Our customers rely on ReversingLabs A1000 Threat Analysis and Hunting Solution to provide an instant malware lab, delivering static and dynamic analysis. Here, we break down the newest improvements to this necessary solution.
Improvements to A1000 that drive security operations forward
At ReversingLabs, we constantly work to improve our clients' security solutions. That’s why we are pleased to announce the availability of Version 8.3 of our A1000 Malware Analysis Platform. Alongside addressing customer requests, we are delivering improvements with the introduction of the Relationships Graph, an improved Search page, and the delivery of a Sandbox verdict.
New and improved features in A1000 Version 8.3 include:
• Relationships Graph (New)
• Merge Submissions to Search (New)
• Option to Enable Sandbox Verdict to File Classification (New)
• Improvements to RL Cloud Sandbox
Here are the essential updates to A1000 8.3 that will aid enterprise security operations centers (SOCs) as they defend their organizations against today’s most pressing cyber threats.
Introducing: The Relationships Graph
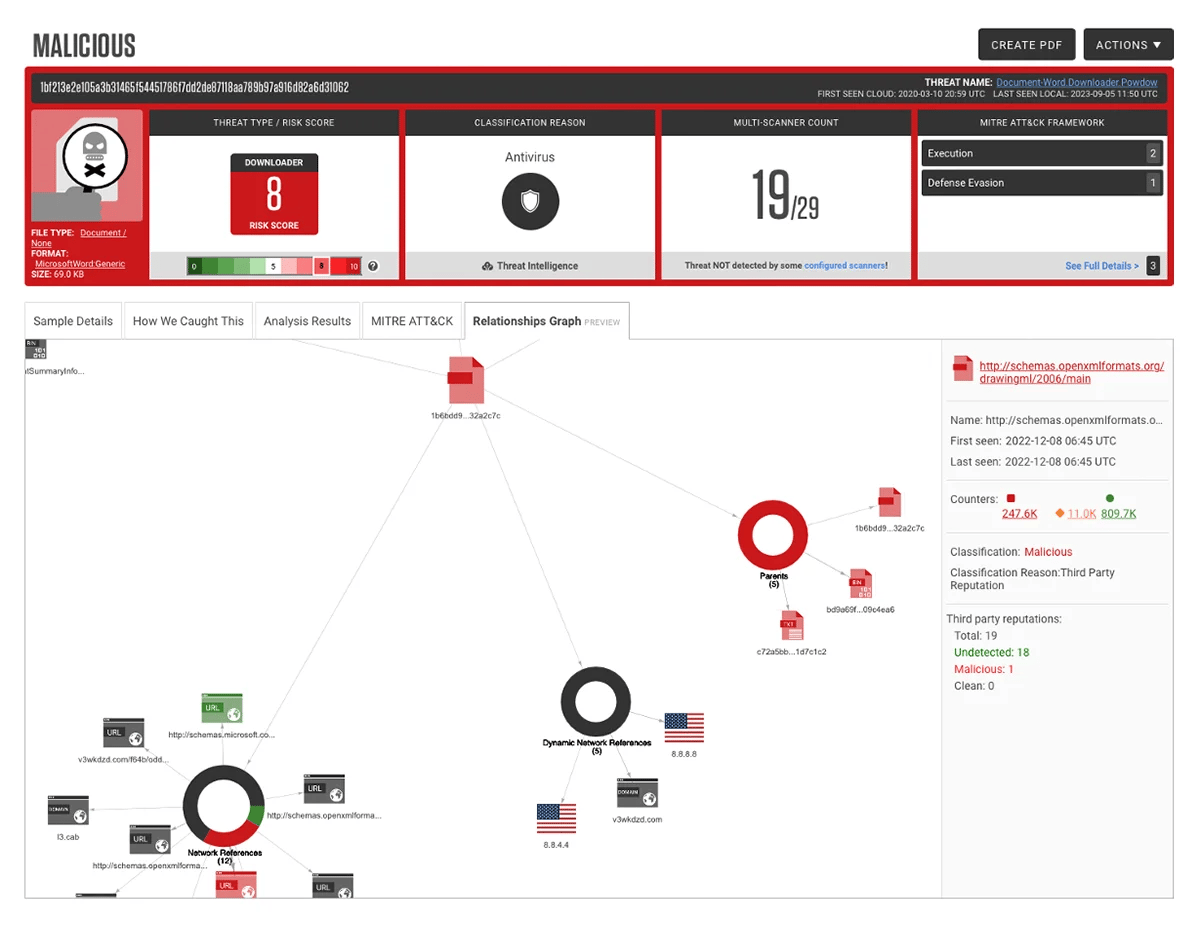
Image 1: A display of the new Relationships Graph in the A1000 platform
For enterprise SOCs, having a visual understanding of a sample and its related network data and files, is essential. An accurate, straightforward visual depiction of all relevant metadata can quickly summarize what is at stake, making threat analysis more intuitive.
This is what can be expected in the newest version of the A1000 platform with the Relationships Graph feature, as seen in Image 1. With the new feature, the enterprise SOC can preview any interesting files and network references extracted from a specific sample using a simple graphical overview. Relationships Graph is a node-based overview generated using RL’s proprietary algorithms. For the enterprise SOC, this delivers usability and better triage productivity.
The Relationships Graph can be used on any kind of sample, such as extracted, dropped, parent, or network connection files. This new feature is also one that we will continue to improve for even greater insights into the samples most relevant to the work of the SOC.
Merging Submissions To Search
Image 2: A visual representation of the Submissions feature being added to Search
To better clarify how to best use the Search feature and differentiate the Search from the Submissions feature, the newest version of RL’s A1000 solution has merged the Submissions view into the Search, removing the Submissions section from the navigation menu. This merger will create less confusion and offer a more practical view of the Search feature for the enterprise SOC.
With this improvement, users will now have a central page for all samples, regardless of if they are submitted to the platform locally or if the user would like to access samples from the entire RL malware repository via Titanium Cloud. This change to the Search feature will in turn, increase triage productivity, better search workflow, and enable workflow efficacy for the busy enterprise SOC.
Including a Sandbox Verdict in the File Classification
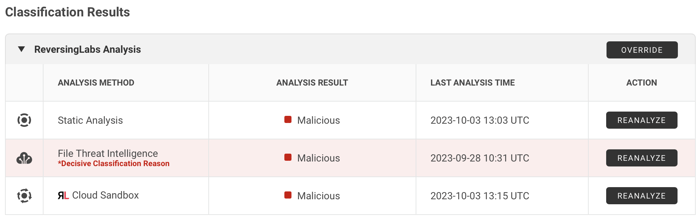
Image 3: An example of File Classification results
File classifications should yield the results the enterprise SOC needs to make informed triaging decisions. The newest version of the A1000 delivers results from running a file through the RL Cloud Sandbox will be included in official file classifications. As can be seen in Image 3, the RL Cloud Sandbox has been listed as an “Analysis Method” alongside Static Analysis and File Threat Intelligence within the File Classification.
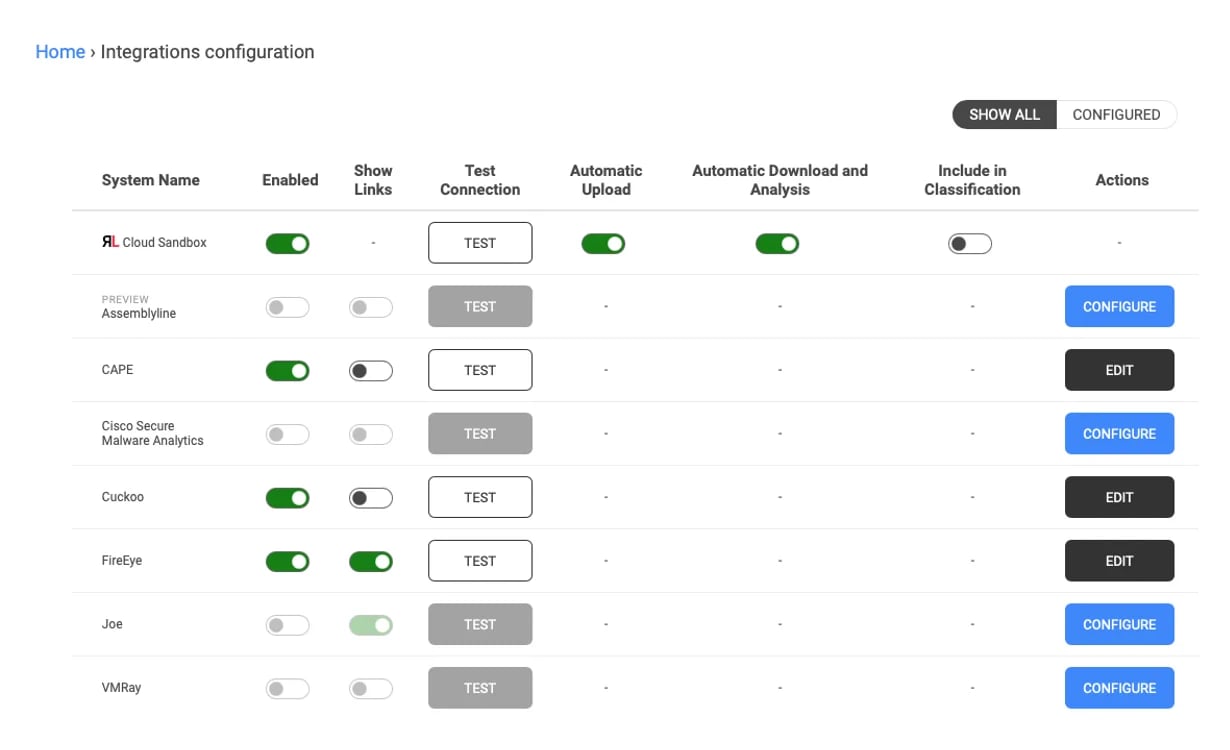
Image 4: Display of how users can enable the inclusion of the RL Cloud Sandbox into their file classifications
For users that choose to enable the new RL Cloud Sandbox view (as can be seen in Image 4 above), teams will be delivered file classifications that will simply display whether the file is malicious or not based on the full RL metadata obtained from both the static and dynamic analysis of the file. This will allow the enterprise SOC to make more informed decisions regarding mitigation with the added view of the file’s dynamic analysis.
This new feature of the A1000’s file classification feature will bring many benefits to enterprise SOCs, such as increased triage productivity, a better workflow for the dynamic analysis of files, along with greater uniformity for improved decision-making.
RL Cloud Sandbox Improvements
The RL Cloud Sandbox feature within the A1000 platform yields important dynamic analysis results for the enterprise SOC. That’s why we made several improvements that will continue to power the SOC’s decision and mitigation efforts. Here are two of them:
Addition of a Risk Score
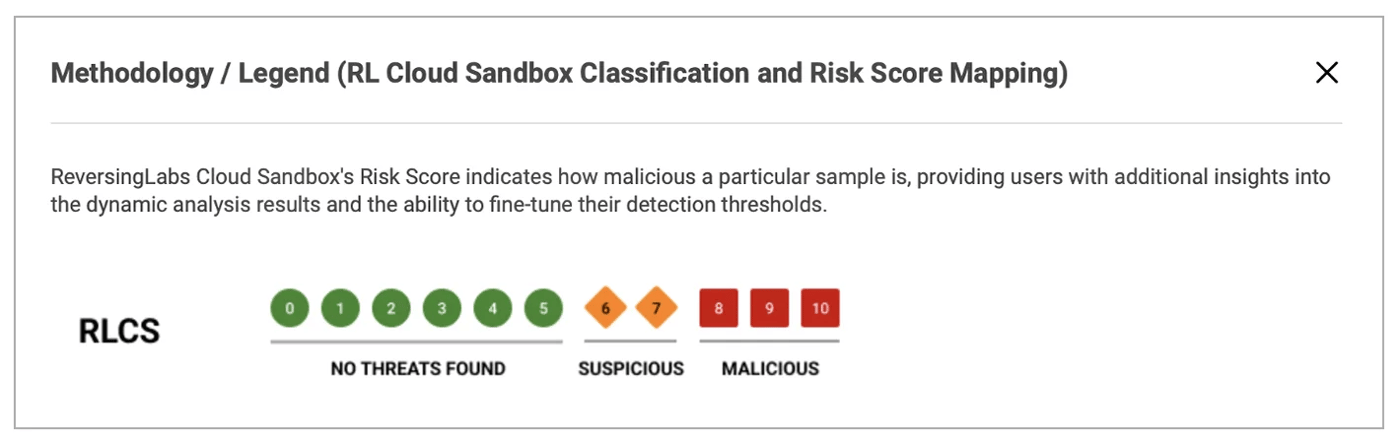
Image 5: The number scale for the RL Cloud Sandbox Classification and Risk Score Mapping
In the newest version of RL’s A1000 platform, users can run a file through the RL Cloud Sandbox and receive a Risk Score for it. As can be seen in Image 5, the RL Cloud Sandbox Risk Score will fall between zero and 10, with 10 being the most malicious, and zero being the least. This new scoring will give the user a quick view into how malicious a sample is, and will provide additional insights into the dynamic analysis results of a sample.
In addition to the new Risk Score, users can fine-tune their detection thresholds to make the scoring system more applicable to their team’s work and needs. And once a Risk Score has been generated, it will be added to the RL Cloud Sandbox’s sample summary, PDF report, and the full API report.
URL Network Data and Threat Intelligence Reputation
