
Experts and a top analyst discussed the state of software supply chain security in a recent Webinar. Here are key takeaways from their discussion.
When discussing popular security threats, looking back at how the security landscape has changed over the past few decades is essential. Software supply chain attacks have surged in recent years, making them a key concern for security teams, as highlighted in The State of Software Supply Chain Security 2022-23.
In a recent related webinar co-hosted by Forrester Research, a panel of security experts were invited to reflect on how the state of software supply chain security came to be. The webinar featured three industry panelists: Sandy Carielli, Principal Analyst at Forrester; Beau Woods, Founder and CEO of Stratigos Security; and Charlie Jones, Software Assurance Evangelist at ReversingLabs.
Here are the key highlights from the expert panel, their insights on the state of software supply chain security — and how security teams should best move forward in 2023.
[ See on-demand webinar: The State of Software Supply Chain Security ]
Supply chain security: How we got here
As Beau Woods noted early on in the panel conversation, there has been a “shift in consequences of cybersecurity failures.” Woods said he's been in the cybersecurity field for 15-plus years, leading to his belief that the industry needs to “innovate new ways to deal with these issues.”
For software security specifically, Woods noted that it was only within the past three to five years that organizations began to want to understand which ingredients are in their software, something that software bills of materials (SBOMs) expose. But only recently, the industry started paying attention to security issues such as undiscovered (zero-day) and unmitigated flaws. Woods also highlighted that software supply chain threats exist via counterfeit code, malicious taint, and supplier risk, which pulls security teams' focus in several directions.
Charlie Jones noted that software supply chain threats are multifaceted and complicated. He believes that the industry must take a comprehensive approach to this problem:
“There is not a single silver bullet to stop a software supply chain attack.”
- Charlie Jones, ReversingLabs
In recent years, conversations about securing software have been dominated by discovering and patching vulnerabilities. However, Jones stressed that we “can’t just stop vulnerabilities” to mitigate software supply chain risks. Instead, industry leaders and practitioners have to focus on the plethora of threats out there.
Forrester Research analyst Sandy Carielli shared how software- and supply chain-based attacks are complex, and include related traditional attack approaches.
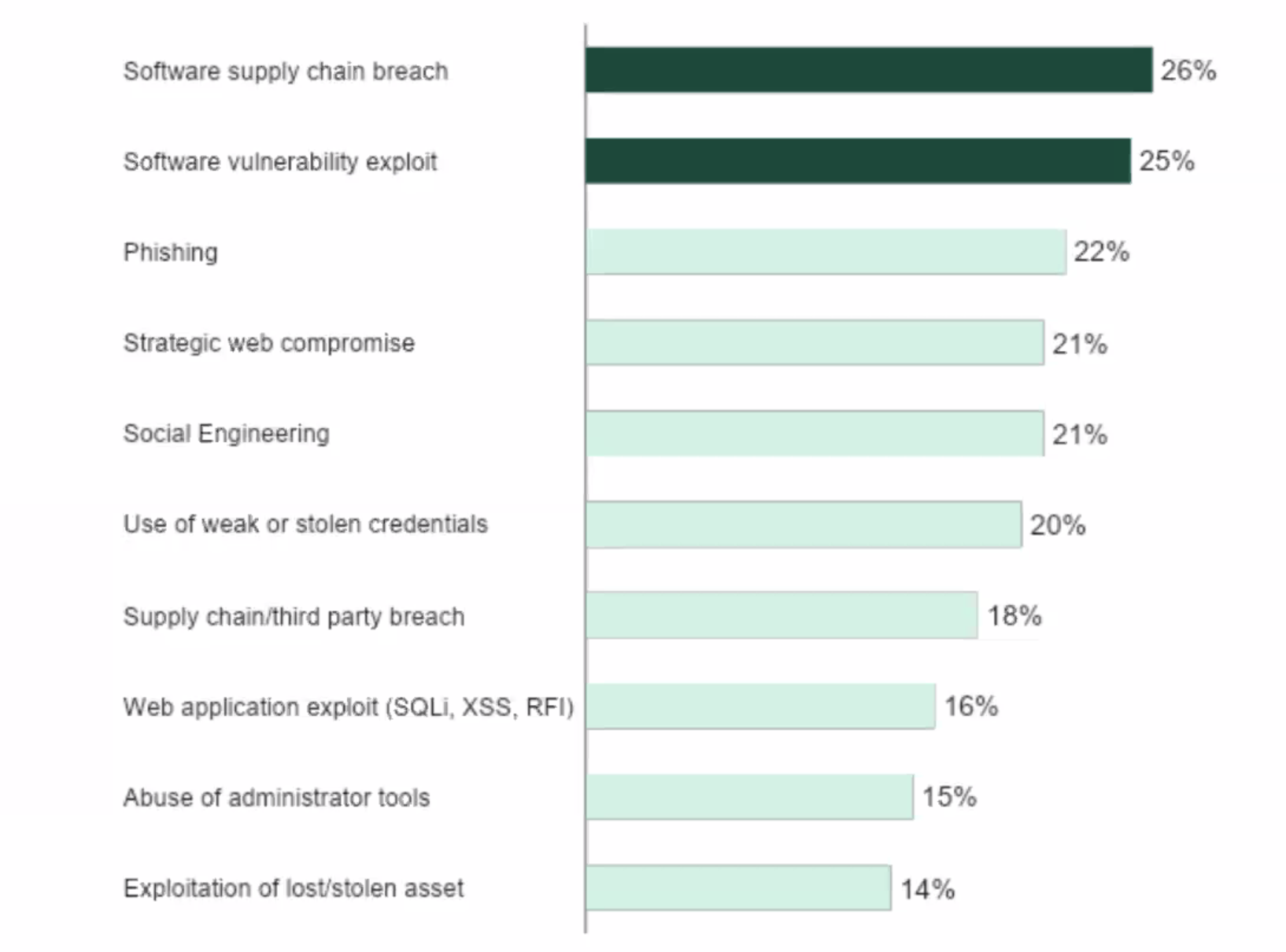
Source: Forrester Analytics Business Technographics Security Survey (2022).
