Microsoft Sentinel is revolutionizing the SIEM market by simplifying the process of deploying and monitoring cloud and on-premises environments for security issues. However, operators face a drawback as Microsoft Sentinel gives them a blank slate, causing new users to question which alerts and content they should install.
ReversingLabs has created a content pack to help address this question for new and existing users of Microsoft Sentinel. The content pack provides Microsoft Sentinel users with example content that works with ReversingLabs TitaniumCloud to tackle malware-related threats and bolster threat intelligence implementations.
Microsoft Sentinel enables partners and third parties to provide additional content via the content hub, where users can install pre-packaged solutions containing playbooks, analytic rules, and more. Here's an overview of the content pack, and how to realize the provided benefits fully.
[ See Free Trial on Azure Marketplace: ReversingLabs Enrichment APIs For Sentinel | Learn More: ReversingLabs Threat Intelligence for Microsoft Sentinel ]
Solution overview
The ReversingLabs content pack is a free download that contains content relating to threat intelligence and file enrichment. There are currently two playbooks designed to work with ReversingLabs TitaniumCloud, and one workbook that provides valuable metrics on threat intelligence and security operations within Microsoft Sentinel. The solution is designed for security operations teams just starting with Microsoft Sentinel and ReversingLabs, or mature teams that want more out of their Microsoft Sentinel experience.
SOAR playbooks for SOC efficiency
Automating manual tasks is critical to ensuring a successful security operations team. To help Microsoft Sentinel users get started with automation and ReversingLabs, a set of example playbooks are included in the content pack. Currently, the content pack contains two playbooks, and both require valid TitaniumCloud credentials.
This video created by ReversingLabs covers installing and configuring these playbooks:
Automate file enrichment
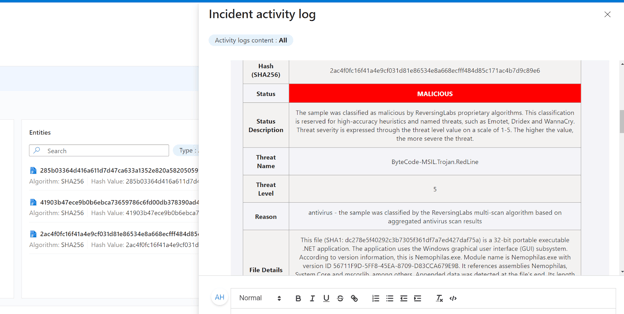
The ReversingLabs-EnrichFileHash playbook enriches file hash entities associated with Microsoft Sentinel incidents with data from ReversingLabs TitaniumCloud. SOC analysts benefit from extracting and formatting rich information from TitaniumCloud's repository of billions of files, enabling faster and more accurate alert triage by providing them with additional context. This analysis includes a classification value and plain-language details about the file. Use this as-is to add context to a Microsoft Sentinel incident or expand on this by automating incident closure for benign file hashes or escalating into deeper workflows for malicious file hashes.
Track API usage
The ReversingLabs-CheckQuota playbook queries the ReversingLabs TitaniumCloud user quota API to check current limits. Data from this playbook is added to a custom log analytics table and visually represented in the workbook described in the next section. This playbook can be set to run regularly or triggered manually from the workbook.
