Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Many software development shops deliver their product releases via virtual machine (VM) disk images. Whether deployed to a cloud environment, data center, or elsewhere, delivering safe and secure images is vital. If vulnerabilities, malware, or even unhardened binaries are present in a disk image delivered to customers, they are exposed to a significant degree of risk every time a VM is spun up using that image. If one of those customers ends up being compromised in a cyberattack due to the VM, both organizations may incur financial loss, as well as reputational damage.
Likewise, when enterprises acquire commercial software to meet their business needs, it may come in the form of a virtual machine or virtual “appliance” — introducing a challenge to ensuring that the appliance does not contain vulnerabilities that would bring unacceptable risk to their organization. Appliances may also hide malware, surreptitiously planted by threat actors, that comes alive to wreak havoc when the VM is brought online.
To understand the security risks of a VM, security teams will typically spin it up in a test environment. Having a virtualized test environment may be challenging. Isolation from production and corporate networks is important, but that translates into complexity and cost.
Assuming the VM is up and running in a test environment, it is then scanned with various tools. Vulnerability management companies specialize in this type of traditional infrastructure scanning. Their products are effective at identifying OS-level vulnerabilities and vulnerabilities in software installed on the machine. Specialized tools – both free and commercial — may be used as well, to check for leaked secrets, generate a software bill of materials (SBOM), or identify security misconfigurations, for example.
Another approach to assessing VMs is to install an agent from a security solutions provider. This type of agent analyzes the running machine in the background and reports back to a centralized dashboard. While not a traditional scan, this is still a slow, run-time approach to the problem.
In some cases, software vendors may have infrastructure as code (IaC) files, such as Terraform configuration files, Azure Resource Manager templates, or AWS CloudFormation templates. These IaC files can often be scanned statically to check for problems like misconfigurations or leaked secrets. While IaC scanning tools are fast, they are very limited in their detection capabilities.
In reality, run-time approaches to assessing VMs are time consuming and mainly focus on identifying vulnerabilities. And while scanning IaC files is fast, it often provides information only about misconfigurations and secrets. But there is a better way.
See Webinar: Securing Your Virtual Machines: The Fastest & Easiest Way to Identify Risk
ReversingLabs Spectra Assure uses a pre-deployment approach to assess VMs, which is not only faster, but more thorough. The solution’s complex binary analysis scan engine — Spectra Core — is the game-changing technology behind Spectra Assure that provides for rapid and comprehensive assessment of VM disk images.
Given a VM image file, Spectra Core recursively unpacks (or “deconstructs”) all software binaries and archives to enumerate and identify the individual files and components that are present. Rich threat and vulnerability intelligence is then applied across the board to detect a wide range of issues including malware, CVEs, exposed secrets, file tampering, license risks, and hardening issues. A comprehensive SBOM and multi-dimensional risk assessment for the disk image is generated as well.
There’s no need to deploy VMs and run multiple tools when you have Spectra Assure. It delivers invaluable information about the safety and security of VMs at lightning speed. No need to run a hypervisor, deploy the VM, or stand up hosting infrastructure of any kind. The image file is all that’s required. Teams can simply upload it to the Spectra Assure Portal for analysis, or scan it with our command-line interface (CLI) tool.
Over a period of 15 years, RL created Spectra Core and infused it with the ability to recognize and unpack a large number of different file formats. RL engineers realized that by adding support for VM disk images, we could unlock a powerful feature for our customers: The ability to assess entire VMs without the need to deploy them.
For that reason, RL’s Research & Engineering teams spent a good portion of 2024 working to broaden our coverage of VM disk image formats. It was no small task, because there are many different formats in use today. Some of the most popular include:
In 2024, the Spectra Assure team added support for all of the above formats.
Another important factor in being able to unpack and analyze VMs in a static form is handling the underlying disk partitions and file system. Disk partitions come in a variety of flavors, including MBR, GPT, EFI, or LVM. LIkewise, there is a plethora of file system types. Some are exclusive to Windows (NTFS, FAT, FAT32), others to Linux (EXT, UFS2, XFS), and also to MacOS (HFS, HFSX, HFS+). The Spectra Assure team spent months researching the technical specifications for these disk partition and file system types, then enhancing the scan engine to support each of them. The Spectra Assure product documentation provides specific details in terms of supported file formats and file systems.
