In today’s ever-changing security landscape, it is vital for security operations teams to have access to reliable and complete information about possible threats. File objects, in particular, can hold a lot of valuable information for defenders. However, accessing this information can be difficult without the right tools.
We recently made a subset of our TitaniumCloud APIs focused specifically on file enrichment available in the Azure Marketplace for Microsoft Sentinel users. This blog post will explore how a SOC analyst can utilize the data provided by the ReversingLabs file enrichment APIs in Microsoft Sentinel.
Overview of Enrichment APIs For Microsoft Sentinel
As a former SOC analyst, dealing with files in security alerts was a huge pain point. Classifying a file is a time-consuming task, especially without the right tools. Smaller teams without the budget for dedicated malware analysts or tools like sandboxes often rely on free third-party reputation information, which can be unreliable as files used by malicious actors tend to change frequently.
The core purpose of the ReversingLabs enrichment offer is to provide better insights into files and file hash entities within Microsoft Sentinel. By querying the ReversingLabs TitaniumCloud File Reputation and File Hash Analysis Report APIs, analysts can gain a deep understanding of the files in their environment backed by ReversingLabs’ powerful static analysis engine and repository containing billions of files.
[ Get Free Trial: ReversingLabs Enrichment APIs For Microsoft Sentinel | Learn More: ReversingLabs Threat Intelligence for Microsoft Sentinel ]
Using the Enrichment APIs For Microsoft Sentinel Offer
It’s easy to get started working with the ReversingLabs enrichment offer. I highly recommend installing the ReversingLabs content pack solution, available in the Microsoft Sentinel content hub, which contains a set of example playbooks that analysts can use to start enriching file hash entities:
[ Get Free Trial: ReversingLabs Content Pack for Microsoft Sentinel ]