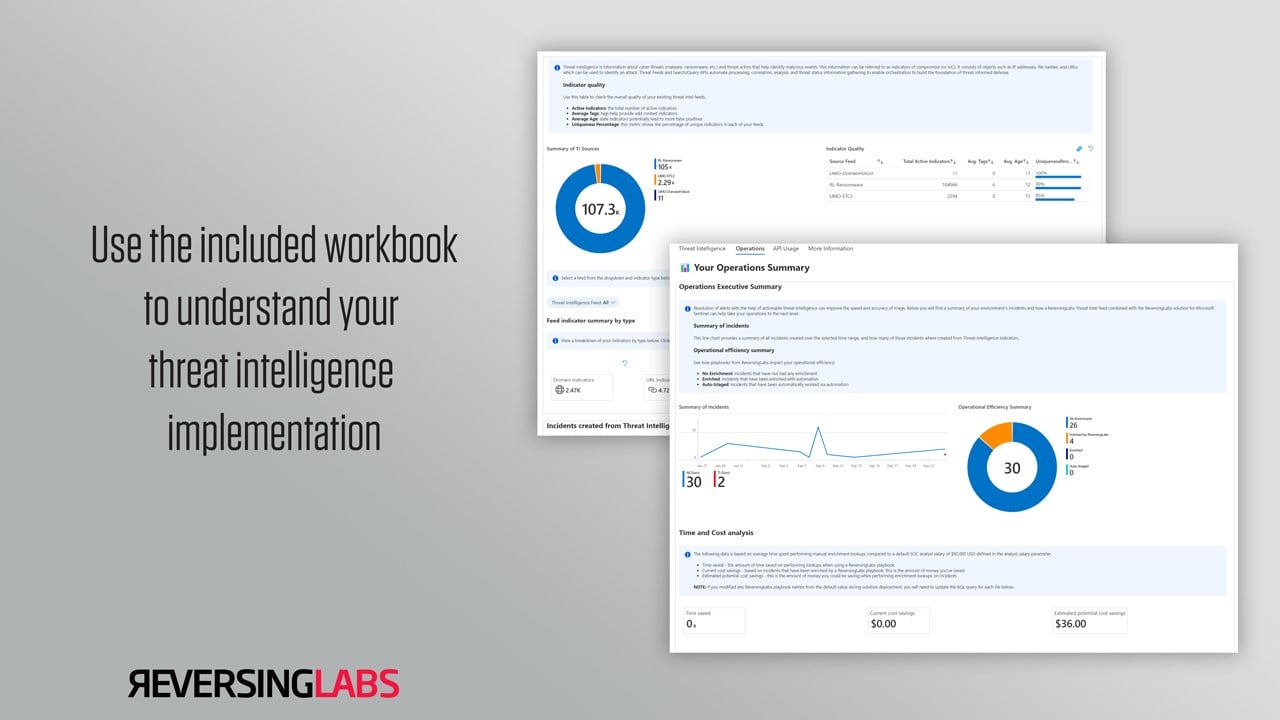
Workbook to visualize value
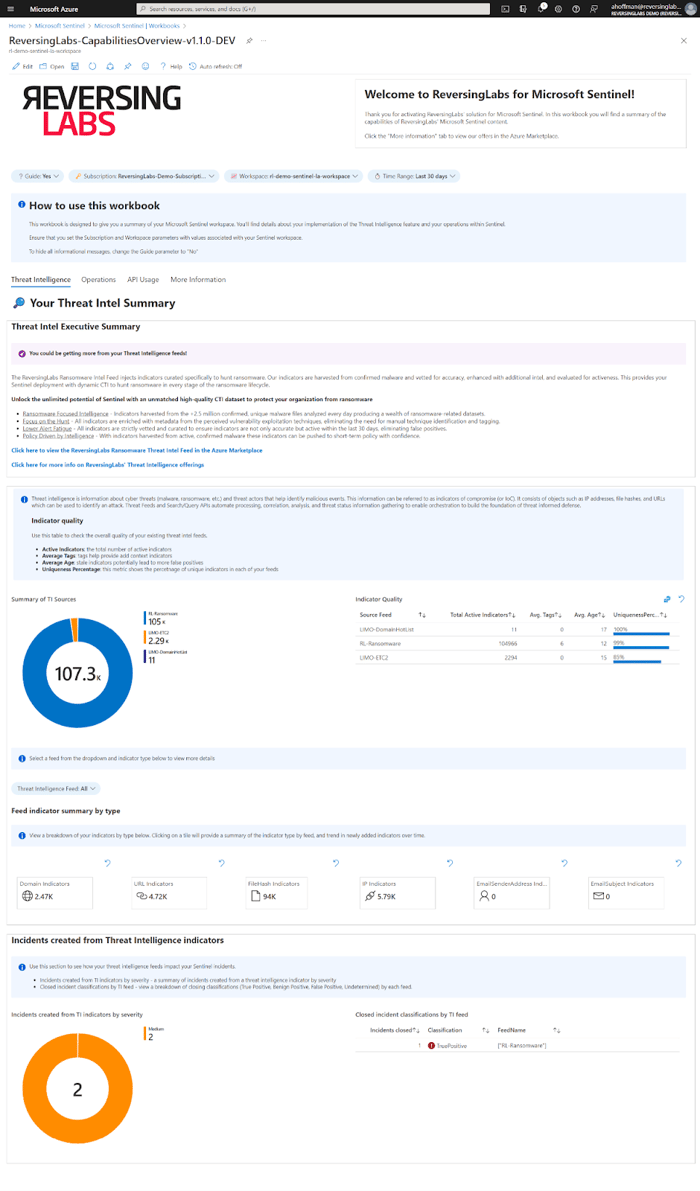
The included Microsoft Sentinel workbook provides an overview of the threat intelligence implementation within Microsoft Sentinel and has a dashboard to monitor ReversingLabs TitaniumCloud API usage. This workbook is designed for all teams of all levels, whether it’s a team just getting started with threat intelligence and ReversingLabs or mature organizations with defined processes.