Improvements to the RL Cloud Sandbox also include enhanced URL analysis. Part of this enhancement is URL Network metadata, which extends network metadata for all URLs extracted during dynamic analysis, as well as their sources. This gives the enterprise SOC a comprehensive view of a URL’s security that is based on both static and dynamic analysis.
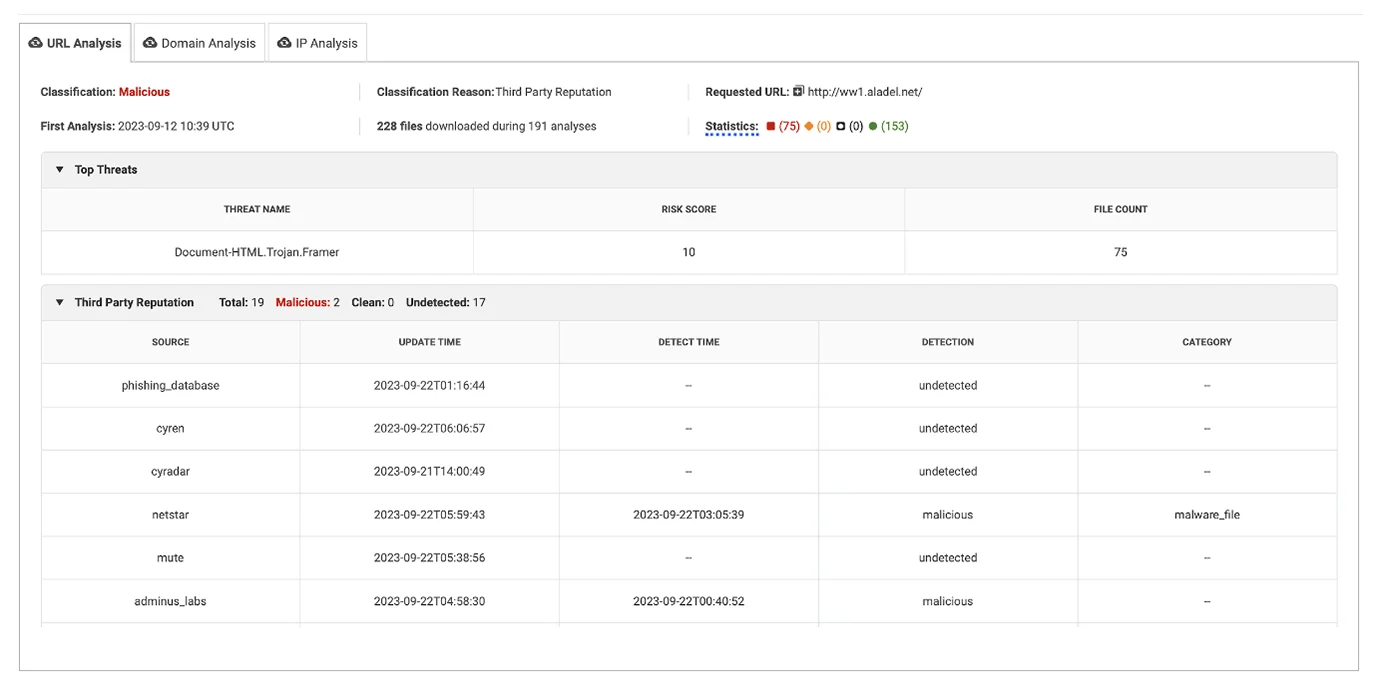
Image 6: View of the enriched URL Network Threat Intelligence section
In addition to the enhancement of network metadata, the Threat Intelligence section of the URL analysis was enriched with classification reason and category. This update offers the user more insight into why a given URL may be malicious.
These enhancements to the A1000’s URL Analysis will be available to users via the URL Sample Summary, the PDF report, the Network Threat Intelligence API, and the full report of the API.
More Sandbox Improvements
In addition to the newest version of the RL Cloud Sandbox having an added Risk Score and enhanced URL analysis, Sandbox improvements with v.8.3 include the following:
- Download and analyze dropped files from dynamic analysis to static analysis, allowing seamless pivoting between the two.
- Linux has been added as a major platform that can be supported by RL Cloud Sandbox, in addition to Windows and macOS.
- Dynamic Signatures (Findings) that provide more descriptive explanations of all processes started during dynamic detonation using a set of pre-defined signatures, all detected and classified by the Sandbox
The ReversingLabs solution
The ReversingLabs A1000 Threat Analysis and Hunting solution presents customers with an immediate malware lab equipped with static and dynamic analysis capabilities for all files and binaries within your company. The ReversingLabs A1000 Threat Analysis and Hunting Solution seamlessly integrates with ReversingLabs file reputation services, offering comprehensive context and threat classification. It encompasses features such as visualization, automated workflows through APIs, global and local YARA rules matching, and integration with third-party sandbox tools.
The analysis outcomes are aligned with the industry-standard MITRE ATT&CK framework to enhance usability and facilitate correlation with other security solutions. This contextual information empowers analysts to defend against global and targeted attacks effectively, expediting investigations and response efforts.
The ReversingLabs Threat Analysis and Hunting Solution aims to deliver value to our customers through various avenues. We minimize cyber risks and safeguard data and file privacy, contributing to the success of our businesses. Practitioners benefit from our advanced technology, which shortens the Mean Time to Detection (MTtD) and prioritizes malicious files for immediate attention and analysis.
Delivering beyond customers’ expectations
It is clear to us at ReversingLabs that there is no true limit to improving solutions for our customers. This is the driving factor of our continued development of ReversingLabs A1000 Threat Analysis and Hunting Solution, enabling organizations to have robust programs to mitigate today’s most serious malware threats.
Updates made to the most recent version of the ReversingLabs A1000 Threat Analysis and Hunting platform, such as the Relationships Graph, the merger of Submission to the Search, and the inclusion of a final Sandbox verdict, will benefit our customers and the mission of ReversingLabs. It’s also important to note that these major updates are just some of the key features that have been made to our Threat Analysis and Hunting solution.
About ReversingLabs
At ReversingLabs, we are providing the world’s largest threat intelligence repository to protect software development and power advanced security solutions, keeping the most advanced cybersecurity organizations and Fortune 500 enterprises informed and ahead of the threats. Our software supply chain security and threat intelligence solutions have become essential to advancing enterprise cybersecurity maturity globally.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.