Once a playbook is created, it’s as simple as running it against a Microsoft Sentinel incident containing file hash entities. A perfect use case is when a user submits a potential phishing email and attachment for review.
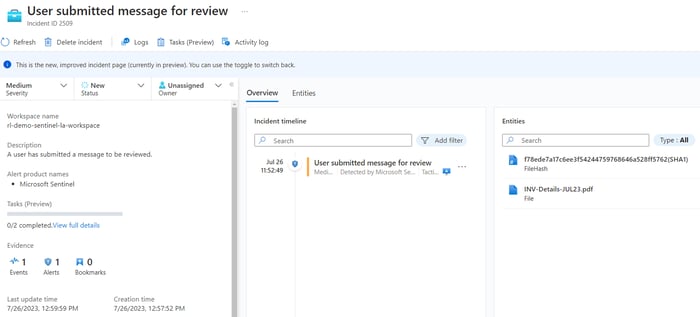
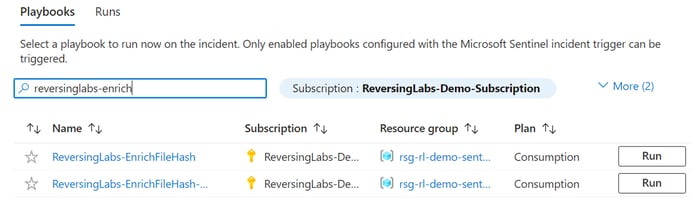
What would typically take a good amount of time to assess the message and attachment only takes a few seconds when using the ReversingLabs enrichment offer. Simply run the playbook by clicking “Incident Actions” -> “Run playbook” -> find the “ReversingLabs-EnrichFileHash” playbook, and click the “Run” button:
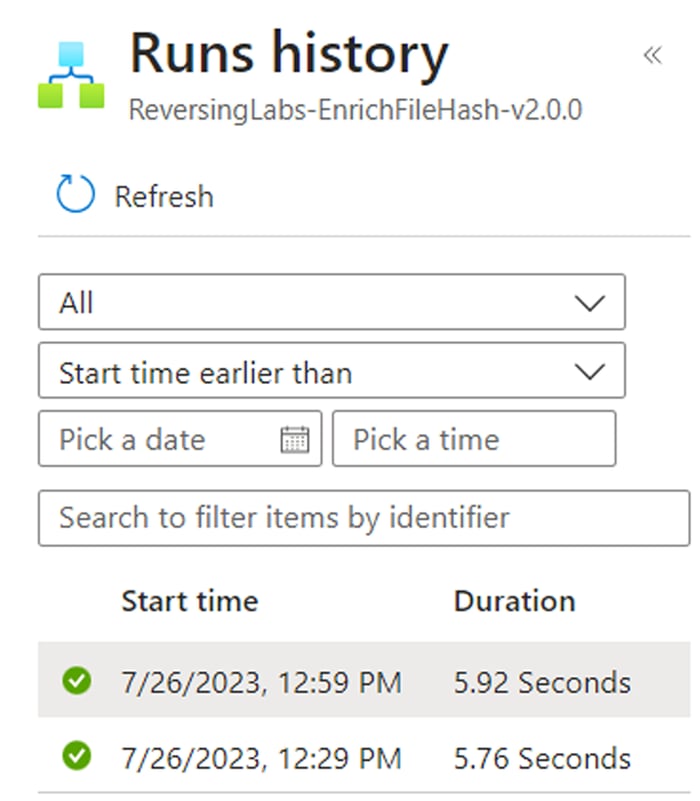
After a few seconds, the playbook will return a summary of the associated file hash directly into the Activity Log. The flow chart below describes a high-level list of steps to take for each file classification type:
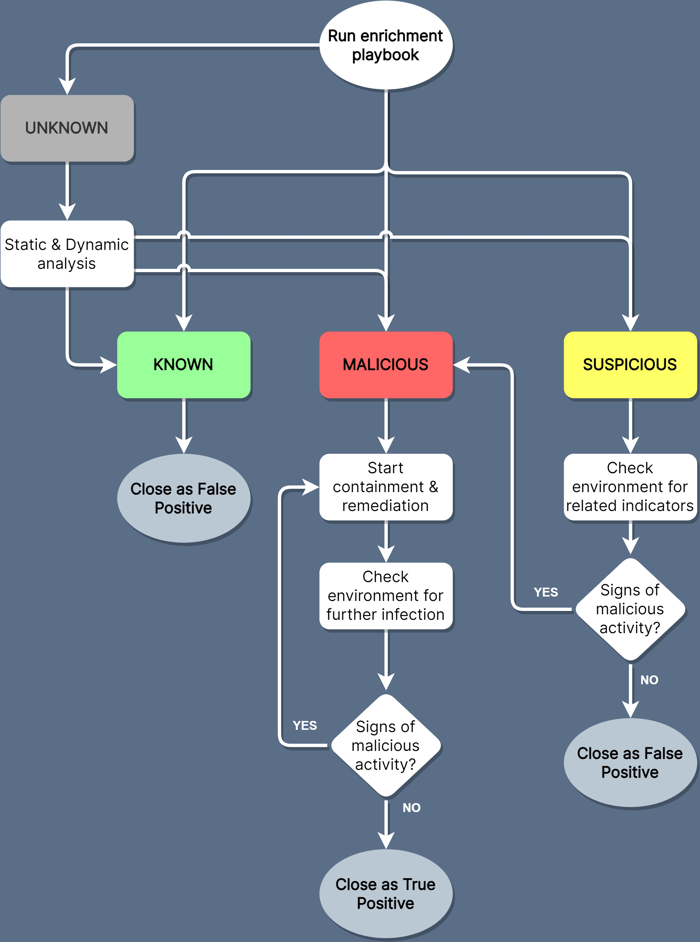
Malicious files
In this example, the attachment is classified as malicious:
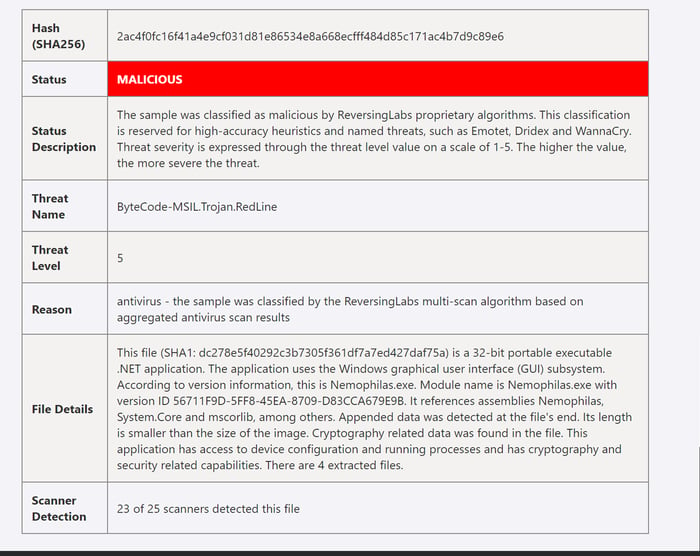
The analyst can kick off the remediation workflow and close the incident, right? But wait! In addition to all that extra time saved, analysts can use detailed data to ensure they eliminate the threat.
The first step is to ensure that the original and similar messages are pulled from users' inboxes and quarantined. A great way to prevent future attacks from the same campaign is to add the file and file hash to a block list across available security tools. However, what if another user has previously downloaded the file and triggered the malware?
In the screenshot above, the playbook includes the “Threat Name” field, which provides the threat actor name. In this case, the file contains RedLine malware.
Additionally, the “File Details” field mentions that there are embedded objects and the file accesses networking. Knowing this information, checking the environment for the latest RedLine indicators would be a good idea. The official MITRE ATT&CK website is a great place to start identifying tactics, techniques, and procedures. From here, using Microsoft Sentinel’s built-in threat hunting capabilities and searching for hunt queries with matching techniques can help verify signs of active infection.
