Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
As the primary investigation console within ReversingLabs Titanium Platform, the A1000 provides authoritative file-level intelligence which is often lacking in security operations, yet desperately needed by Security Analysts, Incident Responders, and Threat Hunters to respond faster, pivot quickly, and resolve incidents expeditiously.
Our new Dashboard summarizes the organization’s overall security posture as well as the productivity and effectiveness of the SOC team. This is represented in key metrics including the number of files analyzed, number of threats identified and their uniqueness to the environment, top malware families investigated broken down by type, and all extracted network observables. And for any given point in time, this information can be exported to a PDF report so SOC teams can showcase the value of their ReversingLabs investment to peers and management.

Figure 1: New A1000 Dashboard
Our new Timeline Analysis panel in the Dashboard presents a perspective into malware dwell times, and how a local A1000 can analyze files and provide visibility into unique threats before global threat databases. Analysts can show how many threats have targeted their organization and gone undetected by others; tangible proof of value in their investment in ReversingLabs.
Interpreting this threat landscape view is simple- everything left of the red vertical bar (labelled Same Day) shows times where A1000 has identified threats before others, indicative of threats potentially unique to your organization. In this case, 545 samples submitted to the A1000 were given a malicious verdict and have never been seen before across global threat databases. Those to the right are indicative of files less unique, in circulation and previously harvested elsewhere and already classified in global databases such as TitaniumCloud. End result: analysts can accelerate their MTTD (mean time to detect) because they can identify threats locally in their environment sooner than later.
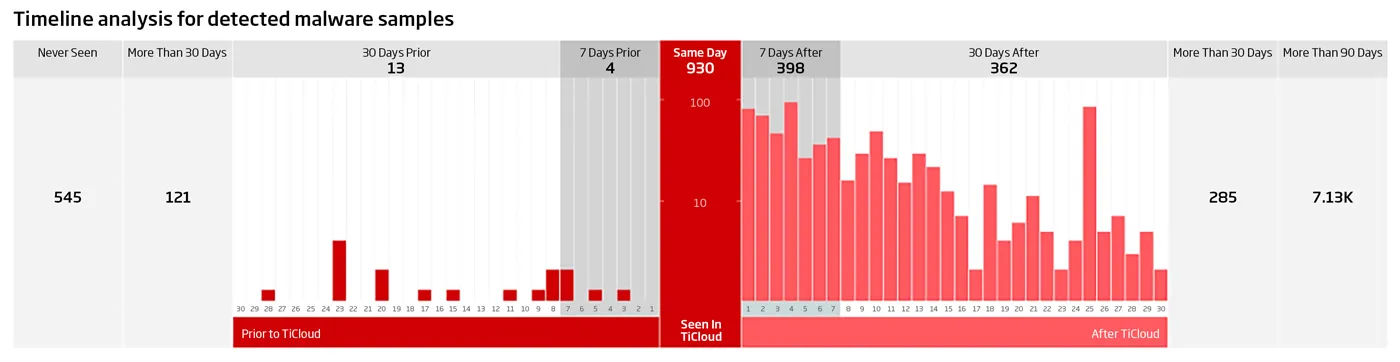
Figure 2: New Timeline Analysis Chart
Intelligence gathered by extracting URIs from malicious samples can accelerate your investigations and help provide an understanding of the full extent of your organization’s exposure to threats delivered over the Internet. By giving security analysts the ability to export these network-based observables from their A1000 to other security tools such as a SIEM, this information can be leveraged to search for other hosts or machines having visited these URLs, and could be potentially compromised. Applying this exported report of network observables against additional datasets comprising host and computer activity puts analysts in a position to identify additional compromises and understand the full extent of their exposure.
Now what’s even more interesting is applying this same information to enable other security defenses such as firewall, web/email gateway, IPS, and EPP/EDR solutions to establish more proactive alerting and blocking at other protection points. Combining this proactive stance with the A1000’s ability to incorporate insights to functionally similar files supports analysts in defending their organization and shutting down as many attack vectors as possible. Consider the potential of defending against attacks yet-to-come based on proactively addressing functionally similar malware based on malware that had previously penetrated your security defenses.
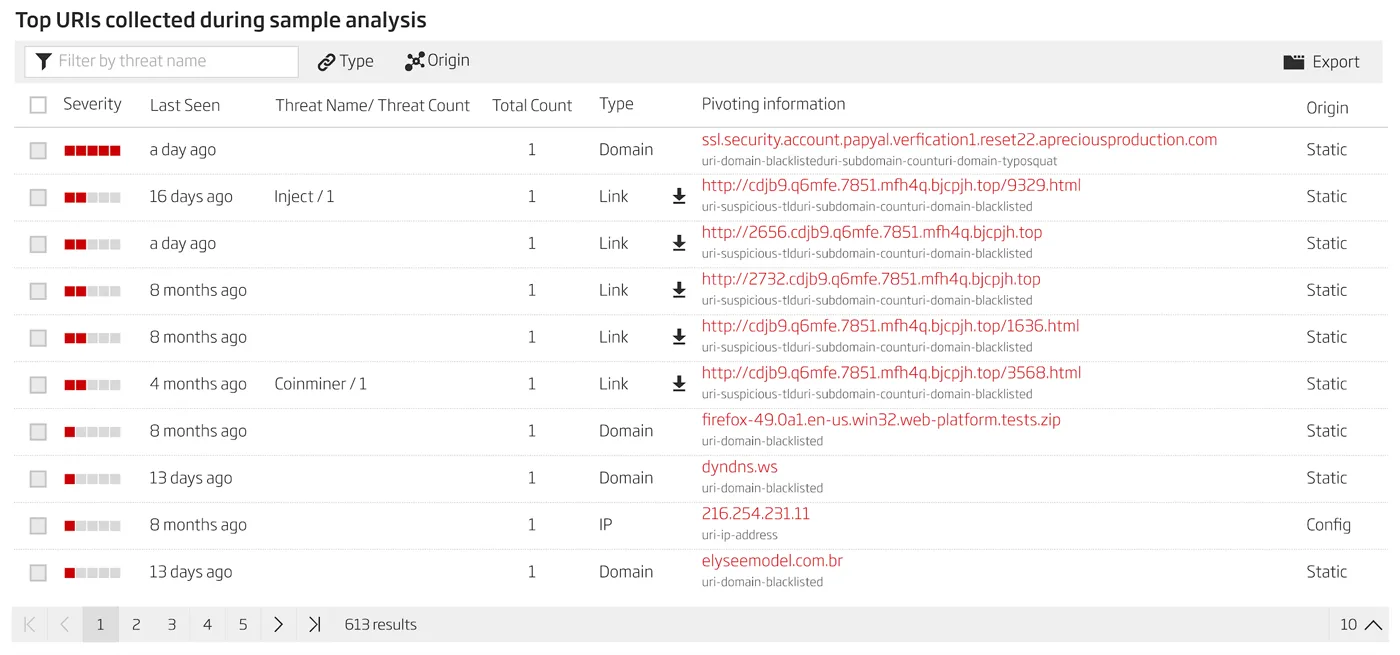
Figure 3: A1000 Network Observables
The A1000 supports the submission of files, hashes, and now URLs. The new URL submission capability accelerates investigations into multi-stage attacks delivered over the Internet, reduces the challenges of gathering samples, and quickly dispositions URLs delivering malicious payloads. And all this can be done without relying solely on expensive sandbox clusters and the subsequent cost of manually analyzing file behaviors. When given suspicious URLs, the A1000 can automatically go out to the Internet and associated network resources, download suspicious samples associated with the host, and analyze through static analysis and additional reputational insights from ReversingLabs TitaniumCloud- all on behalf of the analyst. And this analysis will deliver valuable information for SOC staff including the name of the threat (based on collection of AV providers inputs), severity, the number of files extracted from the threat object or file, which AVs detected, as well as the time when file was last seen, first seen, and first seen locally.

Figure 4: A1000 File and URL Submission
A new A1000 utility allows SOC analysts to configure and administer select connections to active file shares enabling ReversingLabs to continuously monitor for threats as their organizations digital attack surface expands, and alert security teams when malware is detected or when changes in disposition occur. File Shares can include collaboration use cases where employees, contractors, partners and customers are sharing files; disaster recovery use cases where these files are elevated to business critical status in cases of catastrophic events; trusted software distribution use cases where organizations need to validate the integrity of published software before being deployed to endpoints; and software supply chain use cases where engineering teams check in and out code from repositories. File shares may include on-premises or cloud shares including SMB shares, Microsoft SharePoint, OneDrive, Google Drive, Box, Dropbox, Amazon S3, etc.

Figure 5: A1000 File Share Connector Configuration
The A1000 provides a new level of configurability that enables analysts to remain within the product console they prefer by bringing together static and dynamic analysis (sandbox). They now have the most comprehensive set of network and host indicators of compromise and observables in one console, benefiting from having a key subset of sandbox data accessible in the A1000, and this data could very likely be sourced from multiple sandbox providers. Analysts now have a consolidated view of static and dynamic analysis information, with the capability to search and pivot with greater context across a single data source. And all this can be done by remaining in the ReversingLabs solution which speeds triage, simplifies analysis, and optimizes decision support.

Figure 6: A1000 Sandbox Connector Configuration
To meet enterprise policy and production best practices, the A1000 supports new password authentication policies including parameters such as password strength and session duration/rotation.

Figure 7: A1000 Password Policy Configuration
The A1000, analyst investigation solution supports advanced hunting and investigations through high-speed automated static analysis, detecting threats before the rest of the industry. We’re excited by many of the new capabilities and enhancements, and the ongoing roadmap to address new use cases and analyst usability. As part of the Titanium Platform, the A1000 is integrated with ReversingLabs cloud-based file reputation services to provide in-depth rich context and threat classification on over 10 billion files. The A1000 supports an analysis workbench for visualization, APIs for integration with automated workflows, a dedicated database for malware search, global and local YARA rules matching for retro hunting, alert subscription and management, as well as integration with third-party sandbox tools.
To request a Demo of these new capabilities, click here.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial