Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
“Software supply chain security is a critical risk and compliance issue, but most organizations approach it in a fragmented way. The lack of an all-inclusive structure leaves protection gaps.” Gartner Leader's Guide to Software Supply Chain Security
Most enterprises are struggling to identify and address software supply chain attacks and exposures with woefully uncoordinated and ineffectively tooling. Traditional AppSec testing solutions are overly focused on code vulnerabilities, which is only one category of software supply chain risk. Existing third-party cyber risk management (TPCRM) approaches fail to collect threat insights relevant to software and updates about to be released, acquired, or deployed. While the SBOM necessary first step towards software risk management, a list of components by itself cannot answer the critical question: “is this software package or update safe to release or deploy?” In addition to the SBOM, enterprises require an approach that automatically
Only Spectra Assure™ rapidly deconstructs software to provide the most comprehensive SBOM and risk assessment, and now RL has raised the bar for benchmarking software risks with the Spectra Assure SAFE Report.
The SAFE report brings visibility to software supply chain threats embedded within software components, including attack vectors beyond just vulnerabilities (malware, tampering, suspicious behaviors, and more) across the entire software binary. It delivers a summarized view for risk management stakeholders to scale up their program, while fully assessing software packages and updates for attacks and exposures (see Figure 1). Prioritization and remediation details are also provided to support risk mitigation collaboration with both internal and external software providers. To illustrate this, let’s dive into four key aspects of the SAFE report.
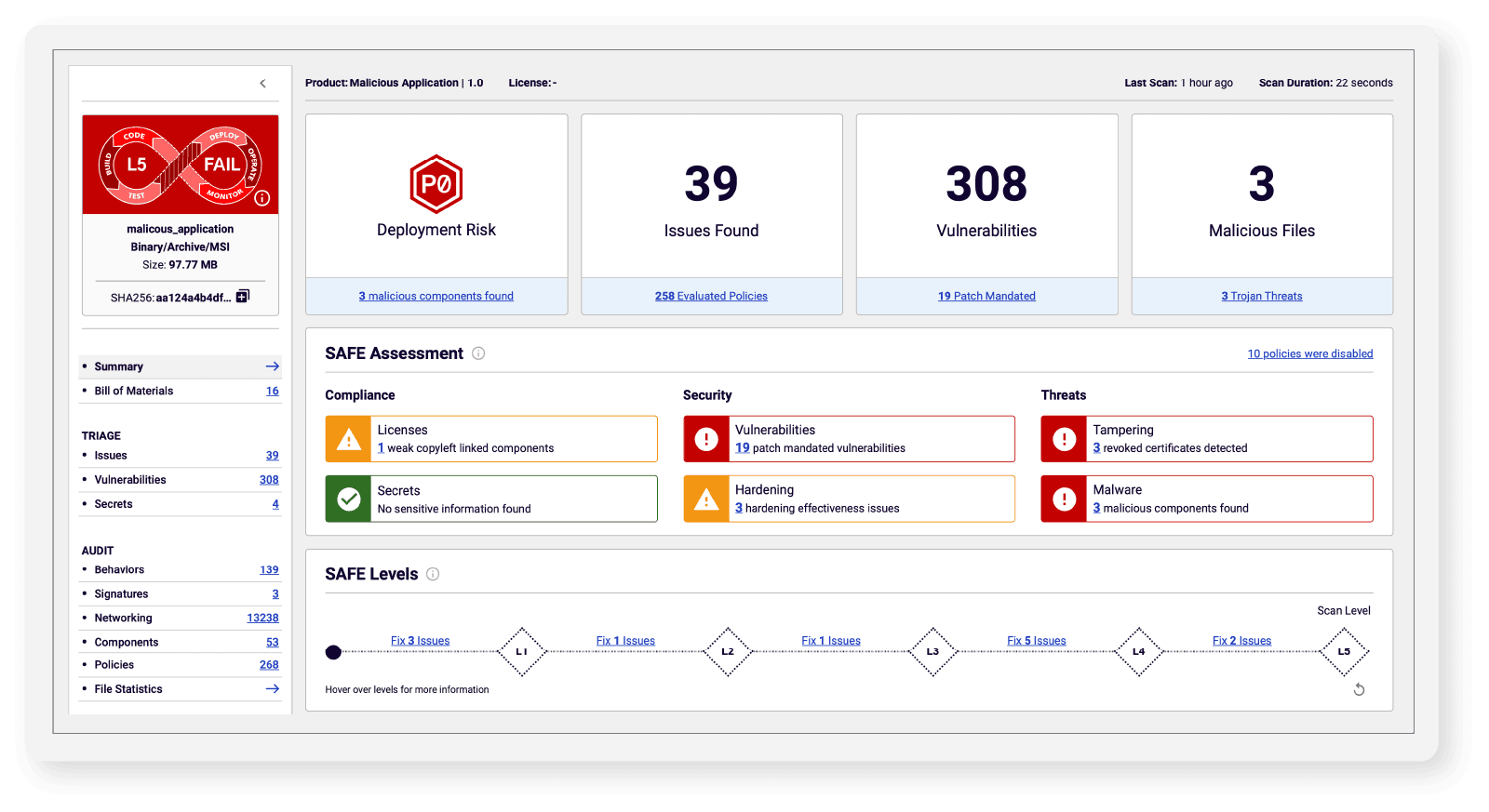
Figure 1: The SAFE report is your single source of truth to gauge the security hygiene of third-party software deployed across your organization.