Another factor the product team had to consider is that VM disk image files are often very large. Spectra Assure can scan files as large as 10 GB (or larger – contact us for more details). Note: RL always recommends compressing the file prior to submitting it for a scan (assuming it’s not already compressed). Most common compression formats work fine, including zip, 7z, and gzip.
Spectra Assure goes beyond checking for vulnerabilities. The fact is that modern software supply chain attacks often don’t involve exploiting a vulnerability. Just ask SolarWinds or 3CX. Spectra Assure leverages ReversingLabs’ 15 years of expertise in malware analysis and threat hunting to identify not only known malware, but also novel supply chain attacks. It does this by analyzing software behaviors and seeing evidence of tampering.
Detection of secrets, software license risks, and hardening issues are also included in Spectra Assure’s analysis. Secrets refer to sensitive information like API tokens or private encryption keys that are exposed in the disk image or software package. License risk issues mainly consist of software components with copyleft licenses, which may require open-sourcing proprietary code. Hardening issues relate to unused compiler or linker options that protect against certain exploits.
For software developers and publishers, using Spectra Assure’s complex binary analysis for scanning allows them to check for these different types of problems and provides assurance that they’re shipping a high-quality product. For software consumers, Spectra Assure allows them to quickly and independently evaluate the quality of large VM images supplied by publishers or system integrators.
Let’s look at an example scan of a VM disk image. A quick Internet search turned up an open-source security monitoring tool. The tool is provided as a virtual appliance in OVA format. The .ova file is publicly available for download, and its size is 3.68 GB.
Scanning this OVA using the Spectra Assure CLI on a laptop took 47 minutes. Scanning it using the Spectra Assure Portal took 35 minutes.
The summary-level scan results are presented below.
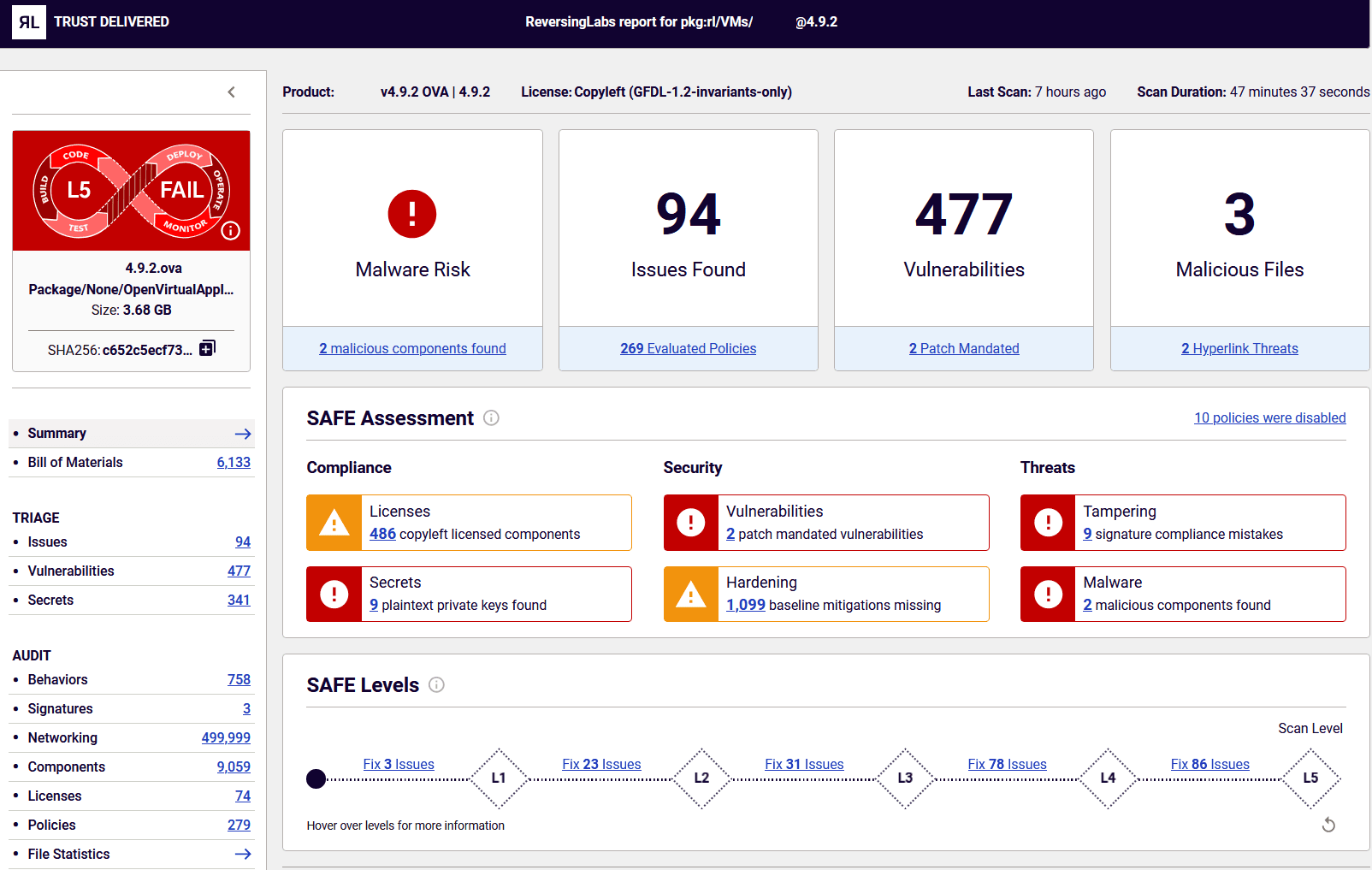
The overall scan status displays “L5 FAIL” in red. This means it did not pass the SAFE Level 5 policy (read more about SAFE Levels). You can also see that Spectra Assure found malicious components, patch-mandated vulnerabilities, plaintext private keys, and digital signature mistakes in this OVA file.
With these results, it would not be wise to deploy this VM in your company’s environment. You may want to inform the VM’s supplier about the unacceptable findings and ask them to fix the issues. At a minimum, consider deploying the VM with strong compensating controls to prevent an incident. On the other hand, if your organization produced the VM, reach out to the appropriate development team and ask them to remediate the issues.
A deep dive into the results is beyond the scope of this article, but the power and comprehensive nature of a Spectra Assure scan is evident nonetheless. With Spectra Assure, users can go from having zero information about a random VM image on the Internet to seeing clear-cut risks — in less than one hour.
Besides identifying security risks, the Spectra Assure report comes with a full, interactive bill of materials that lists all identified software components. It contains more than 6,000 items for this OVA. Spectra Assure can also provide an SBOM in standard CycloneDX or SPDX format, in case you need to share it with others. Sharing of SBOMs is fast becoming essential.
What job roles are usually responsible for the safety and security of VM disk images? It depends.
Regardless of roles or titles, the goal is the same: ensuring that running VMs don’t cause a security incident. That job becomes much easier and less time-consuming with Spectra Assure.
Of course, the ability to operationalize any security scanning tool is an important consideration. While Spectra Assure scans can be done manually by uploading a file or using the CLI, a best practice is to automate scanning in a repeatable fashion. Automation is fairly straightforward with Spectra Assure, because no additional infrastructure is required — unlike run-time analysis.
To simplify the effort for customers, Spectra Assure capabilities can be automated using RL’s rl-scanner Docker image for local scanning, or RL’s rl-scanner-cloud Docker image for SaaS-based (Portal) scanning. Besides the Docker images, RL provides native plugins and extensions for CI/CD tools like GitHub Actions, Azure DevOps, and GitLab. We also provide the Spectra Assure Python SDK, a convenient wrapper for the Spectra Assure Portal REST API.
The traditional way of testing VMs for security issues by spinning them up and running scanning tools against them is time-consuming and costly. Spectra Assure provides a solution that is faster and more thorough in its analysis. Throughout 2024, RL added support for many VM disk image formats, as well as the most common disk partition and file system types. Whether your organization is a software publisher or software consumer (or both), you can now assess the safety and security of entire VMs without needing to run or deploy them.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial