 See RL's Joshua Knox break down the Polyfill.io supply chain attack on YouTube.
See RL's Joshua Knox break down the Polyfill.io supply chain attack on YouTube.
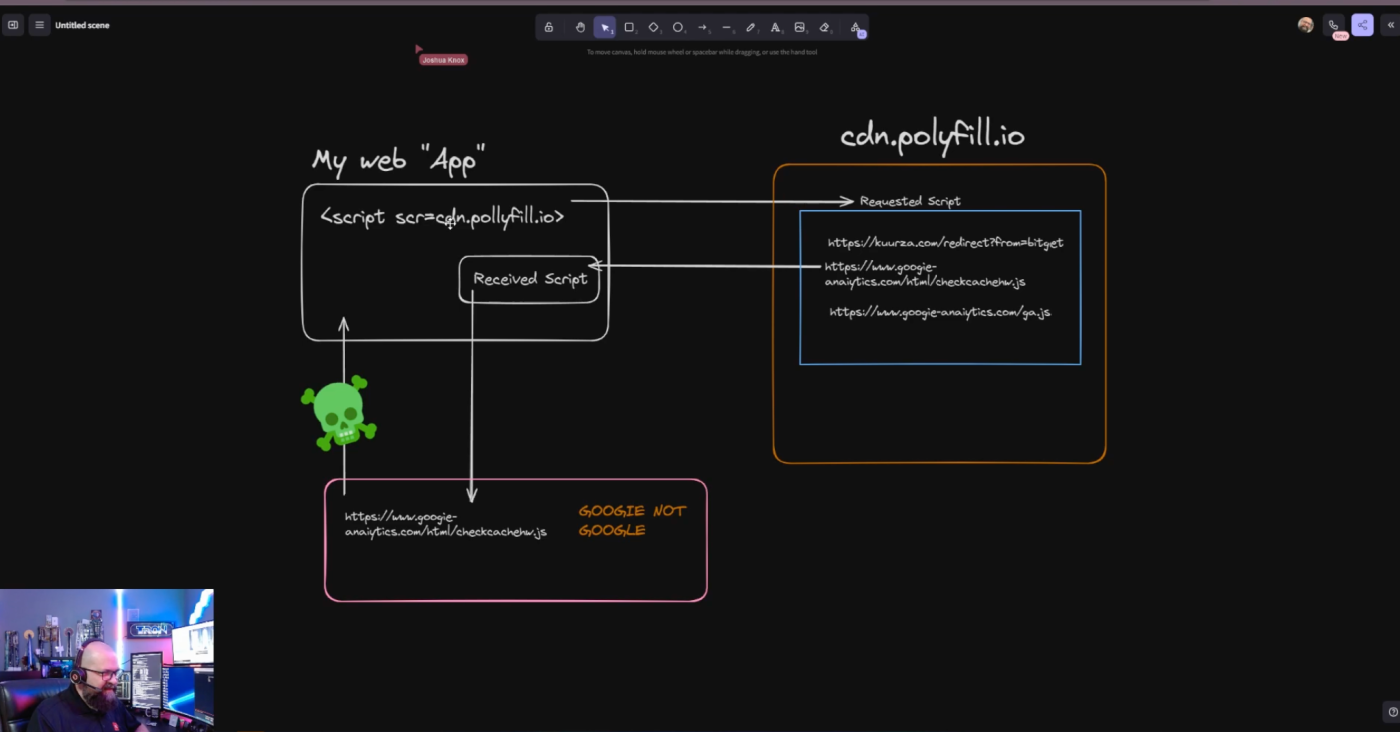
The cybersecurity firm Sansec this week disclosed a significant software supply chain attack that leveraged the content delivery network (CDN) Polyfill.io. The CDN, used by a countless number of websites, was pushing out malicious code and redirecting a significant number of Internet users to spam sites.
Polyfill.io was a community-run CDN service that was bought by Funnull, a Chinese company, in February. Researcher Andrew Betts, who originally developed Polyfill (but had no ownership of the domain, nor any say in its sale) shared a message on X (formerly Twitter) in late February stating: “If your website uses Polyfill.io, remove it IMMEDIATELY.” Funnull announced later that month it officially purchased the domain and its associated GitHub account.
Before the ownership change, Polyfill was used by countless sites that run modern code that isn’t supported by outdated web browsers. After Funnull acquired the domain, the CDN’s script was modified to introduce malicious functions, forcing impacted website maintainers to remove cdn.polyfill.io from their scripts. Despite the warnings and subsequent ownership change of the domain months ago, it wasn’t until this past week that the supply chain attack was identified.
Here's what we know about the Polyfill.io software supply chain attack — and key lessons learned.
[ See RL's new Spectra Assure Community: Free Portal Helps Devs Spot Malicious Open Source Packages ]
Inside the Polyfill vulnerability: What we know
Sansec warned that the Polyfill.io domain injects malware on mobile devices via any site that embeds the CDN. Indicators of Compromise (IoCs) for the attack also include typosquatted URLs, including one masquerading as Google Analytics.
Joshua Knox, Senior Cybersecurity Technologist and evangelist for ReversingLabs (RL), broke down the anatomy of this attack on the RL YouTube channel, noted in his explanation that the lessons of the Polyfill vulnerability are very similar to those raised by Log4Shell, the infamous Log4j open source vulnerability:
“In this case, this cdn.polyfill.io may be something that you're using on your website that you didn’t even know you're using.”
—Joshua Knox
In the case of Log4j, security teams were scrambling to figure out if they even had the vulnerable version of the open source file in their applications. Now, with Polyfill.io, website maintainers are similarly struggling to figure out if their web scripts are running the cdn.polyfill.io. Malicious activity will continue to occur until maintainers replace or remove the CDN.
Sansec also noted that when they tried to decode a malware sample introduced by Polyfill, they found that the code has specific protections against reverse engineering, and the malicious functions won’t be executed to the impacted device if an admin user is detected.
Next steps: Remediation and lessons learned
On the immediate remediation front, website maintainers are urged to review their scripts are calling on cdn.polyfill.io, and remove them immediately. Leak Signal, a cybersecurity firm, created a website (Polykill.io) that allows users to search for sites that use the impacted CDN —and outlines alternatives for those who need to replace it.
The key takeaway from this latest supply chain attack is that security teams need to be vigilant about all third-party services — trust is key. To understand how this attack unfolded, learn how the attack is unique from other landmark software supply chain attacks — and to learn more lessons — see Joshua Knox’s video breaking it down using RL Spectra Analyze on our YouTube channel:
Keep learning
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








