
Within the last decade, ransomware emerged as the preeminent cyber threat facing both public and private sector organizations. Data from firms that track ransomware infections suggest that a large percentage of organizations are victimized by ransomware in any given year. For example, 44% of the more than 5,000 firms surveyed by the security firm Sophos for its annual ransomware report in 2021 said they had been hit by ransomware in the last two years. A majority of those incidents resulted in cybercriminals successfully encrypting data before they were detected and removed.
The stakes involved in ransomware incidents have risen right along with the frequency of ransomware attacks. What started out as nuisance attacks a decade ago quickly evolved such that, by 2016, ransomware was shutting down medical facilities like Hollywood Presbyterian Hospital. The NotPetya wiper attack in 2017 raised the profile of ransomware even higher, showing how determined governments like Russia’s can leverage malware to disrupt both the public- and private sectors and inflict high costs on nations like Ukraine. By 2021, the scourge of ransomware was growing unchecked and crippling critical infrastructure like the Colonial Pipeline on the U.S. East Coast and facilities operated by meat processor JBS. Attacks on medical facilities became commonplace and were linked to a death at an affected facility. The attack that temporarily shut down the Colonial Pipeline in the eastern United States, in contrast, was linked to an affiliate of the for-profit Darkside ransomware group.
A ‘perfect storm’ propels ransomware attacks
How did we get here? Multiple conditions have aligned to make ransomware the significant threat it is today - a kind of “perfect storm” of factors that have produced a global crisis.
First, ransomware attacks benefit from a large and vulnerable population of complex IT systems - many relying on legacy software with known vulnerabilities. Recent, widespread flaws like the ProxyShell and PrintNightmare vulnerabilities, for example, have opened the door to malicious actors and set the stage for ransomware attacks.
The advent of crypto currencies like Bitcoin has also aided ransomware groups by streamlining ransom payments and cash outs - historically the biggest impediments to online crimes.
Incidents like the Colonial Pipeline attack show us that sprawling IT infrastructure and accommodations for remote access have also contributed to ransomware attacks. The Darkside ransomware group, for example, exploited an unmanaged VPN concentrator to gain access to Colonial’s network.
Finally, both criminal and nation-state actors benefit from patchy enforcement of cyber crime laws and hazy rules of engagement around cyber offensive operations. That has produced a ransomware landscape populated by cyber criminal gangs, nation state actors and groups that straddle both.
Desperate times, desperate measures
Tackling ransomware threats has been a top priority for both law enforcement and private sector security vendors for years, but the recent attacks affecting critical infrastructure in the U.S. has injected urgency into the government’s response to the ransomware threat.
Previously controversial strategies like “hack back” are getting traction. For example, following the attack on the Colonial Pipeline, servers and BitCoin wallets used by the Darkside ransomware group and its affiliates were seized and disabled, forcing the group to cease operations.
At the same time, the Biden Administration has rallied like-minded countries to its Counter Ransomware Initiative (CRI). That group will focus on improving cross border coordination in areas like network resilience, money laundering via virtual currencies, criminal investigations and prosecution, and diplomatic cooperation.
We’re gonna need a different boat
The bad news: neither stepped up response nor better international cooperation will make the ransomware problem disappear. There are simply too many factors that make ransomware an appealing proposition for both criminals and rogue governments. Instead, as the threat landscape evolves, we should expect to see the tactics used by ransomware actors adapt.
For example, the strong federal response in the wake of the Colonial Pipeline and JBS ransomware attacks may well make ransomware groups think twice about crippling critical national infrastructure in exchange for ransom. But that won’t prevent them from targeting infrastructure owners. Instead, we may start to see a bifurcation in ransomware attacks, with classical ‘encrypt and extort’ attacks reserved for smaller and less important targets, while bigger targets are extorted in quieter and less disruptive ways intended to avoid scrutiny.
Rather than looking to governments or law enforcement to make the ransomware problem go away, organizations need to improve their ability to detect and prevent emerging ransomware attacks. To quote Chief Brody from the movie Jaws, “we’re going to need a bigger boat” to stop ransomware. What does this “bigger boat” look like? Here are some thoughts.
Quality threat intelligence is key
Ransomware is too sophisticated and too diverse to succumb to any “silver bullet” security solution or tactic. To stand up to ransomware groups, therefore, it is paramount for organizations to develop an in-depth understanding of a ransomware group’s tooling, capabilities, and behaviors leading up to, during and after a ransomware infection.
To get to this level of understanding, your organization needs up-to-date threat intelligence from credible sources. With threat actors’ tactics and techniques unveiled via actionable threat intelligence, security teams know how to bolster cyber defenses.
What makes good threat intelligence?
When speaking of ransomware threat intelligence (TI), the focus should be twofold: the ransomware campaign and the final ransomware malware payload. The reason for this is clear: ransomware attacks never start with ransomware. Instead, deployment of the ransomware malware is among the final stages of an attack. By focusing on the precursors to ransomware attacks and how they track known malware families, organizations can disrupt evolving ransomware incidents in their early stages, lessening the damage and lowering the cost and time needed to recover.
What constitutes ransomware threat intelligence? Depending on the sort of information, intelligence can be tactical, or operational - or both.
- Operational threat intelligence includes information about the “how” and “where” of an attack. It can help you track threat trends, identify the actors behind specific threats and identify malicious tactics, techniques, and procedures.
- Tactical threat intelligence is more specific to a campaign. It provides you with the actual network, file, and other indicators associated with ransomware groups. While tactical threat intelligence doesn’t tell you much about the “who” or “why” of attacks, it provides a wealth of information to support the work of security teams’ as they combat ransomware within your environment.
Local threat intelligence: Use it!
If your organization is just standing up its threat intelligence program, you may encounter a common problem: where (and how) to start? After all, security teams often have little or no budget to fund TI programs. Even with money to spend, figuring out what threat information you need, what is worth paying for, and how to use it is a huge challenge.
The good news is that the answer to the question of “where to start?” is right under your nose, and costs you almost nothing to leverage. In fact, threat intelligence harvested from your own environment - network scans, malicious emails, malicious redirects, intrusion detection alerts - is among the most valuable and actionable information your team has. Collect it!
Leverage free threat intelligence feeds
After you identify internal sources of threat intelligence, your next stop should be the many, free external threat intelligence sources. Open source threat intel feeds come in many forms and include information feeds from VirusTotal, the FBI’s Infraguard, SANS ISC Storm Center and offerings by information technology and information security firms.
These can be valuable sources of information on new and emerging threats. Free threat intelligence feeds can corroborate information gathered internally, or via commercial threat intelligence sources. For organizations that are building out a threat intelligence program, free threat intelligence feeds can also provide a foundation for threat hunting activity without incurring substantial costs for licensing.
However, as the saying goes: “you get what you pay for.” Free threat intelligence feeds are offered “as is” and are often voluminous and poorly tailored to the needs of your organization. That can make them difficult to operationalize. Improperly used, data from these free feeds can inject noise into threat hunting and threat intelligence functions, impairing response.
Furthermore, free threat intelligence sources and data structures are often not standardized and prone to changes - or even to discontinuation. That can significantly impact the ability to absorb the threat intelligence or impose costs on your organization to groom and maintain the data, making a “free” resource suddenly expensive.
Timely data is key
Threat intelligence data loses value over time. Intelligence on emerging phishing attacks or active exploitation of a new vulnerability is of little value if it is delivered too late for attacks to be detected and blocked. And the window of opportunity to act on threat intelligence may be measured in days or weeks, not months. For example, ransomware groups jumped on disclosure of the PrintNightmare Windows vulnerability in July, 2021.
By early August, exploits for the vulnerability were being leveraged by groups like Conti to gain a foothold within target environments. In short: old data is of little value for many of the threat intelligence use cases. That’s something to keep in mind.
Pay attention to coverage, reliability and security
The reliability of threat intelligence data is paramount. It goes without saying that threat intelligence is not vetted for both false negatives and false positive indicators, its utility decreases, as organizations consuming the data will be overwhelmed with misleading indicators.
Organizations considering threat intelligence feeds also need to pay attention to its coverage: the geographies, industries and organization types reflected in the data. Ransomware threats vary based on these factors. If a threat intelligence source is not focused enough, or the coverage is too small, it might not bring much value to a security, incident response or threat hunting organization.
