 Unknown malicious actors compromised an open source library affiliated with the Solana blockchain platform, putting untold numbers of cryptocurrency platforms and individual wallets at risk of theft.
Unknown malicious actors compromised an open source library affiliated with the Solana blockchain platform, putting untold numbers of cryptocurrency platforms and individual wallets at risk of theft.
The npm package, @solana/web3.js, is a Javascript API for use with the Solana blockchain platform. It ranks among the top 10,000 projects in the npm community, with more than 3,000 dependent projects generating 400,000 weekly downloads, and 51 million total recorded downloads.
Versions 1.95.6 and 1.95.7 of @solana/web3.js were discovered to contain malicious functions intended to steal sensitive information. A GitHub advisory published on Tuesday warned that “any computer that has this package installed or running should be considered fully compromised.” Developers should downgrade to Version 1.95.5 or upgrade to 1.95.8 of the @solana/web3.js library and rotate “all secrets and keys stored on that computer” immediately from a different, unaffected system. Given the nature of the compromise, it is possible that attackers will maintain a presence on the infected system even after the compromised library is removed, GitHub warned.
Differential analysis of Solana package finds malicious URLs
Analysis of the affected packages using ReversingLabs Spectra Assure found clear evidence of a compromise including malicious behaviors like stealing and sending private keys to an external source (hxxps[:]//sol-rpc[.]xyz/api/rpc/queue). Spectra Assure’s differential analysis found new file content in both 1.95.6 and .7, compared with previous, non-malicious versions of @solana/web3.js that contained the URLs pointing to suspicious top-level domains (see RL threat hunting policy TH17118).
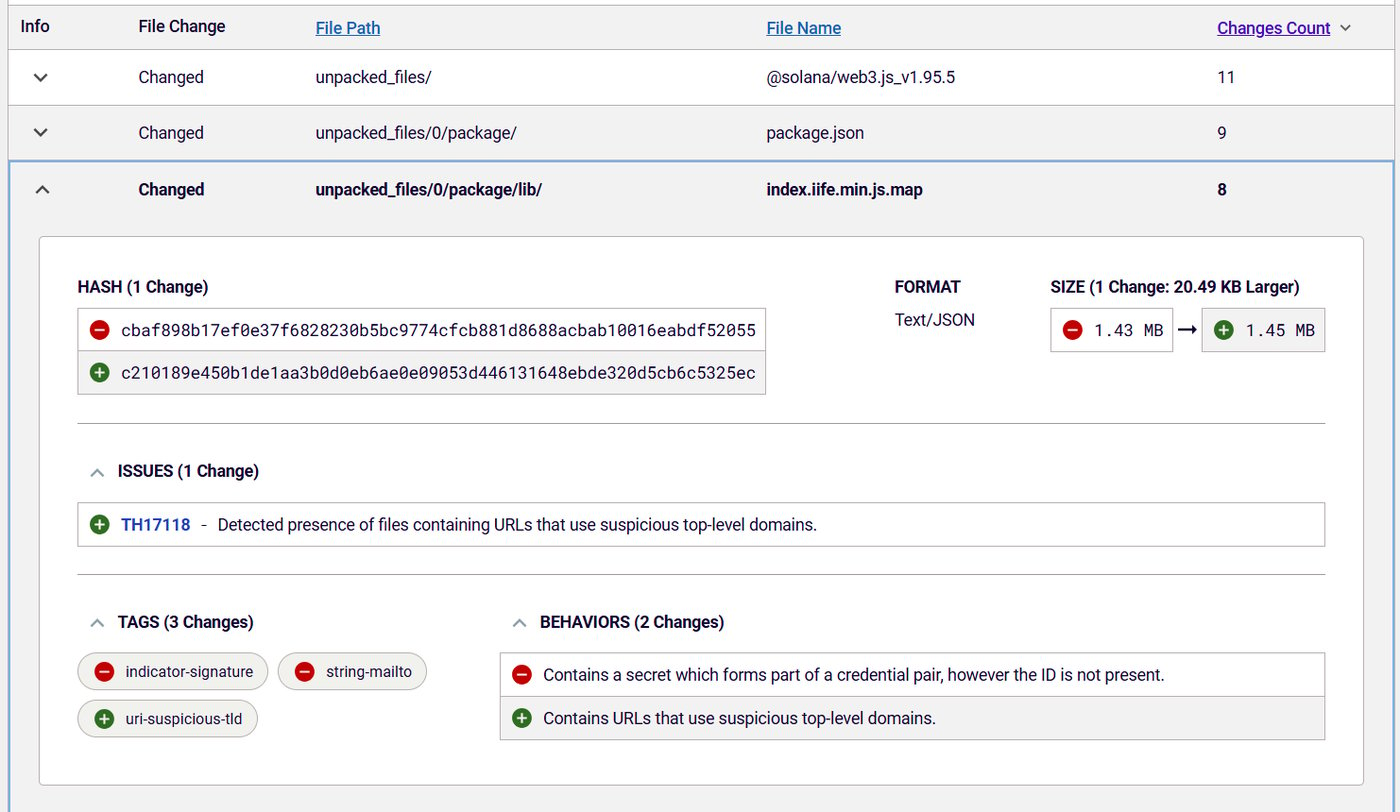
Figure 1: Differential analysis between different versions of @solana/web3.js
Analysis of the affected @solana/web3.js packages by Christophe Tafani-Dereeper, a researcher working for the firm Datadog identified backdoor code inserted in v1.95.7 that adds a function, "addToQueue," that is designed to exfiltrate private keys using legitimate-seeming CloudFlare headers. Calls to the “addToQueue” function were inserted in locations that are used to access the private key, he wrote.
RL's differential analysis of the @solana/web3.js package detected fourteen files in the modified packages that contained URLs with a suspicious top level domain: sol-rpc[.]xyz. Further research by Tafani-Dereeper determined that the domain was first registered in late November and was hosted by Cloudflare.
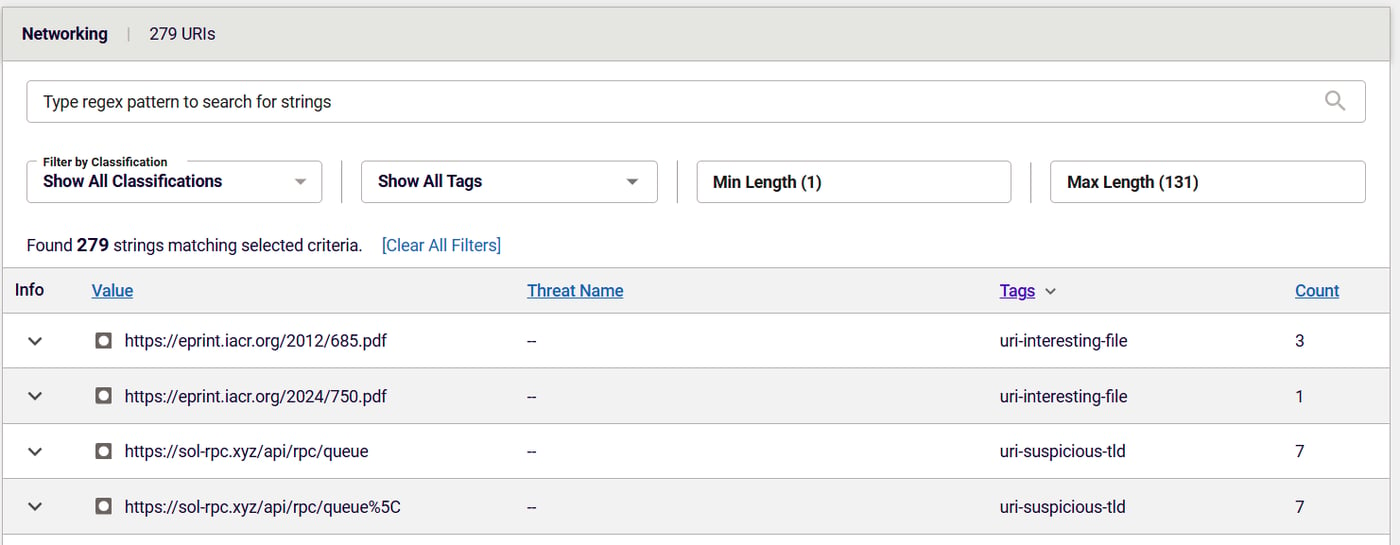
Figure 2: Differential analysis shows presence of URLs that use suspicious top-level domains
Compromised account to blame for supply chain hack?
How the malicious actors gained control over the @solana/web3.js npm library was still a mystery as of late Wednesday. However, there is evidence that the compromise of a @solana/web3.js maintainer account may be to blame. A social media post by Anza, a Solana-focused R&D firm late Tuesday claimed that a publish-access account was compromised by the malicious actors, giving them access to private keys and possibly enabling them to drain funds from crypto bots and other decentralized apps (dapps) that manage private keys directly during transactions.
However, non-automated apps would not be affected by the compromise. And only dapps that updated their @solana/web3.js library between roughly 3 PM (UTC) Tuesday afternoon (December 2nd) and 8:30 PM Tuesday evening would be affected - the narrow window during which the malicious code was undetected.
Crypto (and Solana) a common supply chain target
Code and infrastructure linked to cryptocurrencies are a frequent target of sophisticated cyber attacks, including Solana. In August, the firm Sonatype reported a typosquatting campaign targeting the Solana blockchain platform that played on a discrepancy between the package names for the Solana Python API project on GitHub (“solana-py”) and PyPI (simply "solana"). In that incident, a threat actor published a malicious "solana-py" project on PyPI reproduced code from the legitimate solana package, while also adding malicious features to steal secrets.
In another, recent crypto-focused supply chain campaign in March 2024, RL researcher Karlo Zanki exposed BipClip, a malicious PyPI campaign targeting developers working on projects related to generating and securing cryptocurrency wallets. The attackers sought to fool developers looking to implement the Bitcoin Improvement Proposal 39, or BIP39, a list of 2,048 easy-to-remember words that are used to generate a binary seed that creates deterministic BitCoin wallets (or "HD Wallets").
But the compromise of the @solana/web3.js library is of a higher magnitude of order than typosquatting campaigns that rely on developer error, said RL co--founder and Chief Software Architect Tomislav Peričin. He said the majority of supply chain attacks that target the open source ecosystem rely on social engineering tactics for success. Such attacks have a tiny blast radius, affecting only a few developers before they get discovered and are taken down.
Peričin said this incident is much more than yet another malicious package found in npm. Compromise of a trusted, and widely used library like @solana/web3.js is much more devastating for the community, he stressed.
"With millions of downloads and thousands of library dependents the likely blast radius widens to thousands of developers, and a yet to be determined number of users. This attack is a stark reminder that the trust in software integrity is at an all time low, and that open source security is a far greater challenge than keeping up with the news and filtering out newly published or untrusted packages.”
—Tomislav Peričin
Peričin said the intense focus of malicious actors on cryptocurrency applications and infrastructure raises the bar for development organizations and end users alike. The threat demands increased attention be paid to supply chain risk to respond to such threats, he said.
Keep learning
- Read the 2025 Gartner® Market Guide to Software Supply Chain Security. Plus: See RL's webinar for expert insights.
- Get the white paper: Go Beyond the SBOM. Plus: See the Webinar: Welcome CycloneDX's xBOM.
- Go big-picture on the software risk landscape with RL's 2025 Software Supply Chain Security Report. Plus: See our Webinar for discussion about the findings.
- Get up to speed on securing AI/ML with our white paper: AI Is the Supply Chain. Plus: See RL's research on nullifAI and replay our Webinar to learn how RL discovered the novel threat.
- Learn how commercial software risk is under-addressed: Download the white paper — and see our related Webinar for more insights.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