The SAFE report meets the required data elements of the SBOM, including software versions, publishers, and licenses information across an entire application’s inventory (proprietary, commercial, open-source, and all build components). It is searchable to aid in zero-day incident response and exportable in CycloneDX and SPDX formats. This helps satisfy government regulations and guidance such as:
However, making tangible steps towards mitigating risk requires organizations to also identify which components represent immediate threats. The SAFE report does this by going beyond a simple inventory listing by mapping specific software supply chain threats like malware, tampering, vulnerabilities, and exposed secrets to specific components (see Figure 2). Presenting security data and insights in a clear, digestible format further enables organizations to validate the integrity of software components and collaborate on next steps for continual improvement.
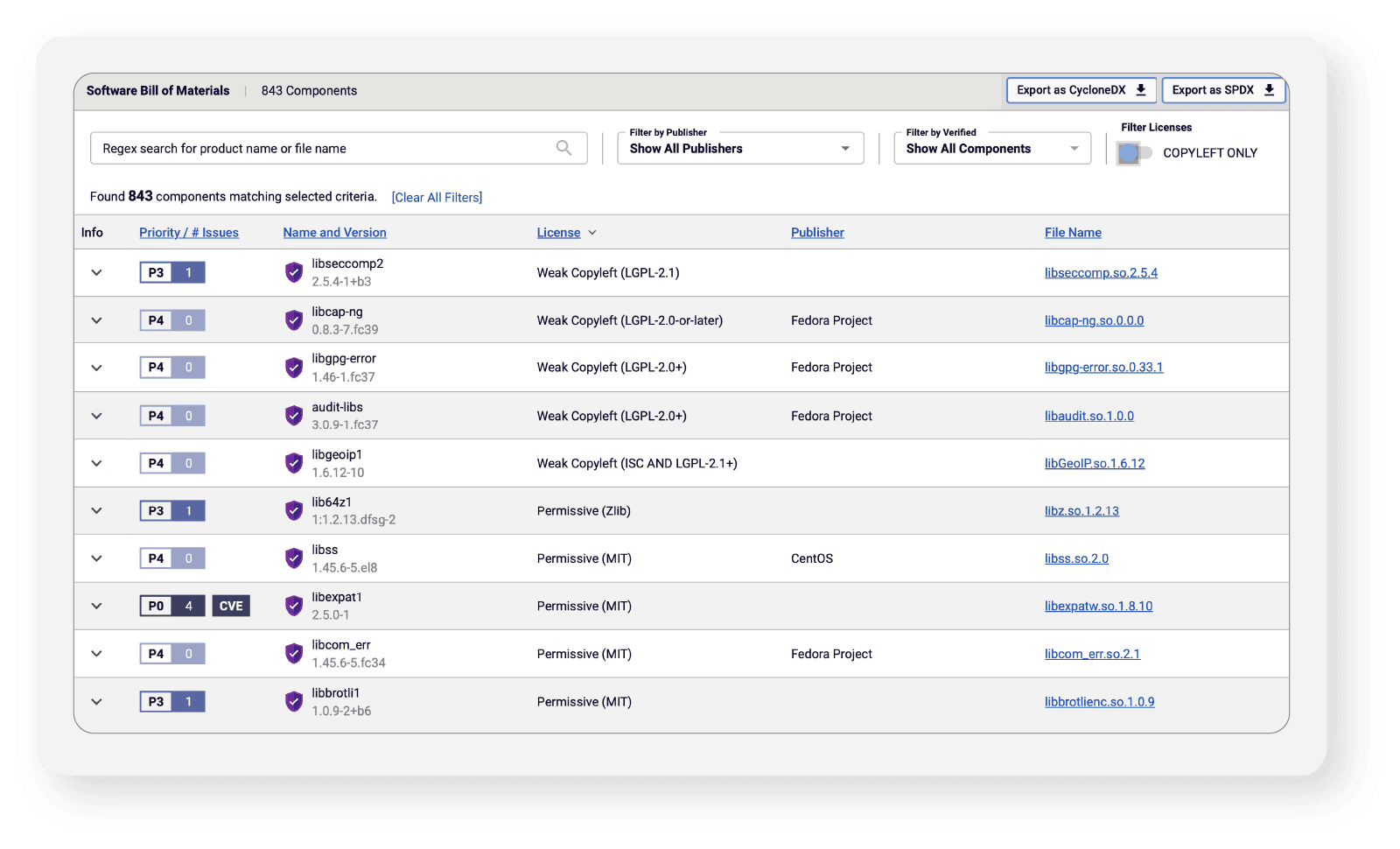
Figure 2: SBOMs within the SAFE report exceed NTIA standard by including the version and publisher of each component, along with critical risk information including embedded malware, vulnerabilities, and other threats.
The SAFE Assessment summarizes all identified issues across six risk categories based on shared characteristics ((see Figure 1). Criterion in each category are designed and prioritized to manage distinct cybersecurity risks effectively:
This categorizations simplifies the effort required to prioritize all of the findings and adjust the Go/No-Go criteria for issuing a red flag (or No-Go status) for each risk category to reflect varying risk toleration across different parts of an enterprise’s software portfolio. The SAFE report recognizes these policy changes and will update the status of a software package based on the new customization.
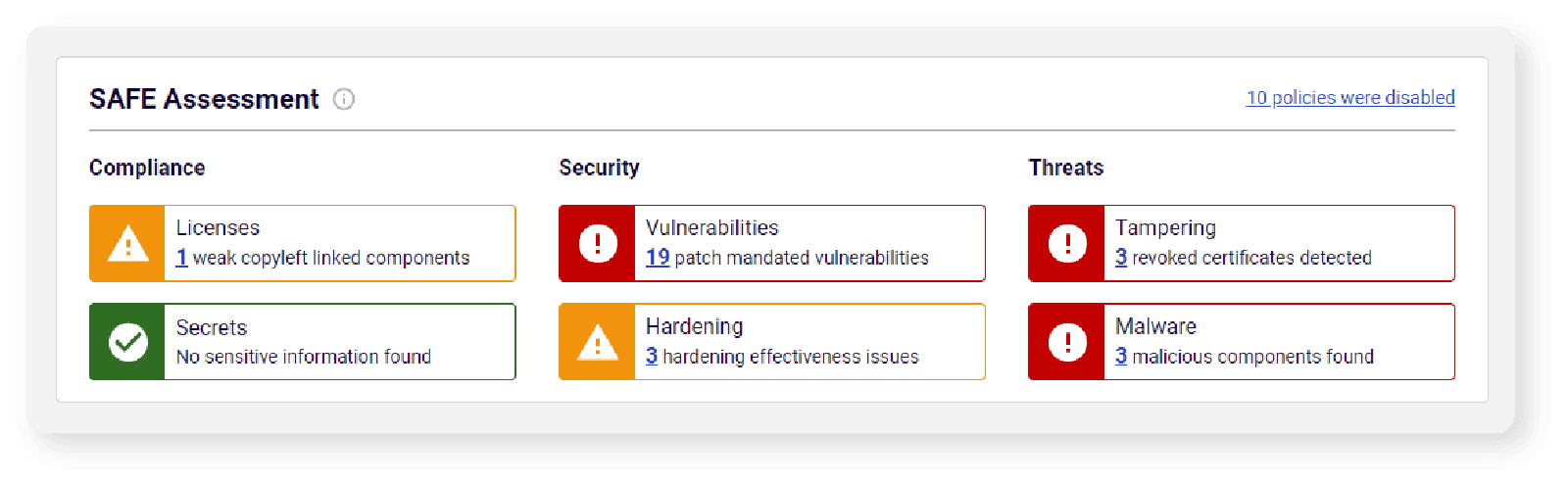
Figure 3: The SAFE Assessment provides a summary of all findings flagged in the most recent analysis and buckets them across six risk categories based on shared characteristics.
SAFE Levels enables non-technical stakeholders (e.g. TPRM, GRC, Procurement, and Legal teams) to gauge the risk that a specific software package presents to their business through a series of predefined, increasingly strict security policies. Organizations can customize Levels according to their risk tolerance for specific software packages or entire categories of software. The dashboard also indicates how many components require remediation for the software to attain the next SAFE Level. Technical teams are provided links to specific components and threat details needed to fix security issues as a series of manageable projects that reduce the burden on developers while improving software supply chain security.
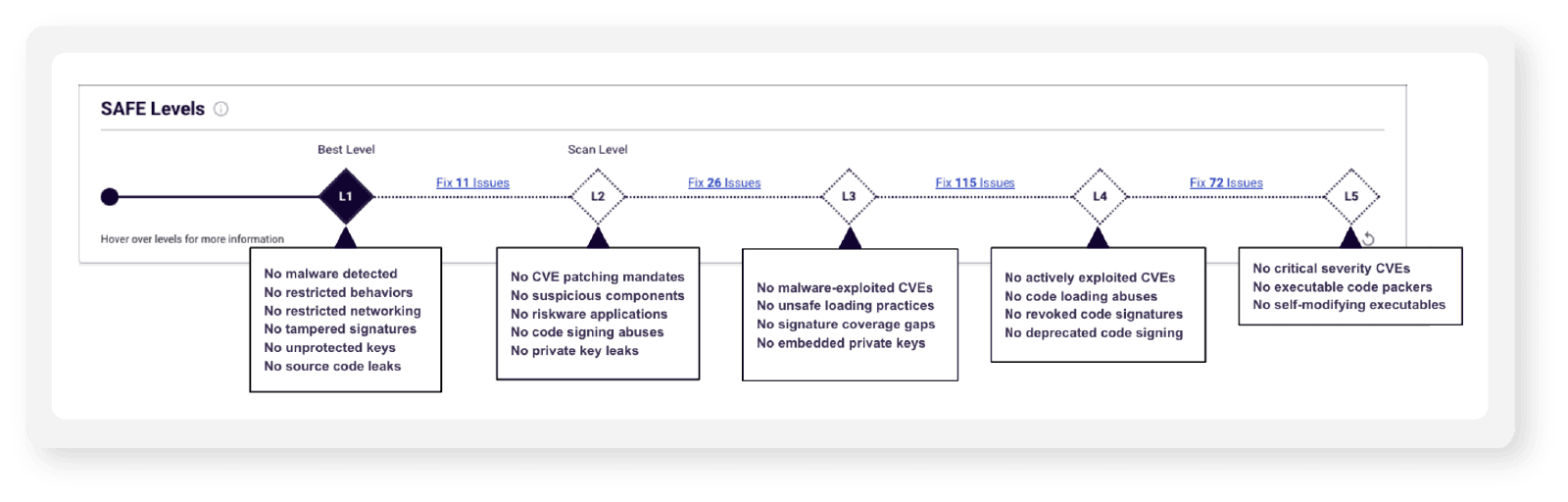
Figure 4: SAFE Levels makes it simple to gauge the risk that a specific software package presents to your business through a series of predefined, increasingly strict security policies.
SBOMs within the SAFE report exceed NTIA standards by including the version and publisher of each component, along with critical risk information including embedded malware, vulnerabilities, and other threats. The SAFE report enables collaboration and transparency with third-parties by allowing businesses to share their report directly with vendors and regulators. The SAFE report shareable link is:
Sharing the SAFE report with vendors directly helps to bring awareness to the most imminent security issues embedded within third-party commercial software and expedites remediation action plans. Sharing reports can also help meet both internal and external compliance requirements in order to prove due diligence in assessing third-party software risk.
Figure 5: Securely sharing SAFE reports enables collaboration and transparency across multiple internal and external stakeholders.
By delivering Spectra Assure’s AI-driven Complex Binary analysis results (i.e. a comprehensive SBOM and risk assessment of an entire application) in a single, digestible and shareable SAFE report format, ReversingLabs empowers organizations to:
By making information understandable and accessible to many stakeholders across multiple organizations, Spectra Assure supports a higher standard for evaluating actual software risk evaluations without relying on manual processes, a stagnant list of ingredients, or unquestioningly trusting self-attestations.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial