Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Thinking about malware files usually leads to thoughts of some criminal organization looking to attack you and steal your files, money or personal data for their own benefit. While attacks through resident malware can often be attributed to criminals, there are dangers to privacy looming from a completely different corner - potentially unwanted applications (PUAs).
These stealthy applications are often installed on a device by hitching a ride with downloads of useful software. After they sneak onto your computer, they usually hijack your browser, insert advertisements, and track you while you surf the Internet. If this doesn't seem like a big deal, think again - these apps could be analyzing and running even on secure sites (like your bank portal, ecommerce/credit card processing website, or email infrastructure), sending data back to their servers.
Although analyzing and categorizing potentially unwanted software is a complex problem, there are general rules that some security vendors follow to classify PUAs. For example, Malwarebytes follows these specific criteria:
There is a general opinion that Windows users are the ones having malware problems and that macOS, because of its Unix under-the-hood “pedigree”, is simply immune to infection. However, that couldn’t be further from the truth.
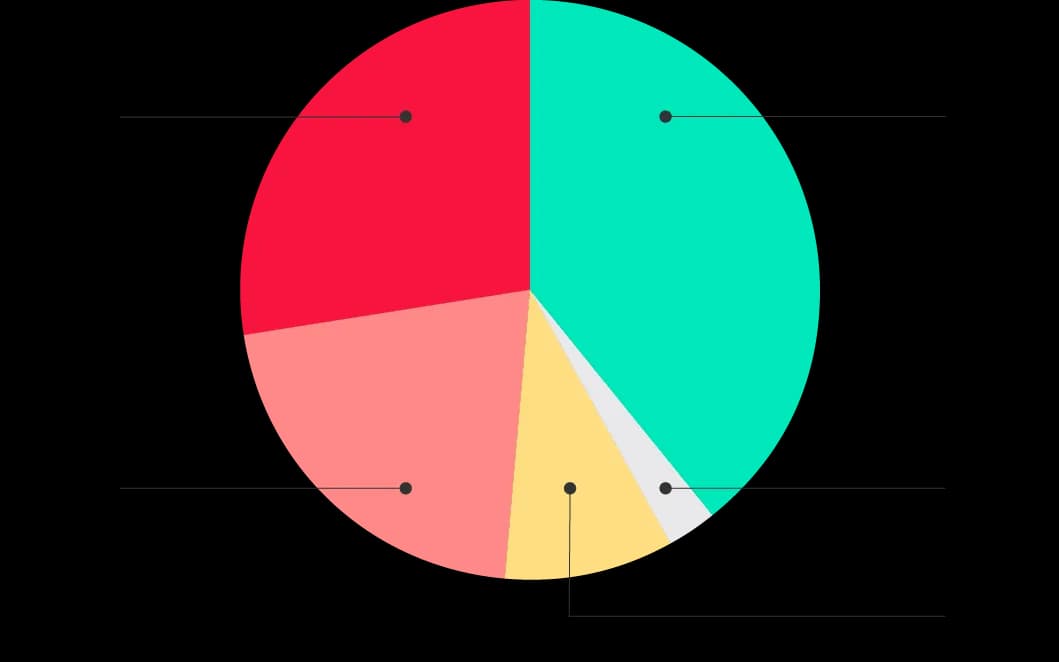
Figure 1: Distribution of macOS Malware Types
ReversingLabs already posted the findings on the state of macOS malware in 2019. We found that one out of every two malicious macOS files is a PUA or Adware file. Recently, Malwarebytes also released a report noting the rise in detected infections on macOS devices, with the majority of detections being varieties of potentially unwanted programs (PUPs).
While their test was run only on devices that already had their software installed, thus introducing a considerable amount of bias, their research also confirms that macOS is particularly targeted by Adware and PUA campaigns. On the one hand, this is because the malware campaigns on macOS tend to be more targeted and limited in scope. On the other hand, Adware and PUA usually trick users into clicking and installing them, and are thus targeting all unsuspecting macOS owners.
