
Welcome to the latest edition of The Week in Cybersecurity, which brings you the latest headlines from both the world and our team about the most pressing topics in cybersecurity. This week: fallout from another supply chain attack involving malicious npm modules. Also: Microsoft backtracks on a pledge to disable Office macros.
This Week’s Top Story
NPM removes malicious modules following report
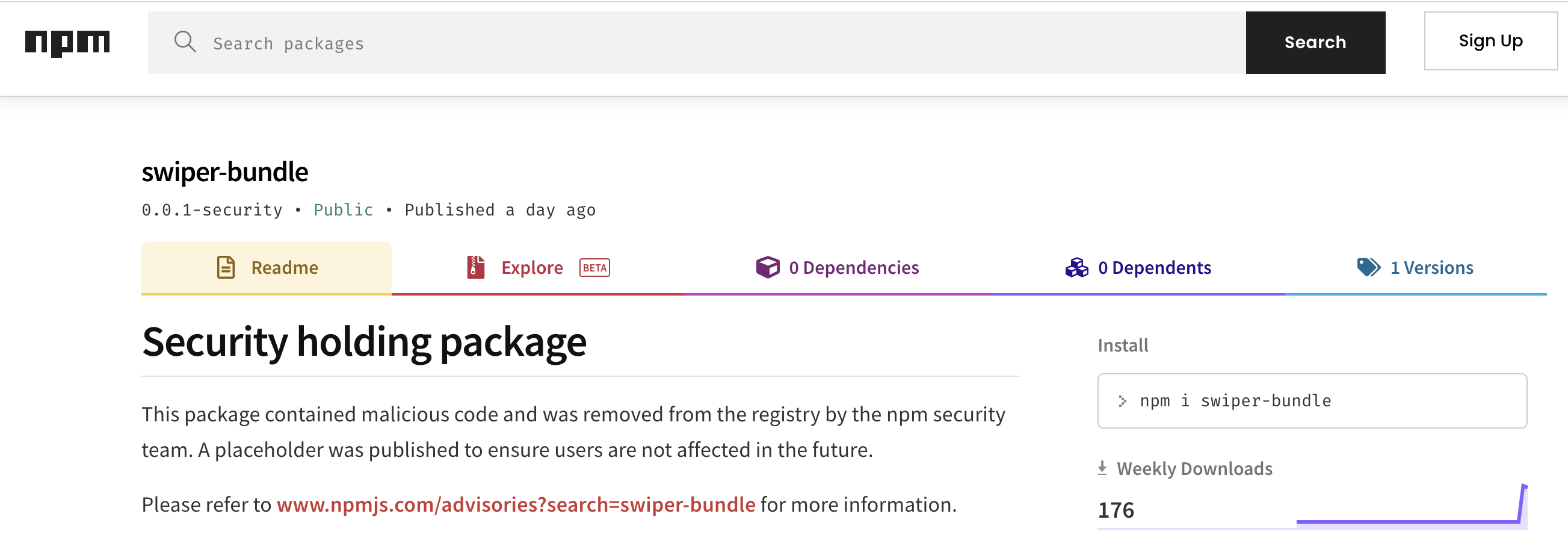
More than 30 malicious Javascript modules were removed from the NPM package repository on Thursday, days after a report by ReversingLabs identified dozens of NPM packages that contained code designed to siphon form data from applications and websites. The packages were replaced with "Security Holding Packages" and a message that the package contained "malicious code and was removed from the registry by the NPM security team."
The decision to take down the suspect packages follows a report by ReversingLabs detailing an extensive campaign, dubbed IconBurst, that seeded NPM with malicious packages, many of them lookalikes for popular, legitimate Javascript modules. ReversingLabs researcher Karlo Zanki identified the modules after noticing the presence of suspicious, obfuscated code in the modules - a rarity in open source packages published in a public repository. Analysis of the obfuscated code revealed it to be malicious and designed to harvest data from forms within applications that used the malicious packages. For example, a malicious NPM package dubbed swiper-bundIe mimicked the popular Javascript framework swiper, and used an embedded jQuery library, extending its end() function with functionality that gathered data from every form element on the page using the swiper-bundle module.
The incident is just the latest involving the NPM platform. Researchers at the firm Checkmarx said they discovered more than 1200 NPM packages linked to 1,000 different accounts that were part of an apparent crypto-mining experiment orchestrated by a malicious actor dubbed “CuteBoi." In May, ReversingLabs and researchers at the firm Snyk uncovered an apparent "dependency confusion" attack using malicious public packages squatting on the names of private NPM packages used by prominent German firms. (That attack was later revealed to be part of a benign "red team" exercise.) Earlier research by ReversingLabs identified a threat labeled Win32.Infostealer.Heuristics hidden in several versions of the nodejs_net_server NPM package.
News Roundup
Cybersecurity never sleeps. Here are the stories we’re paying attention to this week…
Microsoft backtracks on blocking Office macros by default
Microsoft received praise for its decision to begin disabling Office macros by default. But now the company is backtracking on that promise, according to a report by Bleeping Computer. The company announced in February that it would begin disabling macros by default in Excel, Word, Powerpoint and other Office documents. Research by ReversingLabs has shown that the use of macros in Excel documents, for example, has a high correlation with malicious behavior. The new default policy began being rolled out in April with general availability expected in June. However, Microsoft 365 users began noticing that warnings about the presence of macros had disappeared from Office, while features for editing and enabling macros restored. "Based on feedback received, a rollback has started. An update about the rollback is in progress," said Angela Robertson, a Principal GPM for Identity and Security on the Microsoft 365 Office team. The decision could have a big impact on Microsoft customers. Macros are commonly abused by ransomware groups such as Emotet, Qbot, Dridex, and others to gain a foothold on victims' networks. ReversingLabs researchers identified almost 160,000 files in the company’s TitaniumCloud that use Excel 4.0 (XLM) macros. On close inspection, more than 90% were classified as malicious or suspicious.(Bleeping Computer)
AstraLocker ransomware operators shut down their operations
AstraLocker ransomware operators told BleepingComputer they’re shutting down the operation and provided decryptors to the VirusTotal malware analysis platform. AstraLocker is based on the source code of the Babuk Locker (Babyk) ransomware that was leaked online on June 2021. (Security Affairs)
Google Patches Actively Exploited Chrome Bug
While people were celebrating the Fourth of July holiday in the United States, Google quietly rolled out a stable channel update for Chrome to patch an actively exploited zero-day vulnerability, the fourth such flaw the vendor has had to patch in its browser product so far this year. (Threatpost)
Pro-China Group Uses DragonBridge Campaign to Target Rare Earth Mining Companies
A pro-China influence campaign singled out rare earth mining companies in Australia, Canada, and the U.S. with negative messaging in an unsuccessful attempt to manipulate public discourse to China's benefit. (The Hacker News)
Hacker Claims Major Chinese Citizen's Data Theft
A hacker claiming to have stolen personal data from hundreds of millions of Chinese citizens is now selling the information online. A sample of 750,000 entries posted online by the hacker showed citizens' names, mobile phone numbers, national ID numbers, addresses, birthdays and police reports they had filed. (Security Week)
Germany Unveils Plan to Tackle Cyberattacks on Satellites
The German Federal Office for Information Security (BSI) has put out an IT baseline protection profile for space infrastructure amid concerns that attackers could turn their gaze skywards. (The Register)








