On one side you have your SIEM investment – technology that lets you connect multiple security event sources, correlate source information, and create events on anything that looks threatening. On the other side there's your response process, often home built, or maybe you have invested in one of the new security orchestration and automated response (SOAR) tools.
In between are your L2 and L3 analysts investigating the more sophisticated and threatening events. Each of these three areas continues to suffer from event overload, incomplete information, and insufficient context about events, with the number of security tools impacting operational efficiencies. The numbers back this up:
- An enterprise SOC will see upwards of 170K events a week, but their teams are only clearing an average of 12K events, meaning teams remain reactive and can easily miss critical events. (Source: State of SOAR Report)
- Based on an MSSP SOC survey, false-positive rates exceed 44% or more for half of the respondents, meaning teams are wasting significant time on unimportant events. (Source: Advanced Threat Analytics survey)
- Small businesses are using between 15 and 20 tools, medium-size businesses are using 50 to 60, and large organizations or enterprises are using over 130 tools. And most follow no standard of terminology or process flow. Although most have APIs for integration, unifying a process across all detection surfaces and then through investigation and response is nearly impossible. (Source: Palo Alto Networks)
[ See solution brief: Enrich Your SIEM/SOAR with Context-Rich File Intelligence ]
Getting to the Root of the Problem: Destructive Object Insights
At the core of almost all successful attacks, you find some form of malware or destructive object. It might arrive as a phishing attachment, as a web download, a file that entered through a backdoor, or an application upgrade, or hidden in some supply chain object. In the end – malware is the root of the problem. For a security analyst trying to decipher the event information of a possible attack or working to activate the correct mix of playbooks for response and containment, the information about the malware is rarely available where and when they need it. As a result, their decision-making processes are hobbled.
An analyst working within a SIEM needs to quickly and accurately understand if malware is part of the security event, if that malware is known or unknown, and the nature and severity of the threat it poses. With the right level understanding, the analyst can make a very quick decision on prioritization:
- Deprioritize the event because it is a false positive (there is no malware)
- Determine the malware in question is a low threat (simple adware)
- Escalate the event to a full investigation because the event has a high threat level, and the potential malware is unknown
- Pass the event to the response team for immediate containment when the threat level is high and the malware is known
What the L2 or L3 analyst needs when an event is pushed to their queue is a way to quickly move from the SIEM console, where the event workflow originated, to an analysis tool to undertake an investigation of the event and malware involved. Here the analyst can identify the malware, how it will operate, and understand the threat it poses to the organization. With the malware context defined, the investigator can pass that information to the incident response analyst. For an investigation process to truly be effective, it needs to be completed in the range of minutes or hours, not days or weeks.
The incident response analyst responsible for SOAR requires detailed and contextual information about the malware, and a way to systematically define it. This detail covering how the malware operates will help activate the correct mix of playbooks to contain the malware, and then upgrade the relevant detection and prevention controls so the next time the malware comes knocking, it does not sneak through.
File and Malware Context Delivered Directly to Your Security Analysts
One of the greatest unmet needs across event management (SIEM), investigation, and response (SOAR) is obtaining accurate and actionable intelligence that meets the changing needs of the analysts at each stage of the detection and response process. Or more simply stated, security tools need to deliver the right info, to the right people, in the right pane-of-glass, at the right time.
As discussed above, one critical piece of intelligence missing across all areas of the detection and response process is visibility into the underlying files and malware at the root of an attack. That is where ReversingLabs comes into play. We deliver timely and actionable malware and file visibility, and intelligence directly into your SIEM. We integrate with your SIEM to deliver a fast and seamless process of moving an event from evaluation to investigation. We deliver automated static analysis and file reputation intelligence tools to empower your investigators and hunters with the capability to reverse engineer any object. Our solutions enable them to determine if it is malware (regardless of whether an effective signature exists or not) and uncover the context of how the malware infects, evades, and attacks your systems.
Moreover, with our seamless integration to SOAR tools (or our extensive APIs if you build your own) it’s easy to build playbooks that connect ReversingLabs file reputation and file analysis with your SIEM, endpoint, and network devices. These playbooks empower your team to take the right actions immediately, whether you have a malware sample, or just a hash or some other indicator. Most importantly, with our unique analysis engine and architecture, we can do this all very fast and at a massive scale. So how does all this play out in an operational deployment? Let's take a look at a few customer use cases to find out.
Use Case 1: Obtaining Enriched File Intelligence in the SIEM
When an alert comes into the SIEM, your L1 analyst needs to be able to quickly and accurately triage this event, prioritize the event based on severity, decide if the event needs further investigation, or pass the event over to the response team. However, most of the time this analyst does not have the information needed to make the determination. If the event includes any definition of the files involved, with ReversingLabs, the analyst will automatically have critical information about the files to support accurate decision making.
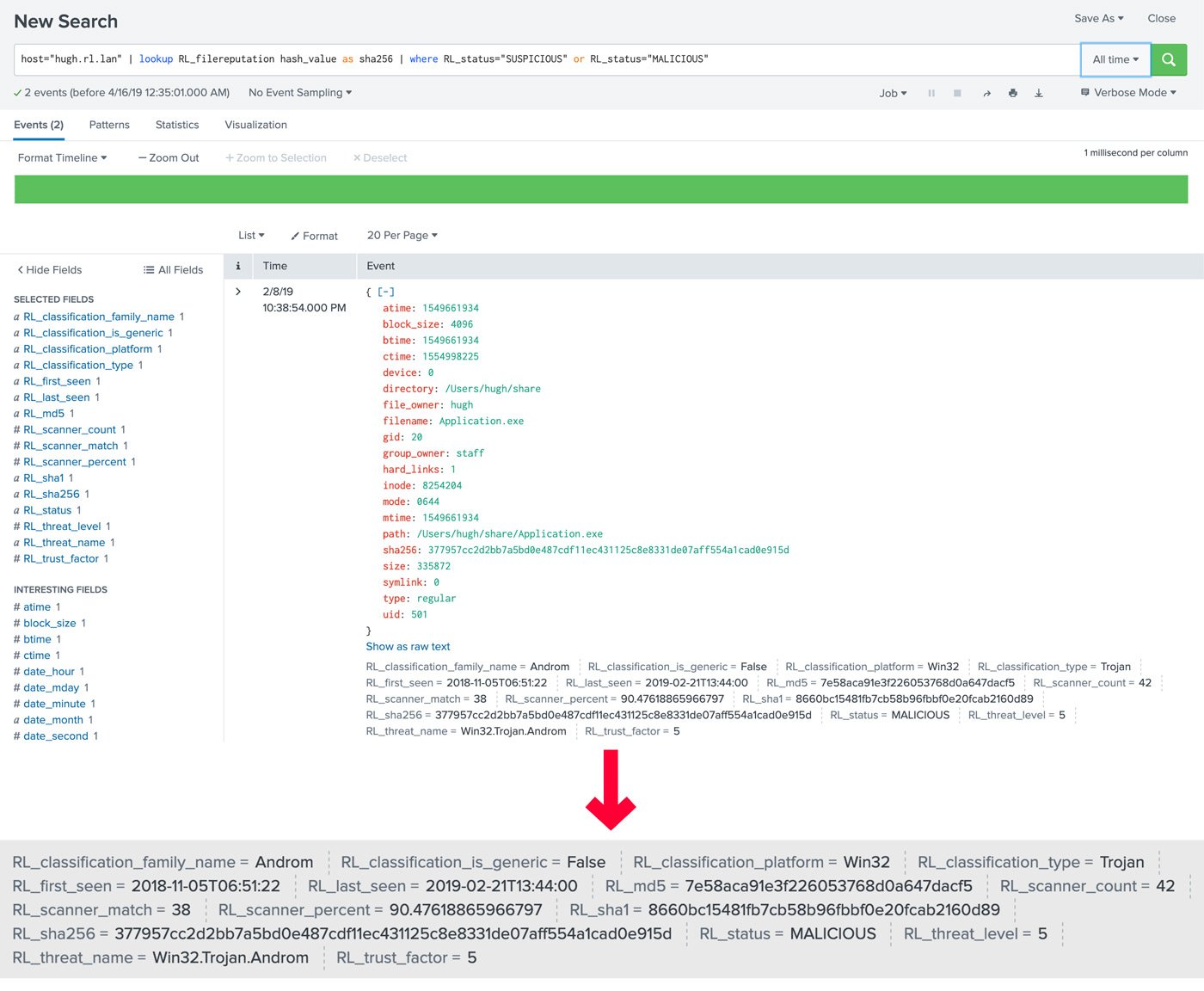 Real-time Malware Intelligence Delivered into a SIEM (in this example - Splunk)
Real-time Malware Intelligence Delivered into a SIEM (in this example - Splunk)
With the SIEM analyst able to immediately understand the context of the underlying file, the decision-making process becomes much more efficient. If the analyst sees that the underlying file is known good, the event is likely a false positive, and the event can be deprioritized. Similarly, if the file intelligence shows the malware type to be a simple form of adware, the analyst can deprioritize the event. If the threat level is high and the malware is verified and known (as in the Trojan malware attack in the screenshot), the analyst can pass the event over to the response team for containment and mitigation.
The result for the SOC is that each analyst can clear more events and in clearing them, have a high level of confidence that the right actions to mitigate the greatest risk have occurred. Speed and accuracy decrease mean time to respond (MTTR), while overall detection and response efficiency in the evaluation stage increases. False-positive recognition also increases – another critical note on having complete event context.
In many cases, connecting security tools together is hard because of the different data models they use. For example, some EDR tools index by MD5 hash, but if your detection event provided a SHA-1 instead, you won’t be able to search for it. ReversingLabs provides SHA-256, SHA-1, MD5, and other hashes for goodware and malware files, so you can pivot from one hash type to another with ease.
Results: SIEM analysts can quickly and accurately remove false positives, prioritize events, activate workflows, and increase the overall numbers of events they can clear each day.
Use Case 2: A Unified Solution for Malware Investigation to Identify Advanced Threats
Some events entering the SIEM are indicators of targeted attacks. These attacks pose the greatest risk to any organization, but security teams often do not have the ability to find and understand them. When an L1 analyst encounters a possible targeted attack where threat levels are high, but the associated files involved are unknown, integrated context-rich intelligence from ReversingLabs enables the analyst to automatically pass that event to L2 or L3 analysts for investigation. The investigating analyst can view the event in the SIEM and with a single click, can move into the ReversingLabs Spectra Analyze (formerly A1000), which offers a complete view and understanding of the files of interest. SOAR tools can submit a file for analysis, receive a report in JSON, and make informed decisions based on verified threat classifications.
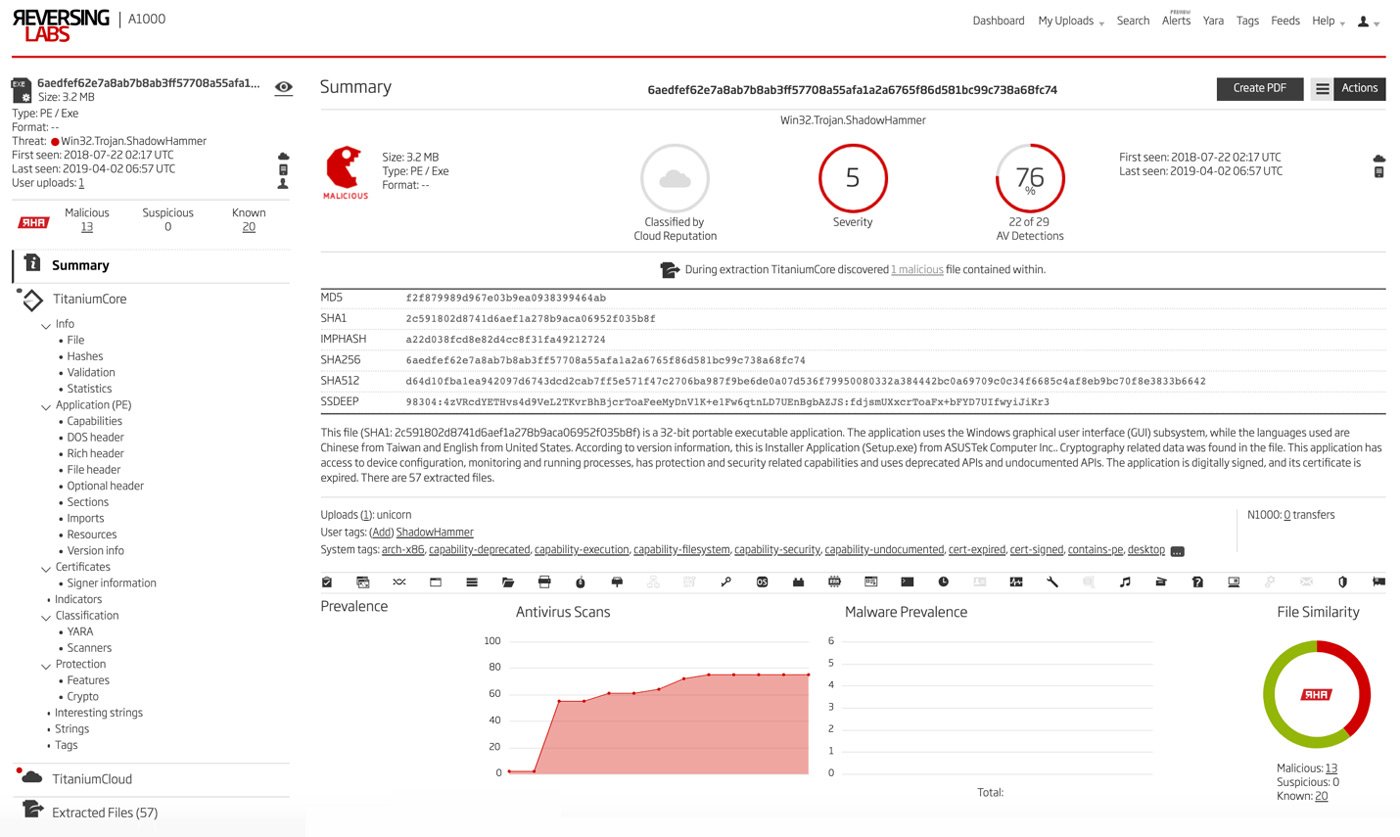 ReversingLabs Spectra Analyze - showing ShadowHammer malware analysis
ReversingLabs Spectra Analyze - showing ShadowHammer malware analysis
Investigators not only have the power of ReversingLabs’ proprietary binary analysis engine to fully deconstruct files, they also have access to tens of billions of malware and goodware samples that are continually processed for the most up-to-date threat intelligence. With this information, investigators can immediately classify malware threats hidden in any file and understand how the malware will attack their environment, and how it will attempt to evade detection tools. All of this intelligence can be automatically delivered to the response team directly within the SOAR tool being used.
Results: Investigators can quickly analyze advanced, even unknown new or polymorphic malware, and determine its threat, evasion, and attack components. If the investigator determines the malware should also be run through a sandbox, the evasion techniques discovered by the binary analysis will improve outcomes of sandbox detonation. Most importantly, unlike any other malware analysis tool, the analysis process from ReversingLabs is completed in seconds, reducing the entire investigation process by as much as 90% (as reported by ReversingLabs customers). By enabling limited investigation resources to be used more efficiently, sophisticated attack detection rates improve and MTTR decreases.
Use Case 3: Optimizing Threat Response and Containment Through Integrated File Intelligence
Incident responders need more in-depth information about events so the appropriate playbooks for both containment and prevention can be activated and produce a high degree of assurance that the threat has been mitigated. Pieces of the required information might come from the SIEM or other detection tools (EDR, NTA, etc.) or investigations. Regardless, the responder must bring together all disparate information to understand all aspects of the threat, including the malware type, infection process, and attack stages. ReversingLabs integration with incident response tools creates a single and unifying view of all incident-related malware. If the responders find they lack information required to determine which playbooks to activate, a file hash query from the response tool calls the ReversingLabs file reputation database and quickly fills in any missing information.
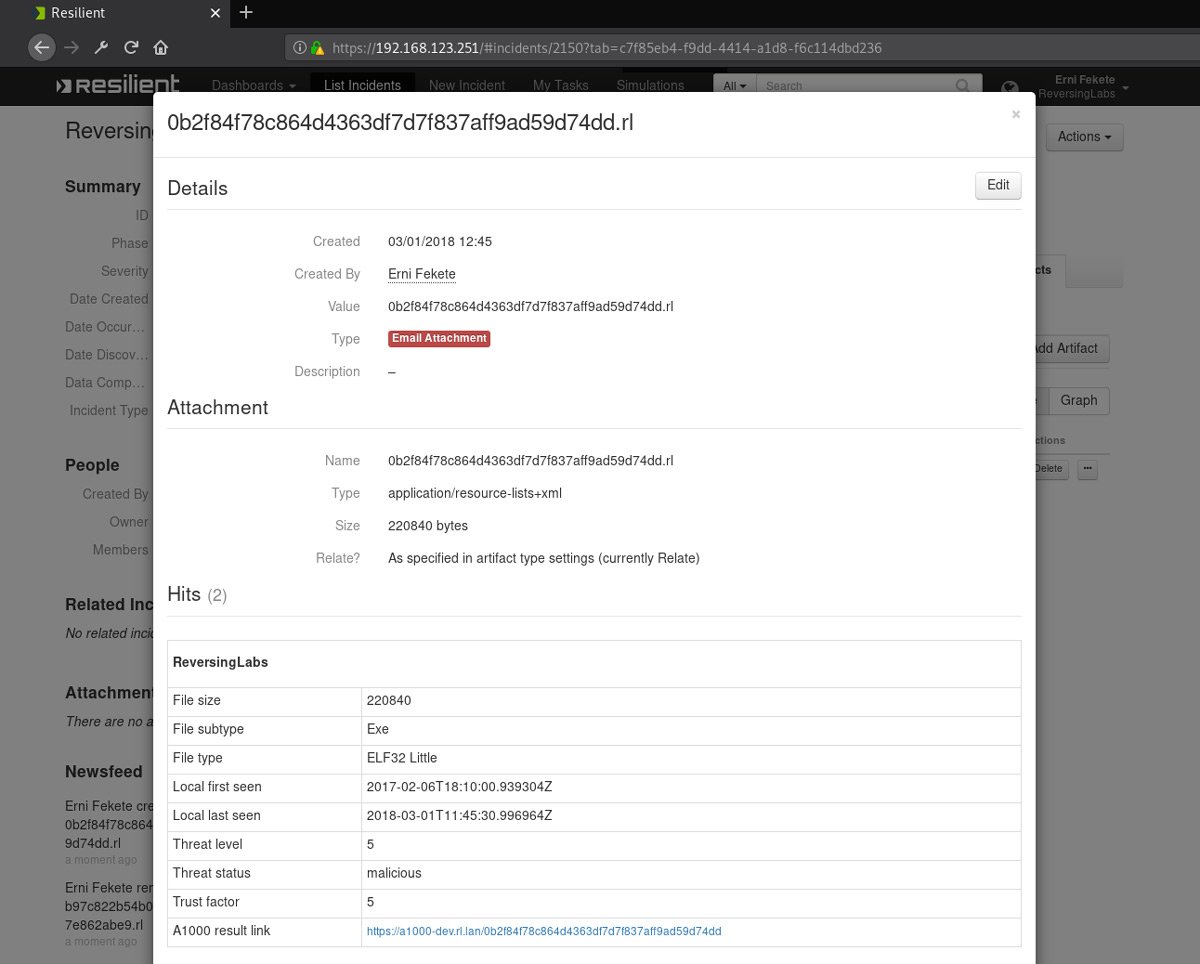 Real-time Malware Intelligence Queried Directly from an Orchestration Tool (IBM Resilient)
Real-time Malware Intelligence Queried Directly from an Orchestration Tool (IBM Resilient)
Results: Responders with a complete view of the context of the malware related to an attack can make timely and accurate playbook activation decisions. Response and SOAR tools and processes are optimized. Risk mitigation assurance is increased, and MTTR is decreased significantly across all three use cases.
Automation of Scalable Threat Classification and Orchestrated Response Processes
It’s a given that large enterprises need to manage and secure an ever-growing volume of global traffic emanating from multiple sources and consisting of varying types of incoming files and objects. The volume, velocity, and variety of incoming traffic creates many ways for threats to enter your environment unchecked. In this situation, surfacing malware threats hidden within files becomes critical in the detection process. To deal with the issue of massive scale, experienced security teams are turning to automation and a new class of security orchestration and automated response (SOAR) tools. ReversingLabs supports scalable automation in SOAR tools to increase efficiency and response capabilities.
First, ReversingLabs is capable of automatically analyzing and classifying files and objects in real time and at massive scale. Inputs to the threat classification engine include email, network, web, and cloud data. Customers report classification numbers as high as 10 million files per week. The resulting high-risk threat classification information can be delivered into a SIEM or SOAR solution where alerting can occur, and the same rich, actionable malware intelligence is provided.
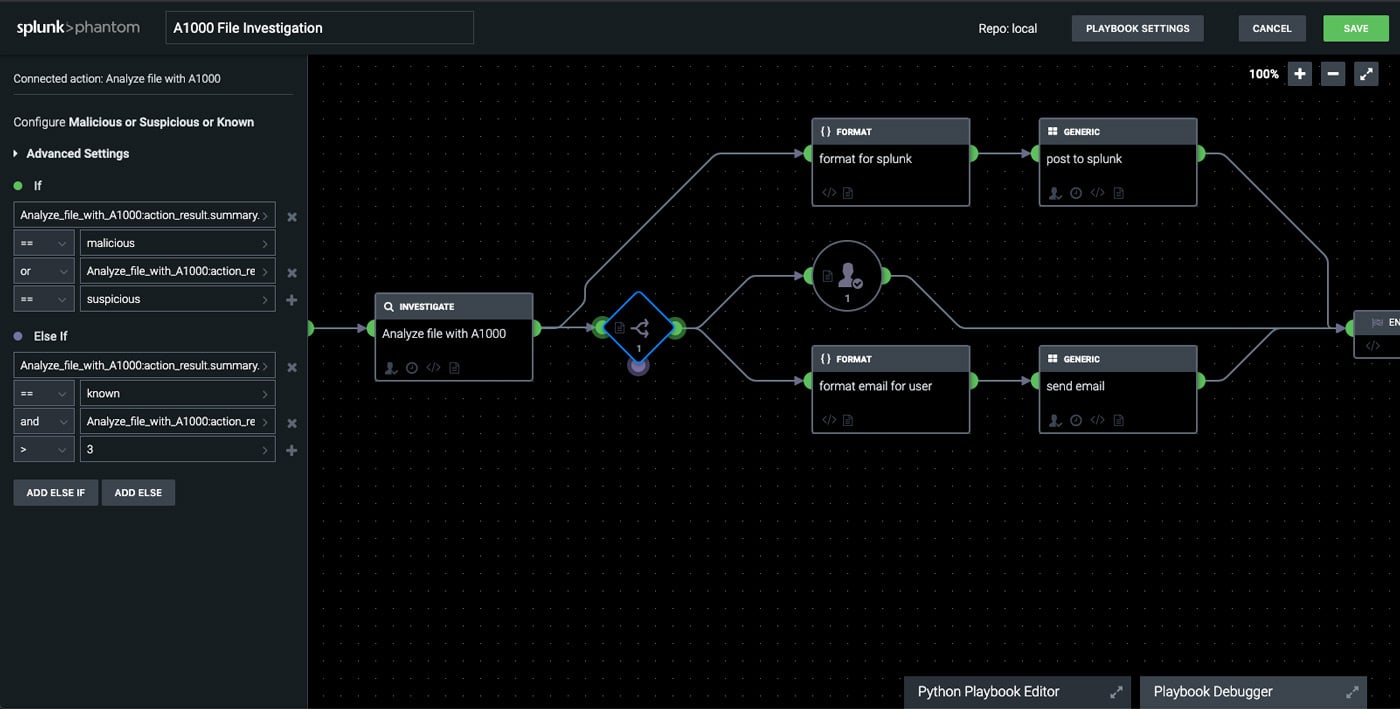 Splunk Phantom Workflow Integrated with ReversingLabs Spectra Analyze Solution
Splunk Phantom Workflow Integrated with ReversingLabs Spectra Analyze Solution
Second, all components of Spectra Analyze can be integrated into SOAR workflows and playbooks to further automate security processes. Regardless of whether the input is threat classification, threat intelligence, vulnerability information, or the results of an unknown malware investigation, ReversingLabs helps optimize the delivery of actionable information across SOAR workflows.
The increase in automation delivered by ReversingLabs’ direct integrations provides comprehensive malware identification across security operations stages, increases in operational efficiencies and threat surface coverage, all the while improving defenses against known and unknown malware types.
The outcome is a better understanding of targeted attacks while optimizing automated playbook effectiveness, dramatically streamlining workflows, and reducing the workload of all types and levels of SOC analysts. If more information or investigation is required, an incident responder or threat hunter can seamlessly pivot to the advanced malware analysis solution with a single-click to continue with the workflow and obtain necessary information to archive with each case.
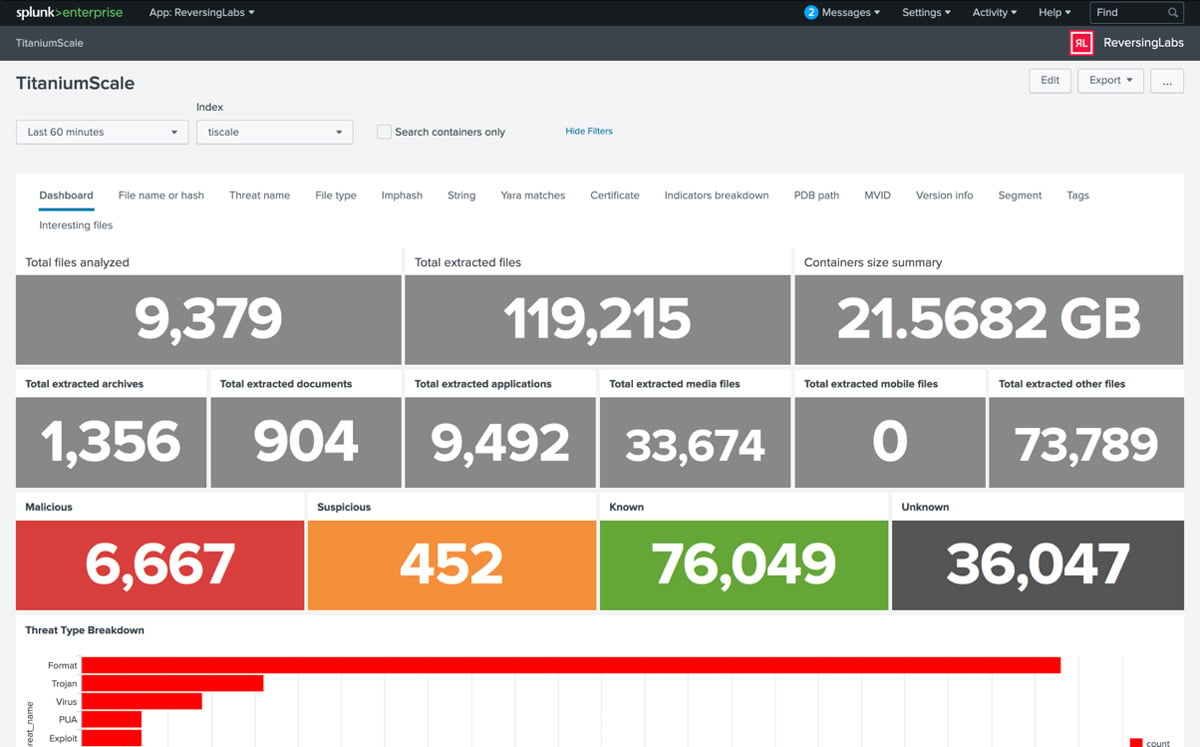
ReversingLabs App for Splunk - providing a summary of file and object analysis
Conclusion
SOC teams are struggling to deal with an overwhelming number of events. Benchmarks show that clearing just 20% of events weekly means they are making above average progress. The same teams waste a significant amount of time working through each event, as almost half of them are likely to be false positives. Add on the inability to gather the needed event context and intelligence in a single location and with a common language to have any chance at understanding if the event is a high-risk threat, a low-risk threat, or a false positive, and you begin to understand why cyberattacks continue to succeed. One critical piece of intelligence that is missing throughout the detection, investigation, and response process and highlighted throughout this blog is malware identification and context.
ReversingLabs solves this problem with our proprietary, AI-driven complex binary analysis technology, backed by the industry’s largest file and network reputation database and seamless integrations, which deliver both the context-rich malware intelligence and advanced analysis capabilities needed to significantly improve security operations for SIEM, investigation, and SOAR response workflows.
[ See solution brief: Enrich Your SIEM/SOAR with Context-Rich File Intelligence ]
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








