
Newly discovered open source software packages on the npm platform contain scripts that broadcast peace messages related to ongoing conflicts in Ukraine and on the Gaza Strip when they are deployed, according to research conducted by ReversingLabs.
The packages are just the latest examples of so-called “protestware,” a recurrent issue in the open source software ecosystem in which application developers conceal political messages inside open source code, often designing it to display to the user after an application is installed or when it is executed.
Although the latest packages are not malicious, they underscore a persistent risk in open source software, in which unintended and malicious features can lurk undetected — even in widely used applications.
Protest package for Palestine
The npm package e2eakarev, version: 7.1.0, published in late October, describes itself as a “free Palestine protest package” and was posted by the npm user ~updater.downloader. It has a total of 8 downloads. ReversingLabs researcher Lucija Valentić found that installing the package launches a postinstall script, index.js, which checks to see if the package is being launched in Israel. If it is, an English language message calling for peace is displayed in the terminal.
“The world has witnessed too much suffering in Palestine, and it is time for us to take a stand,” the message reads in part. It calls on those reading the message to raise awareness of the “Palestinian struggle,” donate to humanitarian aid and back the “Boycott, Divest, Sanction" (BDS) movement, which seeks to encourage individuals and businesses to divest from Israel.
The message is signed “The Anonymous Protester.” And that… is about it. The package was not observed to perform any other actions — malicious or not, Valentić said.
Protestware: Sneaky!
Another npm package that was found recently to contain protestware is @snyk/sweater-comb, version 2.1.1, which was first published in August, 2023 by the firm Snyk. Sweater-comb is described as a “tool which provides guardrails with automation” of Snyk APIs by applying custom Optic CI rules to Snyk's OpenAPI specifications. Version 2.1.1 includes the module es5-ext, ECMAScript 5 extensions, a common module with more than 7.3 million weekly downloads. This is the last version of the Snyk package that includes the es5-ext module, with protestware functionality. All package versions since have opted out from using it as a dependency.
What does this protestware do? After installation, es5-ext launches a postinstall script, _postinstall.js, which attempts to determine the geographic location of the host. If the host machine is located in Russia, it shows a message, in Russian, that is critical of Russia's invasion of neighboring Ukraine, and in Russian when the package is installed in Russia.
“The whole world condemned the unjustified invasion and decided to impose unprecedented sanctions against Russia,” it reads. “With each new day they will be felt stronger and stronger among civilians.” Russian speakers reading the message are encouraged to download the Tor browser, and visit a web page on how to circumvent censorship in the country.
As it turns out, es5-ext is a package with a long history. The firm Checkmarx reported on it in March 2022, noting that the protestware feature was added to the es5-ext package in early March of that year, shortly after Russia invaded Ukraine. The same report also highlighted another module, styled-components, that was likewise updated to include a post-install script that offered pro-Ukraine protest messages.
ReversingLabs researchers have subsequently found the es5-ext used in other popular applications, including the installation executable for Signal Messenger for Windows. With about 10 million weekly downloads, the reach of the es5-ext package is broad. Within developer forums, the issue of the protestware features frequently crops up, as developers utilizing the es5-ext module contend with antivirus programs flagging their wares as infected with a virus.
Since July 2023, ReversingLabs detected 179 npm packages using the es5-ext package (a count that includes every version of each npm package). That isn’t a huge number. However, that list includes many legitimate packages like sweater-comb, Signal and version 6.4.0 of the shut framework with substantial distributions and user bases.
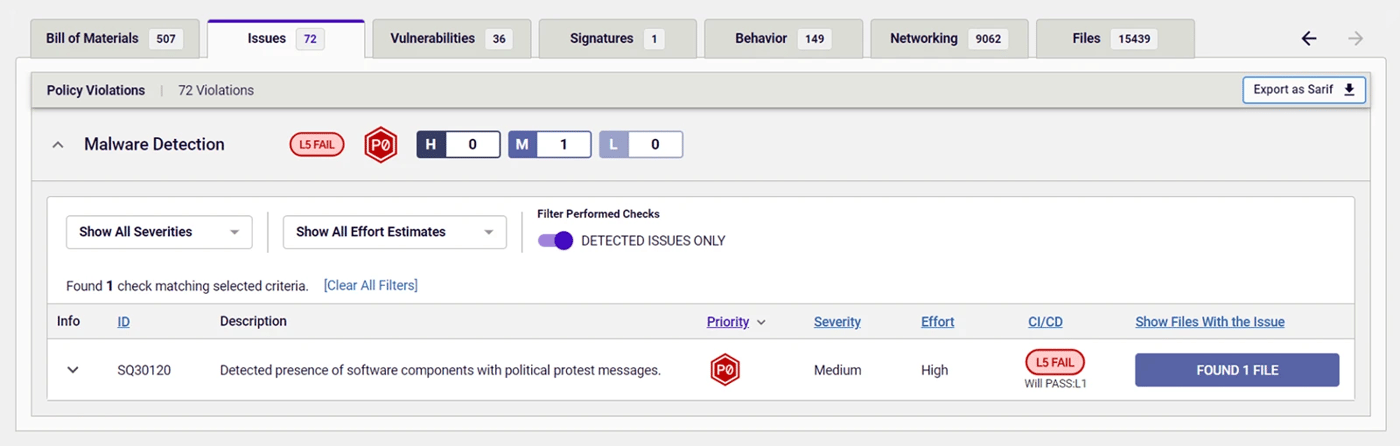
Figure 1: ReversingLabs’ report for Signal Messenger Windows installation executable showing the presence of protestware
That is concerning, because even though the postinstall script displaying the pro-Ukraine message isn’t malicious, it is unneeded.
“The problem is that this package is doing more than it advertises. It not only extends es5 with extra methods and shims, it also implements a "Call for peace" message. I think it's an unacceptable practice that slows done [sic] installation process,” a developer with the handle Rush commented on GitHub.
And that’s a problem. The ability of sketchy and unnecessary code like the latest protestware in es5-ext to work its way into widely used and legitimate applications and platforms like Signal, the shut framework and sweater-comb suggests that the cyber risks lurking in software supply chains are real.
Righteous? Yes. Malicious? Maybe.
Both of the examples of protestware cited above were just that: software that is used to convey a message of protest. ReversingLabs did not observe malicious functionality designed to disrupt the systems running the protestware, steal sensitive information or engage in lateral movement in either case.
However, not all protestware is benign. In the immediate aftermath of Russia’s invasion of Ukraine in February 2022, for example, an update to the vue-cli open source module was updated to include functionality that identified systems running in Russia and then wiped them of sensitive files and information.
As violent conflicts crop up around the globe, expect more instances of protestware that takes up the cause of both innocent victims and warring parties. In some cases, that protestware may come in the form of updates to benign and even well-established modules. A certain percentage of it will cross the line from benign display messages to actually inflicting damage on targeted systems.
Dig deep on package security
The lesson for organizations is that the days of whistling past the graveyard when it comes to software supply chain threats is over. Developers inclined to make hasty conclusions about the security or integrity of any piece of software based on its past performance, age or popularity are setting themselves up to be disappointed, said Tomislav Peričin, the co-founder and Chief Software Architect for ReversingLabs.
“We have seen an increase in the number of software supply chain attacks, impactful vulnerabilities, and other incidents. The risks that developers and software consumers face have never been higher, and that includes political messages. Having software perform random acts of political activism does little for the specific cause. But it does decrease the private sector’s already shaky trust in software."
—Tomislav Peričin
If you’re lucky, that disappointment may come in the form of a postinstall script throwing up an unexpected appeal for peace. At the worst, the protest may take the form of a wiped system, stolen data or a fast-spreading worm.
The presence of political protest messages in open source code is just one more indicator of the need for development organizations to dig deeper into the function and integrity of the open source, as well as third-party and proprietary code they rely on. Postinstall scripts like the ones found in e2eakarev and es5-ext may not cause damage, but they are often an indication of the willingness of the package developers to use their code as a platform for their own words, actions and ideas. When that happens without adequate disclosure to the users of the module (as was the case with es5-ext), it is cause for concern and additional scrutiny for any development organization.
ReversingLabs is constantly hunting for suspicious package behaviors. Our Software Supply Chain Security platform uses behavior indicators that can track if packages have postinstall scripts, allowing us to spot protest packages like e2eakarev and es5-ext and determine whether they are benign, malicious or somewhere in between. That kind of scrutiny of software dependencies is increasingly important as both malicious and political actors look to software supply chains to make their presence felt.
Next steps
As the discovery of these latest examples of protestware indicate, development and application security teams need the ability to peer deeper inside software packages and distinguish malicious functions from legitimate ones.
This can be challenging with legacy application security testing tools, and demands specialized skills and knowledge that many organizations lack. Modern tools like ReversingLabs Software Supply Chain Security can bridge the gaps, and help development and application security teams protect their supply chain from compromise.
Indicators of Compromise (IoC)
The following IoCs were collected as part of ReversingLabs researchers' investigation of the e2eakarev and sweater-comb/es5-ex protestware packages.
| package_name | version | SHA1 |
| e2eakarev | 7.1.0 | a509f299c5a76ac0c91f9bfdd333cc367ce17dfa |
| sweater-comb | 2.1.1 | b76ec90d7e1ae59b108b62ee8f8979a98b99da28 |
Keep learning
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








