
There is a general belief amongst Mac users that there is no malware attacking the macOS, and hence they do not need endpoint security or antivirus software. However, this could not be further from the truth, as Macs have been affected by malware for the most of their existence. Even some of the first viruses, like Elk Cloner, affected Apple computers rather than MS-DOS computers. With evolving technology, the state of malware attacks gets more sophisticated and harder to detect.
ReversingLabs constantly tracks emerging macOS threats as well as the old, persistent ones. Mac malware developers are actively becoming more clever, attempting to make it harder to detect the malicious nature of their software.
ReversingLabs solutions have evolved to detect and triage macOS malware, and we have developed an algorithm that identifies code similarity between unknown macOS samples and previously seen malware samples. By the end of 2019, our reputation database contained more than 1.5 million malicious macOS files. During the year of 2019, we identified more than 150.000 previously unknown malicious macOS samples.
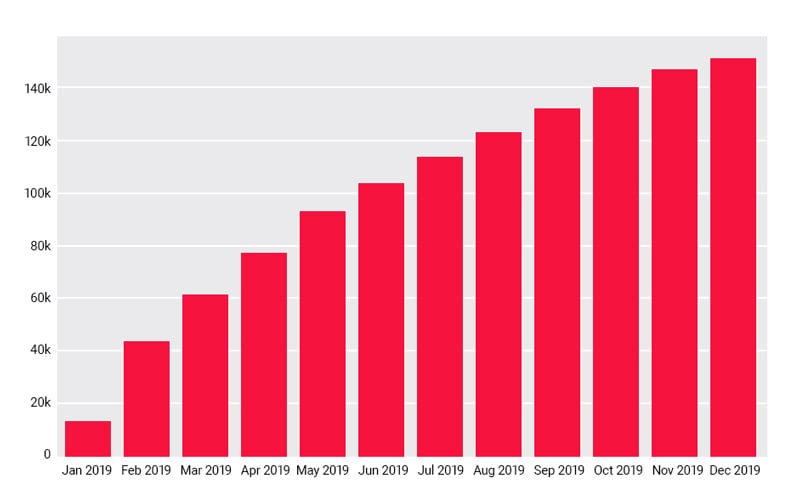
Figure 1: Cumulative Overview of macOS Malware in 2019
We observed some new variants of old malware families as well as some new, never-before-seen threats like Linker, LoudMiner, etc.
It's evident that criminal gangs as well as the nation-state backed APTs are increasingly targeting macOS users. We have looked into the ReversingLabs repository and checked for some interesting malware families to increase the awareness of macOS malware present in the wild. Furthermore, we have extracted interesting malware families in the following three groups:
- The abounding - threats with the most volume in the ReversingLabs repository in the past year,
- The persistent - threats that have been in the wild for a long time, and
- The fresh - threats observed in the past year for the first time.
The abounding
FlashBack
FlashBack, also known as Fakeflash, is a Trojan horse affecting personal computer systems running Mac OS X. Flashback is a form of malware designed to grab passwords and other information from users through their Web browser and other applications, such as Skype. It is often mistaken for a legitimate browser extension because it often masks itself as such while visiting a malicious Web site. At that point, the software installs code designed to gather personal information and send it back to remote servers. In its most recent incarnations, the software can even install itself without user interaction. In the past year, we observed more than 80 thousand different instances of FlashBack malware.
MacControl
The clue is in the name - Mac Control is a very dangerous Trojan that aims to take control over your Mac. Mac Control executes when the system starts, and will establish a connection to the C&C in order to wait for commands. Investigation into the malware itself shows it has the ability to allow remote shells, as well as the ability to send, receive, and delete files. It can steal your files, copy your saved passwords, and even obtain financial data that you may enter in your browser, like credit card details.
MacKeeper
MacKeeper is a rogue antivirus software for macOS designed to "optimize and clean a computer system". It is considered to be a malicious antivirus due to the misleading advertising and promotion tactics, including aggressive affiliates, pop-under ads, and planting sock-puppet reviews as well as websites set up to discredit their competitors. MacKeeper allegedly fakes virus infections to scare users into paying for unneeded fixes. The software is also reported to be problematic to uninstall.
The persistent
MacKeeper
The MacKeeper is not only one of the malware families with most samples, but they have been around for a while now. The first beta-version of MacKeeper 0.8 was released on May 13th, 2010, and it has been observed in the wild ever since. In the meantime, MacKeeper had gone through some major updates, but the spiel remained the same. The numerous “critical” issues that it will identify on even a brand-new, out-of-the-box Mac, are not real. This is simply a scare tactic to encourage users to purchase the software while evaluating the trial version.
Xamloader
Xamloader, also known as WeDownloader, is deemed a potentially unwanted program that performs malicious actions once installed on the computer. It is usually bundled to freeware or shareware applications, and targets mostly known browsers like Internet Explorer, Google Chrome, Mozilla Firefox, and Safari. This threat performs changes on browser settings that may result in home page hijacking and browser redirect problems. Xamloader also drops an add-on to achieve other malicious tasks. To start instantly when the browser is opened, it installs itself as a browser helper object. This also gives the malware the ability to control the browser, and install its own search engine and toolbar object.
WebDownloader
WebDownloader is considered a web browser add-on that is installed without your knowledge as a plugin or extension in your browser. After installation, it starts displaying unwanted ads when you browse the Internet. This type of adware is not limited to displaying ads, but can also redirect you to other malicious websites and constantly display annoying popup ads.
The fresh
LoudMiner
LoudMiner is an unusual case of a persistent cryptocurrency miner, distributed for macOS and Windows. It uses virtualization software – QEMU on macOS and VirtualBox on Windows – to mine cryptocurrency on a Tiny Core Linux virtual machine, making it cross-platform. It comes bundled with pirated copies of VST software. The miner itself is based on XMRig (Monero) and uses a mining pool; thus, it is impossible to retrace potential transactions.
MacEnizer
MacEnizer is categorized as a potentially unwanted application (PUA) since developers promote it using dubious, deceptive methods. Most people download and install PUAs unintentionally. However, MacEnizer is advertised as a system optimizer; a tool that supposedly cleans and maintains Mac computers.
CVE-2019-6225
A vulnerability has been found that has been classified as critical. The manipulation with an unknown input leads to memory corruption. The issue was addressed with improved validation and fixed in iOS 12.1.3, macOS Mojave 10.14.3, tvOS 12.1.2. Using this exploit, a malicious application may be able to elevate privileges.
Linker
Linker is a generic name for malware that exploits a zero-day macOS Gatekeeper vulnerability to infect the system. Infections of this type are designed to use symbolic links (or 'symlinks') to bypass macOS protection by accessing a Network File System (NFS) server and injecting malicious applications into the system (rather than downloading them directly from the Internet).
As we can see, not only are there multiple malware threats on the macOS, but the old ones also tend to stick around while new attacks become increasingly sophisticated.
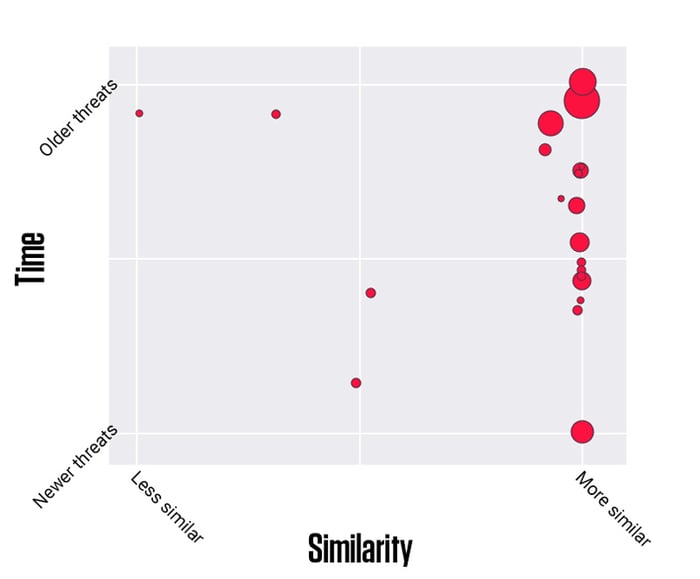
Figure 2: Functional similarity of macOS Malware families in 2019
While evolving technology allows more refined and harder-to-detect attacks, ReversingLabs continues to improve and advance its threat detection tools. The descriptions above clearly illustrate how a lot of macOS malware files are functionally similar to one another. We had seen that some of the most common tactics include tricking users to download malicious payload themselves, coin miners that hijack a portion of your computing power, or some potentially unwanted applications that aren’t necessarily malicious, but do have malicious intents like tricking users to buy unnecessary premium options.
ReversingLabs has developed a way to identify and triage functionally similar files. All our products come equipped with our ReversingLabs Hashing Algorithm (RHA) that identifies code similarity between unknown samples and previously seen malware samples in macOS. This feature, along with many others, means that our products can be used as the first line of your company's defense. For more information, please check our homepage or contact us directly.
Read about our Titanium Platform technology to counter these attacks
Download our eBook on The Destructive Objects Playbook
Keep learning
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








