Assess and Manage Third-Party Software Security Risk
Open the Black Box of Commercial Software
Cybersecurity and third-party risk managers don’t have the right tools to identify the risks and threats in the commercial software they deploy across their organizations. Security questionnaires, pentests, and spreadsheets cannot provide an in-depth review of a vendor’s software prior to purchase, and cannot scale to identify attacks embedded within software updates.
Spectra Assure introduces a primary control for any third-party software before, during, and after deployment to detect threats such as malware, tampering, suspicious behaviors, and more that other manual and cumbersome methods miss outright.

The ideal case is that you're running ReversingLabs on everything prior to purchase. I not only get the SBOM, I also get insights into malicious code or tampering.
Tim Brown | CISO
We have almost every cybersecurity tool, but Spectra Assure showed us risks we couldn’t see before. That was huge.
Global Head of Windows | Large Global Bank
We get a lot of requests to install different applications. Spectra Assure lets us know if that software is safe or not, and simplifies that 'yes' or 'no' discussion with employees.
Security Operations Manager | Local Municipality
BEFORE YOU BUY
Quickly identify risks in third-party software. Share actionable reports with vendors, cyber, GRC, and procurement.
BEFORE YOU DEPLOY
Identify critical security issues for risk and security teams. Collaborate with vendors on fixes via shareable SAFE reports.
SECURE UPDATES
Automate threat analysis on updates to proactively stay ahead of risk stemming from compromised updates.
RAPID RESPONSE
Address newly reported supply chain attacks and zero-days that may be present in your environment.
Spectra Assure’s Complex Binary Analysis delivers a comprehensive assessment of commercial, freeware, and open-source software without the need for source code, closing the gap in vendor risk management. Spectra Assure is simple and effective. Upload and analyze the complete software binary, regardless of size and complexity, and identify embedded threats like malware, tampering, vulnerabilities, and exposed secrets within minutes.
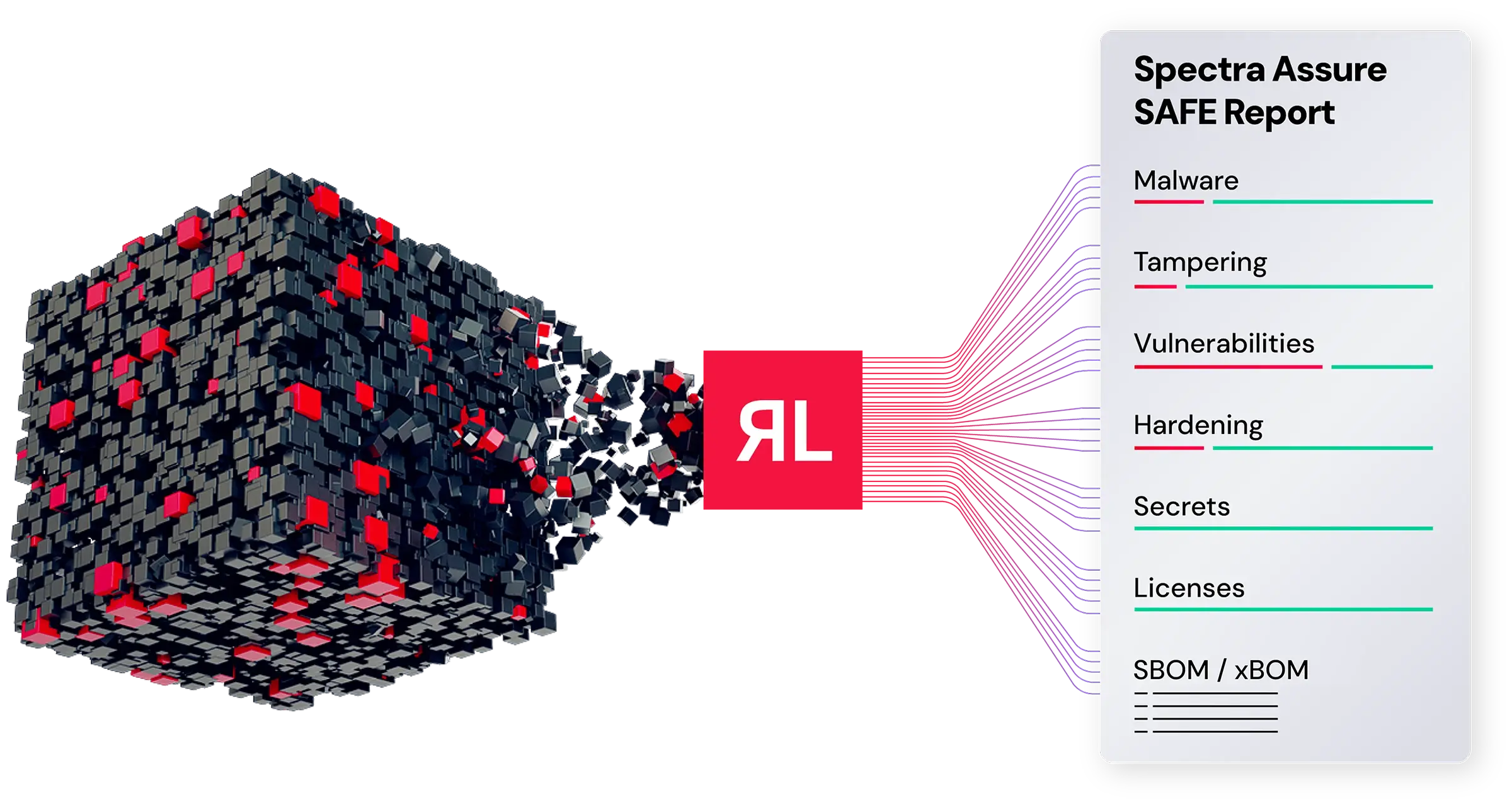

Spectra Assure provides the most comprehensive risk analysis of third-party applications prior to purchase or deployment. Providing a clear pass or fail reporting to expedite procurement decisions across multiple vendors.

The SAFE report goes beyond the SBOM by providing much more than a mere list of ingredients. It creates a comprehensive risk assessment of any third-party software package by highlighting embedded threats like malware, tampering, suspicious behaviors, and more.

The SAFE report can be securely shared with vendors to share security findings and communicate policy requirements with vendors. This fosters collaboration and urgency towards remediation action plans. Shareable SAFE reports are:
Spectra Assure comes out of the box with risk tiers known as SAFE Levels. These provide a benchmark for security and risk teams to make quick and informed decisions about the threat level of the application being analyzed.

Spectra Assure provides users with a consistently up-to-date view of their application risk profile as new updates are made. Version differential analysis flags new threats introduced with new patches, versions, or updates, making ongoing maintenance and monitoring of third-party software risk that much simpler.

Pentesting is important for regulatory compliance (e.g. PCI-DSS). But it’s too expensive and not scalable for identifying risks in third-party software. You could be saving money using Spectra Assure. Check out the RL Cost Savings Calculator to find out.


The SunBurst supply chain attack, which was behind the SolarWinds compromise, took sophistication and patience.
Learn More
Discover key attack trends in RL’s third-annual Software Supply Chain Security Report. Get expert insights on emerging threats over the past year.
Learn More
See what product and application security teams need to know to protect against software supply chain compromises.
Learn More