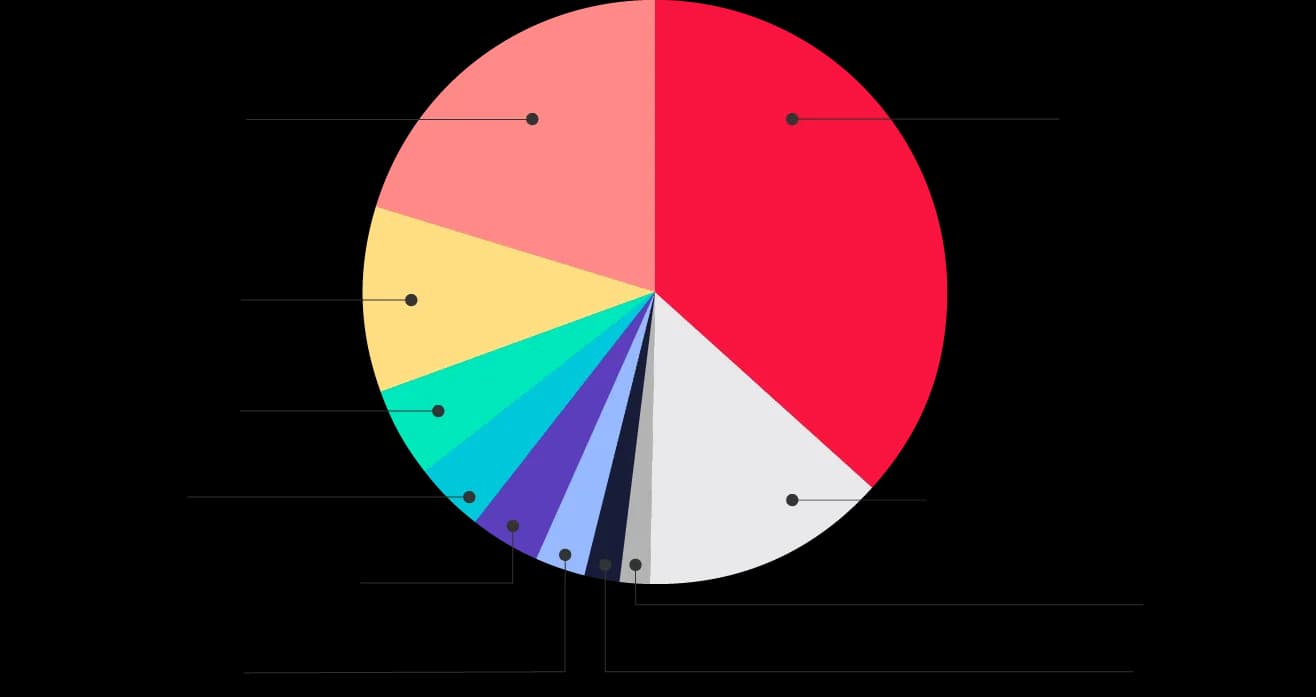
Figure 2: Distribution of macOS PUA Families
One of the most popular PUAs in 2019 was MacKeeper. MacKeeper is a long-lasting and controversial threat; the first beta-version of MacKeeper 0.8 was released on May 13th, 2010, and it has been observed in the wild ever since. It is a rogue “antivirus” (AV) application for macOS designed to "optimize and clean a computer system." MacKeeper is considered malicious due to its:
The software is also reported to be problematic to uninstall.
In the meantime, MacKeeper had gone through some major updates, but the spiel remained the same. The numerous “critical” issues that it will identify on even a brand-new, out-of-the-box Mac, are not real. This is simply a scare tactic to encourage users to purchase the software while evaluating the trial version. One way to identify MacKeeper is by looking at its certificate information. The ReversingLabs A1000 platform provides an overview of the certificate trust chain, as illustrated below.

These files are signed because they are essentially legitimate software distributed by legitimate companies. However, that software relies on unethical tactics with a goal of selling more official licenses. Since ReversingLabs Automated Static Analysis extracts certificate information from binary objects, it can be used to filter interesting PUA files, and blacklist specific certificates you find undesirable in your environment.
If you are wondering whether you are infected or not, there are some telltale signs to look out for; namely:
While you may think some PUA and Adware are not putting your Mac at risk, they could act as a backdoor into your Mac - a way for cybercriminals to steal data, passwords and other sensitive details. They could also give the intruders access to the CPU and GPU (the processing power your Mac needs) to use your computer as part of an illegal cryptocurrency mining operation for example.
There are many ways to protect yourself against these threats, but your goal should be to not get infected in the first place. The most frequent way for adware to get onto systems is through user interaction, so it's important to stay up-to-date and be wary of any odd links or advertisements.
The safest thing you can do is use the Mac App Store to install applications whenever possible. Applications on the App Store have been verified by Apple, and should not contain any malware. When you do need to install an application from elsewhere, make sure it’s really a trusted source, read every window it opens, and never accept the installation of third-party options they offer. If you use a Mac, stay alert, use credible antivirus software, and don’t allow yourself to be lulled into a false sense of security. Remember: you are the first line of defense.
If you are an organization that wants to be safe from these threats, and you’ll want to check whether your employees' Mac computers have been infected. ReversingLabs offers various solutions like A1000, or our Certificate Index, Analytics and Thumbprint search APIs. For more information, please check our homepage or contact us directly.
Read our other macOS blogs:
Read about our Titanium Platform technology to counter these attacks
Download our eBook on The Destructive Objects Playbook
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial