
We’re proud to be working with our technology partner Sophos on the SOREL-20M project to help organizations accelerate their threat hunting programs and malware research. This project is a collaboration between SophosAI and ReversingLabs threat researchers to produce a production-scale dataset of 20 million Windows Portable Executable (PE) files that will allow researchers to improve security detection and response industry-wide. This curated dataset further includes 10 million disarmed malware samples available for download, and use in research and feature extraction. This aids organizations' efforts to understand how malware is targeting their networks and allows them to adjust their defenses accordingly.
The idea of threat intelligence sharing among the security community isn’t new but is more critical than ever given the innovation threat actors have shown over the past several years. Organizations have begun to realize they have to take a more active role in their defense by building threat research programs into their security operations. Machine learning (ML) and AI have become central to these efforts allowing threat hunters and SOC teams to move beyond a reliance on signatures and heuristics, and become more proactive in detecting new or targeted malware. That said, while the introduction of machine learning technologies represents a significant leap forward for threat detection at scale, these systems are only as good as the datasets they have access to. As Sophos stated, “Standardized datasets are the way in which new features and models are developed, tested, and compared to each other,” which makes it imperative for us to provide our partners and customers with access to our data and do our part to move the industry forward.
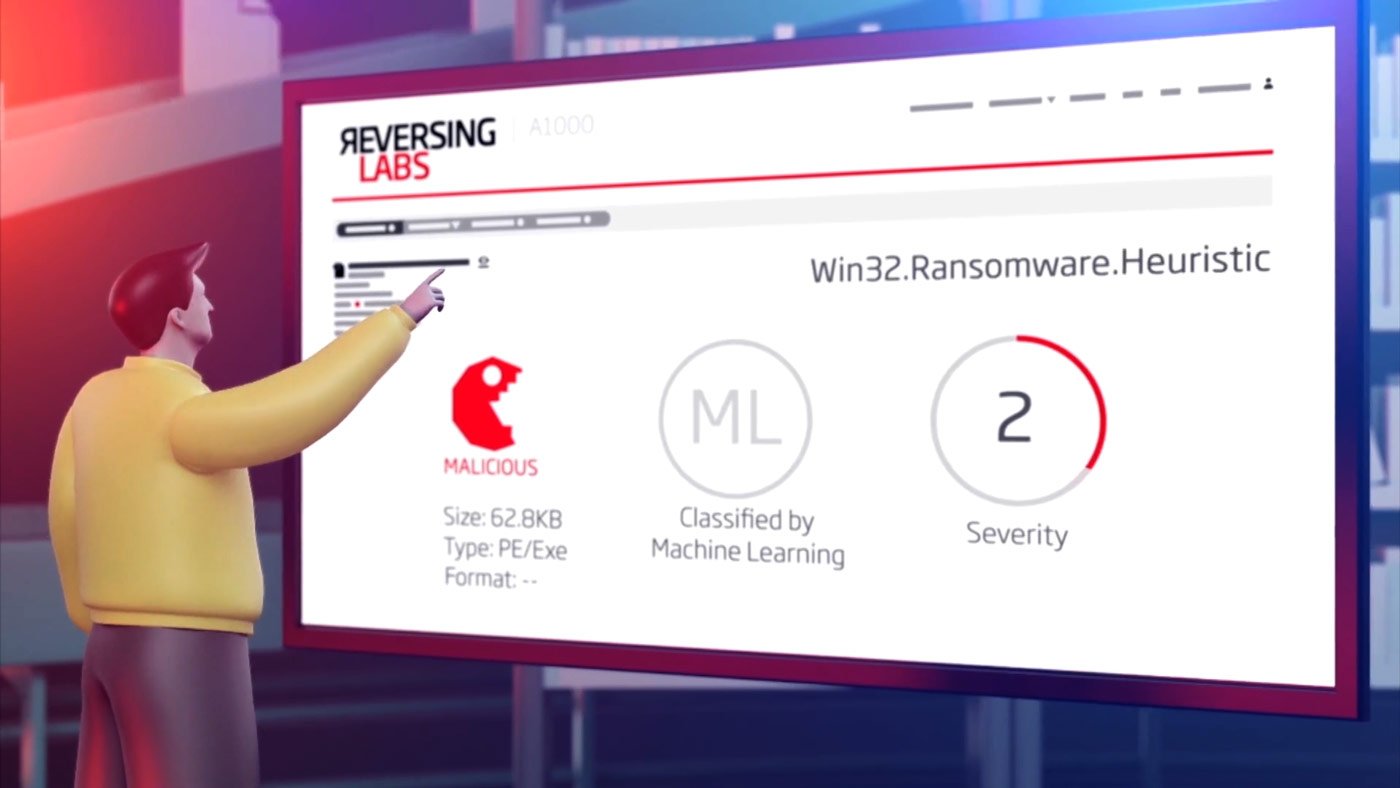
As an industry, we know malware isn’t limited to Windows or even executable files, which is why researchers and security teams will always need more data representative of the infrastructure to be protected. Here at ReversingLabs, we gave ourselves the goal of providing analysis capabilities for malware across every major operating system and file format to ensure we could provide the most accurate and timely intelligence and alerts to our customers. This is an almost impossible challenge given the scale and depth of modern malware. But our team stepped and today ReversingLabs supports the analysis of over 4,000 different file types and formats, and provides a reputation database on over 12 billion good ware and malware files. All this data gives our customers a well defined dataset of threat intelligence to leverage in their defenses, and as part of their threat hunting programs, to both block active attacks and search for threats that may otherwise be invisible to the traditional security stack.
Security technology can’t act in a vacuum which is why we continue to push the boundaries of file analysis, malware research, and threat intelligence. New security paradigms recognize the need for more insight beyond threat levels and classifications. Threat detection also needs to be explainable, allowing security teams to better understand the conclusions derived through technology in order to make better decisions in response. Collaborating with our security partners like Sophos means better data for ML and AI engines to process which results in more trust in the automated systems organizations use to protect their critical assets. We’re excited that this is only the start of a great partnership.
Read our blog on Explainable Threat Intelligence:
https://blog.reversinglabs.com/blog/introducing-explainable-threat-intelligence
Learn more about exposing hidden malware in EDRs:
https://www.reversinglabs.com/solutions/edr-malware-detection-integration
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