Finally, organizations considering implementing threat intelligence feeds should consider the availability and security of those feeds. Mature threat intelligence programs demand stable, “always on” threat intelligence streams to feed ongoing analysis. But that creates risks, as well. Data poisoning or malicious attacks that exploit the access provided to threat intelligence providers should be part of an organization’s risk planning. This is a more and more important requirement with the rising trend of supply chain attacks such as SolarWinds and Kaseya.
How ReversingLabs Ransomware Feed can help
ReversingLabs Ransomware Feed incorporates the concepts and recommendations above in order to offer a new type of threat intelligence feed capable of supporting multiple cyber security teams’ needs.
File repository provides deep intel
The starting point of all the indicators in our ransomware feed is ReversingLabs’ file repository, one of the largest file sets available on the market. On average, 2.5 million unique malware files are analyzed every day to produce a wealth of ransomware-related datasets that encompasses more than 13 billion classified files, 3 billion of them malicious.
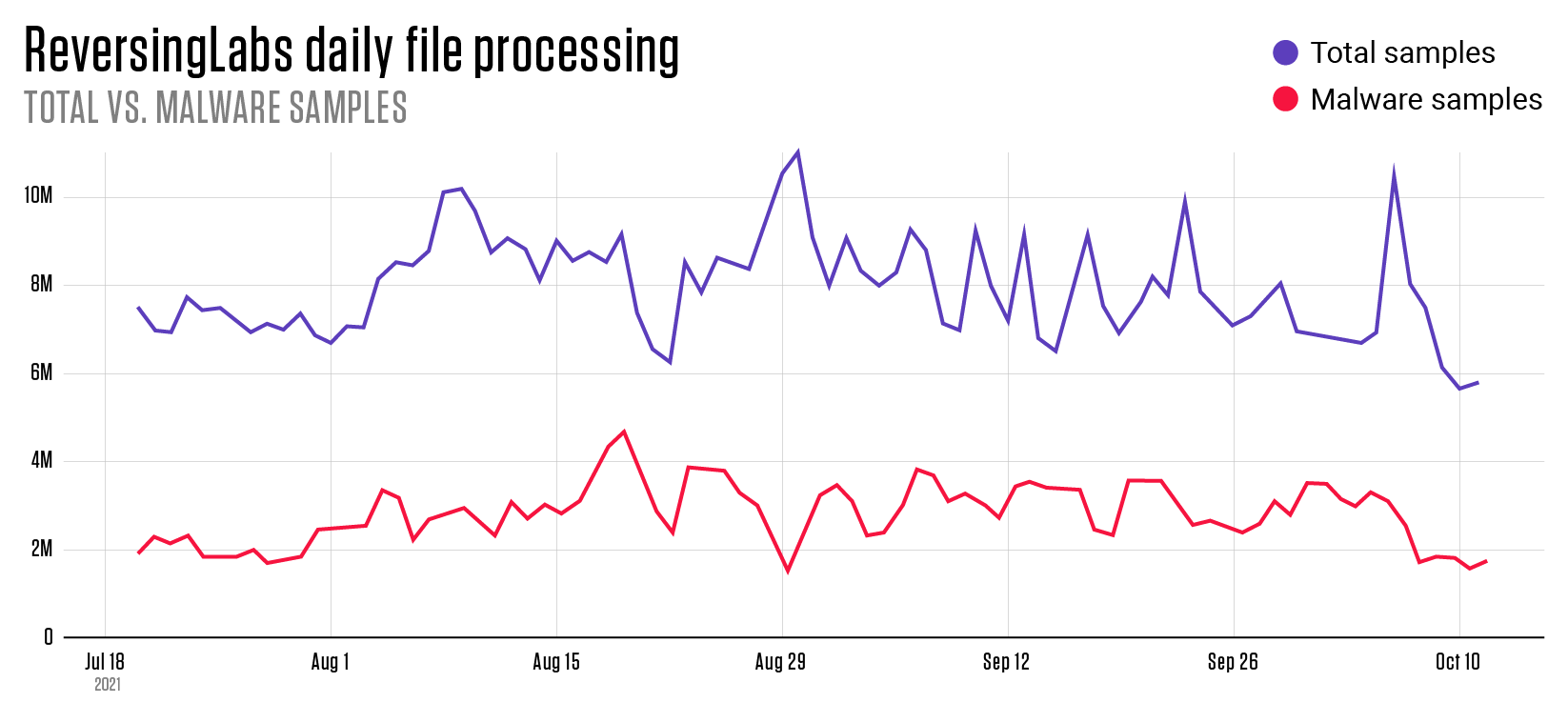
Figure 1: ReversingLabs daily file processing: Total vs. Malware samples
This deep knowledge base of good, bad, and suspicious files means that organizations that leverage our threat intelligence feed can count on having the latest insights on new and emerging threats. Our threat indicators are a great resource for blue teams to augment the defense system’s intrusion monitoring capabilities.
Threat modeling using MITRE ATT&CK
ReversingLabs uses advanced static and dynamic analysis engines to generate both network and file indicator lists. Those indicators are matched to standardized MITRE ATT&CK tags to streamline threat modeling and provide a more complete picture of cyber risk across an organization.
Security engineers can use these threat models to determine which detection methods are missing or misconfigured. They can also signal what additional logs would be beneficial to collect or create, or if existing prevention and blocking rules are aligned with threats, or outdated and in need of tweaking or replacement.
Timely and relevant
ReversingLabs threat landscape monitoring is delivered in a timely manner with wide scope, but focused on relevant threats. Our Ransomware Feed is also timely: publishing new threat indicators with the smallest possible delay from a first encounter “in the wild.” Our feed is also constantly evolving. New technique, tactic and procedure (TTP) yields a fresh set of ideas and hypotheses to test for threat hunting teams working or outside the perimeter.
Our strict vetting process for new intelligence also ensures indicators that reach customers are of high quality, with a very low number of false positives. That high fidelity makes the ReversingLabs Ransomware feed ideal for triaging SOC alerts, training SIEM/SOAR solutions to detect new security incidents, or even filtering and blocking network traffic.
Customizable
ReversingLabs global network gives it access to the newest malware samples and network signatures. Detection engineers use our technology to test and improve the effectiveness of cyber defense systems: creating new detection rules or fine-tuning existing detections. ReversingLabs download services allow customers to download any detected malware samples for use internally as part of “live fire” testing.
The network and file data is served with a rich metadata context like threat identification, MITRE ATT&CK indicators, attack lifecycle stage, and a list of actors - the usual suspects tied to threats identified.
To generate indicators, several methods are intertwined: static and dynamic file analysis, malware configuration extraction, and malware URI payload detection. We then automatically enrich the data to additionally bolster the dataset (e.g. adding threat actor metadata). Once the data preparation is done, multiple correlations make it possible to analyze the kill chain of the entire attack.
Figure 2: Ransomware Lifecycle
Diverse applications
ReversingLabs Threat Intelligence Feed for Ransomware can be leveraged in a number of ways by your internal security teams. Among the applications of the information provided via the feed are:
|
Application |
Description |
|
Security events triage |
Data from our Ransomware feed can be used to identify and prioritize security events that may indicate attacks in progress. |
|
Threat landscape monitoring |
Use our Ransomware Threat Intelligence feed to monitor changes to the threat landscape including the emergence of new malware, phishing attacks and more. |
|
Threat hunting |
Data from the Ransomware Threat Intelligence feed can help identify threats within your organization including files, behavior and malware that is a precursor to ransomware deployment. |
|
Threat modeling |
Fine tune your defenses and remediations using our Ransomware Threat Intelligence feed to test responses to known threats and malware. |
|
Security incident detection |
ReversingLabs Threat Intelligence feed can fine tune incident detection and incident response within your organization, providing IR teams with the latest threat data and indicators of compromise. |
|
Active threat blocking |
Analysis of existing and emerging cyber threats on the Ransomware Threat Intelligence feed can inform your security team’s defensive planning and remediation efforts: identifying and closing off avenues of compromise exploited by ransomware groups. |
|
Improving cyber defense |
ReversingLabs Threat Intelligence feed doesn’t just allow you to defend against ransomware infections. It improves the overall defensive posture of your organization by providing information on a wide range of threats and malicious activity that might lead to a compromise of your organization. |
Contacting ReversingLabs
ReversingLabs threat intel is natively available in many threat intelligence platforms. You can request a free trial today from your vendor's marketplace or can contact us to find out more by emailing sales@reversinglabs.com.