Software supply chain breaches, not vulnerabilities, were the leading cause of external attacks on organizations, Forrester noted in its Forrester Analytics Business Technographics Security Survey (2022). Additionally, Forrester’s survey found that attacks were fairly distributed among 10 different threats, including vulnerabilities, phishing attacks, third-party breaches, and others.
As noted in a recent analysis of the National Vulnerability Database (NVD), focusing on one piece of the problem has not served software security efforts effectively.
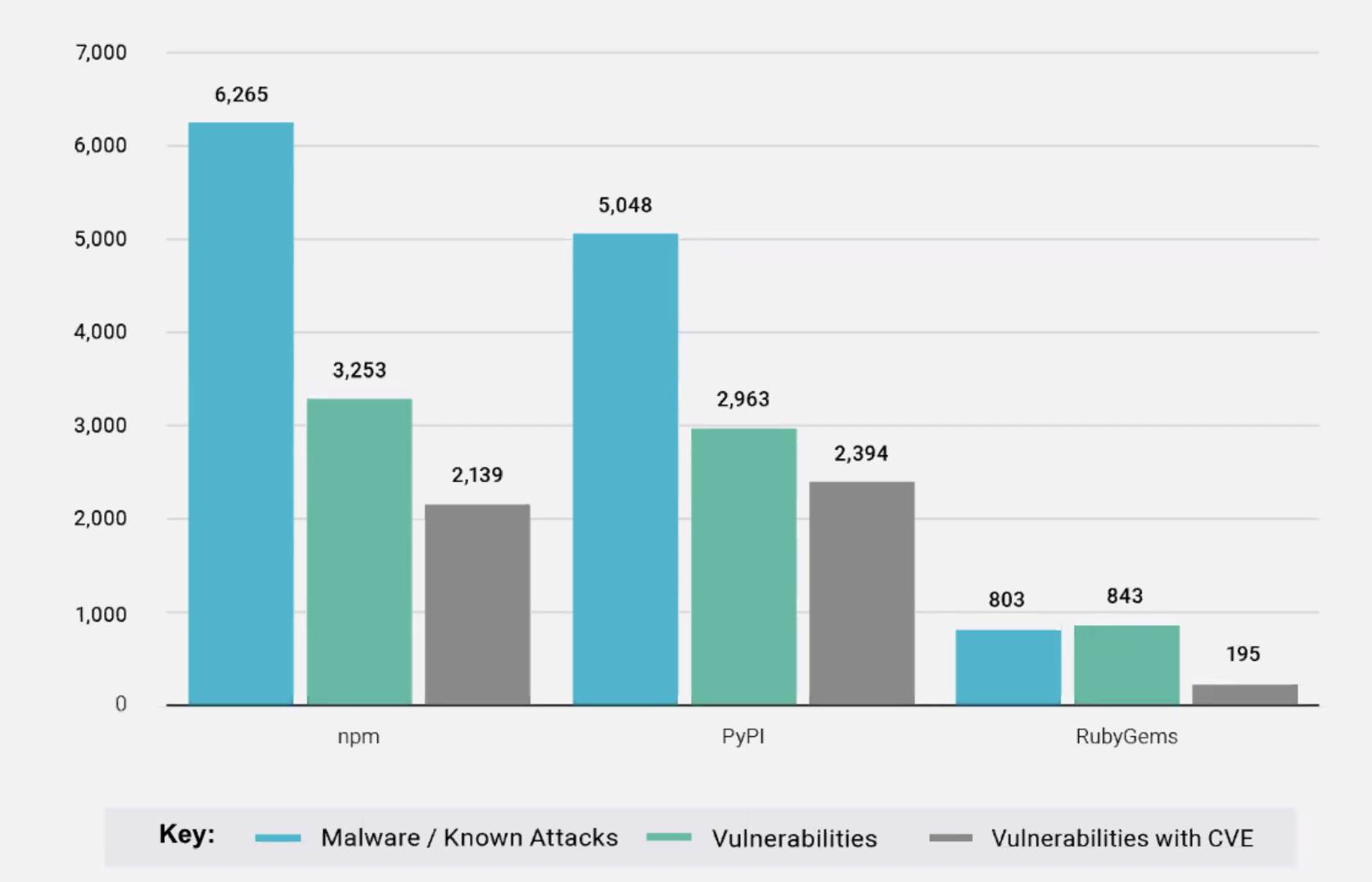
Source: ReversingLabs threat research. See the related full infographic.
ReversingLabs' NVD Analysis 2022: A Call to Action of Software Supply Chain Security highlighted that despite the rising number of vulnerabilities submitted to the National Vulnerability Database (NVD) in recent years, malware insertions and targeted attacks against the software supply chain via open source repositories and packages are outpacing vulnerabilities as an attacker’s vector of choice. The takeaway: Paying attention to vulnerabilities alone leaves huge gaps in coverage when defending against software supply chain attacks.
The State of Software Supply Chain Security panel agreed that the focus of security teams has been too narrow to actually mitigate the complicated nature of the software supply chain — and that this focus must change to properly prevent supply chain attacks.
Software supply chain security: What’s next?
While the panelists agreed that there are clear gaps in the effort to secure the software supply chain, they also believe that software supply chain security has now come to the forefront of conversation among application security and security operations teams.
Carielli said that there is an “expansion of understanding the problem” and that “people are paying attention.” However, being aware of the issues at hand is different than knowing how to handle them, she emphasized.
“I’m not certain everyone knows how to defend against [software supply chain attacks].”
—Sandy Carielli, Forrester Research
Woods said that the old rule of security applies here: When the community learns how to best tackle one threat, a new threat suddenly emerges. Software supply chain attacks have captured the attention of the industry since SolarWinds, highlighted by the Federal Government putting it front and center in 2022. Now the industry is finally catching up, and learning how to handle the emerging software supply chain security problem.
Executive Order 14028: SBOMs and beyond
Taking the charge in mitigating the software problem, the U.S. Federal Government has created a “steady drumbeat” in securing the software supply chain, said Carielli. What started with the Biden Administration’s May 2021 Executive Order on Improving the Nation’s Cybersecurity (14028) was followed by a list of subsequent guidelines and mandates that have built policy around software supply chain security.
These policies have set a precedent for the expectations of software publishers, practitioners and consumers going forward. Specifically, the White House’s Office of Management and Budget released a memorandum (M-22-18) mandating that in 2023, any software provider in business with the Federal Government must self-attest to producing secure software.
Carielli said that while this mandate is not applicable to software development teams outside of the U.S., these new policies aimed at securing the software supply chain “provide a roadmap for enterprise and commercial companies [globally].”
Software Bills of Materials (SBOMs) are now being widely adopted, thanks to federal guidance. While not mandated specifically in M-22-18, the document does suggest that the best way for software teams to attest that their software is secure is by using an SBOM. SBOMs tell the story of what makes up a software product, acting as an essential first step in preventing software supply chain attacks.
While Carielli pointed out that SBOMs are not a “panacea,” being only the first step in an organization’s software security journey, Woods believes that the “mere presence” of an SBOM is beneficial, since it demonstrates an organization’s solid security posture while also holding all parties using the software accountable for its components.
These panelists agreed that as a result of the Federal Government taking charge in software supply chain security policy, the industry is now better equipped to follow best practices that can help to mitigate and prevent software supply chain attacks.
Step up your supply chain security efforts
The State of Software Supply Chain Security 2022-23, pointed out the many positive efforts that have been made to defend against and prevent supply chain attacks. Panelists also emphasized the progress the industry has made in trying to tackle this problem. However, security teams need to double down on efforts to continue securing the software supply chain.
With software development's complexity set to accelerate in 2023 and beyond, software supply chain security is a major concern for all organizations, and requires an end-to-end security approach, as noted in Supply Chain and the SOC: Why End-to-End Security is Key.
“Supply chains are the foundation of everything that comes after.”
—Beau Woods, Stratigos Security
[ See on-demand webinar: The State of Software Supply Chain Security ]
Keep learning
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








