Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Today's enterprises run on commercial-off-the-shelf (COTS) software for nearly every critical function, from payroll and human resources to IT infrastructure - all provided by trusted vendors. Today’s businesses rely on a dense ecosystem of dozens, if not hundreds, of different third-party software providers to deliver business-critical products and services. The drastic rise in software supply chain attacks targeting third-party software providers, combined with increased government and regulatory oversight have spurred Governerance, Risk, and Compliance (GRC), IT, and Third-Party Cyber Risk Management (TPCRM) professionals to pay special attention to software vendors and the layers of risk that commercial software poses to their business.
There is good news on two fronts. First, new technology provides GRC, cybersecurity, and TPCRM professionals a primary control to identify the risk and threats associated with the commercial software coming into the enterprise in minutes without the need for source code. Second, these tools can be easily integrated into existing teams’ workflows enabling organizations to identify and rectify issues with third-party software. Hence, the introduction of Third-Party Software Risk Management (TPSRM), enabling proper ownership and scalable methods to determine whether third-party applications pose a material risk to the business.
TPSRM is a subset of Third-Party Cyber Risk Management (TPCRM) focused specifically on flagging threats and risks embedded in third-party commercial software. It defines the people, processes, and technology needed to help cybersecurity, IT, and risk professionals make informed software buying decisions before deploying across the IT environment. TPSRM aims to implement scalable controls to identify software supply chain threats in not only new software purchases, but any third-party commercial software already deployed across the environment.
Current approaches to TPSRM have heavily leaned on security questionnaires, penetration testing, security rating services, or even sandboxing to analyze commercial software packages. However these approaches are untenable in the long-term due to their cost and lack of coverage for the wider spectrum of application-level threats like malware, tampering, suspicious behaviors, and others.
To combat these challenges, organizations need to operationalize their third-party software risk management by embedding it into every stage of the software procurement lifecycle—from procurement to deployment and ongoing monitoring.
Although the responsibility for evaluating supply chain security risks of any prospective or new software vendor may reside with the TPRM or TRCRM team, the ongoing management and remediation of security issues presented by software consumed will undoubtedly fall across a variety of business functions.
As a result, it is critically important that organizations clearly define the roles and responsibilities within the organization to identify, detect, respond, and recover from software supply chain security issues that may arise throughout the lifecycle of software use. This includes the acquisition, deployment, maintenance, and ongoing monitoring of software.
Figure 1 below presents a high-level example RACI demonstrating a potential distribution of responsibilities across job functions for managing software supply chain risk:
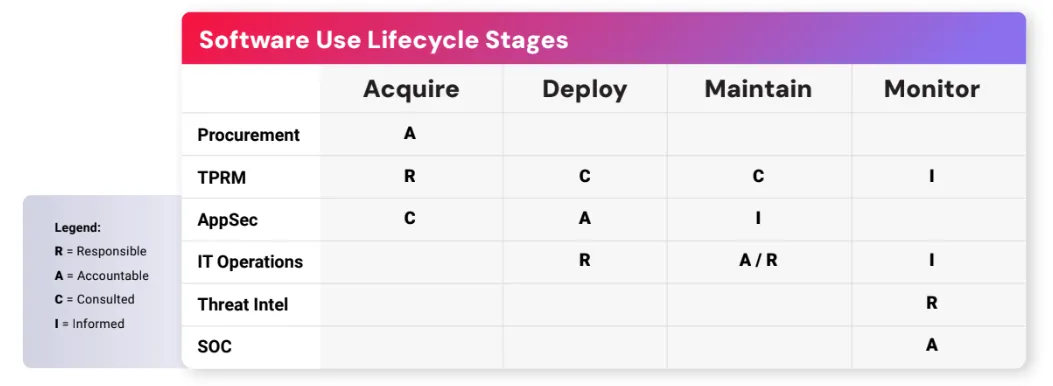
Figure 1: Aligning ownership within cybersecurity, risk, and IT functions will ensure specific controls and considerations are met when acquiring, deploying, maintaining and monitoring COTS software.
Functional groups within cybersecurity, IT, procurement, and risk management each draw from their respective disciplines to properly vet third-party software packages for embedded risks, ensure proper safeguards are in place, and monitor for zero-day threats to ensure rapid response.
Establishing repeatable workflows with consistent ownership is paramount to a sustainable TPSRM program. But without the proper technology to serve as your primary control, it’s extremely difficult (nearly impossible) to consistently verify that third-party software is safe to deploy in your environment.
Spectra Assure™ delivers the primary control that GRC, cybersecurity, and TPCRM professionals need to verify the risk and threats of software coming into the enterprise. It prevents software supply chain incidents by ensuring the software you purchase is free of costly threats. Spectra Assure’s AI-Driven Complex Binary Analysis delivers deep analysis of third-party software in minutes without the need for source code, providing a definitive Go/No-Go mechanism to assess third-party software risk.
The data analysis from Spectra Assure delivers the Software Assurance Foundational Evaluation (SAFE) report. The SAFE report is the most comprehensive SBOM and software risk analysis that identifies embedded threats like malware, tampering, vulnerabilities, suspicious behaviors, and more. Each section serves specific purposes to identify threats, prioritize fixes, and gauge an acceptable level of risk to your cybersecurity and third-party risk management teams. This data can be shared both internally and externally to coordinate with IT and Security Operations on implementing proper controls for known attack vectors and collaborate with vendors on required security fixes.
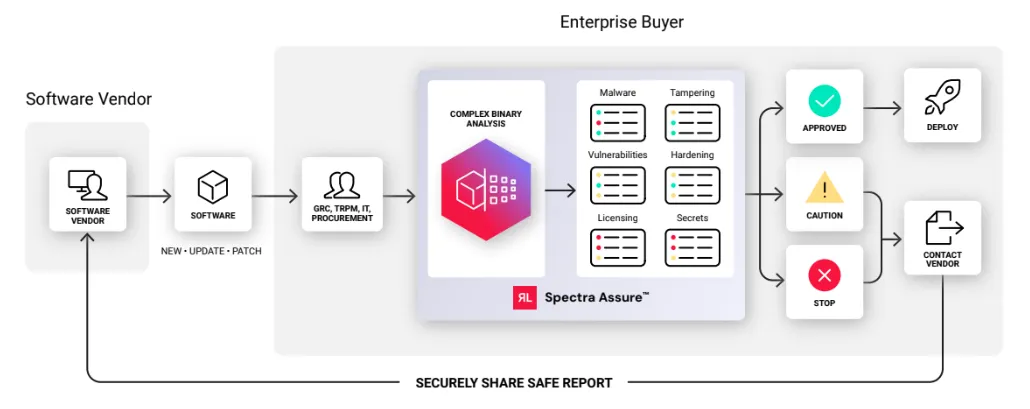
Figure 2: Spectra Assure delivers the primary control to assess for embedded risks & threats in applications before purchase or deployment. The SAFE report can then be shared back with the vendor for expedited remediation.
The proliferation of software supply chain threats targeting trusted software providers, combined with rising regulatory pressure means that security and risk leaders must demonstrate due diligence for ALL software that is deployed in their environment. Third-party commercial software risk is a black box, and organizations must be proactive about flagging embedded risk within the software they buy.
By aligning on roles and responsibilities, and implementing security checks throughout the software lifecycle—from acquisition to deployment to monitoring to updates—companies can protect themselves from potentially devastating attacks. Spectra Assure provides an independent assessment and a consistent, primary control that is needed to ensure third-party software is safe to use.
For more details on how to operationalize Third-Party Software Risk Management, check out The CISO Survival Guide: Operationalizing Third-Party Software Risk Management.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial