Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Vulnerability reports to MITRE’s Vulnerabilities and Exposures (CVE) list, part of NIST’s National Vulnerability Database (NVD), are accelerating. New vulnerabilities in the first half of 2022 outstripped the same period in 2021. At the current rate, more than 24,000 vulnerabilities will be added to the NVD this year — breaking last year’s record of slightly more than 20,000.
But the NVD as it is today does not tell the full story of software risk. The new report NVD Analysis 2022: A Call to Action on Software Supply Chain Security finds that the jump in vulnerabilities in recent years is likely to continue, for two key reasons:
Seen in the context of the rise in software supply chain attacks, the growth in reports to the NVD suggest that the focus of malicious actors is shifting. And yet, the NVD is still dominated by flaws in a handful of legacy platforms by firms including Microsoft, Red Hat, Google, Apple and Oracle.
These factors form a call to action for NIST. The NVD is a critical resource for both software development and security organizations. To remain relevant, NIST should expand the NVD in two ways:
Here are five key takeaways from the NVD Analysis report.
Get special report: NVD Analysis 2022: A Call to Action on Software Supply Chain Security
Top software makers were the leaders in NVD reported vulnerabilities. Linux led the pack with more than 2,000 flaws found in two distributions of the operating system — Fedora with 1,123 and Debian with 958. Google, Microsoft, Oracle, and Apple all had more than 500 vulnerabilities each. Although more than 3,500 vendors reported vulnerabilities to MITRE Corp’s Vulnerabilities and Exposures (CVE) list, part of the National Institute of Standards and Technology’s (NIST) National Vulnerability Database (NVD), a third of all flaws were found in the software of the top 20 vendors.
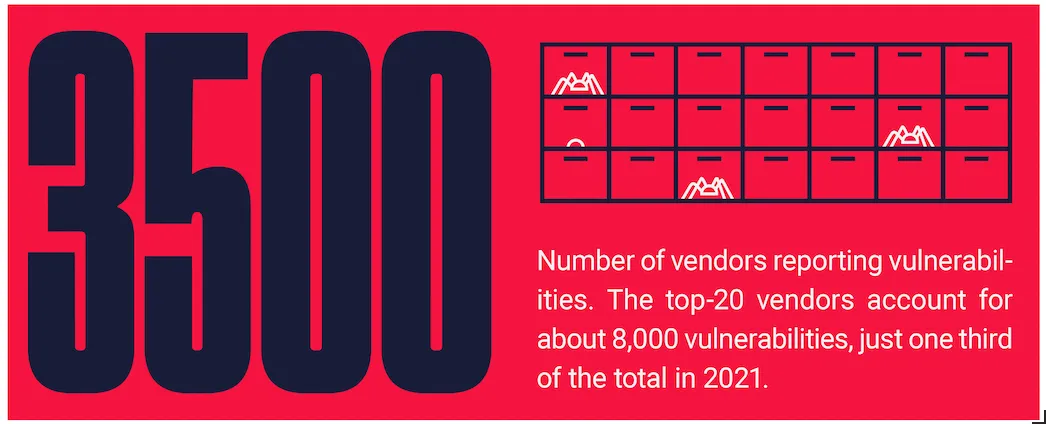
For some time, security firms have maintained that vulnerability growth is being driven by greater risks. In fact, much of the growth is being fueled by MITRE's expansion of reporting authorities to some 3,500. That can be seen in the marked jump in reported vulnerabilities from 2016 (6,649) to 2017 (14,644), when MITRE invited more organizations into the reporting fold.
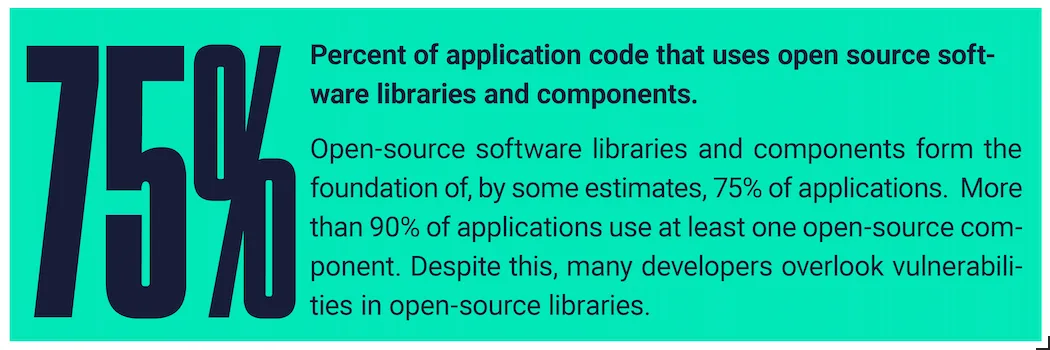
While the number of reporting authorities has leveled off, expansion in other areas will contribute to continued growth in reported vulnerabilities. For example, more countries and companies will start to participate in the CVE program. In addition, more projects — especially open-source projects — will be covered by the existing reporting authorities. More than 75% of code today uses open source, and 90% use at least one open source component.
What's more, the move to impose more rigorous measures on software supply chains will lead NIST and MITRE to expand the CVE program to cover the wide variety of open-source projects on which web applications, internet infrastructure, and commercial software rely.
Historically, vulnerability hunters have focused their attention on standalone applications and operating systems. Now that focus has shifted from applications running on desktops, laptops, and servers to finding vulnerabilities in web applications, API servers, and mobile devices, as well as the software components used to develop them.
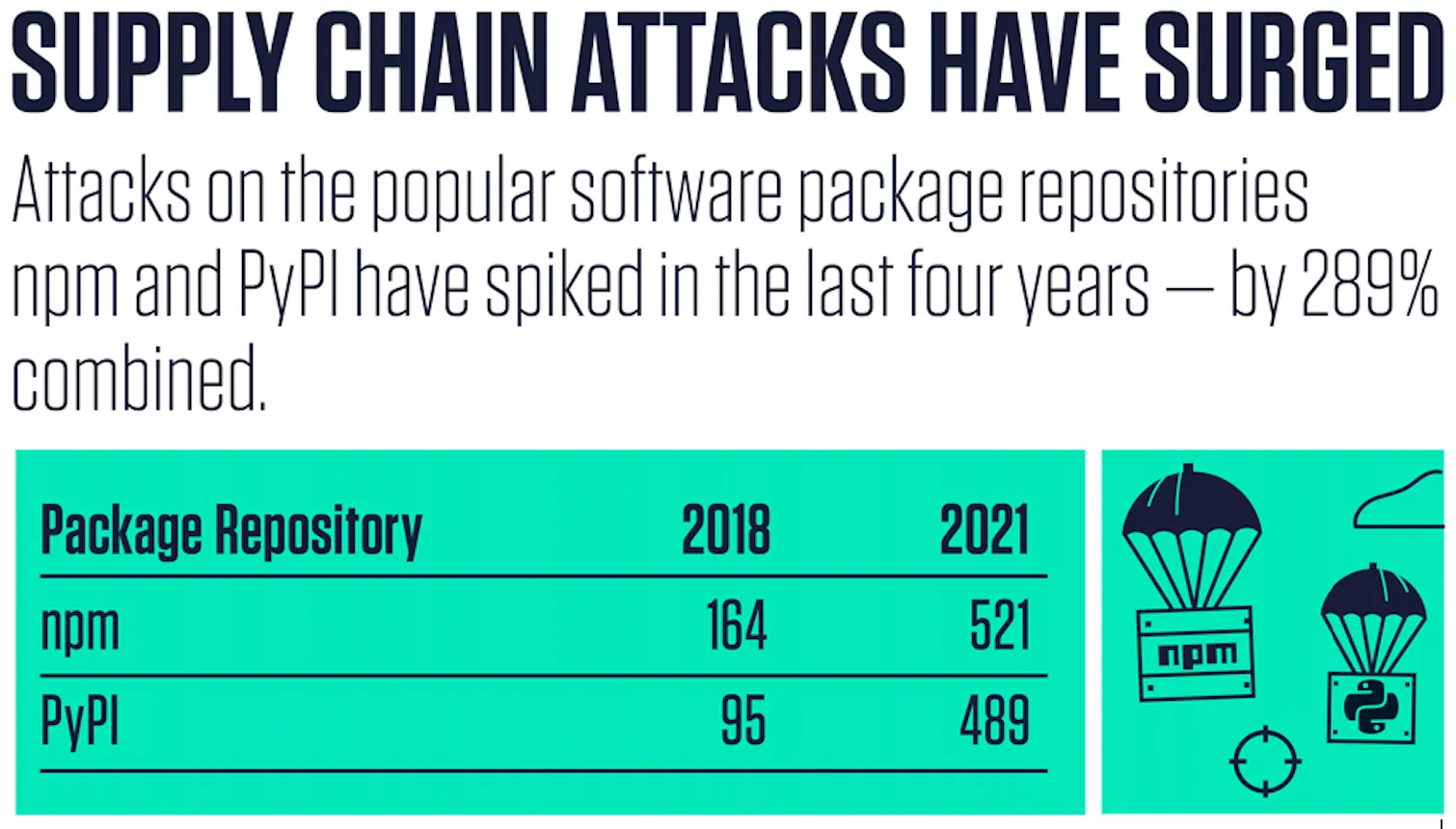
Attackers are broadening their horizons and focusing on finding ways into the enterprise that include DevOps tools and platforms that are integral to most software development teams. And attacks on open-source repositories like npm and PyPI have surged 289% combined since 2018.
Essentially, researchers and attackers are more interested in the software components and infrastructure underpinning the security software programs and services that in one-off vulnerabilities in specific products. So while it's easy to get wrapped up in the sheer metrics of vulnerabilities, trying to patch every flaw in every program in an organization is a Herculean task. It's also unnecessary. What's important is focusing on where attacks are occurring — and increasing.
Vulnerabilities in the NVD represent only a minority of threats to software supply chains. That's because the database doesn't take into account the burgeoning number of attacks And the attacks are outpacing vulnerabilities found in those repositories, especially vulnerabilities with a CVE designation.
The NVD needs to evolve, as does our software team's security approach.

Many tools designed to secure software development pipelines focus on ratings. The problem is that even code from a trusted source can be compromised. For example, ordinarily an upgrade from a software vendor is coming from a trusted source, but in the case of SolarWinds, the trusted source was pushing infected software. Catching those kinds of mistakes requires a focus on how code behaves, regardless of where it came from.

Attacks on the software supply chain can be devastating, but oftentimes they have nothing to do with software flaws. If NIST wants the NVD to stay relevant, it needs to expand the scope of its database to include software supply chain exposures. However, the current absence of those exposures in the NVD shouldn't deter organizations from expanding their security teams’ scope to include software supply chain security.
An expansion of the NVD's approach would better equip security and software development teams responsible for software security to broaden their security approach to address software supply chain exposures that are currently being overlooked. But don't wait. With exposures and attacks on the rise, it's time to modernize your organization's scope — and its tooling.
Get special report: NVD Analysis 2022: A Call to Action on Software Supply Chain Security
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial