Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
A step that an adversary takes during the post exploitation phase of an attack is to establish a command line interface (CLI) with a computer inside the victim’s network. One recent incident demonstrates the entire intrusion set operated by FIN6[1], a financially motivated threat actor group. This incident shows the phishing email used to gain initial access to the various attack chain components including a reverse shell DLL to provide a command line interface to the adversary.[2] The use of the More_eggs[3] Javascript backdoor in this intrusion set links this incident to FIN6.[4] Companies in the retail and hospitality sectors have been targeted by this group with a specific interest in attacking point of sale (PoS) systems.[5] What follows is a focused examination of the reverse shell DLL[6] used by FIN6 in this particular incident. Incident responders or threat hunters can take the insights learned here and apply them to similar threats to speed up their investigations.
Starting with static analysis of the DLL, one export is found: DllRegisterServer. This is important later on during dynamic analysis in a debugger and in an automated malware analysis environment. This export is how the DLL must be executed when analyzing it via rundll32.exe. This export can be found using the Titanium Platform as seen in Figure 1.
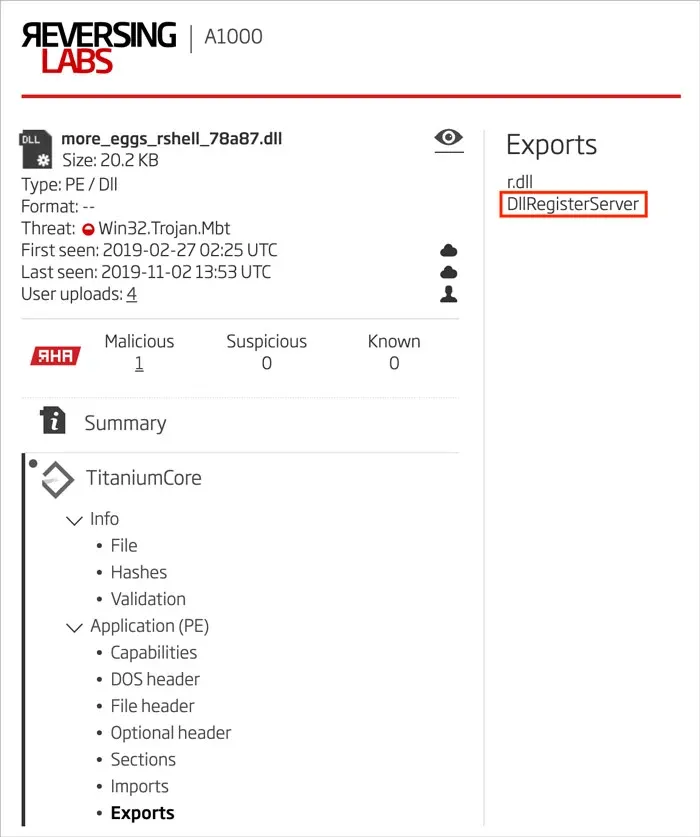
Figure 1: DllRegisterServer Export
Next, looking at the assembly code of the DLL in a disassembler, the procedure immediately after the entry point is a form of execution dispatcher. This particular procedure matches a publicly available YARA rule, “PureBasicDLLNeilHodgson”.[7] The instructions matched by this rule are are highlighted in Figure 2.
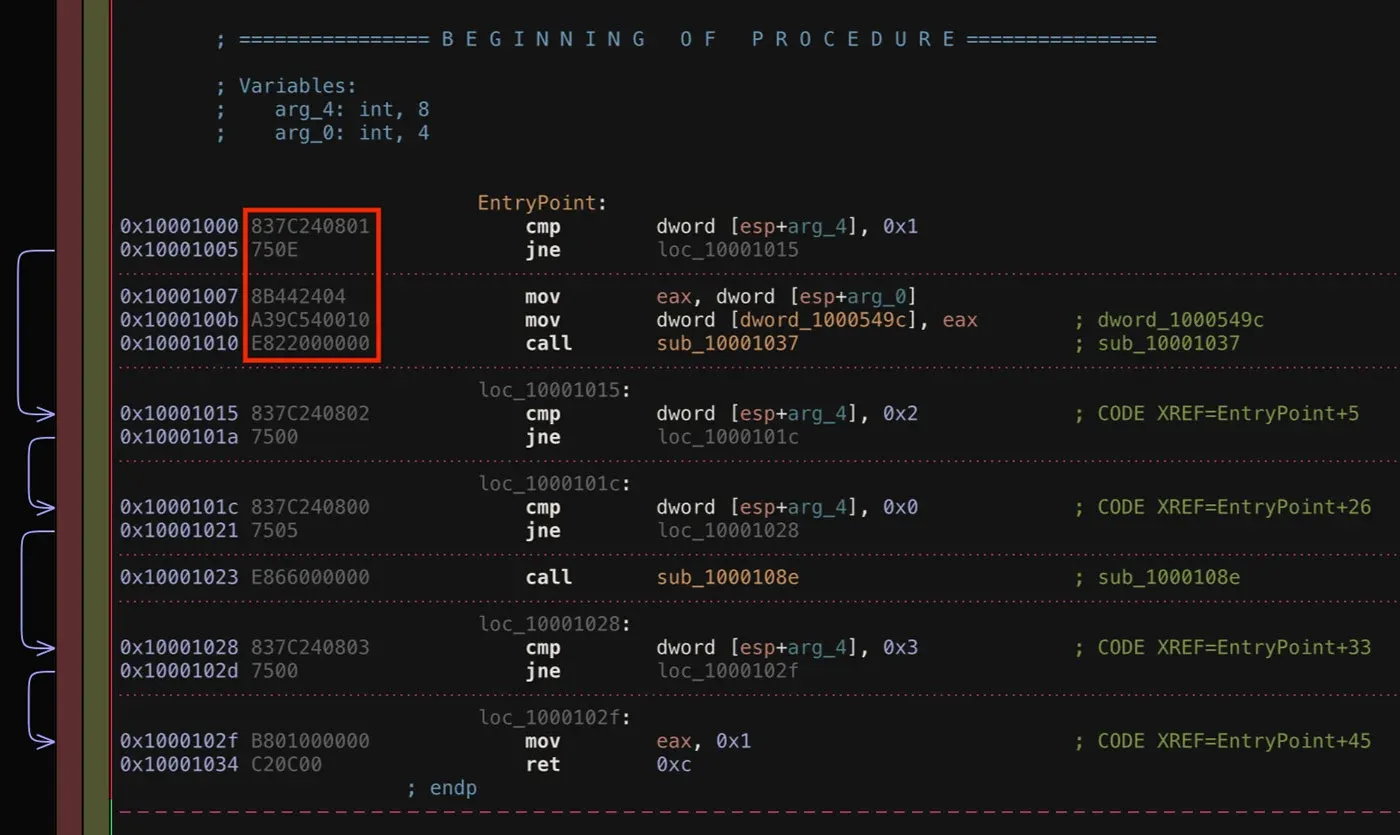
Figure 2: Instructions Immediately After Entry Point
The byte string shown here hones in on the first instructions in this procedure:
83 7C 24 08 01 75 ?? 8B 44 24 04 A3 ?? ?? ?? 10 E8
This rule is effective, but does not cover the entire procedure. Depending on inclusion or exclusion of certain PureBasic options in the source code itself, this procedure can change. Therefore, to write a rule which is resilient to any of this type of change, a reference set of benign DLLs compiled using PureBasic must be used. Starting with the source code for a sample DLL which has no user code, a set of “hello world” DLLs were compiled using PureBasic versions 4.10 to 5.71. By analyzing the reference DLLs created by this process, an improved YARA rule for detecting PureBasic DLLs was developed. This new YARA signature is provided at the end of the blog.
The next step is to execute the DLL in an analysis environment and observe the execution in a debugger. By placing a breakpoint on the DllRegisterServer export location in Figure 3, the malicious code in the DLL may be examined.
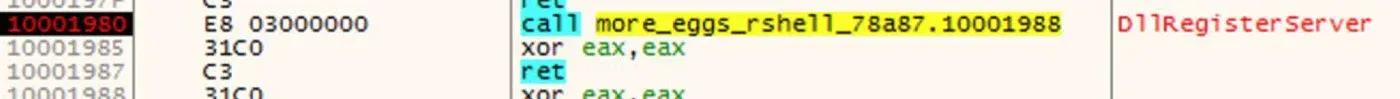
Figure 3: DllRegisterServer Export Location
The IP address and port used to communicate with the command and control infrastructure are both obfuscated in an identical manner as shown in Figures 4 and 5. This obfuscation is a type of defensive evasion meant to prevent these indicators from being extracted during static analysis.[8] This same obfuscation technique is seen throughout the sample to hide various strings that are important for the malware’s execution.
![C2 IP Address 185.204.2[.]182](/_next/image?url=%2Fapi%2Fmedia%2Ffile%2FFigure-5-C2-IP-Address-185-1400x178.webp&w=3840&q=75)
Figure 4: C2 IP Address 185.204.2[.]182
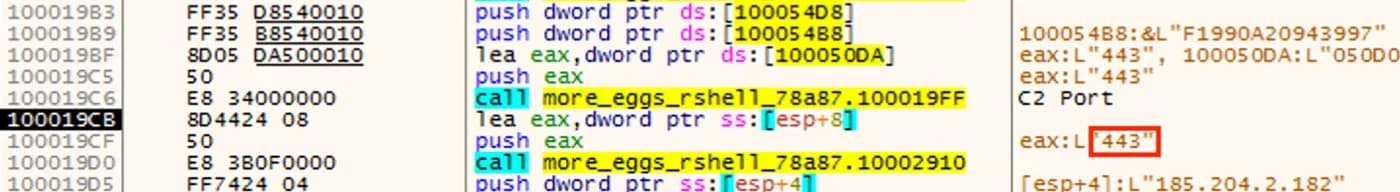
Figure 5: C2 Port 443
During dynamic analysis, the sample connects out to this IP address over HTTPS. It presents a cmd.exe shell for the adversary to use in the directory that the DLL is located. This allows the adversary to run arbitrary commands on the victim’s computer. This SSL traffic can be decrypted and observed as seen in Figure 6 showing the command prompt.
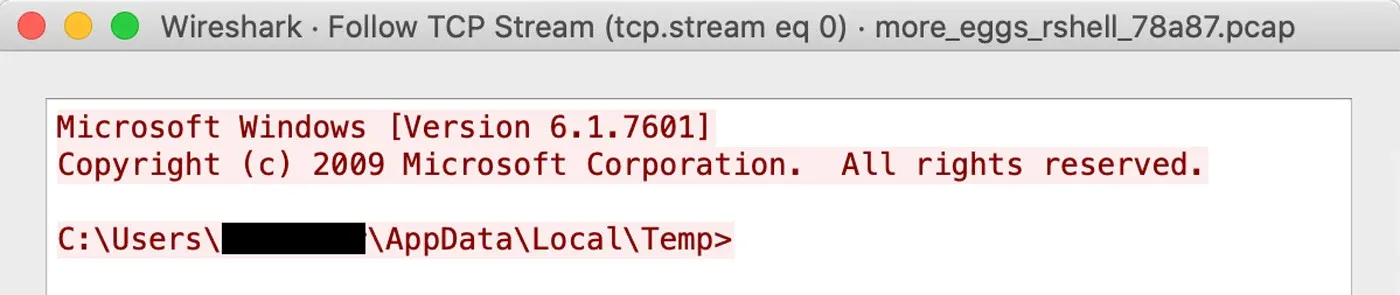
Figure 6: Decrypted Command Shell C2 Traffic
This particular sample is cryptographically signed using a software signing certificate. The organization name for this certificate is “D Bacte Ltd”. The details of the software signing certificate can be seen in Figure 7.
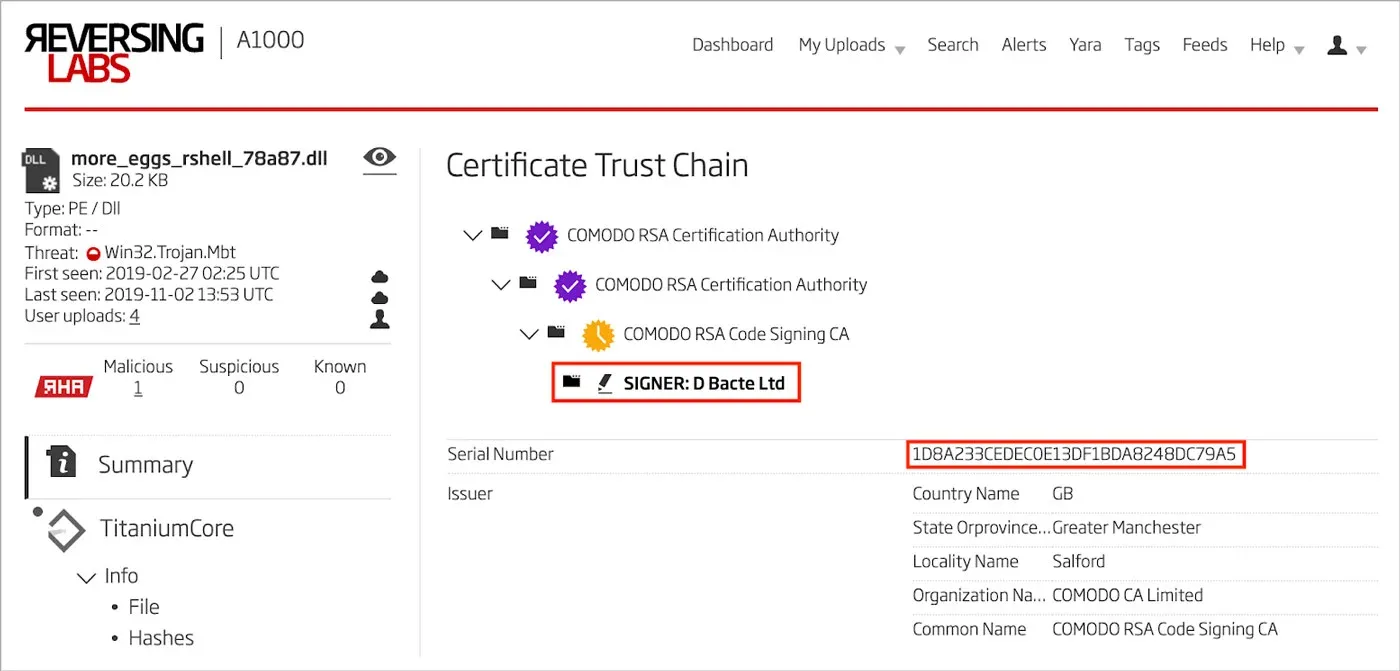
Figure 7: Software Signing Certificate
By using the search feature in the Titanium Platform, two additional related malicious DLLs are found that have the same serial number. [10] [11] Both of them are related to the FIN6 DLL and were signed using the same certificate.[12] The specific search index used to find them is the “cert-serial” query keyword. Details from these two files is shown in Figure 8.
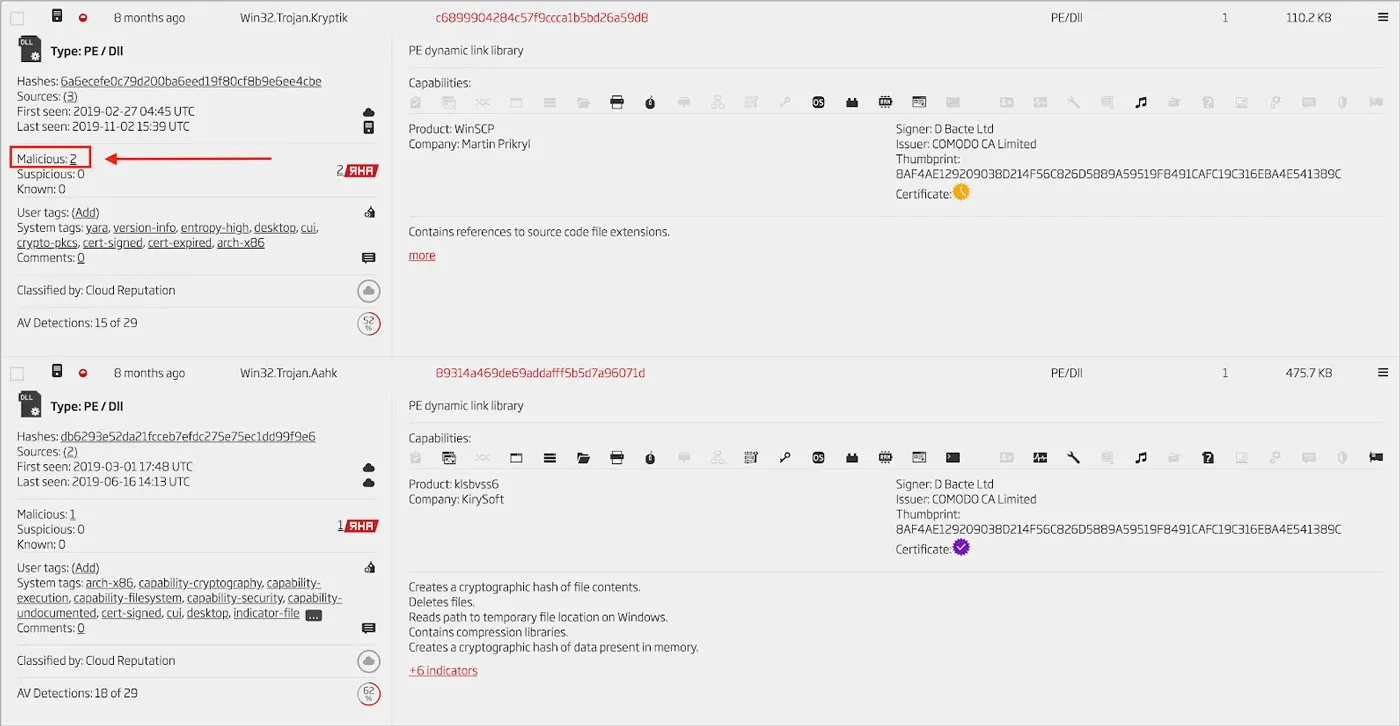
Figure 8: Files Related via Signing Certificate
In addition to these two files related via signing certificate, one additional file is found to be related via the ReversingLabs Hash Algorithm (RHA). This algorithm finds files with similar functionality and features, often leveraged by threat hunters to pivot during their analysis.[13] This additional file can be seen in Figure 9.[14]
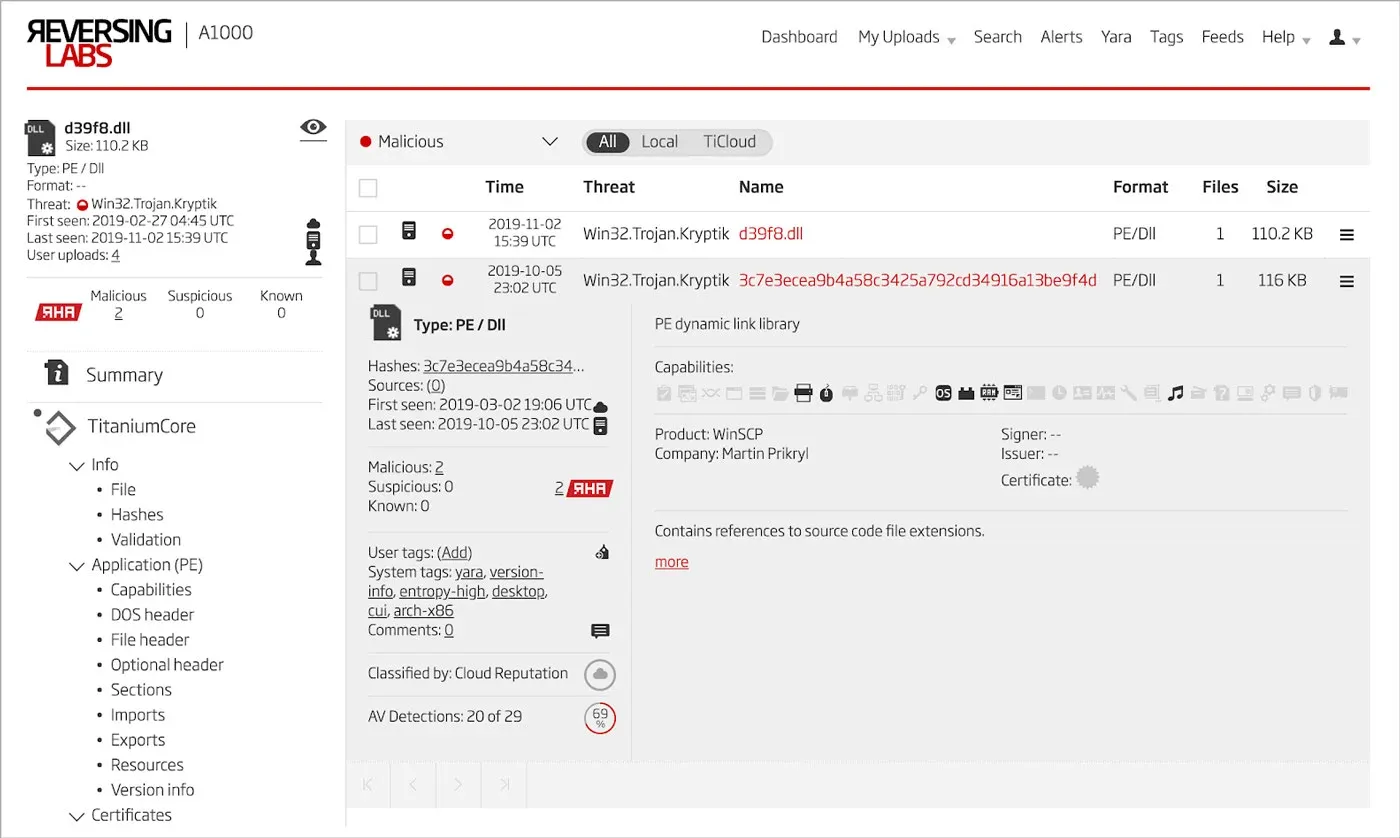
Figure 9: Malware Related via RHA
In addition to these three related malware files, a cluster of five more files can be found by focusing on the specific bytes of the obfuscation algorithm used throughout the sample. These additional files are quite interesting in that there is no other clear relationship between them and the main sample in question. According to information about the More_eggs javascript backdoor found on the open source, it is being peddled as malware-as-a-service (MaaS) in the underground.[15] The source code for the obfuscator found in this reverse shell DLL is probably being reused by the MaaS provider in other malware files. A full set of identifying hashes of these additional files all related by code reuse is provided at the end of the blog. A YARA rule for detecting this obfuscation technique is provided at the end of the blog.
As we have seen, there are multiple methods one can use in the Titanium Platform to discover related malware files starting with a single malicious DLL. In addition to focusing on code reuse across malware families, checking for abused certificates used to sign other files can reveal additional campaigns from the same adversary. Finally, using multiple static features in the files, the ReversingLabs Hash Algorithm can reveal even more files that may not have any other obvious linkages to the sample in question.
MD5 | 3b9646bf2d791e5ef4633e802f23e305 |
SHA1 | aeedcec7df9cf5d1241649c8066e652d688da4b3 |
SHA256 | 78a87d540c1758c6b4dcabb7b825ea3a186ef61e7439045ece3ce3205c7e85a2 |
ssdeep | 384:a2Ln/QKEX+olUWivxFqlveUigMK6js28h:apKEJlU1Uni7Kgs28h |
Import Hash | 0a0a6d30a8b0852b78b5c722c5688921 |
Cert Serial | 1d8a233cedec0e13df1bda8248dc79a5 |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 20728 |
Compile Timestamp | 2017-07-21 15:43:17 |
First Seen | 2019-02-27T02:25:43Z |
MD5 | c6899904284c57f9ccca1b5bd26a59d8 |
SHA1 | 6a6ecefe0c79d200ba6eed19f80cf8b9e6ee4cbe |
SHA256 | d39f8aa90d54fd010484d7bb54c18549c3f03b02385020a35589dbe49e979bab |
ssdeep | 3072:L/5Xcl35B58QHis6EYr6iWEQq1TvlYWWi2lO3HgmUkYp5V+ZK:raF3S1s6EYhB1VvldWNlOwfJDX |
Import Hash | d65969f77a5bbb126f5984c18adf9c0a |
Cert Serial | 1d8a233cedec0e13df1bda8248dc79a5 |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 112888 |
Compile Timestamp | 2019-02-21 12:01:42 |
First Seen | 2019-02-27T04:45:17Z |
|
|
MD5 | 89314a469de69addafff5b5d7a96071d |
SHA1 | db6293e52da21fcceb7efdc275e75ec1dd99f9e6 |
SHA256 | 511ad7705b216e7e472e496beba53856c97520eac12c83fa0d391594327e80f7 |
ssdeep | 12288:/qKrUC3639ewCGQEbr0AC2VvpGV1OtQxd6+dxRk5aOE+Cj5TyvV01BQDpCY:/qKrUCqN9CGQEbr0AC2VvsVgwdbk5aOV |
Import Hash | e9bfa7a6ac5a0973e87f28d7aab26ddd |
Cert Serial | 1d8a233cedec0e13df1bda8248dc79a5 |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 487160 |
Compile Timestamp | 2019-02-21 10:36:05 |
First Seen | 2019-03-01T17:48:00Z |
MD5 | 70f299ab247519e2dda8e172ae346277 |
SHA1 | 3c7e3ecea9b4a58c3425a792cd34916a13be9f4d |
SHA256 | db93d7f80dddb450e0efeabb302d4e6d48a53457309a6369760007911b8f4af8 |
ssdeep | 3072:R/5Xcl35B58QHis6EYr6iWEQq1TvlYWWi2lO3HgmUkYp+V:JaF3S1s6EYhB1VvldWNlOwfJi |
Import Hash | d65969f77a5bbb126f5984c18adf9c0a |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 118784 |
Compile Timestamp | 2010-08-01 10:32:37 |
First Seen | 2019-03-02T19:06:00Z |
MD5 | ec885733d385c50954bdbb8b76e8b33d |
SHA1 | af2d788829c401319522de8f8cd43659137c4ed7 |
SHA256 | 06cc276d474aa6295b1034ce4ee110681fcd45a2897e6891867036bf4ecc6fd3 |
ssdeep | 3072:IYtL4J6vafaEI/gISKDgU8JuD6A7WcCUEDTpeL9kZ6owF+5cJ2LLtUhEKNqAdy:VtLtZEIYId8k2IChD166zwF+o2Li8E |
Import Hash | b293d2c7113526ce6d7caceb0f7f4012 |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 247808 |
Compile Timestamp | 2001-08-17 20:52:32 |
First Seen | 2019-10-24T06:07:05Z |
|
|
MD5 | fe2d6b4511ac81221684a5f6a0634a4b |
SHA1 | d44f36b61ae119b1109829d8b2b2230b1d51cc6f |
SHA256 | 09ed9ba079a9d73291aff33b654f9b92b2b277049bc908b5b2359d9b8766bd4b |
ssdeep | 1536:IMgAK2KE7gFlvM3gkb0tuWXOvkJtxfVpICdtJ4n/5RbOhekj:9gAKVsgFl1kApJJt1cCLJqxRb/k |
Import Hash | 88f82612e092beed65357b6b88dda282 |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 125440 |
Compile Timestamp | 2019-01-03 8:34:14 |
First Seen | 2019-09-07T14:01:31Z |
|
|
MD5 | 14503cc985d8a9517fa530293865dae4 |
SHA1 | 6a2320c4b2782659cdbe358f8ea348d1a7c7e010 |
SHA256 | 683ab2f2dd56486c9dcd6ee3593d2b5f69cd354713fee46abd5ab4e8e6ac3646 |
ssdeep | 6144:SC0nhiurEfFN98UX/CXTVSWHSg/N1NiseD:SC0hHGBPEV/bN1zeD |
Import Hash | 887bae442dd37f1dc38db6af1a67e0ee |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 243712 |
Compile Timestamp | 2001-08-17 20:52:32 |
First Seen | 2019-09-17T21:03:25Z |
|
|
MD5 | 39702286994d7023b3d002cf31e1a6ad |
SHA1 | d2c57b707099ed02e2f2a32600d5356ee2e0d1d0 |
SHA256 | bb4346b5d92cf4b0333096c2d2da785e30893ee3c60b700a79bb26df7f349e04 |
ssdeep | 3072:F13opWebS6mwwk0CB387bbsQoJSc8sj5fzTt/fBNC0fX:LA8Po836jjFTx7tfX |
Import Hash | 9f6f979fc06c9cd0b73dd25469a8ad6f |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 151552 |
Compile Timestamp | 2014-02-26 1:43:53 |
First Seen | 2018-04-17T05:35:36Z |
|
|
MD5 | 302461e359118d3b8024dab1c75e7ff9 |
SHA1 | eda80c82c81f7439e8221e05dc3abd59b322a5e0 |
SHA256 | f25a4f09d8115bc7781e31356a082143182925529e7d7548ea5ff139c3b37afd |
ssdeep | 6144:G1C2gy43AgNoZ97WwaEkzp+bQLx64hLQD:G1C2gy596VfpZED |
Import Hash | 574fc17ae9337d6a0c26327a263a2a0f |
File Type | Win32 DLL |
Magic | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
File Size | 243200 |
Compile Timestamp | 2019-07-05 11:50:34 |
First Seen | 2019-07-12T17:59:27Z |
185.204.2[.]182 |
rule PureBasicDLL
{
meta:
author = "Malware Utkonos"
date = "2019-11-02"
strings:
$op1 = { 83 7C ( 24 | 25 ) ?? 0? 75 }
condition:
pe.DLL and all of them and
$op1[1] at pe.entry_point and
for 4 i in (1..#op1) : ( @op1[i] >= pe.entry_point and @op1[i] <= pe.entry_point + 100 )
}
rule ObfuscatorDLL
{
meta:
author = "Malware Utkonos"
date = "2019-10-05"
exemplar = "78a87d540c1758c6b4dcabb7b825ea3a186ef61e7439045ece3ce3205c7e85a2"
strings:
$op1 = /(\x8d\x15.{4}\x8d\x0d.{4}\xe8.{4}){3}/
condition:
pe.DLL and all of them and
uint32(@op1 + 13) - uint32(@op1 + 30) == uint32(@op1 + 30) - uint32(@op1 + 47)
}
[1] https://malpedia.caad.fkie.fraunhofer.de/actor/fin6
[2] https://securityintelligence.com/posts/more_eggs-anyone-threat-actor-itg08-strikes-again/
[3] https://malpedia.caad.fkie.fraunhofer.de/details/js.more_eggs
[4] https://usa.visa.com/dam/VCOM/global/support-legal/documents/fin6-cybercrime-group-expands-threat-To-ecommerce-merchants.pdf
[5] https://attack.mitre.org/groups/G0037/
[6] 78a87d540c1758c6b4dcabb7b825ea3a186ef61e7439045ece3ce3205c7e85a2
[7] https://github.com/Yara-Rules/rules/blob/master/Packers/packer.yar
[8] https://attack.mitre.org/techniques/T1140/
[9] https://attack.mitre.org/techniques/T1116/
[10] 511ad7705b216e7e472e496beba53856c97520eac12c83fa0d391594327e80f7
[11] d39f8aa90d54fd010484d7bb54c18549c3f03b02385020a35589dbe49e979bab
[12] 1d8a233cedec0e13df1bda8248dc79a5
[13] https://www.reversinglabs.com/technology/reversinglabs-hash-algorithm
[14] db93d7f80dddb450e0efeabb302d4e6d48a53457309a6369760007911b8f4af8
[15] https://medium.com/@quoscient/golden-chickens-uncovering-a-malware-as-a-service-maas-provider-and-two-new-threat-actors-using-61cf0cb87648
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial