Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
This year’s AWS re:Invent conference leaned heavily into the transformational change in cloud computing, with keynotes on generative AI and distributed machine learning, among others. This is unsurprising as we enter 2025, with AWS environments are becoming increasingly complex.
This complexity brings a unique set of security challenges that traditional solutions simply can't address. Whether it is managing a massive S3 data lake, orchestrating intricate CI/CD pipelines, or safeguarding sensitive data across multiple AWS services, your security needs are evolving — and so must your security strategy.
Here's what you need to know about the challenges of securing complex AWS environments — and how to employ modern tooling to tackle these challenges in 2025.
One of the most common challenges AWS users face is securing S3 buckets. Organizations must manage multiple buckets across different business units and protect data across development, staging, and production environments. All this is in an environment where malicious actors are hunting for vulnerable S3 configurations.
Another critical area is CI/CD pipeline security. With tools like AWS CodeBuild, ensuring the security of public and private repositories, securing artifacts throughout the build process, and integrating security into existing DevOps workflows without slowing down deployments is essential.
In recent years, numerous high-profile data breaches have occurred due to misconfigured S3 buckets. Some notable examples include:
These incidents highlight the critical importance of securing S3 buckets and implementing robust security measures. By following best practices and utilizing advanced security solutions like Spectra Analyze, organizations can significantly reduce the risk of data breaches and protect their sensitive information.
Many organizations have already benefited from these solutions. For example, a Fortune 500 ReversingLabs customer uses Spectra Analyze to secure thousands of S3 buckets, process petabytes of data, maintain compliance across regions, and enable secure cross-region replication. They have been able to more rapidly identify and quarantine malicious packages attempting to be uploaded into their environment before they can cause harm.
A FinTech ReversingLabs customer enhanced its AWS CI/CD security by scanning code artifacts, protecting container images, and securing third-party dependencies. All of this is done without compromising deployment velocity.
To address these challenges, ReversingLabs offers a suite of advanced security solutions specifically designed for AWS environments. They include:
Spectra Analyze: This powerful solution provides advanced S3 protection by natively integrating with AWS S3, leveraging Lambda-based processing for efficient scanning, and directly integrating with AWS security tools and IMAP and SMTP email services. It also supports AWS Organizations and multi-account structures, ensuring comprehensive security across your entire AWS environment.
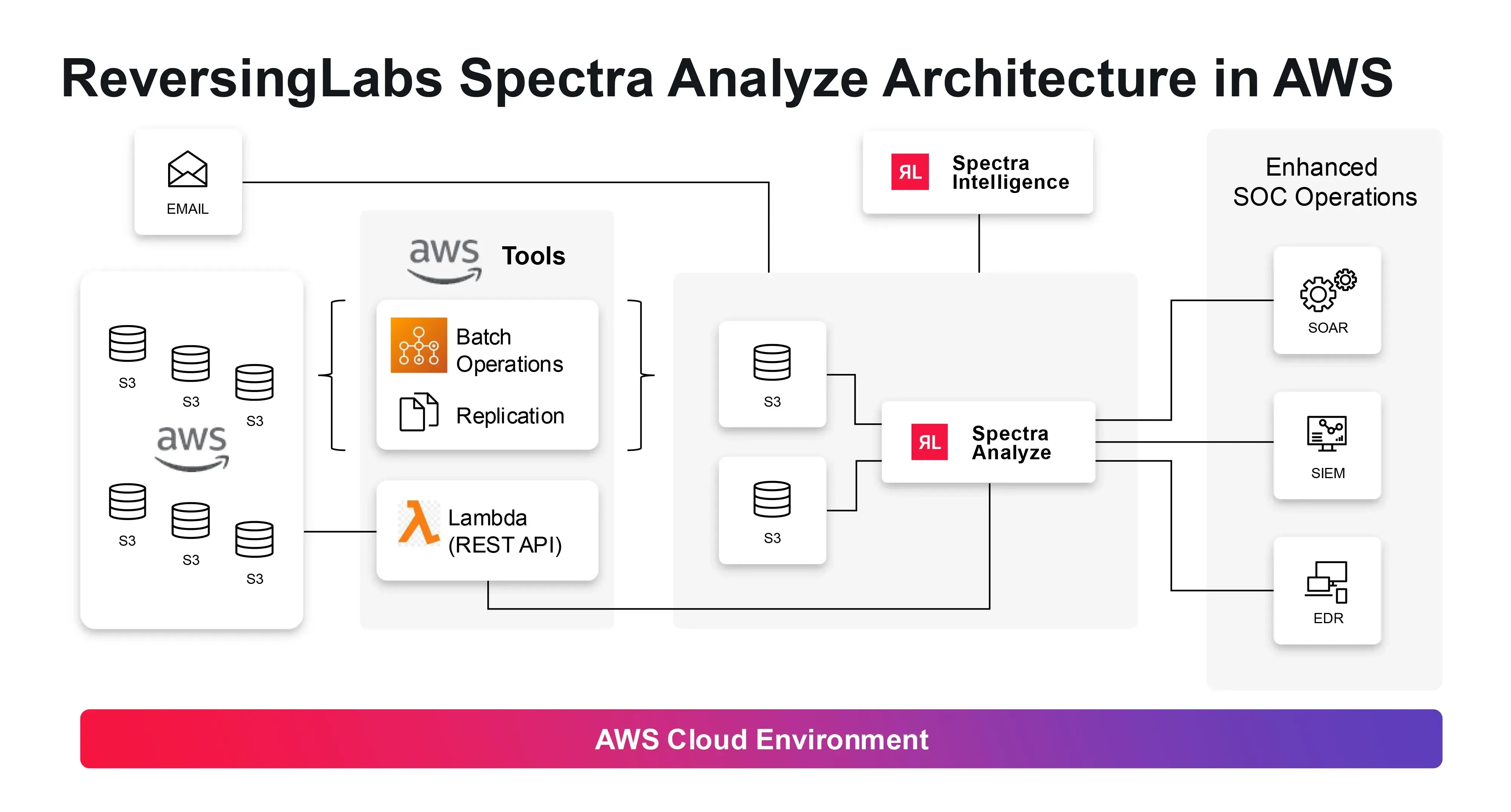
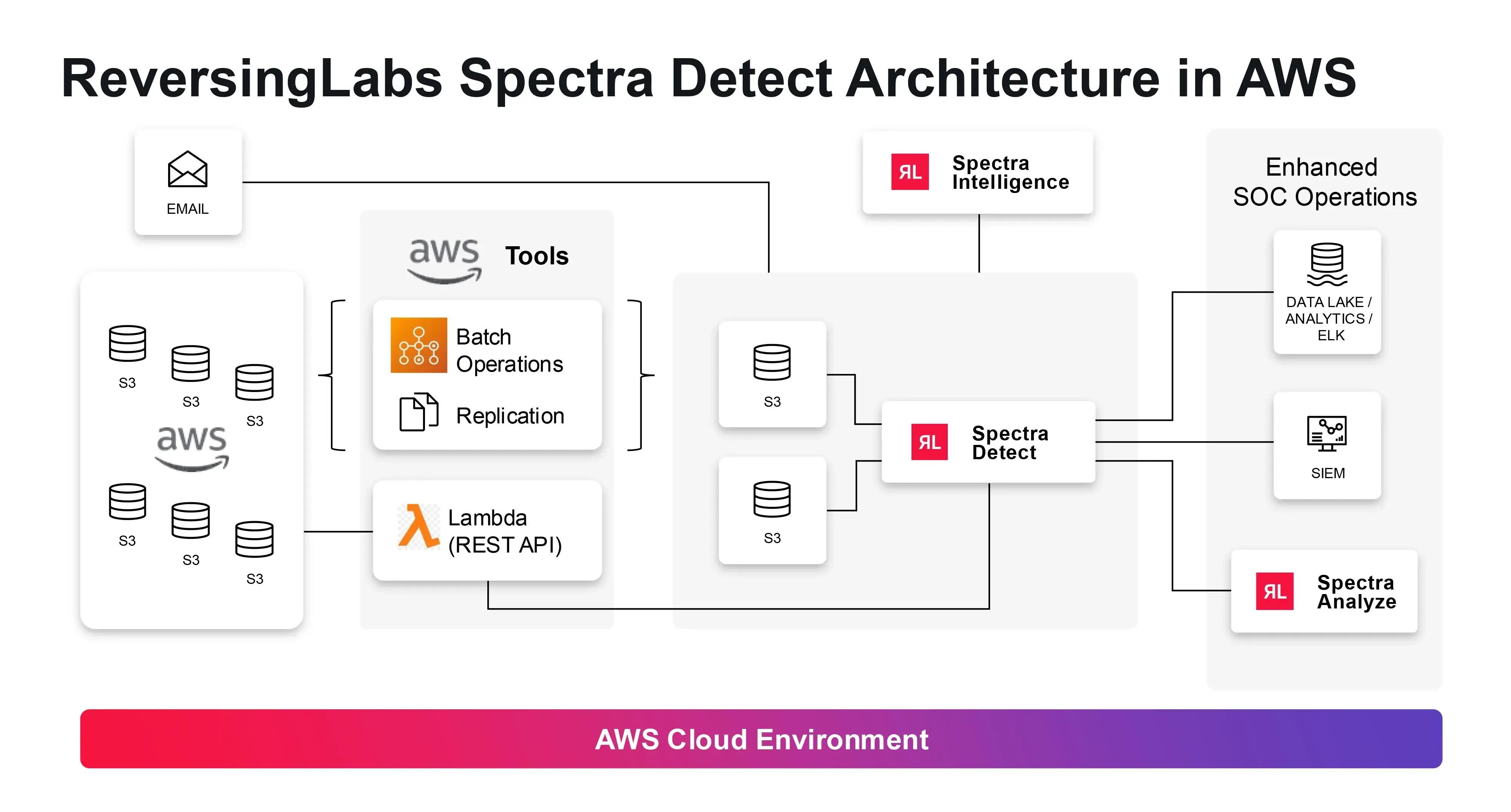
Spectra Detect: This solution is purpose-built for threat detection in AWS environments. It integrates seamlessly with AWS data lakes and analytics, provides real-time monitoring of S3 events and Lambda functions, offers advanced threat detection across various AWS services at scale, and directly integrates with SIEM tools and data lake analytics for comprehensive visibility.
Spectra Assure: Easily integrated into AWS CodeBuild environments, this tool automates security scanning in CI/CD pipelines, integrates with AWS artifact management, supports AWS CodePipeline workflows, and enforces security policies for AWS deployments.
