CyberThreatAlliance, of which ReversingLabs is a contributing member, published an analysis on one of the most lucrative ransomware attacks

The Cyber Threat Alliance (CTA), of which ReversingLabs is a contributing member, undertook a huge effort of pooling the Alliance’s collective resources to track and analyze CryptoWall, a prominent ransomware attack discovered in 2014. With the initial success of uncovering and subsequent protection against CW3, CTA continued to monitor CryptoWall’s activity to learn and understand the repercussions and reactions from the malware authors. Unsurprisingly, CryptoWall authors were not deterred with the publication of CW3 and sharing of associated IOCs but were determined to release a fourth variant of CryptoWall (CW4) to overcome known malicious characteristics of its predecessor.
Based on the analysis of CW4, CTA researchers found the refreshed malware had similar traits to its predecessor but differed sufficiently to attempt evasion and kept an otherwise similar infrastructure of operation and distribution.
Key Highlights of CW4:
- 15 campaign code identifiers
- 7,194,840 attempted infections
- 36,118 confirmed victims
- Estimated US$18 million in damages
During the period from November 2015 to June 2016, CW4 had reached a total of 7.1 million attempted infections spread across the globe with the largest impact found in North America.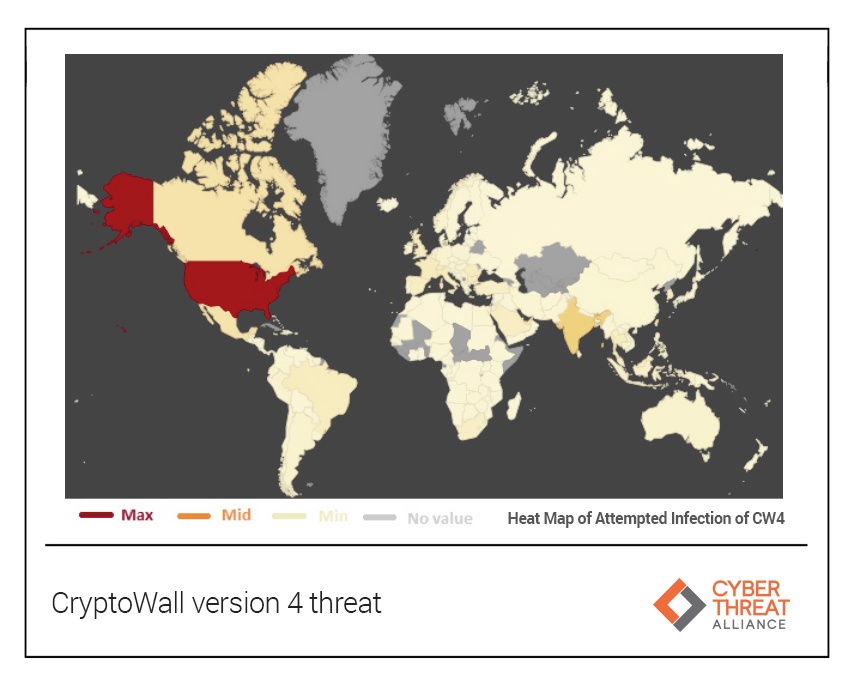
India was identified as the second most-impacted country, per the study found. India’s fast-growing IT industry typically supports multinational companies and operates mainly through the Internet. These factors have made them a significant target for CryptoWall as India rose from the bottom of the Top 10 in CW3 to second in CW4.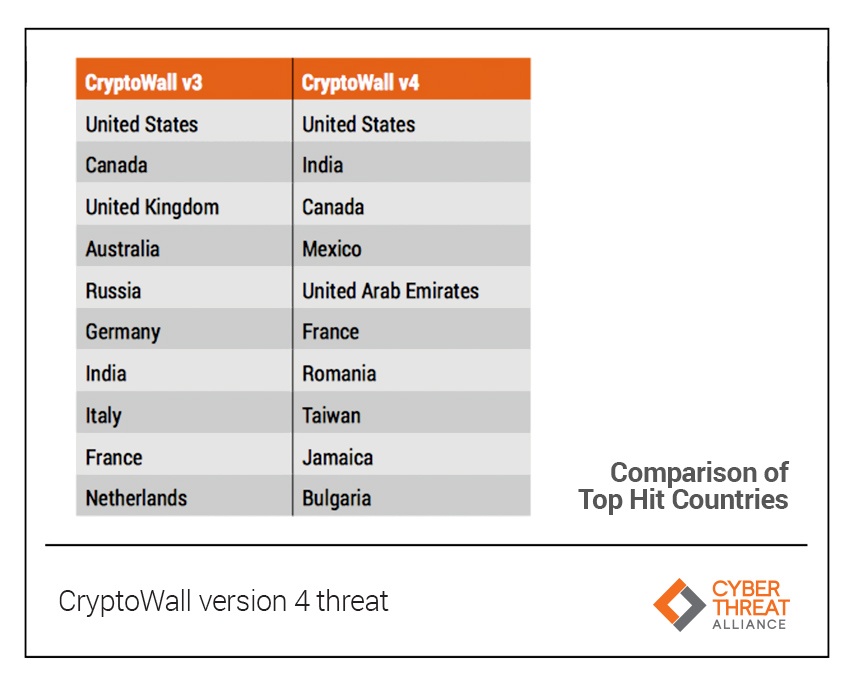
During CW4’s eight-month- long operation, CTA saw a total of 7,194,840 attempted infections with a peak of 228,496 in one day. This pales in comparison with CW3’s 406,887 total attempted infections. Although CW4 was much more aggressive in its attempt to spread the malware (i.e., 18 times more than CW3), the number of confirmed victims was just 36,118. CW3, on the other hand, impacted hundreds of thousands of victims.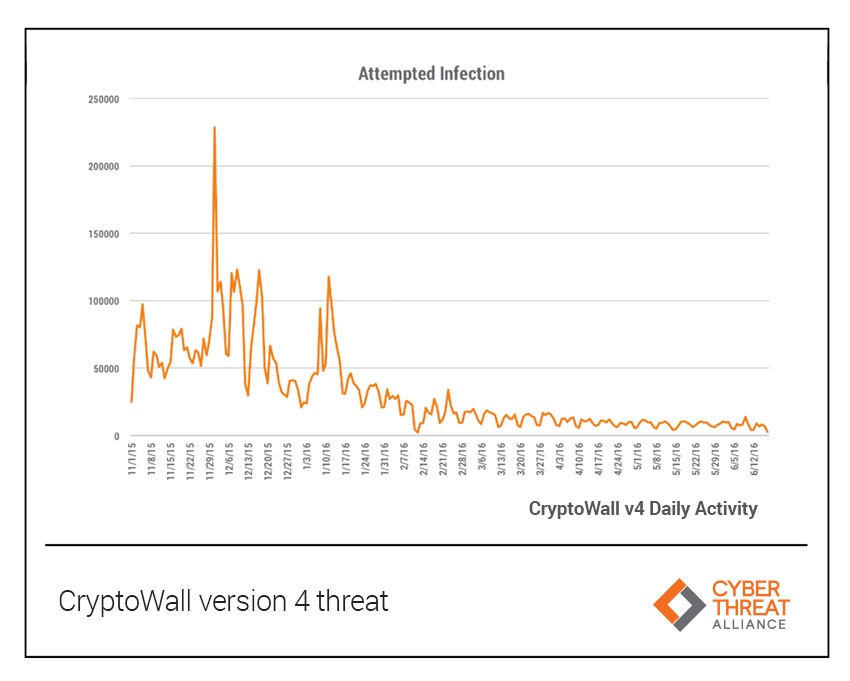
CTA researchers analyzed CW4 campaigns from May 19 to June 14, 2016 (Figure 6), and discovered “crypt7” was the most active campaign in CW4 as was in CW3. This indicates the same individual or group that was most active (i.e., 8,000+ sessions) and enjoyed past financial success with CW3 increased its investment by almost seven times on the fourth variant, reaching up to 55,170 sessions. Unfortunately, it did not pan out financially, as the total CW4 profit was estimated at $18 million when compared to CW3’s profit of $325M.
Read the full report here:
http://cyberthreatalliance.org/cryptowall-report.pdf