[ Sign up for our weekly newsletter to get our weekly malware family indicators and queries for Microsoft Sentinel ]
Suspicious files
Occasionally a file itself may not do anything malicious but still exhibit suspicious behavior. Many phishing attacks often just add a fake “click here now” button to a file that attempts to trick users into downloading first-stage malware.
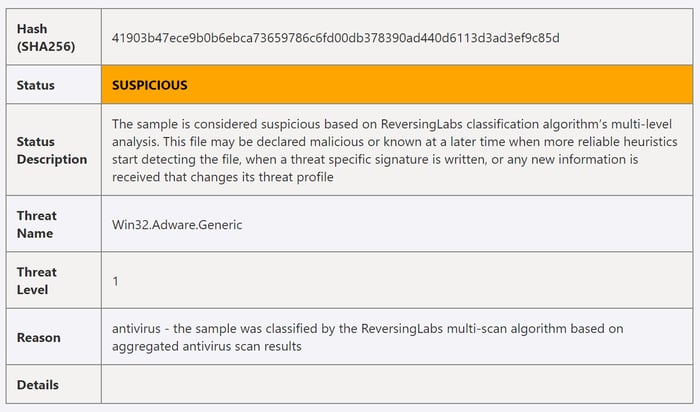
Each organization will have a particular risk appetite that dictates how to respond to this appropriately. Still, the general idea is to check for any additional indicators of compromise and pivot from the other information learned during triage. If there are signs of infection, it’s time to start the containment and remediation process. Adding the file and file hash to a block list may still be a good idea if there are no strong indicators of an active infection.
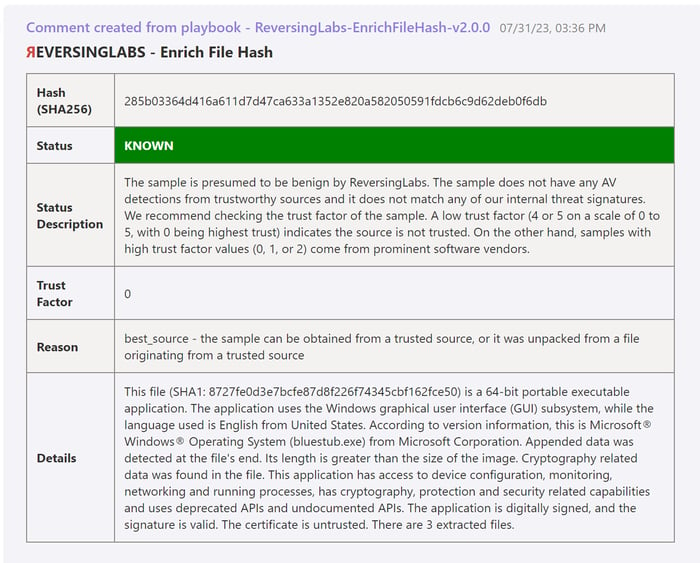
Known files
The best result is files classified as known goodware. These files, such as properly signed operating system files, have been vetted and can be assumed to be safe. Depending on the organization's needs, it may be a good idea to filter this file or file hash out of the alert to prevent future false positives.
Unknown files
Sometimes, the classification of a file may be “unknown”, and it is important to make sure it is not harmful through static and dynamic analysis. Microsoft Sentinel currently does not have a built-in feature for detonating files (outside of integrating with Microsoft Defender for Endpoint’s deep analysis feature), so third-party tools are recommended.
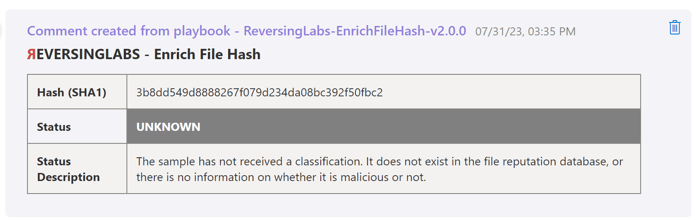
We’re working on creating another Azure marketplace offer for this use case that will make it easy for SOC teams using Microsoft Sentinel to add this capability to their toolset. Still, any existing TitaniumCloud or A1000 customers can use the newly updated Logic App connectors to upload files for analysis. Watch for future details on the marketplace offer and a blog post on handling file objects with Logic apps!
Know your file classifications
This blog post covered how a SOC analyst might use the ReversingLabs file enrichment APIs for Microsoft Sentinel. There are four file classification values, each with a unique workflow:
-
Malicious. Results in an immediate remediation workflow and effort to identify further infection
-
Suspicious. Depending on the organization's risk appetite, the analyst may kick off the remediation workflow immediately or perform additional analysis for signs of infection.
-
Known. Previous analysis of these files ensures they are benign. It’s safe to assume that file-related alerts with this classification can be immediately closed, saving time and effort.
-
Unknown. Static and dynamic analysis is required to understand the file's purpose fully.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.








