Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Let’s say you own a Mac, you read our blogs and you want to protect yourself. After installing an antivirus program, it suddenly detects your favorite video transcoder: HandBrake. As this is clearly a false positive, you decide to go about your way and ignore this detection. Well, you might have been infected with the Proton backdoor.
A backdoor is a vulnerability that gives the attacker unauthorized access to a system by bypassing normal security mechanisms. It is a threat that hides and works in the background, making it difficult to detect or remove. Red teams are using backdoors to gain access to systems from remote locations, steal personal information, install unwanted software, or take control of the entire computer.
The Proton threat was present on the HandBrake’s official download site between 02/May/2017 14:30 UTC and 06/May/2017 11:00 UTC. The user would unknowingly download the infected application and install it on their system. Upon running the application, the malicious copy of HandBrake would immediately ask for the admin password. This is strange behavior for a video transcoding application, but such requests are often ignored by the end-users. Proton would then exfiltrate the keychain containing all the passwords and pose as a backdoor for hackers. The Proton threat had the 0935a43ca90c6c419a49e4f8f1d75e68cd70b274 SHA1 checksum that could have been compared against the checksum on the official web site, preventing the infection.
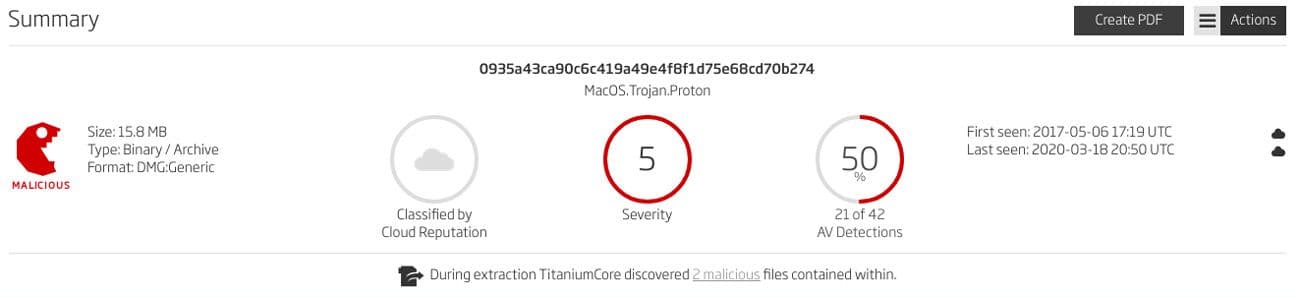
Figure 1: Proton sample detected by ReversingLabs solutions
This is not the first time, nor the last time, we’re seeing Proton-like attacks. Proton already posed as Elmedia Player, using C&C servers registered as eltima[.]in / 5.196.42.123. Later on, a new threat emerged in the form of Calisto. The Calisto malware is a Mac backdoor that was created in 2016 but managed to remain under the radar until as late as 2018. The malware authors who created Calisto disguised the malware as the ninth version of Intego security for Mac, sample SHA1: 55800dc173d80a8a4ab7685b0a4f212900778fa0
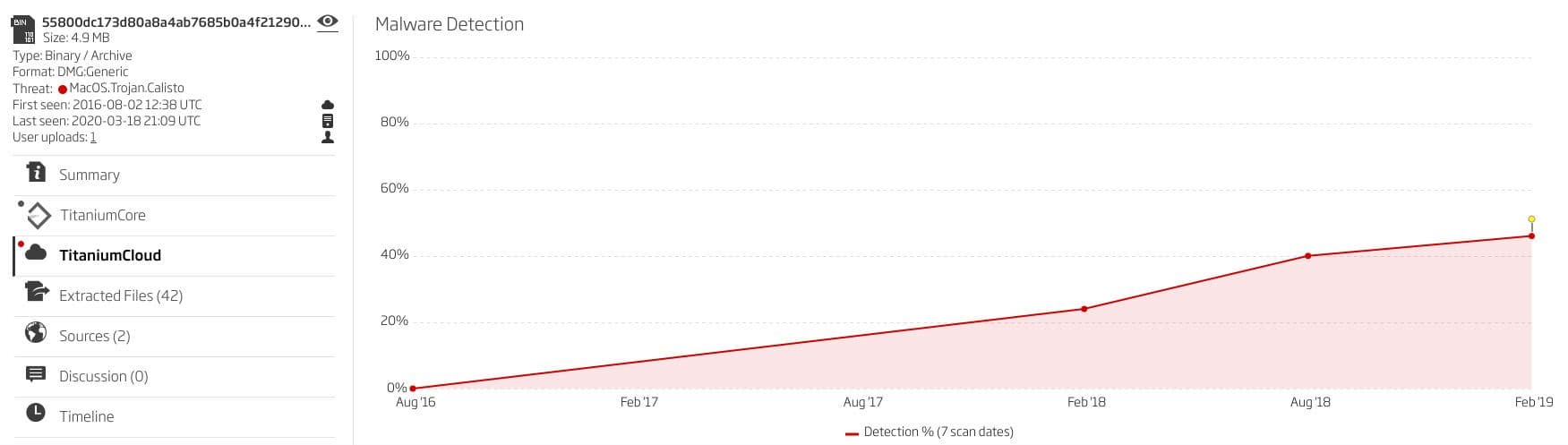
Figure 2: Increasing Calisto detection rate
These samples are just for the showcase, but what they show is there are similarities between various malware samples, and it’s only a question of time when a new threat will emerge. To protect yourself against backdoors you should increase awareness of their existence in the wild.
Never download email attachments or open links sent by people you don’t know. When you download files from the web, make sure they are coming from official sources, and compare checksums against officially listed ones. Be careful when visiting less secure sites, as they can contain a so-called “drive-by download” which can install malware on your computer simply by visiting a compromised web page. Remember, you are the first line of defense, and locking your backdoors can help you keep your environment safe.
For more information, please check our homepage or contact us directly.
Read about our Titanium Platform technology to counter these attacks
Download our eBook on The Destructive Objects Playbook
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial