HPE once again depends on ReversingLabs data for their annual Cyber Risk Report

ReversingLabs provides comprehensive information on exploits in the wild and the vulnerabilities that may be present in organizations. Through deep content inspection and a massive private sample collection, ReversingLabs solutions alert companies as well as inform other vendor solutions depth of coverage in regard to the danger potentially lurking in their networks. With an opportunity to dig deeper on specific details SOC/analyst teams can drive remediation via very fast, automated inspection and analysis solutions.
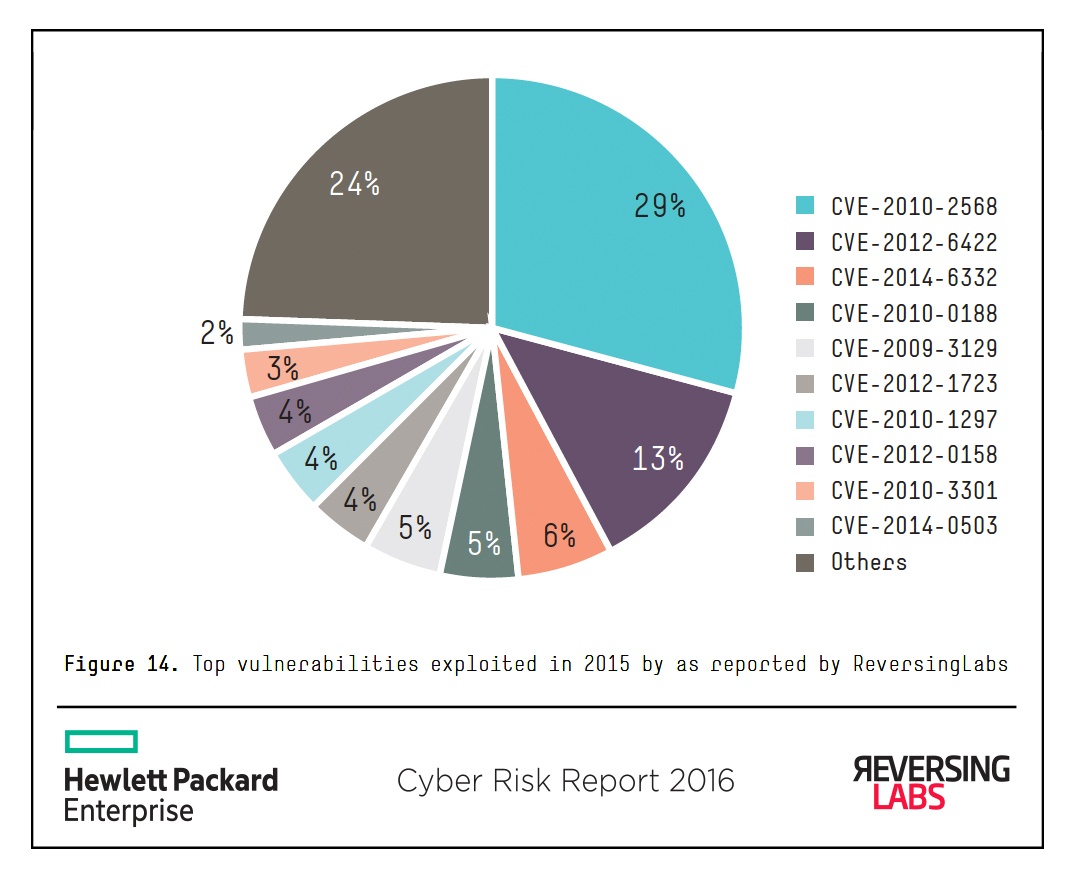
As we learned in last year’s report, attackers leverage more than just the newest vulnerabilities to carry out successful attacks. Looking at newly discovered exploit samples for all known vulnerabilities, not just those discovered in 2015, different patterns emerge. Alarmingly, 2015 is still dominated by CVE-2010-2568224 (patched again in early 2015225), although the overall proportion is a bit lower (29% in 2015 vs. 33% in 2014). In fact, it is disheartening to see that the top 10 vulnerabilities exploited overall (Figure 14) continue to be those that are more than a year old (and 48% are five or more years old).
Surprisingly, the old Shortcut Icon Loading Vulnerability first discovered by VirusBlokAda during the initial analysis of Stuxnet is followed by samples exploiting CVE-2012-6422,226 a vulnerability in Samsung Exynos processors, which allows the attacker to escalate privileges by being able to arbitrarily read and write system memory. The prevalence of CVE-2012-6422 is likely indicative of the increased popularity of Samsung smartphones and the Android operating system.
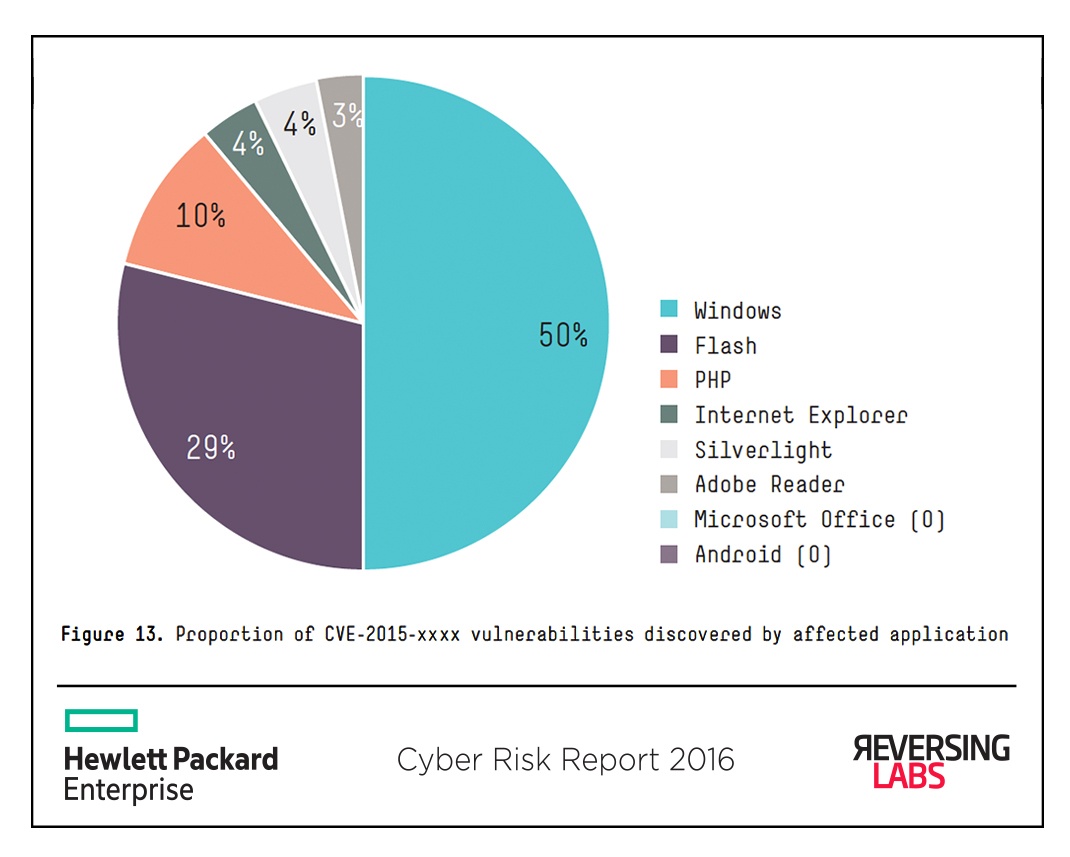
Looking at the proportion of samples discovered by ReversingLabs in 2015, it is Microsoft vulnerabilities that dominate the top 20, accounting for nearly 50% of all discovered samples, followed by Adobe Flash (29%) and a single PHP vulnerability (10%).
In addition to its massive collection of samples, ReversingLabs provides REST APIs for deeper awareness and analysis in multiple areas including Exploits in the Wild. This can enable organizations to take on and accelerate analysis and remediation activities that have previously been highly manually and in the domain of security experts, a rare commodity as companies scramble to recruit and retain talent.
Exploits
As detailed in the “business of bugs” section earlier in this report, finding vulnerabilitiesin software is usually the domain of security researchers, with many of them participating in coordinated disclosure with vendors. Despite the progress made with a record- setting year (both reporting and patching), exploits remained one of the main vectors allowing remote code execution and privilege escalation by attackers.
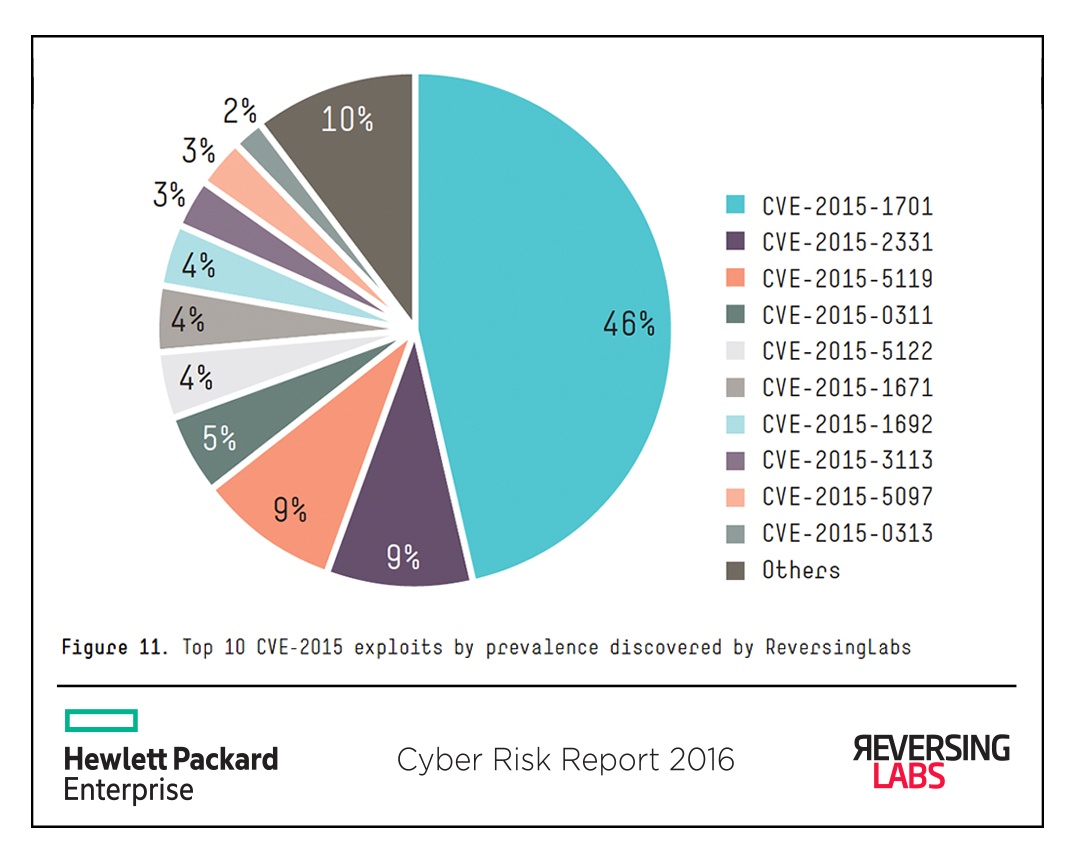
The distribution of newly discovered samples for vulnerabilities identified in 2015 (CVE-2015- xxxx) shows the high prevalence of exploits for the Windows privilege escalation vulnerability CVE-2015- 1701,218 which accounts for over 45% of exploit samples for the year. CVE-2015- 1701, first observed in a highly targeted attack, 219 was used in combination with Adobe Flash remote code execution exploits.
Also, here we have a lot of interesting information about malware:
While the palette of attacker’s tools and techniques continues to evolve, as the Report concludes, malware is still dangerous and pervasive. And attackers aren’t necessarily doing all that much work to create new malware but are often merely slightly altering well-known and proven samples…enough to escape detection by traditional AV solutions. ReversingLabs, with its massive collection of malware and goodware samples as well as its RHA code functional similarity algorithm, is able to find these variations based on what has been used before while at the same time continuously adding new samples to increase effective incident response.
Malware: still dangerous, still pervasive
While malware still represents a significant threat to the digital enterprise in 2015, it seems the linear growth of newly discovered malware samples did not materialize. According to the independent German security testing organization AV-TEST, there were about 140 million newly discovered malware samples for the Windows platform. This largely agrees with the 135 million samples HPE Security Research partner ReversingLabs tracked. It’s important to note that ReversingLabs’ number includes potentially unwanted applications (PUAs).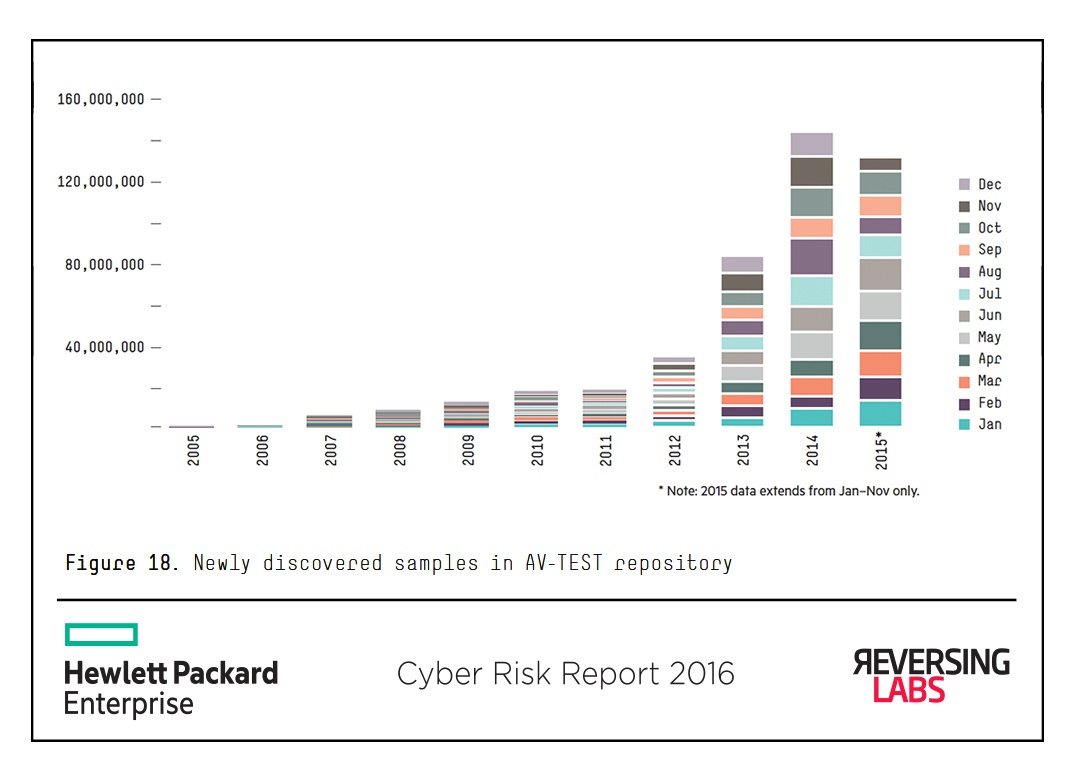
Read more: hp.com/go/hpsr


