Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial-1-1400x732.webp&w=3840&q=75)
Cambridge, MA—April 30, 2024 — ReversingLabs (RL), the trusted name in file and software security, today announced a significant evolution in its product lineup with the launch of the Spectra Advanced File Analysis and Malware Detection suite, its comprehensive, unified suite of tools designed to meet the diverse needs of modern cybersecurity and SOC teams. The newly updated suite includes Spectra Detect, Spectra Intelligence, and Spectra Analyze, all powered by the cutting-edge Spectra Core technology.
"Our mission has always been to provide the most credible, trusted file analysis and malware detection to secure every enterprise file or software package," said Mario Vuksan, CEO and Co-Founder of ReversingLabs. "With Spectra, we are expanding the landscape of deep file inspection by providing an integrated solution that delivers faster and better insights for security operations and threat intelligence teams - regardless of volume, file size, or location across the enterprise."
This strategic update merges RL’s acclaimed complex binary file analysis and threat detection products into a single, cohesive product suite to address some of the most critical issues facing enterprise security teams:
The Spectra portfolio is built on:
The Spectra portfolio* for advanced file analysis includes:
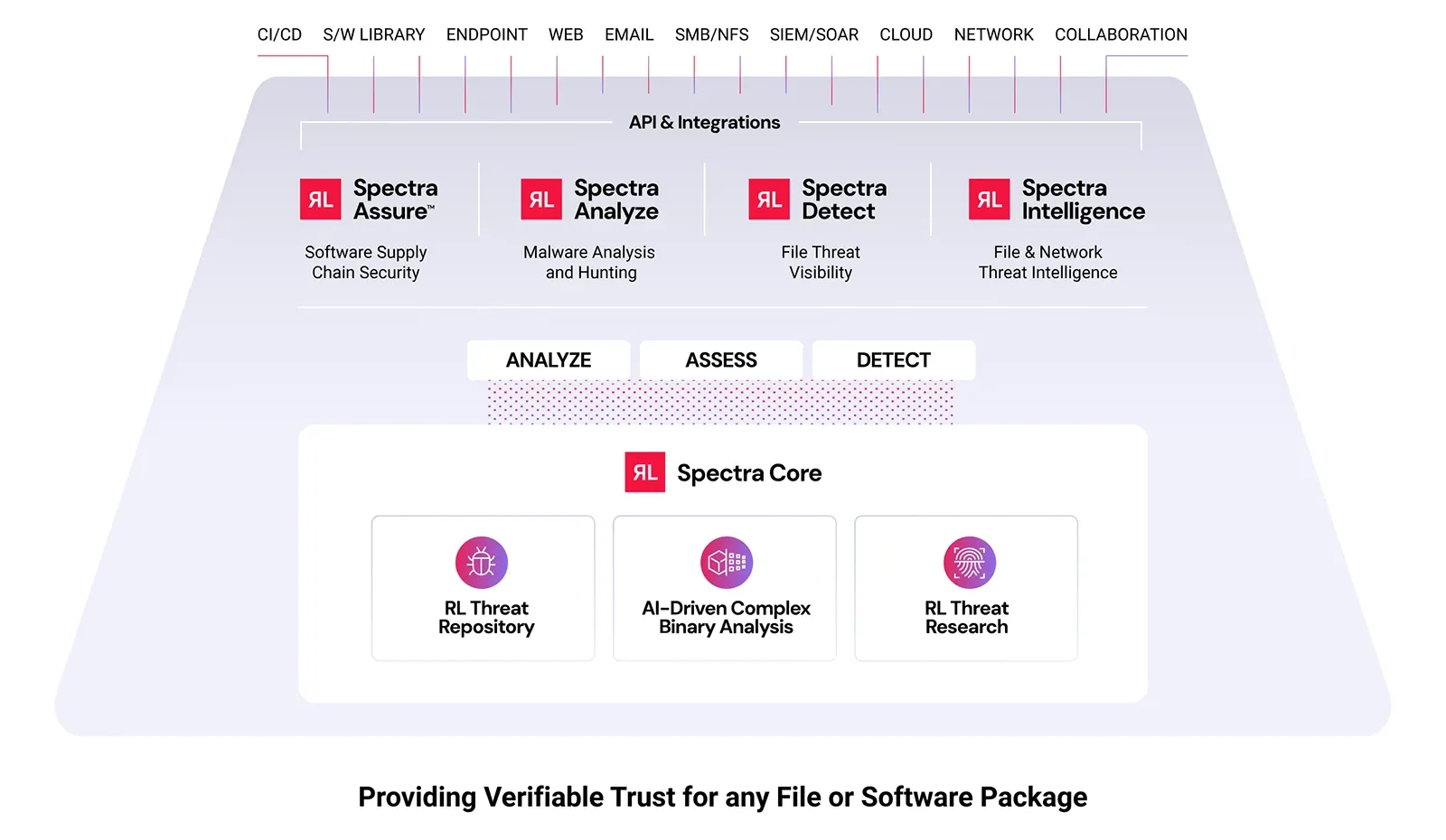
ReversingLabs is the trusted name in file and software security. We provide the modern cybersecurity platform to verify and deliver safe binaries. Trusted by the Fortune 500 and leading cybersecurity vendors, RL Spectra Core powers the software supply chain and file security insights, tracking over 40 billion files daily with the ability to deconstruct full software binaries in seconds to minutes. Only ReversingLabs provides that final exam to determine whether a single file or full software binary presents a risk to your organization and your customers.
*The Spectra suite of products were formerly known as Titanium Scale, A1000, Titanium Cloud, and Titanium Core.

Seasoned Security Leader to Accelerate Go-to-Market Strategy Amid Surging Demand for Software Supply Chain Visibility and Trust

ReversingLabs Joins the Microsoft Security Store Partner Ecosystem

ReversingLabs Further Accelerates Public Sector Momentum Through Key Partnerships with Norseman Defense Technologies, Carahsoft, Mission First Cyber, and Vibrint