Threat intelligence summary
The threat intelligence summary tab is your one-stop shop to guide your implementation of threat intelligence within Microsoft Sentinel. This tab provides a breakdown of indicators based on type. In addition, an “indicator quality” table shows critical metrics about your threat intelligence indicator feeds, such as indicator uniqueness, number of tags, and average age. This table should help you understand the value of your indicator feeds, where a “good” indicator feed is highly unique, has relevant context, and has new indicators.
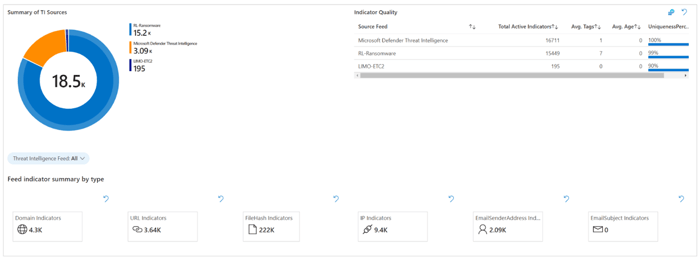
Understanding the specifics of your indicator feeds is only one aspect of their value; the accurate measure lies in their impact on your security operations. The latter portion of this tab offers an overview of the Microsoft Sentinel incidents associated with indicators from your indicator feeds. It summarizes the total number of resolved incidents based on the closing classification for each threat feed. This feature helps identify whether any specific threat intelligence feed tends to produce false positives.
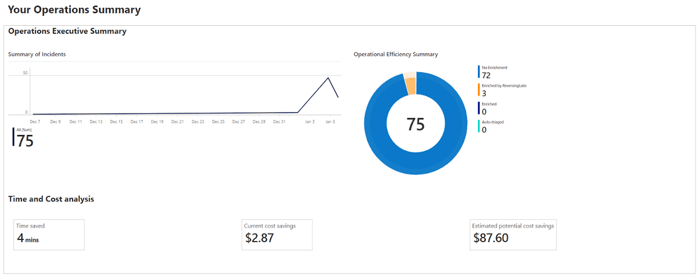
Operations summary
The operations tab within Microsoft Sentinel actively presents an overview of your security operations, showcasing the impact of threat intelligence and content from ReversingLabs. This tab offers a concise breakdown of incidents automated by a ReversingLabs playbook and provides a time and cost analysis, demonstrating the enhanced efficiency of these playbooks. The resulting estimate is derived from a typical SOC analyst's salary and estimates the time saved by automating manual actions.
The SOC analyst salary value is fully adjustable by opening the workbook editor and changing the “analyst_salary” parameter value.
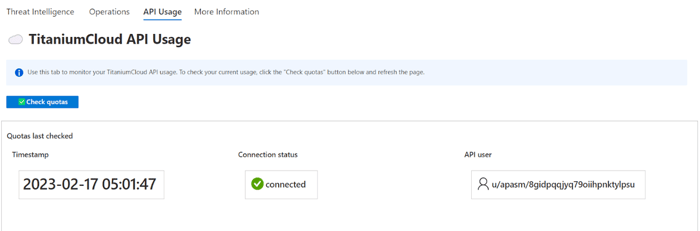
API usage
The final tab in Microsoft Sentinel offers a dashboard that visually presents the usage of the TitaniumCloud API. This tab facilitates understanding of the number of queries sent to the API and provides information about the API user configured in Sentinel playbooks, among other details. It is worth noting that the utilization of this tab requires the presence of the ReversingLabs-CheckQuota playbook.
What’s next?
ReversingLabs is constantly working on adding integrations that benefit Microsoft users. Keep an eye out for additional playbooks developed for Microsoft Sentinel. If you are an existing ReversingLabs customer looking for a specific feature that could enhance your Microsoft security operations, drop us a line at support@reversinglabs.com.
[ Sign up to get the Sentinel Threat Intelligence Briefing newsletter delivered weekly ]
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








