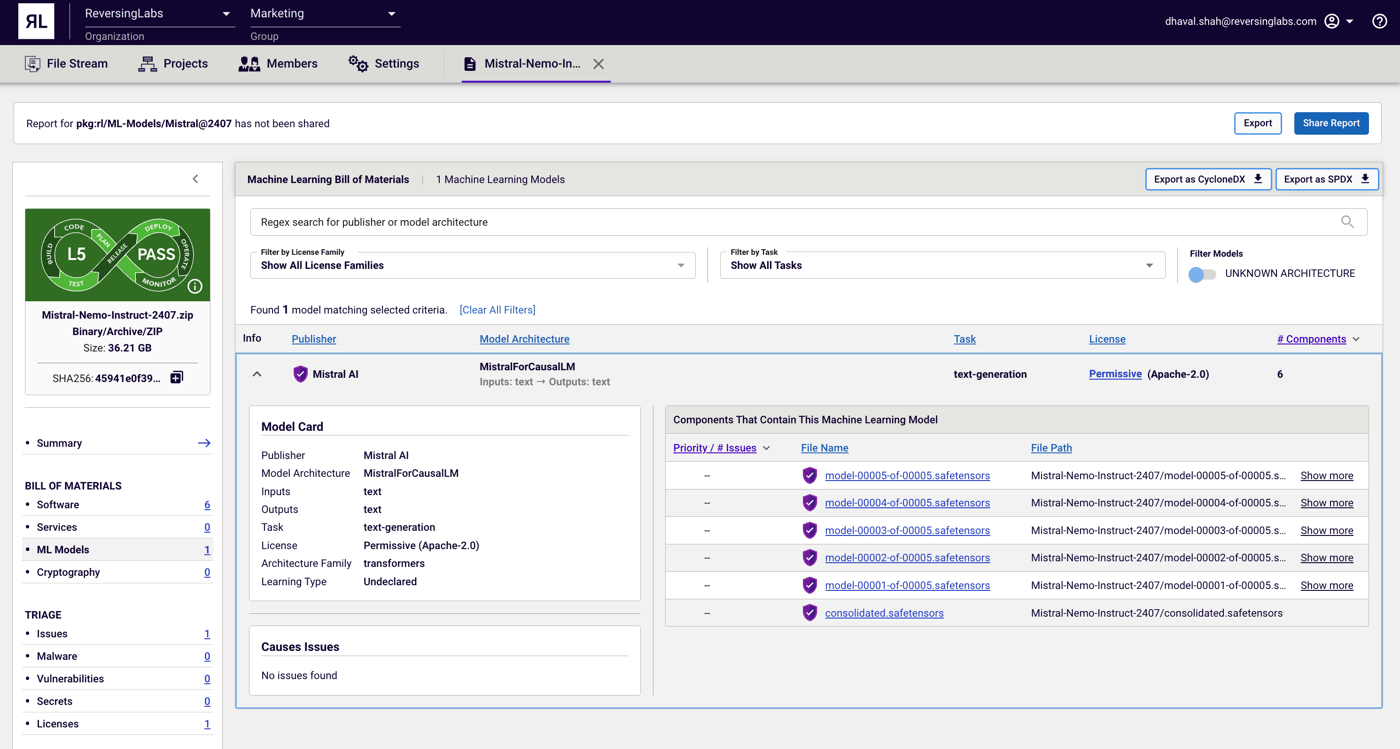
Figure 3: Spectra Assure ML-BOM delivers insight into ML models and threats within an application.
The CBOM
Spectra Assure provides a detailed inventory of all cryptographic assets in a particular product. This includes cryptographic algorithms, tokens, certificates, and keys that are implemented within a system, as well as how they relate to software components. Quantum security level refers to the strength of cryptographic algorithms designed to resist attacks from quantum computers, using standardized categories developed by NIST.
This level of detail helps organizations ensure their encryption methods are secure and remove any outdated algorithms or expired certificates. It also makes it easier for organizations to comply with cryptographic policies and standards and gives them better insight into their overall security posture and cryptographic dependencies.
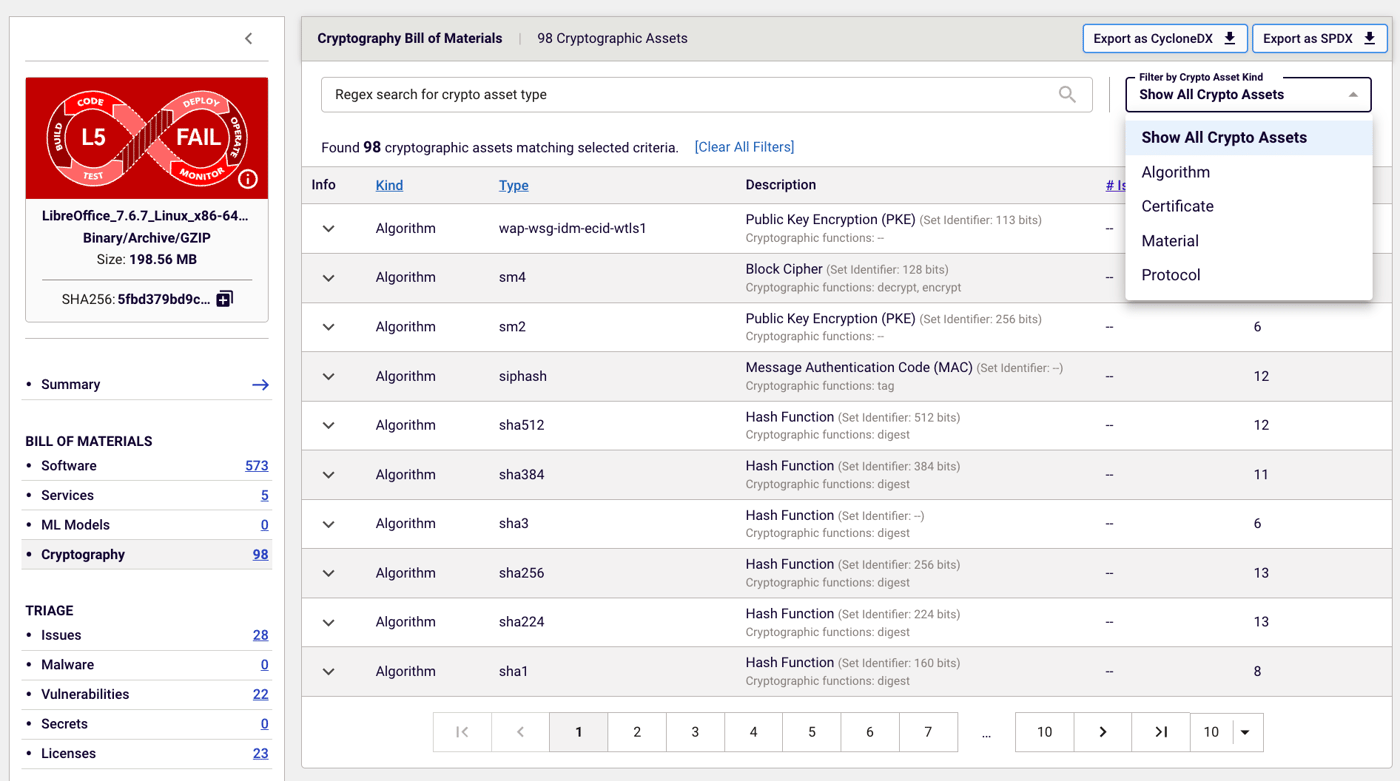
Figure 4: Spectra Assure CBOM delivers insights into cryptographic assets within software, enabling organizations update expired certificates and algorithms
Going Beyond the SBOM/xBOM
The xBOM put forth by CycloneDX v1.6 addresses the nature of how various assets move through and are incorporated into software supply chains. Industry guidelines and regulations are increasingly calling for the SBOM – and now the xBOM – to bring detailed visibility into their software ecosystems by representing comprehensive inventories of software components, dependencies, and relationships. Spectra Assure supports these standards, and the insights they bring.
While these insights are essential, they alone do not bring visibility into malware, tampering, or other exploits that impact software development and their pipelines. To learn how Spectra Assure goes beyond the SBOM/xBOM, click here.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