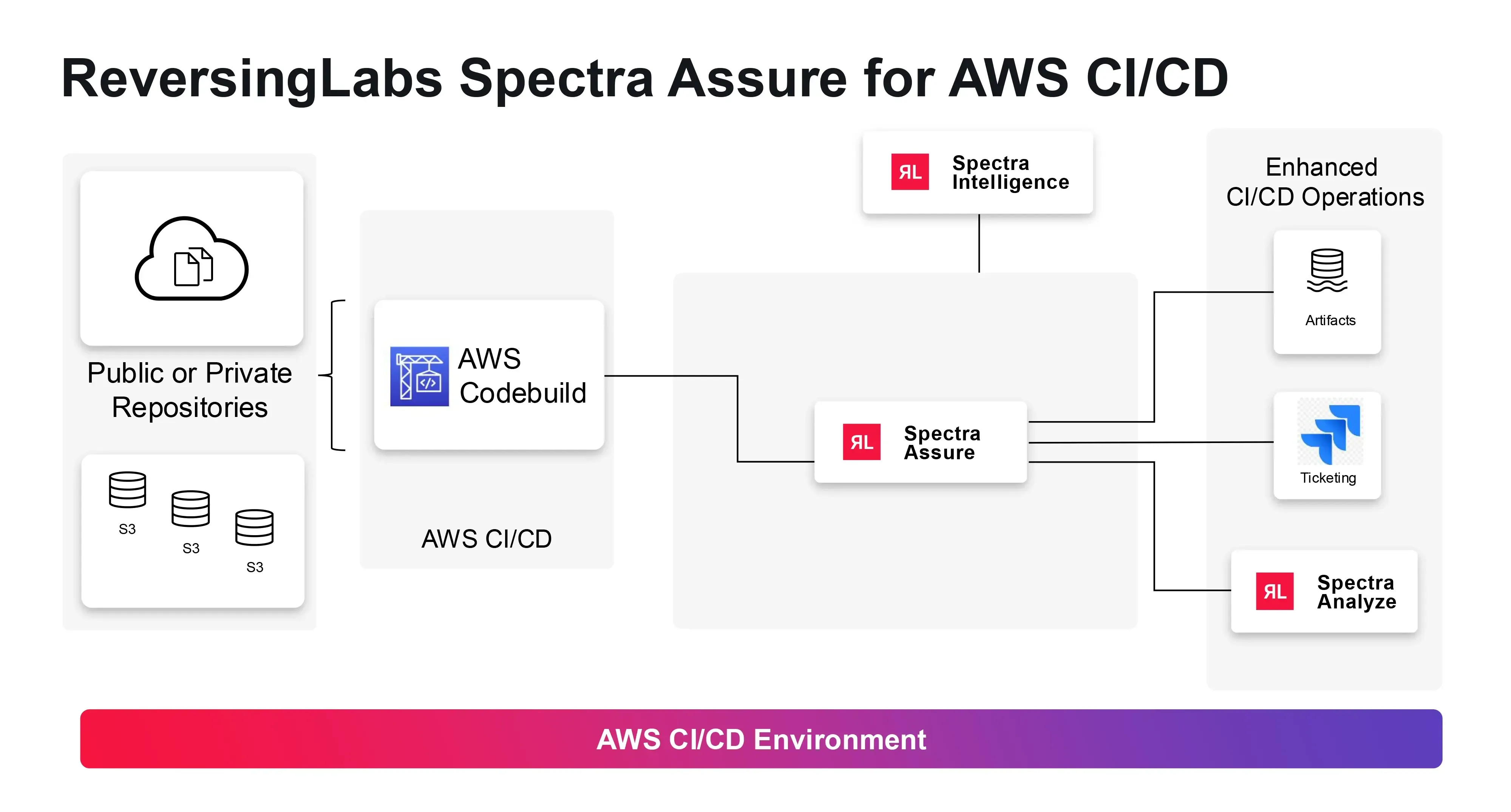
To effectively implement these solutions, a solid architectural foundation is crucial. This involves seamlessly integrating with S3 buckets, utilizing Lambda-based processing for efficient scanning and resource management, and leveraging AWS tools like Security Hub, CloudWatch, and Organizations.
To maximize the benefits of these solutions and strengthen your overall AWS security posture, consider the following best practices:
As AWS continues to evolve, so too must security solutions. ReversingLabs' suite of tools offers a comprehensive security framework that scales with your AWS workloads, supports new AWS services, maintains security best practices, and enables business innovation.
By embracing these advanced security solutions and following best practices, you can effectively address the evolving security challenges in your AWS environment and protect your organization's critical assets.
To learn more about how ReversingLabs can support a more secure AWS environment, visit us on AWS Marketplace, or schedule a time with one of our experts.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial